[MRCTF2020]pyFlag
[MRCTF2020]pyFlag
在3张图片结尾发现有隐藏的压缩包信息
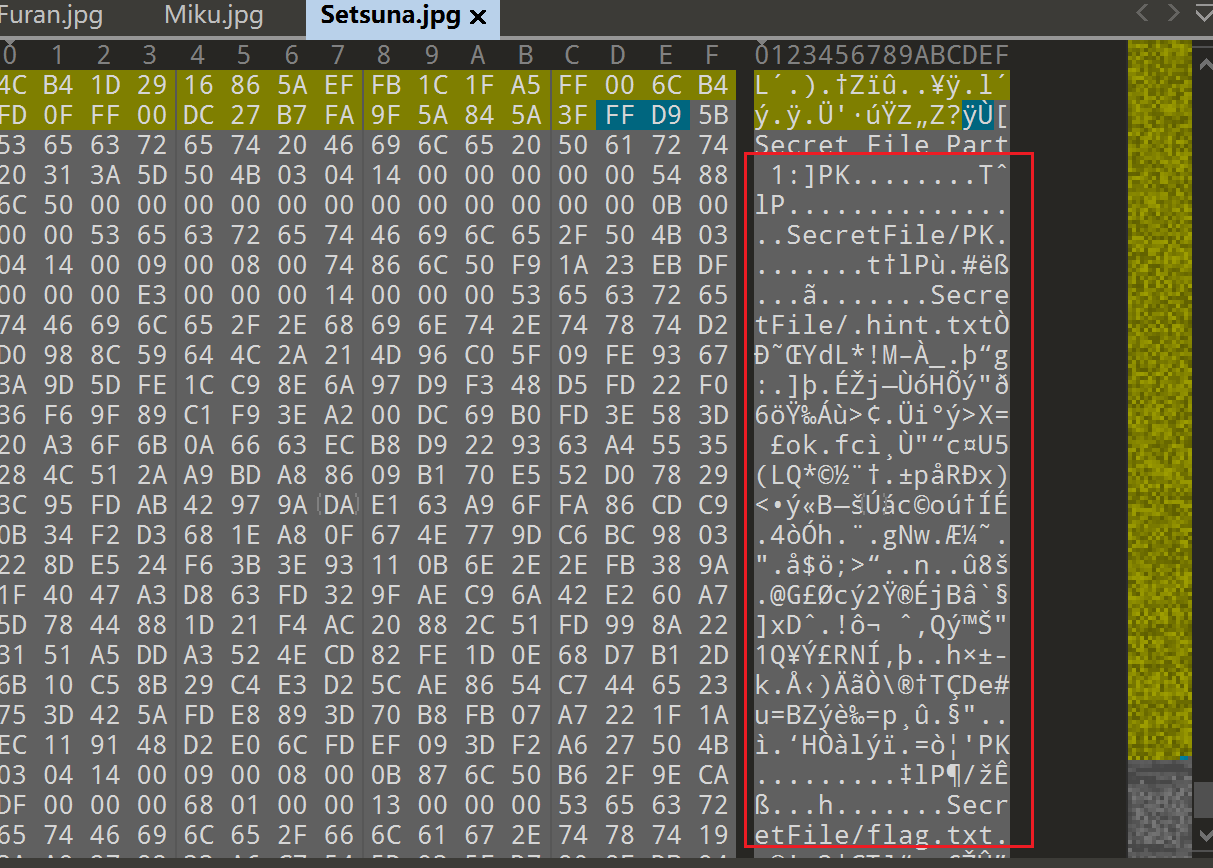
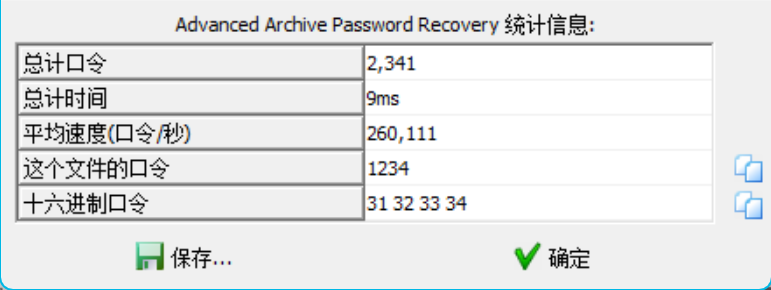
提取出来组合成一个压缩包,暴力破解得到密码1234
打开压缩包里的2个txt,发现提示和编码后的字符串
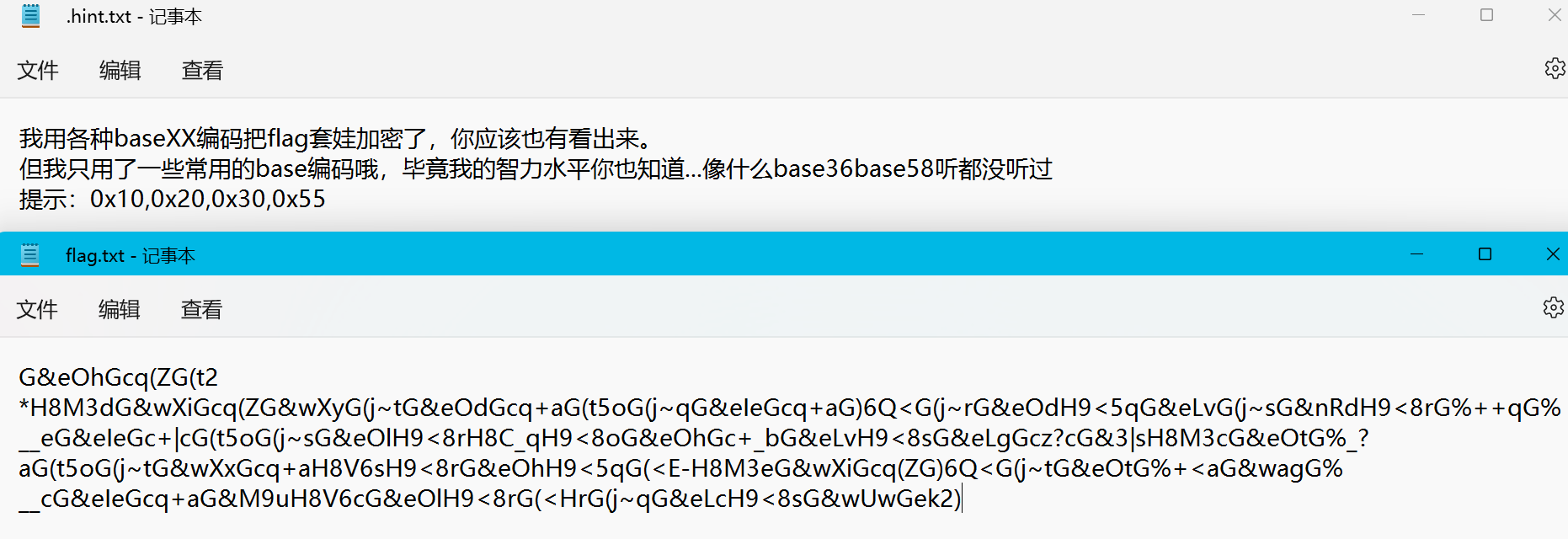
根据.hint.txt文件的说明,得知flag经过了base加密,且为base16,base32,base64、base85,我们需要根据种base编码的特征来提取信息并解码。
base16:构成为字母A-F数字0-9;匹配正则"^[0-9A-F]+$"
