Juniper SRX1500 防火墙 Internet与SDWAN分流配置
Chassis
管理接口fxp0
大多数SRX设备都有独立的管理接口,名称为fxp0。 低端一些的设备,比如SRX300/320是没有独立的fxp0的。 需要从接口中挑一个作为管理接口。
Interface Renumbering
Juniper的堆叠叫Chassis, 堆叠的节点分别叫node0和node1。
堆叠建立以后, 在查看配置的时候,针对SRX1500,node0上的接口ge-0/0/0, node1的对应接口就变成了ge-7/0/0。 不同的设备不一定是7,根据设备的不同而不同,官方叫的名称叫”SRX Series Firewalls Interface Renumbering“。
官方文档参考:Configuring Chassis Clustering on SRX Series Devices
Redundant Ethernet Interfaces
堆叠的设备中配置冗余接口叫reth,概念有些像华为/华三设备中的vrrp。配置的时候先配置一个虚拟的reth接口,然后把这个虚拟接口应用在物理接口上。
interfaces {
ge-2/0/2 {
gigether-options {
redundant-parent reth2;
}
}
reth2 {
redundant-ether-options {
redundancy-group 1;
}
unit 0 {
family inet {
address 10.1.1.1/24;
}
}
}
}
建立堆叠
SRX堆叠需要互联两对接口,一对作为控制口(Control Port),一对作为数据口(Fabric Port), 在配置中的名称为fab0和fab1;其中控制口要指定连接特定的物理接口,比如:
- SRX1500有专门的HA接口作为Control Port,
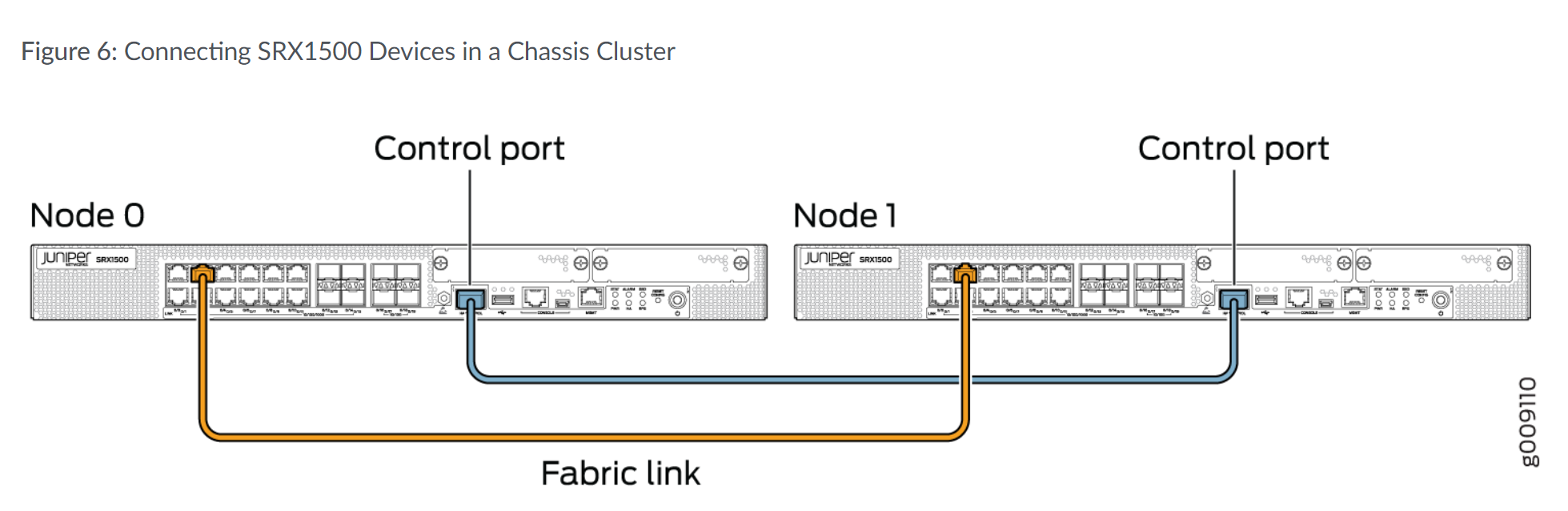
- SRX4100上Control Port和Fabric Port都是独立的

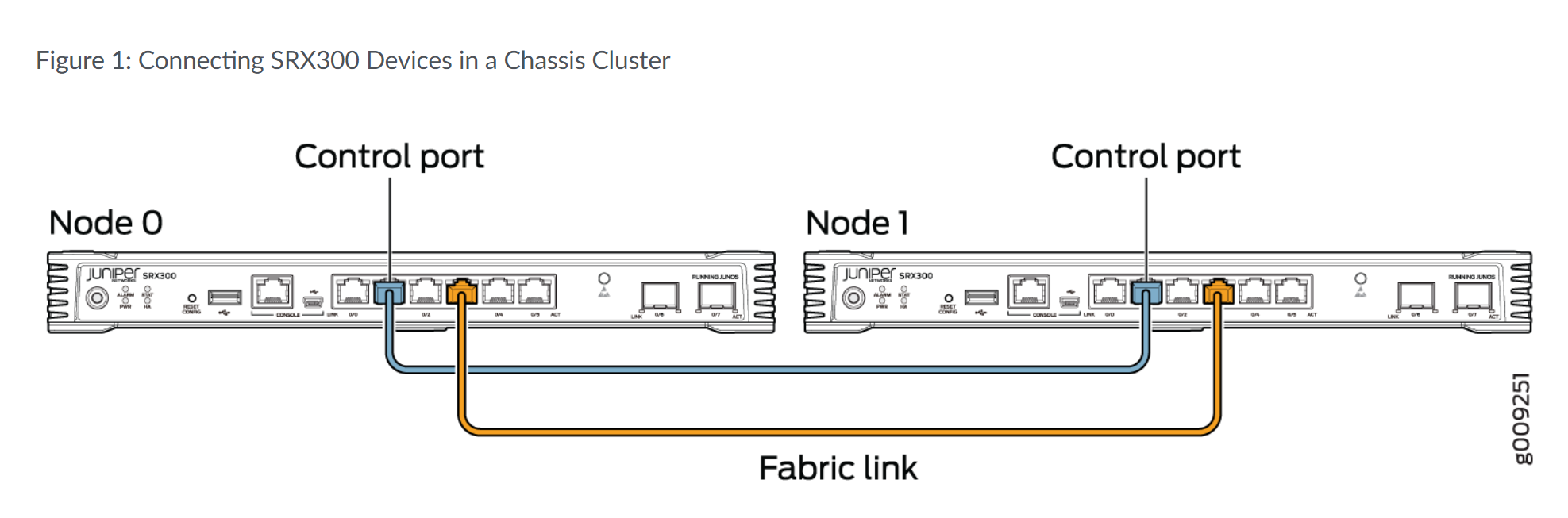
- SRX300连接node0上的ge-0/0/1,和node1上的ge-1/0/1。(SRX300的Renumbering Constant是1)
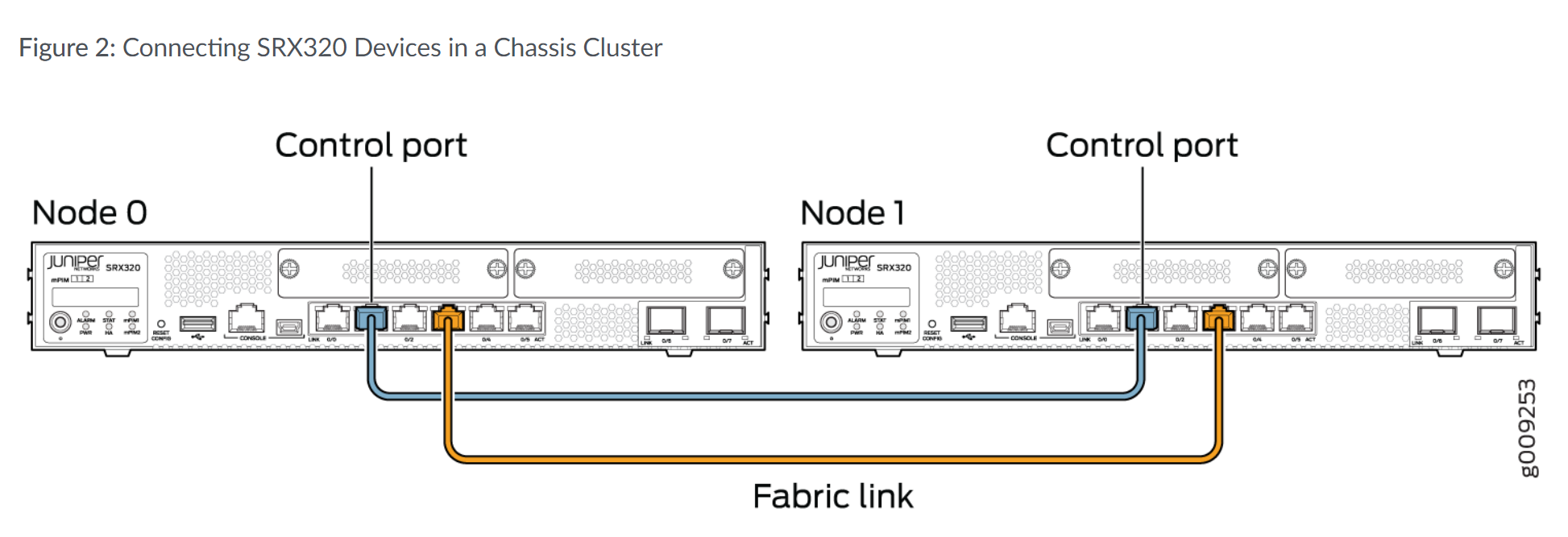
- SRX320连接node0上的ge-0/0/1和node1上的ge-3/0/1。 ge-3/0/1其实就是node1上的ge-0/0/1, 因为SRX320的Renumbering Constant 是3, 我们就称呼node1上的接口为ge-3。 SRX300上的也是一样的道理,不同的是SRX300的Renubmering Constant是1。
官方文档参考:Configuring Chassis Clustering on SRX Series Devices
建立堆叠的配置
set groups node0 system host-name node0-router
set groups node0 interfaces fxp0 unit 0 family inet address 10.1.1.1/24
set groups node1 system host-name node1-router
set groups node1 interfaces fxp0 unit 0 family inet address 10.1.1.2/24
set apply-groups “${node}”
在set groups node0和node1里面你还可以往里面加更多的配置,比如ntp服务器之类的, 配置加好了之后执行一下set apply-groups "${node}", 而后 commit就可以在两个node上一起生效。 以下是一个加项的的例子
set groups node0 system ntp server ntp.aliyun.com prefer routing-instance mgmt_junos
set groups node1 system ntp server ntp.aliyun.com prefer routing-instance mgmt_junos
set apply-groups “${node}”
commit
基础配置
-
新系统console登录用户名为root,密码为空;
-
在>模式下可以执行查看状态类的命令,比如ping, 在#下想执行的话可能需要加run空格
-
set是设置一个不存在的属性,edit是设置一个已经存在属性。 一个属性存在的时候也可以用set,但是有时候一个不存在的属性用edit是不行的
-
配置要commit才能生效
#进入CLI模式
cli
#进入配置模式
configure
#配置root密码, 不配置密码无法commit变更
set system root-authentication plain-text-password
#创建一个新管理员用户
set system login user owlhero class super-user authentication plain-text-password
#配置设备名称及域名
set system host-name mysrx
set system domain-name owl.local
#启用ssh登录
set system service ssh
#配置系统DNS
set system name-server 223.5.5.5
#配置时区
set system time-zone asia/shanghai
set system ntp server ntp.aliyun.com
# 提交
commit
配置接口地址
#配置接口地址
set interfaces ge-0/0/0 unit 0 family inet address 192.168.6.2/23
set interfaces ge-0/0/1 unit 0 family inet address 10.200.1.254/24
