审计系统---堡垒机项目之strace追踪ssh
strace 追踪ssh的进程ID,记录操作的命令[实际上是内核里面记录的东西],进行操作日志的Py解析达到效果。
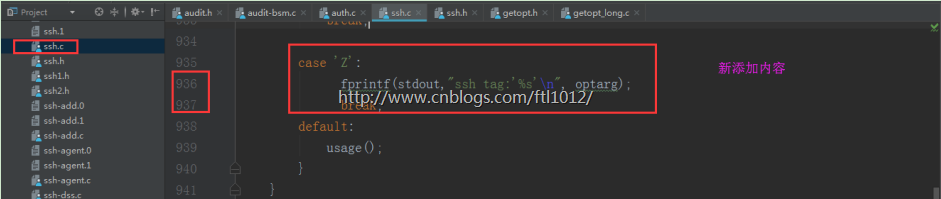
修改ssh源码添加访问标志位
源码下载:【本文示例:openssh-7.4p1.tar.gz】
https://cloudflare.cdn.openbsd.org/pub/OpenBSD/OpenSSH/portable/
导入工程到PyCharm
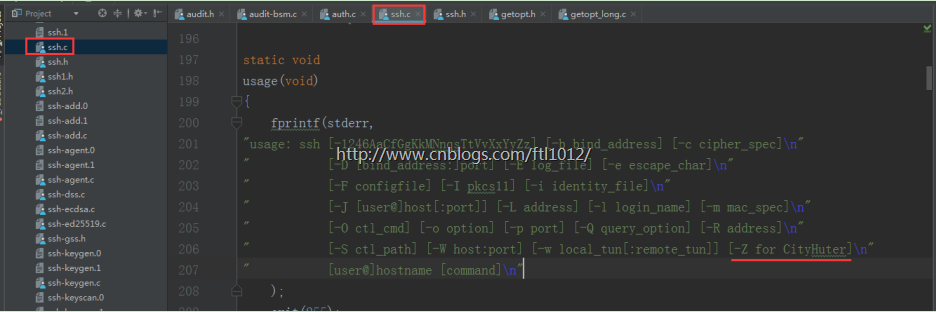
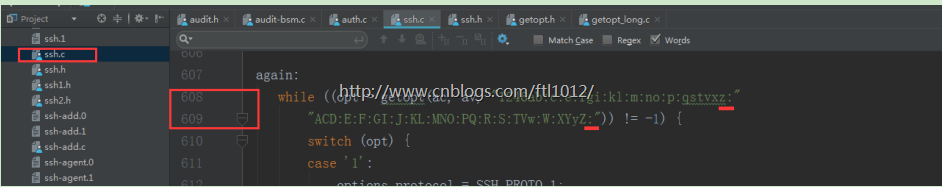
ssh.c
在ubuntu上安装openssl dev组件
sudo apt-get install zlib1g sudo apt-get install zlib1g-dev sudo apt-get install libssl-dev
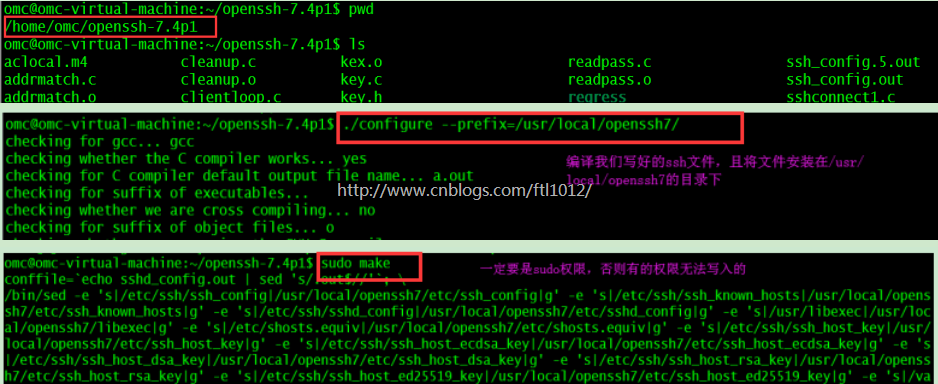
上传软件包到Ubuntu并解压:
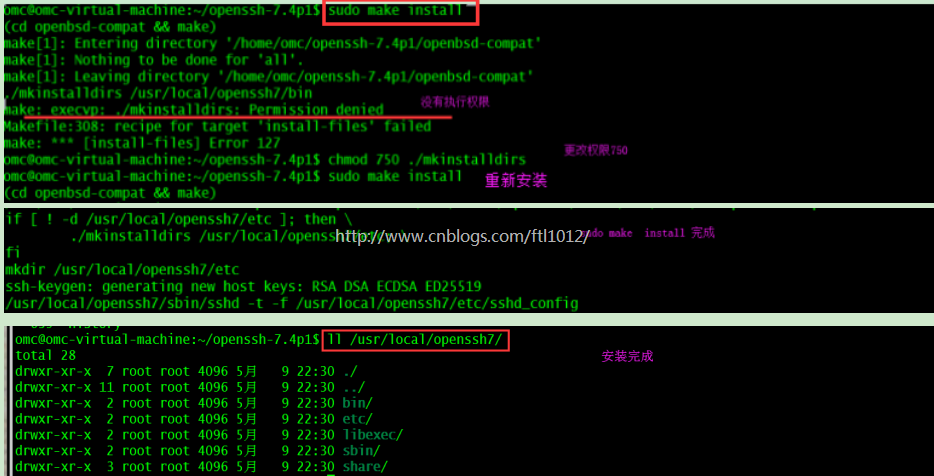
unzip openssh-7.4p1.zip cd src/openssh-7.4p1/ chmod 750 ./mkinstalldirs chmod 7500 ./configure sudo ./configure --prefix=/usr/local/openssh7/ sudo make && sudo make install 【make clean 可以清除上次的编译结果】
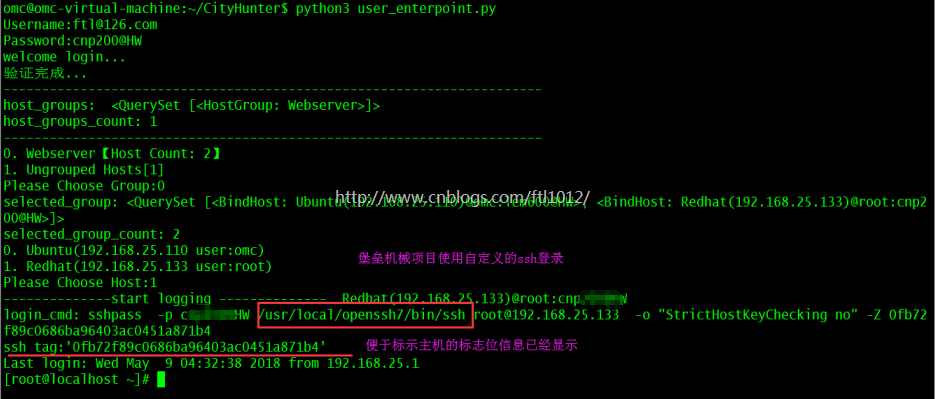
登录成功
omc@omc-virtual-machine:~/CityHunter$ python3 user_enterpoint.py
audit.py
#_*_coding:utf-8_*_
import re
class AuditLogHandler(object):
'''分析audit log日志'''
def __init__(self, log_file):
self.log_file_obj = self._get_file(log_file)
def _get_file(self,log_file):
