Identityserver4中ResourceOwnerPassword 模式获取refreshtoken
一、IS4服务端配置
1、配置Client
new Client { ClientId = "xamarin", ClientSecrets = { new Secret("123456".Sha256()) }, AccessTokenLifetime = 1800,//设置AccessToken过期时间 AllowedGrantTypes = GrantTypes.ResourceOwnerPassword,
//RefreshTokenExpiration = TokenExpiration.Absolute,//刷新令牌将在固定时间点到期 AbsoluteRefreshTokenLifetime = 2592000,//RefreshToken的最长生命周期,默认30天 RefreshTokenExpiration = TokenExpiration.Sliding,//刷新令牌时,将刷新RefreshToken的生命周期。RefreshToken的总生命周期不会超过AbsoluteRefreshTokenLifetime。 SlidingRefreshTokenLifetime = 3600,//以秒为单位滑动刷新令牌的生命周期。
//按照现有的设置,如果3600内没有使用RefreshToken,那么RefreshToken将失效。即便是在3600内一直有使用RefreshToken,RefreshToken的总生命周期不会超过30天。所有的时间都可以按实际需求调整。
AllowOfflineAccess = true,//如果要获取refresh_tokens ,必须把AllowOfflineAccess设置为true AllowedScopes = new List<string> { "api", StandardScopes.OfflineAccess, //如果要获取refresh_tokens ,必须在scopes中加上OfflineAccess StandardScopes.OpenId,//如果要获取id_token,必须在scopes中加上OpenId和Profile,id_token需要通过refresh_tokens获取AccessToken的时候才能拿到(还未找到原因) StandardScopes.Profile//如果要获取id_token,必须在scopes中加上OpenId和Profile } }
2、实现IResourceOwnerPasswordValidator接口,自定义用户登录
public class ResourceOwnerPasswordValidator : IResourceOwnerPasswordValidator { public Task ValidateAsync(ResourceOwnerPasswordValidationContext context) { //根据context.UserName和context.Password与数据库的数据做校验,判断是否合法 if (context.UserName == "test" && context.Password == "test") { context.Result = new GrantValidationResult( subject: context.UserName, authenticationMethod: OidcConstants.AuthenticationMethods.Password); } else { //验证失败 context.Result = new GrantValidationResult( TokenRequestErrors.InvalidGrant, "invalid custom credential" ); } return Task.FromResult(0); } }
3、在Startup中加入如下配置
services.AddIdentityServer() .AddSigningCredential(IdentityServerBuilderExtensionsCrypto.CreateRsaSecurityKey()) .AddInMemoryApiResources(Config.GetApis()) .AddInMemoryIdentityResources(Config.GetIdentityResources()) .AddInMemoryClients(Config.GetClients()) .AddProfileService<ProfileService>() .AddResourceOwnerValidator<ResourceOwnerPasswordValidatorService>();//注入自定义用户登录验证
二、客户端获取access_token+refresh_token
如果是后台代码需要获取access_token+refresh_token,则可以参考官方Samples,https://github.com/IdentityServer/IdentityServer4.Samples/tree/release/Clients/src/ConsoleResourceOwnerFlowRefreshToken
如果是前端需要获取access_token+refresh_token,则可以通过 http://localhost:5000/connect/token 接口获取
1、获取access_token+refresh_token
获取access_token+refresh_token的参数配置如下,Content-Type的值是 application/x-www-form-urlencoded
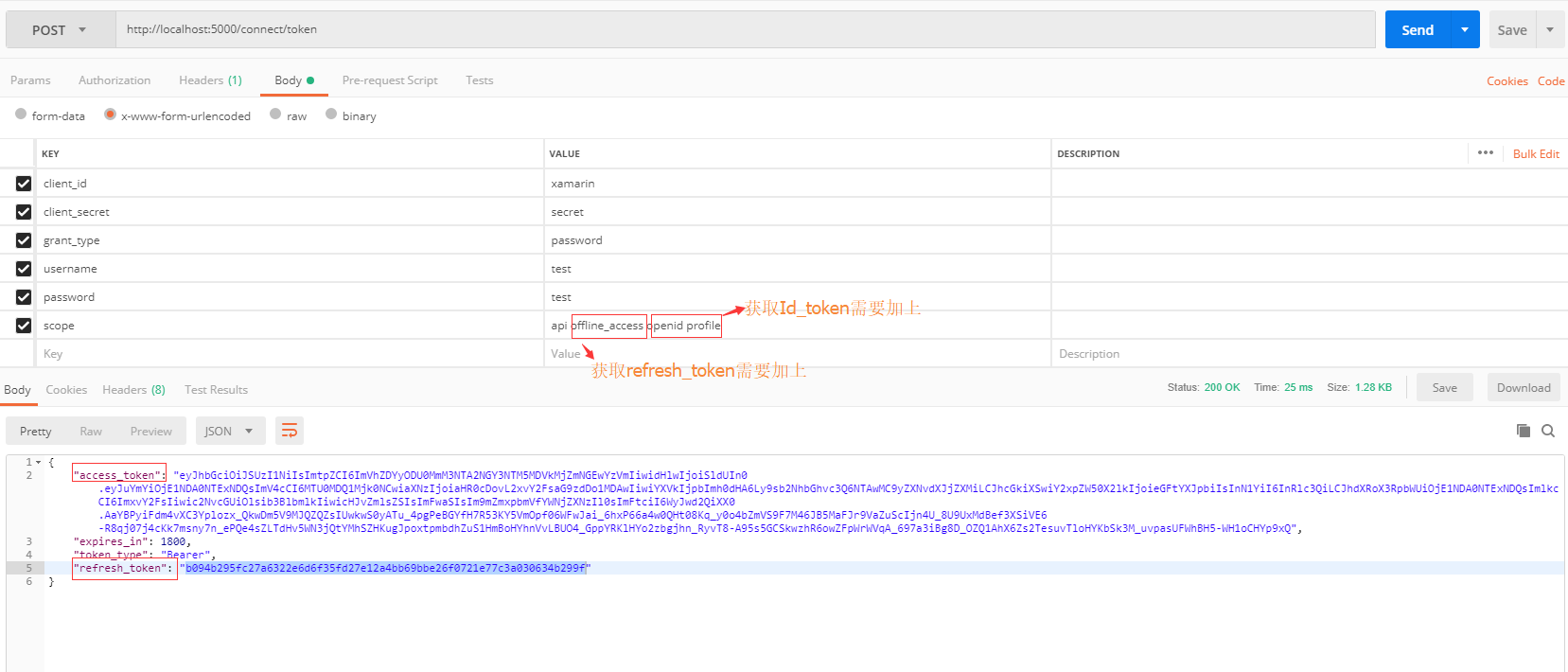
2、通过第一步获取到的refresh_token去刷新access_token




 浙公网安备 33010602011771号
浙公网安备 33010602011771号