#配置静态路由
set routing-options static route 0.0.0.0/0 next-hop 192.168.7.254
配置VLAN
JunOS里面vlan叫irb
#配置vlan
set vlans vlan10 vlan-id 10
set vlans vlan10 l3-interface irb.10
set vlans vlan10 vlan-id 20
set vlans vlan10 l3-interface irb.20
#配置vlanif
set interfaces irb unit 10 family inet address 10.200.10.254/24
set interfaces irb unit 20 family inet address 10.200.20.254/24
#配置access类型的物理接口
set interfaces ge-0/0/3 unit 0 family ethernet-switching vlan members vlan10
#配置trunk类型的物理接口
set interfaces ge-0/0/7 unit 0 family ethernet-switching interface-mode trunk
set interfaces ge-0/0/7 unit 0 family ethernet-switching vlan members all
配置基础安全域
#配置安全域,经典的trust与untrust
set security zones security-zone untrust interface g-0/0/0
set security zones security-zone trust interface g-0/0/1
set security zones security-zone trust host-inbound-traffic system-services all
#配置默认的trust to untrust的安全策略
edit security polices from-zone trust to-zone untrust policy trust-to-untrust
set match source-address any
set match destination-address any
set match applicaiton any
set then permit
配置DHCP
#配置一个DHCP池
set access address-assignment pool p1 family inet network 10.200.10.0/24
set access address-assignment pool p1 family inet range r1 low 10.200.10.101
set access address-assignment pool p1 family inet range r1 high 10.200.10.200
set access address-assignment pool p1 family inet dhcp-attributes maximum-lease-time 2419200
set access address-assignment pool p1 family inet dhcp-attributes name-server 223.5.5.5
set access address-assignment pool p1 family inet dhcp-attributes router 10.200.10.254
#配置DHCP在vlan10接口上生效
set system services dhcp-local-server group client-dhcp interface irb.10
#在该接口所在的zone或者接口上要配置放行dhcp的系统服务
set security zones security-zone trust interfaces irb.10 host-inbound-traffic system-services dhcp
配置SNAT
#配置snat上网
set security nat source rule-set snat_rules from zone trust
set security nat source rule-set snat_rules to zone untrust
#定义snat的源地址为内网网段
set security nat source rule-set snat_rules rule default_nat match source-address 10.200.1.0/24
#定义snat的出网地址为接口地址
set security nat source rule-set snat_rules rule default_nat then source-nat interface
#至此, 在ge-0/0/1上接入的主机,配置10.200.1.0/24网段的静态地址,是可以正常上网的
端口映射
配置DNAT端口映射
#DNAT 地址和端口转换
set security nat proxy-arp interface ge-0/0/0.0 address 192.168.6.2/32
set security zones security-zone trust address-book address server-1 10.200.10.102/32
set security nat destination pool dst-nat-pool-1 address 10.200.10.102/32
set security nat destination pool dst-nat-pool-1 address port 445
set security nat destination rule-set rs1 from zone untrust
