Linux基础——CVE漏洞查询及CVE-2025-26465 CVE-2025-26466修复方法
一、Openssh社区安全公告
# Openssh安全公告
https://www.openssh.com/security.html

#release notes
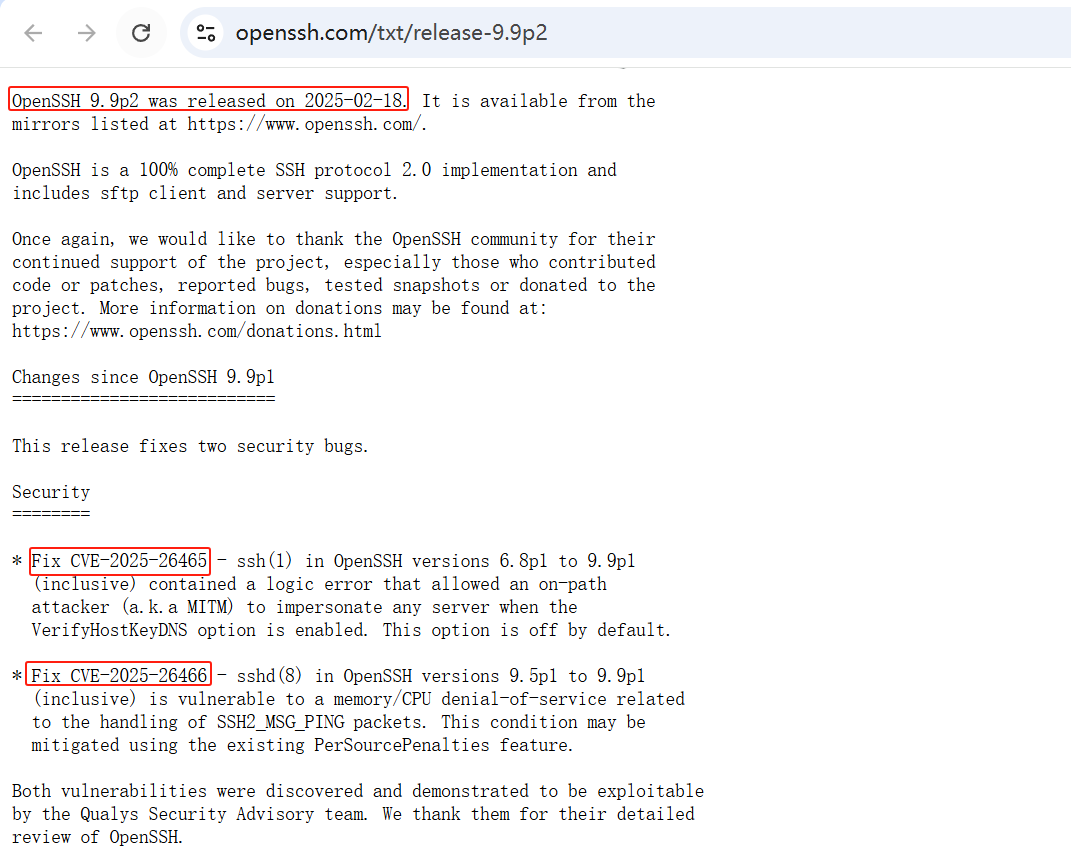
https://www.openssh.com/txt/release-9.9p2
# 漏洞代码详情及实验案例
# Qualys Security Advisory Team
https://www.qualys.com/2025/02/18/openssh-mitm-dos.txt
# 漏洞公告目录
======================================================================== Contents ======================================================================== Summary Background Experiments Results MitM attack against OpenSSH's VerifyHostKeyDNS-enabled client DoS attack against OpenSSH's client and server (memory consumption) DoS attack against OpenSSH's client and server (CPU consumption) Proof of concept Acknowledgments Timeline
CVE-2025-26465: MitM attack against OpenSSH's VerifyHostKeyDNS-enabled client. CVE-2025-26466: DoS attack against OpenSSH's client and server.
========================================================================
Summary
========================================================================
We discovered two vulnerabilities in OpenSSH:
- The OpenSSH client is vulnerable to an active machine-in-the-middle
attack if the VerifyHostKeyDNS option is enabled (it is disabled by
default): when a vulnerable client connects to a server, an active
machine-in-the-middle can impersonate the server by completely
bypassing the client's checks of the server's identity.
This attack against the OpenSSH client succeeds whether
VerifyHostKeyDNS is "yes" or "ask" (it is "no" by default), without
user interaction, and whether the impersonated server actually has an
SSHFP resource record or not (an SSH fingerprint stored in DNS). This
vulnerability was introduced in December 2014 (shortly before OpenSSH
6.8p1) by commit 5e39a49 ("Add RevokedHostKeys option for the client
to allow text-file or KRL-based revocation of host keys"). For more
information on VerifyHostKeyDNS:
https://man.openbsd.org/ssh_config#VerifyHostKeyDNS
https://man.openbsd.org/ssh#VERIFYING_HOST_KEYS
Note: although VerifyHostKeyDNS is disabled by default, it was enabled
by default on FreeBSD (for example) from September 2013 to March 2023;
for more information:
https://cgit.freebsd.org/src/commit/?id=83c6a52
https://cgit.freebsd.org/src/commit/?id=41ff5ea
- The OpenSSH client and server are vulnerable to a pre-authentication
denial-of-service attack: an asymmetric resource consumption of both
memory and CPU. This vulnerability was introduced in August 2023
(shortly before OpenSSH 9.5p1) by commit dce6d80 ("Introduce a
transport-level ping facility").