base32:构成为字母A-Z数字2-9符号=;匹配正则"^[A-Z2-7=]+$"
base64:构成为字母A-Z,a-z,数字0-9符号+/=;匹配正则"^[A-Za-z0-9+/=]+$"
base85:比较复杂;直接作为判断条件的else
这里我发现编码几个网站上的base85解码都有问题
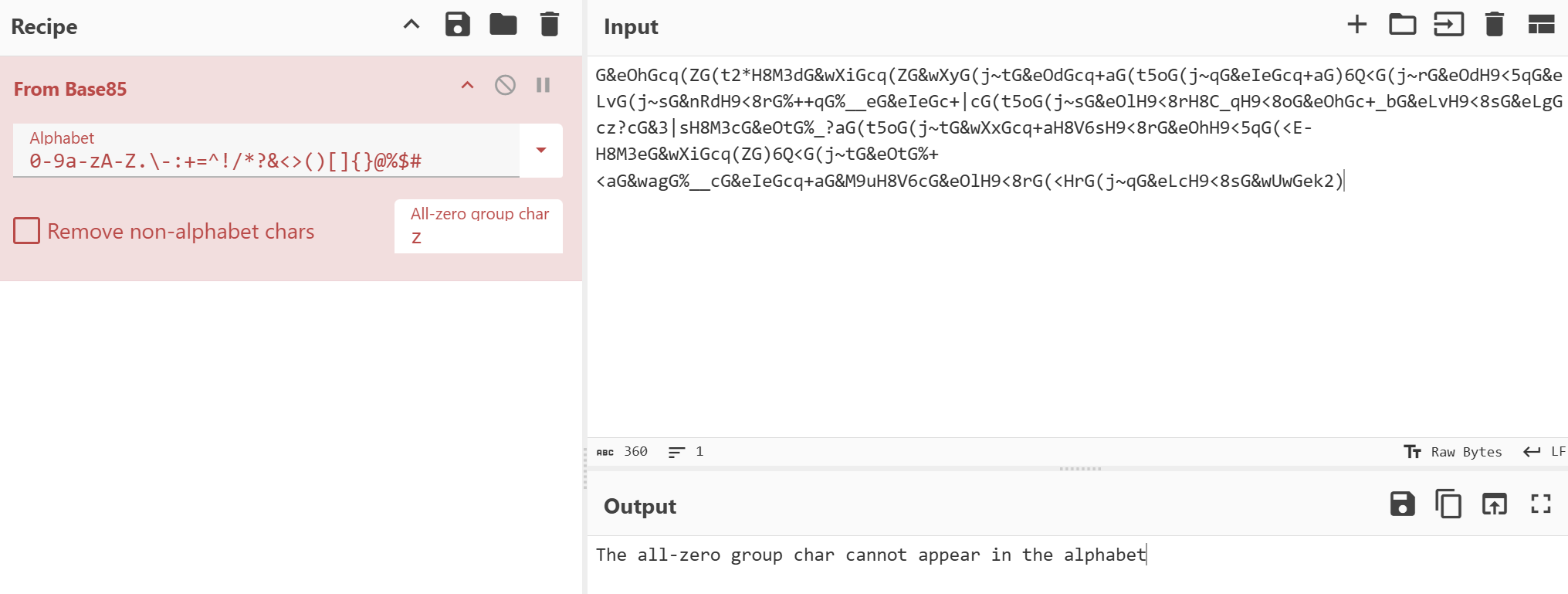
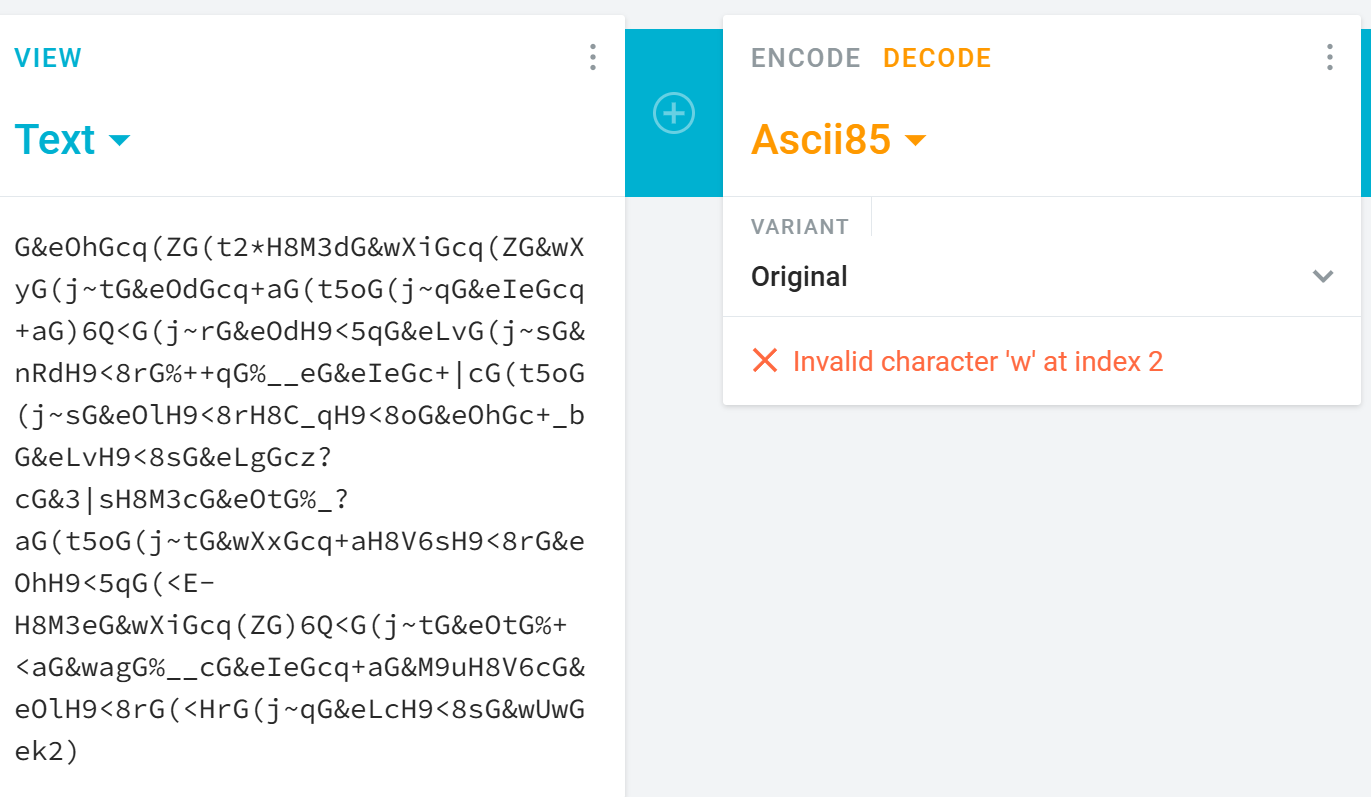
只能使用python来解码了
#!/usr/bin/env python
import base64
import re
def baseDec(text,type):
if type == 1:
print(1)
return base64.b16decode(text)
elif type == 2:
print(2)
return base64.b32decode(text)
elif type == 3:
print(3)
return base64.b64decode(text)
elif type == 4:
print(4)
return base64.b85decode(text)
else:
pass
def detect(text):
try:
if re.match("^[0-9A-F=]+$",text.decode()) is not None:
return 1
except:
pass
try:
if re.match("^[A-Z2-7=]+$",text.decode()) is not None:
return 2
except:
pass
try:
if re.match("^[A-Za-z0-9+/=]+$",text.decode()) is not None:
return 3
except:
pass
return 4
def autoDec(text):
while True:
if b"MRCTF{" in text:
print("\n"+text.decode())
break
code = detect(text)
text = baseDec(text,code)
with open("flag.txt",'rb') as f:
flag = f.read()
autoDec(flag)
得到flag{Y0u_Are_4_p3rFect_dec0der}



 浙公网安备 33010602011771号
浙公网安备 33010602011771号