set security nat destination rule-set rs1 rule r1 match destination-address 1.1.1.1/32
set security nat destination rule-set rs1 rule r1 match destination-port 445
set security nat destination rule-set rs1 rule r1 then destination-nat pool dst-nat-pool-1
set security policies from-zone untrust to-zone trust policy server-access match source-address any
set security policies from-zone untrust to-zone trust policy server-access match destination-address server-1
set security policies from-zone untrust to-zone trust policy server-access match application any
set security policies from-zone untrust to-zone trust policy server-access then permit
配置DNAT地址映射(1对1)
#DNAT在公网IP地址充分的情况下的1对1的映射 DNAT for Single Address Translation
set security zones security-zone trust address-book address server-1 192.168.1.200/32
set security nat destination pool dst-nat-pool-1 address 192.168.1.200/32
set security nat destination rule-set rs1 from interface ge-0/0/0.0
set security nat destination rule-set rs1 rule r1 match destination-address 1.1.1.1/32
set security nat destination rule-set rs1 rule r1 then destination-nat pool dst-nat-pool-1
set security nat proxy-arp interface ge-0/0/0.0 address 203.0.113.200/32
set security policies from-zone untrust to-zone trust policy server-access match source-address any
set security policies from-zone untrust to-zone trust policy server-access match destination-address server-1
set security policies from-zone untrust to-zone trust policy server-access match application any
set security policies from-zone untrust to-zone trust policy server-access then permit
Address Book
官网文档参考:Address Books and Address Set
Address Book可以用以下方式定义对象
-
Predefined Addresses 预置的的地址:Any, Any-ipv4 , Any-ipv4
-
Network Prefixes: 203.0.113.0/24 ,这样的地址书写方式,必须是一个有效的网络地址
-
Wildcard 地址:192.168.*.11 , 192.168..0.11/255.255.0.255
-
DNS地址:对于SRX5400以上或者vSRX系统,可以用DNS来定义地址。 注意, 针对每一个DNS服务器,只能配置一个DNS来源地址, 所以在使用DNS地址簿前,要配置:set system name-server 10.5.0.1 source-address 10.4.0.1 ,强制墙的所有的DNS查询都来自一个来源地址。
SRX300支持2048个地址对象, SRX1500和SRX4100支持4096个。
Global Address Book
全局定义的地址,和Zone无关,但是启用了Global Addressbook后就不能再用zone specific address book了:
-
做NAT策略的时候, NAT策略只能引用Global Address Book里面的地址
-
做Global Policy的时候
set global address a1 203.0.113.0/24;
set global address a2 198.51.100.0/24;
set global address a3 192.0.2.0/24;
set book1 address a1 203.0.113.128/25;
Zone Address Book
在Zone下面有效的Address Book,例如:
set secrutiy zones security-zone trust address-book address a1 192.168.10.0/24
Address Set
set address a1 203.0.113.1
set address a2 203.0.113.4/30
set address a4 2001:db8::/32
set address a5 2001:db8:1::1/127
set address example dns-name www.example.com
set address-set set1 address a1
