csdn 网站逆向之console破解
本来是想破解显示它的内容来着,最近刚好写了几个破解相关的工具,想试试水,哈哈,结果摘了一个大跟头!
原因是console的日志功能被隐藏了, 输出任何东西都不好使!
想破解的它的第一步,就得先破console。
正文开始:
这是csdn的网站的显示:
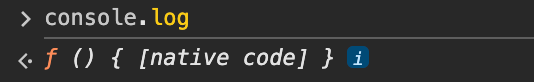
其他网站的显示:

很明显,csdn做了手脚。
做了什么手脚呢? 查看log的原型

这里有3个有用的信息, toString, name和 boundThis. boundThis可以找
看到这里我想到了一个奇淫技巧,这个toString是突破口, 因为它是用的真实的log.toString()的, 先看看这个toString方法

离成功近了一丢丢,因为看到了boundThis. 以为我可以 通过this方法这个log。
通过特别的方法拿到了这个value: console.log['toString']['bind'](console.log)
这个value是真的console.log.toString方法, 现在问题变成了如果通过toString拿到真实的console.log引用?
尝试将这个this渗透到新方法试试?通过实际测试无法渗透到真实的console.log. 只能获取真实的toString. 无法获取它里面的this。 它就像闭包一样,从语言层无法突破!
那就从开发者工具调试着手, 通过断点拿到真实的log