return open(log_file)
def parse(self):
cmd_list = []
cmd_str = ''
catch_write5_flag = False #for tab complication
for line in self.log_file_obj:
#print(line.split())
line = line.split()
try:
pid,time_clock,io_call,char = line[0:4]
if io_call.startswith('write(9'):
if char == '"\\177",':#回退
char = '[1<-del]'
if char == '"\\33OB",': #vim中下箭头
char = '[down 1]'
if char == '"\\33OA",': #vim中下箭头
char = '[up 1]'
if char == '"\\33OC",': #vim中右移
char = '[->1]'
if char == '"\\33OD",': #vim中左移
char = '[1<-]'
if char == '"\33[2;2R",': #进入vim模式
continue
if char == '"\\33[>1;95;0c",': # 进入vim模式
char = '[----enter vim mode-----]'
if char == '"\\33[A",': #命令行向上箭头
char = '[up 1]'
catch_write5_flag = True #取到向上按键拿到的历史命令
if char == '"\\33[B",': # 命令行向上箭头
char = '[down 1]'
catch_write5_flag = True # 取到向下按键拿到的历史命令
if char == '"\\33[C",': # 命令行向右移动1位
char = '[->1]'
if char == '"\\33[D",': # 命令行向左移动1位
char = '[1<-]'
cmd_str += char.strip('"",')
if char == '"\\t",':
catch_write5_flag = True
continue
if char == '"\\r",':
cmd_list.append([time_clock,cmd_str])
cmd_str = '' # 重置