set address-set set1 address a2
set address-set set1 address a2
set address-set set2 address bbc
域间策略
set security policies from-zone trust to-zone untrust policy test-policy-1
set security policies from-zone trust to-zone untrust policy test-policy-1 match source-address address-book-1
set security policies from-zone trust to-zone untrust policy test-policy-1 destination-address address-book-10
set security policies from-zone trust to-zone untrust policy test-policy-1 application any
set security policies from-zone trust to-zone untrust policy test-policy-1 then permit
用PBR分流公网与内网流量
背景
SRX1500防火墙上有两个外网出口,
其一为SDWAN出口, SDWAN可以建立通往各分支机构的内网ipsec隧道,也可以加速海外访问;
其二为纯Internet, 主要用来让服务器对外发布使用,也可以用于纯上Internet。
历史上我们只有SDWAN的出口,上网,内网访问, 服务器发布均通过这个出口。 现在我们要增加第二个纯Internet出口,在对外发布业务服务器时可以不通过SDWAN服务商。
因为历史上我们只有一个SDWAN出口,所以路由实例也只一个默认的inet.0。 PS:还有一个mgmt instance用于带外管理。
接入第二条Inetnet线路
从墙到运营商设备增加一根线, 配置接口地址为公网地址, 新建一个Internet-CT1 域,地位和原来的untrust并列,用意都是untrust,但是不能直接利用原来的untrust,因为原来的untrust上并没有做NAT,而新建的这个Internet-CT1要做SNAT。
set interfaces reth2 redundant-ether-options redundancy-group 1
set interfaces reth2 unit 0 family inet address 3.3.3.3/24
set interfaces ge-0/0/1 gigether-options redundant-parenet reth2
set interfaces ge-7/0/1 gigether-options redundant-parenet reth2
set security zones security-zone Internet-CT1 interface reth2.0
配置Chassis 层面的心跳监控
set chassis cluster redundancy-group 1 interface-monitor ge-0/0/1 weight 255
set chassis cluster redundancy-group 1 interface-monitor ge-7/0/1 weight 255
Trust到Internet-CT1做SNAT
set security nat source rule-set snat_rules from zone trust
set security nat source rule-set snat_rules to zone Internet-CT1
set security nat source rule-set snat_rules rule snat_CT1 match source-address 0/0
set security nat source rule-set snat_rules rule snat_CT1 then source-nat interface
新增Routing Instance
新增加的纯Internet出口我们增加一个独立的Routing Instance ,命名为ChinaTelecom1,类型是转发。 路由实例的默认网关指向新接的公网接口, 配置到各分支机构内网地址的流量仍然走SDWAN。
官方论坛三ISP配置参考 ,在这个例子里面还有一个增加static route的用法是用 qualified-next-hop 1+ preference 的配置,在一个路由实例下面配置多个默认网关,然后用preference来区别,这样当最高级的线路断的时候,可以走第二条线路
set routing-instances ChinaTelecom1 instance-type forwarding
set routing-instances ChinaTelecom1 routing-options static route 0/0 next-hop 3.3.3.3
set routing-instances ChinaTelecom1 routing-options static route 10.24.0.0/16 next-hop 192.168.254.1
Routing Policy Prefix List
配置RIB和Filter的时候,可以事先把需要打包在一起的地址写到Prefix List里面,然后再引用
show policy-options
prefix-list client-to-Internet-CT2 {
172.16.1.16/28;
172.16.1.32/28;
172.16.1.48/28;
172.16.1.64/28;
172.16.2.16/28;
172.16.2.32/28;
172.16.2.48/28;
172.16.2.64/28;
172.16.3.16/28;
172.16.3.32/28;
172.16.3.48/28;