有点意思,实际console.log 居然不会断点进入, 那么就直接搞它吧, 不讲武德的方式盘它:
找到代码:
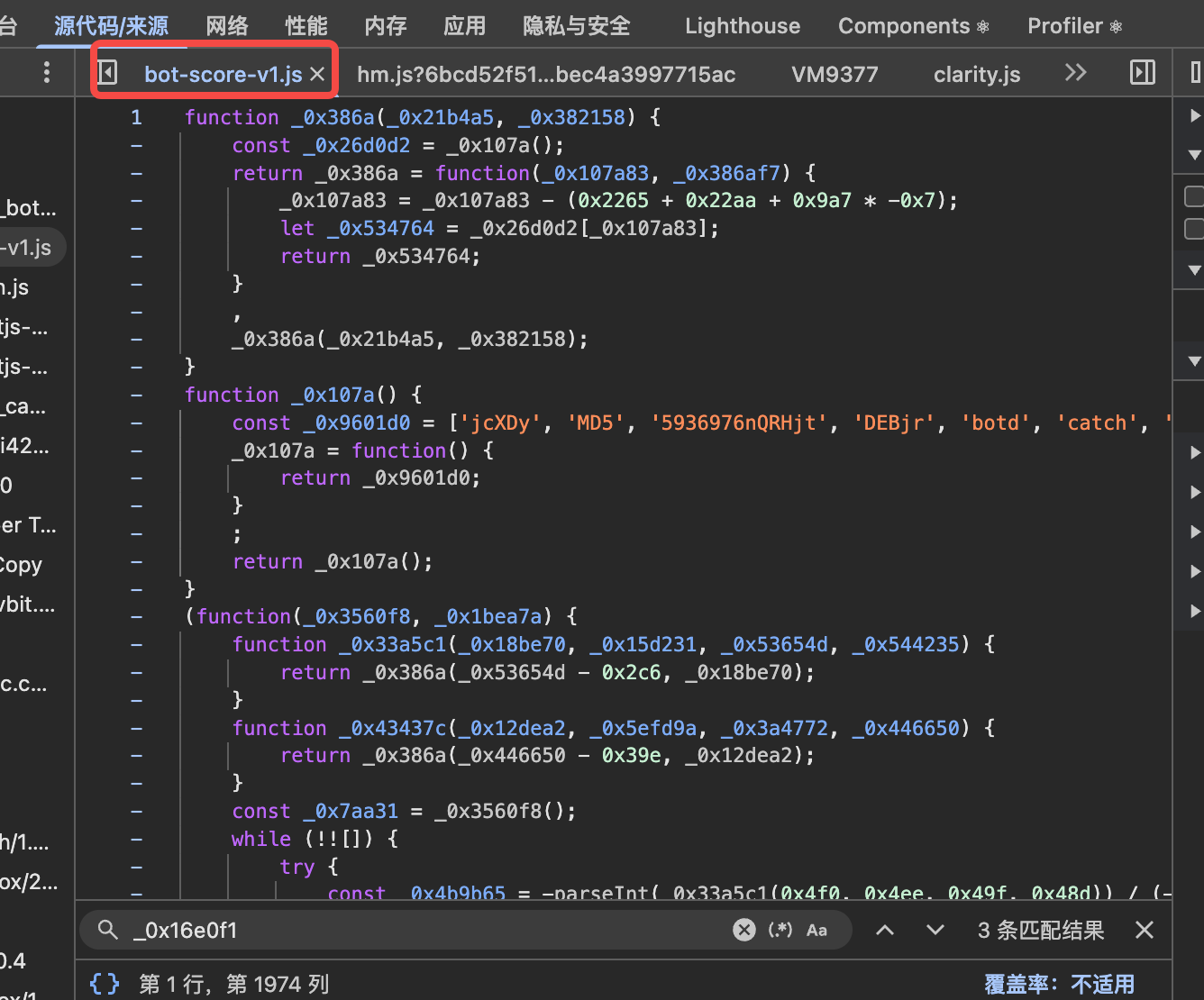
混淆了,so easy 那就反混淆吧, 一切防护在我这里都是花拳绣腿:
!(function (...args) { const _0x228bed = (() => (_0x39af13, _0x346630) => { const _0x14990f = function () { if (_0x346630) { const _0x22a92b = _0x346630.apply(_0x39af13, args); _0x346630 = null; return _0x22a92b; } }; return _0x14990f; })(); const _0x4c84d5 = _0x228bed(this, () => { const _0x17b582 = () => { let _0x20d217; try { _0x20d217 = (() => (() => {}).constructor("return this")())(); } catch (_0x2c3910) { _0x20d217 = window; } return window; }; const _0x15847f = _0x17b582(); const _0x23f78c = (_0x15847f.console = _0x15847f.console || {}); const _0x37fa34 = [ "log", "warn", "info", "error", "exception", "table", "trace", ]; for (let _0x122429 = 0; _0x122429 < _0x37fa34.length; _0x122429++) { const _0x219b17 = _0x228bed.constructor.prototype.bind(_0x228bed); const _0x37fa34__0x122429 = _0x37fa34[_0x122429]; const _0x16e0f1 = _0x23f78c[_0x37fa34__0x122429] || _0x219b17; _0x219b17.__proto__ = _0x228bed.bind(_0x228bed); _0x219b17.toString = _0x16e0f1.toString.bind(_0x16e0f1); _0x23f78c[_0x37fa34__0x122429] = _0x219b17; } }); _0x4c84d5(); function _0x4a7a78(_0x430275) { const _0x406624 = document.cookie.split("; "); for (let _0xe472dd = 0; _0xe472dd < _0x406624.length; _0xe472dd++) { const _0x1b0487 = _0x406624[_0xe472dd].split("="); if (_0x430275 == _0x1b0487[0]) { return unescape(_0x1b0487[1]); } } return ""; } function _0x26f755(_0x3fa7c8, _0x57d1e2) { const _0x48e1fe = CryptoJS.MD5(_0x57d1e2).toString(); const _0x3e3ba2 = CryptoJS.enc.Utf8.parse(_0x48e1fe.substring(0, 16)); const _0x250784 = CryptoJS.enc.Utf8.parse(_0x48e1fe.substring(16)); const _0x58361c = CryptoJS.AES.encrypt(_0x3fa7c8, _0x3e3ba2, { iv: _0x250784, mode: CryptoJS.mode.CBC, padding: CryptoJS.pad.Pkcs7, }); return _0x58361c.toString(); } function _0x44786b(_0x4f5fba) { let _0x5c5e80 = {}; _0x5c5e80.visitorId = _0x4f5fba.visitorId; _0x5c5e80.confidence = _0x4f5fba.confidence.score; let { components, botd } = _0x4f5fba; if (components != undefined) { (_0x5c5e80.fontsLength = components.fonts.value != undefined ? components.fonts.value.length : 0), (_0x5c5e80.audio = components.audio.value != undefined && components.audio.value > 0), (_0x5c5e80.colorGamut = components.colorGamut.value != undefined), (_0x5c5e80.colorDepth = components.colorDepth.value != undefined ? components.colorDepth.value : 0), (_0x5c5e80.hardwareConcurrency = components.hardwareConcurrency.value != undefined ? components.hardwareConcurrency.value : 0), (_0x5c5e80.sessionStorage = components.sessionStorage.value), (_0x5c5e80.localStorage = components.localStorage.value), (_0x5c5e80.indexedDB = components.indexedDB.value), (_0x5c5e80.canvas = components.canvas.value != undefined ? components.canvas.value.winding : false), (_0x5c5e80.languagesLength = components.languages.value != undefined ? components.languages.value.length : 0), (_0x5c5e80.touchSupport = components.touchSupport.value.touchStart), (_0x5c5e80.cookiesEnabled = components.cookiesEnabled.value), (_0x5c5e80.videoCard = components.videoCard.value), (_0x5c5e80.pdfViewerEnabled = components.pdfViewerEnabled.value), (_0x5c5e80.platform = components.platform.value); } let botd_components = botd.components; if (botd_components != undefined) { _0x5c5e80.userAgent = botd_components.userAgent.value; _0x5c5e80.windowSize = botd_components.windowSize.value; _0x5c5e80.pluginsLength = botd_components.pluginsLength.value; _0x5c5e80.webGL = botd_components.webGL.value != undefined; _0x5c5e80.webDriver = botd_components.webDriver.value; _0x5c5e80.android = botd_components.android.value; _0x5c5e80.distinctiveProps = botd_components.distinctiveProps.value; _0x5c5e80.browserKind = botd_components.browserKind.value; _0x5c5e80.browserEngineKind = botd_components.browserEngineKind.value; } _0x5c5e80.bot = botd.bot; if ( botd.bot != true && (botd_components == undefined || botd_components == undefined) ) { _0x5c5e80.bot = true; } return _0x5c5e80; } function _0x4f90d3(_0x2291a1) { let _0x47dd0b = _0x4a7a78("bc_bot_session"); let _0x2291a1_visitorId = _0x2291a1.visitorId; let _0x436630 = _0x26f755( JSON.stringify(_0x2291a1), _0x47dd0b + _0x2291a1_visitorId ); const _0x478b03 = {}; _0x478b03.fp = _0x2291a1_visitorId; _0x478b03.enc = _0x436630; const _0x57c8ed = _0x478b03; fetch("/cdn_cgi_bs_bot/api", { method: "POST", headers: { "Content-Type": "application/json", }, body: JSON.stringify(_0x57c8ed), }) .then((_0x3115e2) => _0x3115e2.json()) .then((_0x31b2d2) => _0x31b2d2.status == 1) ["catch"]((_0x34cbcd) => console.error("Error:", _0x34cbcd)); } let _0x2fcdf7; const _0x24d047 = import( "/cdn_cgi_bs_bot/static/fingerprintjs-botd-v1.js" ).then((_0x511b68) => _0x511b68.load()); _0x24d047 .then((_0x117ba8) => { let _0x15de72 = _0x117ba8.detect(); _0x15de72.components = _0x117ba8.components; _0x15de72.detections = _0x117ba8.detections; return _0x15de72; }) .then((_0xc5e992) => { _0x2fcdf7 = _0xc5e992; }) ["catch"]((_0x408cce) => console.error(_0x408cce)); const _0x179f3f = import("/cdn_cgi_bs_bot/static/fingerprintjs-v3.js").then( (_0x189e19) => _0x189e19.load() ); _0x179f3f .then((_0x513bf9) => _0x513bf9.get()) .then((_0xdd40f6) => { _0xdd40f6.botd = _0x2fcdf7; let _0x24c03c = _0x44786b(_0xdd40f6); _0x4f90d3(_0x24c03c); }); })();
凑合着看吧, 能搞事情就行。
调试它:

破解成功:

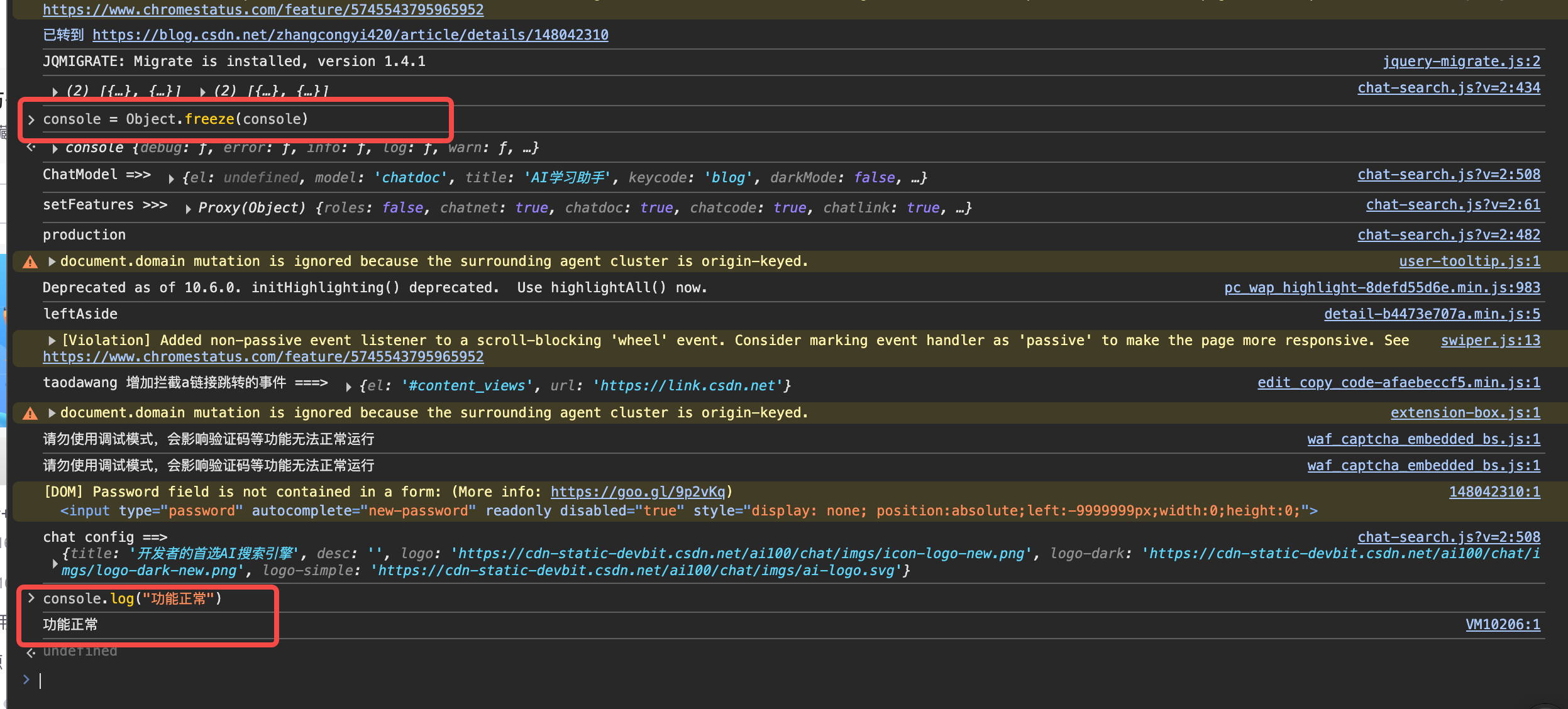
另外的一种破解方式: console = Object.freeze(console)



 浙公网安备 33010602011771号
浙公网安备 33010602011771号