if char == '"':#space
cmd_str += ' '
if catch_write5_flag: # to catch tab completion
if io_call.startswith('write(5'):
if io_call == '"\7",': # 空键,不是空格,是回退不了就是这个键
pass
else:
cmd_str += char.strip('"",')
catch_write5_flag = False
except ValueError as e:
print("\033[031;1mSession log record err,please contact your IT admin,\033[0m",e)
#print(cmd_list)
for cmd in cmd_list:
print(cmd)
# return cmd_list
if __name__ == "__main__":
parser = AuditLogHandler('ssh.log')
parser.parse()
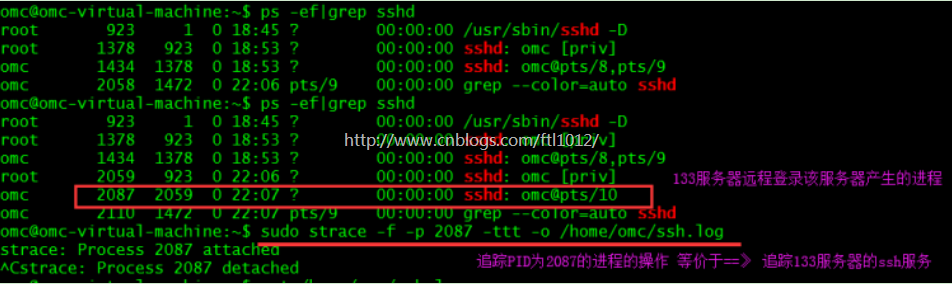
追踪进程并写入ssh操作到文件中
Ps: 此时机器A已经ssh登录了机器B,这里的2087就是它的ssh进程PID
机器A登录后的操作命令就记录在了ssh.log文件中了
omc@omc-virtual-machine:~$ sudo strace -f -p 2087 -ttt -o /home/omc/ssh.log
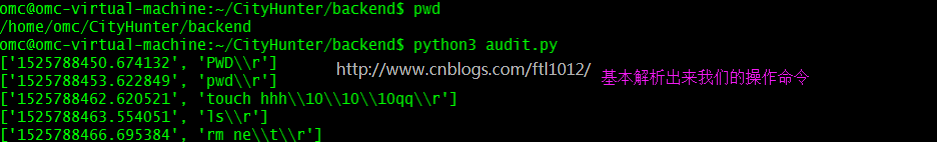
追踪到的ssh操作文件的解析:
omc@omc-virtual-machine:~/CityHunter/backend$ cd /home/omc/CityHunter/backend omc@omc-virtual-machine:~/CityHunter/backend$ vim audit.py omc@omc-virtual-machine:~/CityHunter/backend$ cp /home/omc/ssh.log ./ [复制文件到当前目录] omc@omc-virtual-machine:~/CityHunter/backend$ python3 audit.py


 浙公网安备 33010602011771号
浙公网安备 33010602011771号