172.16.3.64/28;
}
配置Firewall Filter
从核心到墙也只有一根线,因为原来也只有一个通路,所有的流量都从这根线由核心到墙上,为了区分从核心到墙的流量,需要配置一个Firewall Filter, 把从这根线过来的流量以源地址的方式分出来,扔到新的RI-Internet-CT1路由实例。此Filter要应用于从核心过来的那根线的接口上。
如果从LAN到墙是多物理线路,则可以配置多个filter。 我们的环境是一根线,所以就要在一个filter下面写多个term。
set firewall filter family inet filter filter-to-ISPs term 1 from source-address 192.168.20.0/24
set firewall filter family inet filter filter-to-ISPs term 1 then routing-instance ChinaTelecom1
set firewall filter family inet filter filter-to-ISPs term 2 from source-address 192.168.30.0/24
set firewall filter family inet filter filter-to-ISPs term 2 then routing-instance ChinaTelecom2
set firewall filter family inet filter filter-to-ISPs term 99 then accept
配置RIB
配置主路由导入副路由
把默认路由表也导入新的路由实例, 关于rib, 好困惑, 这里有个文档解释了很多;默认情况下, rib-import只会导入direct的路由,如果要共享ospf,参见下一点
#这里这个rib-group的名字随便起, 在routing-options,针对于种协议只能有一个rib-group
set routing-options interface-routes rib-group inet RG-DEFAULT-TO-VRs
#inet.0是默认的路由表, ChinaTelecom1.inet.0是对应的新路由实例的路由表, 按顺序写,第一个inet.0就是源, 后面写的就是复制到的目标
#ChinaTelecom1.inet.0中的ChinaTelecom1必须是一个路由实例的名字。
set routing-options rig-groups RG-DEFAULT-TO-VRs import-rib inet.0
set routing-options rig-groups RG-DEFAULT-TO-VRs import-rib ChinaTelecom1.inet.0
# 如果有更多的出口,可以接下去
set routing-options rig-groups RG-DEFAULT-TO-VRs import-rib ChinaTelecom2.inet.0
配置主路由复制ospf到副路由表
如果主路由表中有OSPF的信息,而且这些OSPF的信息要复制到别的VR, 如果信息很少,你可以在别的VR中手动加入静态路由。 全部都要或者大量需要的话,需要配置rib-group到ospf协议里, 再通过policy去过滤路由导入。
set protocols ospf rib-groups inet RG-DEFAULT-TO-VRs
双ISP配置DNAT的注意点
把两个ISP的接口放到不同的路由实例,两个路由实例里面都要有到内网的路由
Destination NAT on Juniper SRX in a dual ISP environment: dealing with Routing Instances <- 这个哥们写了5种方法
Virtual Routing Instances(举例)
Virtual Routing and Forwarding (VRF), 允许用户把一台设备切分成逻辑上的多台设备, 每个逻辑的三层接口都只能属于一个Routing Instance。
#建立一个VRF
set routing-instances DMZ1 instance-type virtual-router
set routing-instances DMZ1 routing-options static route 0.0.0.0/0 next-hop 1.1.1.1
#绑定物理(三层)接口
set routing-instances DMZ interface reth1.0
set routing-instances DMZ2 instance-type virtual-router
set routing-instances DMZ2 instance-type virtual-router routing-options static route 0.0.0.0/0 next-hop 2.2.2.2
set routing-instances DMZ interface reth2.0
双ISP Failover(举例)
How to configure Filter Based Forwarding on SRX for a typical dual-ISP scenario
配置内外网接口
set interfaces ge-0/0/0 unit 0 family inet address 1.1.1.1/24
set interfaces ge-0/0/0 unit 0 description IPS1
set interfaces ge-0/0/1 unit 0 family inet address 2.2.2.2/24
set interfaces ge-0/0/1 unit 0 description IPS2
set security zones security-zone untrust interfaces ge-0/0/0.0
set security zones security-zone untrust interfaces ge-0/0/1.0