On the server side, this attack can be easily mitigated by mechanisms
that are already built in OpenSSH: LoginGraceTime, MaxStartups, and
more recently (OpenSSH 9.8p1 and newer) PerSourcePenalties; for more
information:
https://man.openbsd.org/sshd_config#LoginGraceTime
https://man.openbsd.org/sshd_config#MaxStartups
https://man.openbsd.org/sshd_config#PerSourcePenalties
二、Openssh修复包
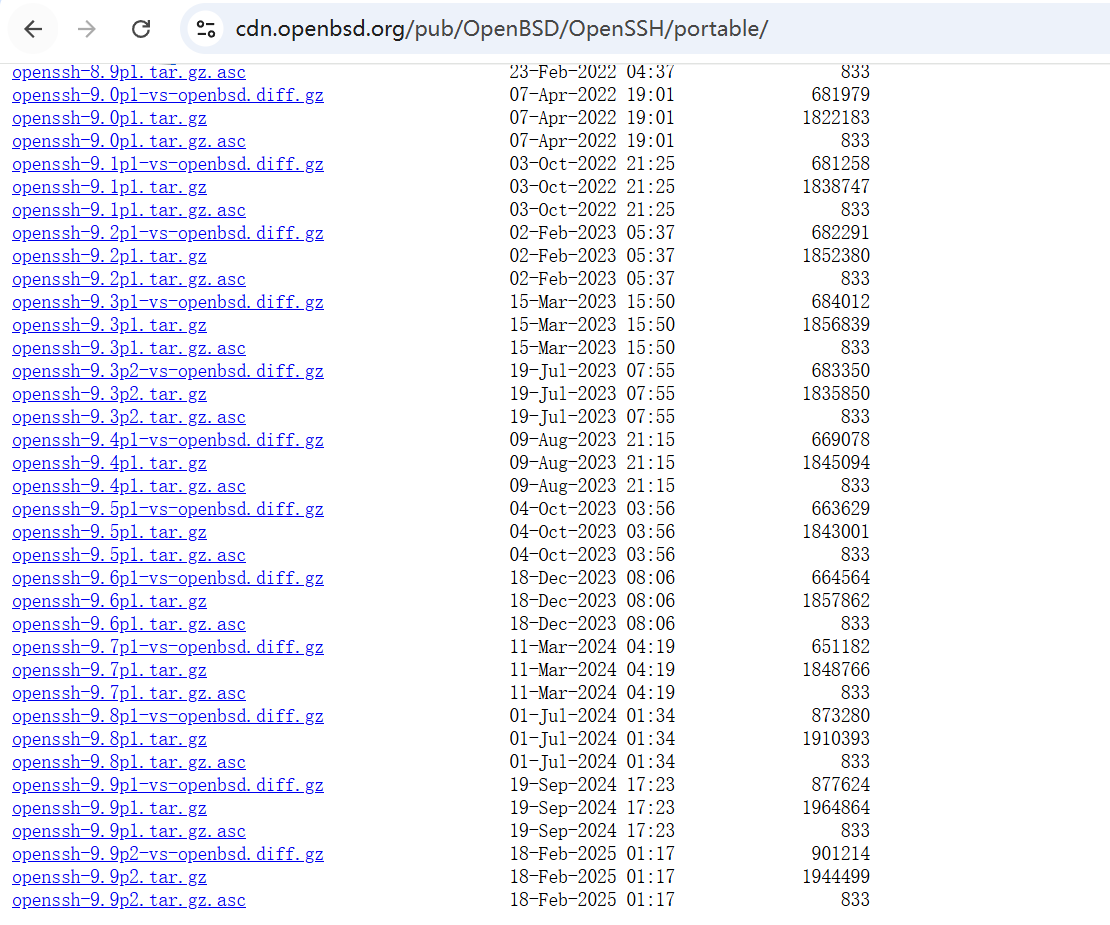
# portable目录下包含所有小版本
# 目前最新openssh-9.9p2
https://cdn.openbsd.org/pub/OpenBSD/OpenSSH/portable/openssh-9.9p2.tar.gz
三、RPM包构建
# 参考
https://www.cnblogs.com/gkhost/p/18783442
帮助
# /etc/ssh/sshd_config配置参数详情 https://man.openbsd.org/sshd_config#LoginGraceTime
# 安全工具
https://docs.metasploit.com/docs/pentesting/metasploit-guide-ssh.html
https://www.kali.org/tools/metasploit-framework/
稳步前行,只争朝夕。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号