set security zones security-zone untrust host-inbound-traffic system-services traceroute
set security zones security-zone untrust host-inbound-traffic system-services ping
set security zones security-zone untrust host-inbound-traffic system-services rpm
set interfaces ge-0/0/2 unit 0 family inet address 192.168.100.254/24
set interfaces ge-0/0/2 unit 0 description LAN
set security zones security-zone trust interfaces ge-0/0/2.0
set security zones security-zone trust host-inbound-traffic system-services ping
set security zones security-zone trust host-inbound-traffic system-services traceroute
配置RIB
Routing Information Based Group是一种像模板一样的配置, 提供了一种方式,把某一种路由协议流入多个路由表中。 其配置格式如下 :
routing-option {
rib-groups {
<rib-group name> {
import-rib [ source-routing-table destination-routing-table1 destination-routing-table2 ......... ]
import-policy policy-name;
}
}
}
一种通常例子是把默认的ipv4路由注入一个新的RIB路由表(名称为VR-A, VR-B)中, 你可以在这个过程通过增加import-policy来增加控制的颗粒度,如果不加任何policy,就是把所有源路由表的信息复制到目标路由表,
routing-options {
rib-groups {
RG-DEFAULT-TO-VRs { # Copy prefixes from default routing instance to all virtual routers
import-rib [ inet.0 VR-A.inet.0 VR-B.inet.0 ];
import-policy PL-RG-DEFAULT-TO-VRs; # Optional route filtering policy
}
}
}
policy-options {
policy-statement PL-RG-DEFAULT-TO-VRs {
term VR-A {
from {
protocol direct;
route-filter 198.18.1.0/24 orlonger;
}
to rib VR-A.inet.0;
then accept;
}
term VR-B {
from {
protocol direct;
route-filter 198.18.2.0/24 orlonger;
}
to rib VR-B.inet.0;
then accept;
}
then reject;
}
}
#配置两个VRF
set routing-instances IPS1 instance-type forwarding
set routing-instances IPS2 instance-type forwarding
#配置两个VRF的默认路由
set routing-instances IPS1 routing-options static route 0/0 next-hop 1.1.1.1
set routing-instances IPS2 routing-options static route 0/0 next-hop 2.2.2.2
set routing-options rib-groups dual-ips import-rib inet.0
set routing-options rib-groups dual-ips import-rib IPS1.inet.0
set routing-options rib-groups dual-ips import-rib IPS2.inet.0
set routing-options interface-routes rib-group inet dual-isp
配置PBR
set firewall filter PBR term 1 from source-address 192.168.100.0/24
set firewall filter PBR term 1 then routing-instance ISP1
set firewall filter PBR term 2 from source-address 192.168.100.0/24
set firewall filter PBR term 2 then routing-instance ISP2
set firewall filter PBR term 3 then accept
set interfaces ge-0/0/2 unit 0 family inet filter input PBR
配置PBR监控
set services rpm probe ISP1RPM test Ali target address 223.5.5.5
set services rpm probe ISP1RPM test Ali probe-count 10
set services rpm probe ISP1RPM test Ali probe-interval 5
set services rpm probe ISP1RPM test Ali probe-interval 10
set services rpm probe ISP1RPM test Ali thresholds successive-loss 10
set services rpm probe ISP1RPM test Ali thresholds total-loss 5
set services rpm probe ISP1RPM test Ali destination-interface ge-0/0/0.0
set services rpm probe ISP1RPM test Ali next-hop 1.1.1.1
set services rpm probe ISP2RPM test Ali target address 223.5.5.5
set services rpm probe ISP2RPM test Ali probe-count 10
set services rpm probe ISP2RPM test Ali probe-interval 5
set services rpm probe ISP2RPM test Ali probe-interval 10
set services rpm probe ISP2RPM test Ali thresholds successive-loss 10
set services rpm probe ISP2RPM test Ali thresholds total-loss 5
set services rpm probe ISP2RPM test Ali destination-interface ge-0/0/1.0
set services rpm probe ISP2RPM test Ali next-hop 2.2.2.2
set services ip-monitoring policy ISP1Monitor match rpm-probe
set services ip-monitoring policy ISP1Monitor match rpm-probe IPS1RPM
set services ip-monitoring policy ISP1Monitor then preferred-route routing-instances ISP1 route 0/0 next-hop 1.1.1.1
set services ip-monitoring policy ISP2Monitor match rpm-probe IPS2RPM
set services ip-monitoring policy ISP2Monitor then preferred-route routing-instances ISP1 route 0/0 next-hop 2.2.2.2
set services ip-monitoring policy ISP1Monitor match rpm-probe IPS2RPM
配置3条ISP Failover(参考)
security {
nat {
source {
rule-set ISP-NAT {
from zone LAN;
to zone ISP;
rule R1 {
match {
source-address 192.168.0.0/16;
}
then {
source-nat {
interface;
}
}
}
}
}
}
policies {
from-zone LAN to-zone ISP {
policy ALLOW-ANY {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone ISP to-zone LAN {
policy ALLOW-ANY {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
}
zones {
security-zone ISP {
interfaces {
ge-0/0/0.0;
ge-0/0/1.0;
ge-0/0/2.0;
}
}
security-zone LAN {
interfaces {
ge-0/0/3.0;
ge-0/0/4.0;
ge-0/0/5.0;
}
}
}
}
interfaces {
ge-0/0/0 {
unit 0 {
family inet {
address 1.1.1.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 2.2.2.2/24;
}
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 3.3.3.3/24;
}
}
}
ge-0/0/3 {
unit 0 {
family inet {
filter {
input ISP-1;
}
address 192.168.1.1/24;
}
}
}
ge-0/0/4 {
unit 0 {
family inet {
filter {
input ISP-2;
}
address 192.168.2.1/24;
}
}
}
ge-0/0/5 {
unit 0 {
family inet {
filter {
input ISP-3;
}
address 192.168.3.1/24;
}
}
}
}
#如果用的是一根线从核心到墙,刚在一个filter下面写多个term
firewall {
family inet {
filter ISP-1 {
term t1 {
then {
routing-instance ISP-1;
}
}
}
filter ISP-2 {
term t2 {
then {
routing-instance ISP-2;
}
}
}
filter ISP-3 {
term t1 {
then {
routing-instance ISP-3;
}
}
}
}
}
routing-instances {
ISP-1 {
routing-options {
static {
route 0.0.0.0/0 {
qualified-next-hop 1.1.1.254 {
preference 6;
}
qualified-next-hop 2.2.2.254 {
preference 7;
}
qualified-next-hop 3.3.3.254 {
preference 8;
}
}
}
}
instance-type forwarding;
}
ISP-2 {
routing-options {
static {
route 0.0.0.0/0 {
qualified-next-hop 1.1.1.254 {
preference 8;
}
qualified-next-hop 2.2.2.254 {
preference 6;
}
qualified-next-hop 3.3.3.254 {
preference 7;
}
}
}
}
instance-type forwarding;
}
ISP-3 {
routing-options {
static {
route 0.0.0.0/0 {
qualified-next-hop 1.1.1.254 {
preference 7;
}
qualified-next-hop 2.2.2.254 {
preference 8;
}
qualified-next-hop 3.3.3.254 {
preference 6;
}
}
}
}
instance-type forwarding;
}
}
routing-options {
interface-routes {
rib-group inet ISP-RIB;
}
rib-groups {
ISP-RIB {
import-rib [ inet.0 ISP-1.inet.0 ISP-2.inet.0 ISP-3.inet.0 ];
}
}
}
公司环境下日常对外发布业务
变量定义
# 为了增加通用性,在下文命令中用变量名而且不是具体的值
$outzone:Internet-CT1
$public_ip:58.34.192.11
$public_port:3389
$server_port:3389
$server_ip:192.168.30.8
$server_name: test-server-1
$nat_pool:dst-nat-pool-1
$NUM:1
做DNAT池
# dnat
# 定义dnat pool, 指定该服务器地址和端口,每一台服务器每一个端口都对应着一个条目,如果有一段连续的端口要发布,在这里不要指定port;或者外网用的端口和内网的不同,则需要在这里定义内网的服务器端口
set security nat destination pool $nat_pool address $server_ip port $server_port
DNAT策略
# 定义dnat 策略,把来自公网的指定端口的访问转发到该服务器的端口,注意,这里是指定外网端口的地方。
# 一个from zone对应一个rule-set 是,一个服务器对应一条rule 1/2/3这样
# 在此指定destination-port为外网端口,可以指定一个端口,也可以指定一段端口,比如destination-port 5000 to 6000;也可以分几条命令几次写入多个端口
set security nat destination rule-set rs1 rule $NUM match destination-address $public_ip/32
set security nat destination rule-set rs1 rule $NUM match destination-port $public_port
# set security nat destination rule-set rs1 rule $NUM match destination-port $public_port1
# set security nat destination rule-set rs1 rule $NUM match destination-port $public_port1 to $public_port2
set security nat destination rule-set rs1 rule $NUM then destination-nat pool $nat_pool
set security nat destination rule-set rs1 rule $NUM description "some comments"
域间安全策略
# 安全策略
# 把需要发布的主机添加到Internet-CT1到trust的域间策略里去
set security zones security-zone trust address-book address $server_name $server_ip
# 到Internet-CT1到trust的域间策略中放行该服务器
set security policies from-zone $outzone to-zone trust polic $server_name match destination-address $server_name
set security policies from-zone $outzone to-zone trust polic $server_name match source-address any
set security policies from-zone $outzone to-zone trust policy $server_name match application any
set security policies from-zone $outzone to-zone trust policy $server_name then permit
SNAT策略
# snat
# 把需要发布的主机添加到clients-to-Internet-CT1, 以使它从.11这个接口出去
set policy-options prefix-list clients-to-Internet-CT1 $server_ip



 浙公网安备 33010602011771号
浙公网安备 33010602011771号