iscc训练赛-A记录
今天又是涨知识的日子,学了几道题,今天才发现流量包可以加密。
题目是要看小明看的是什么网站,A记录百度一下
也就是要过滤一下dns
这个下载后是一个流量包,用wireshark打开发现出错
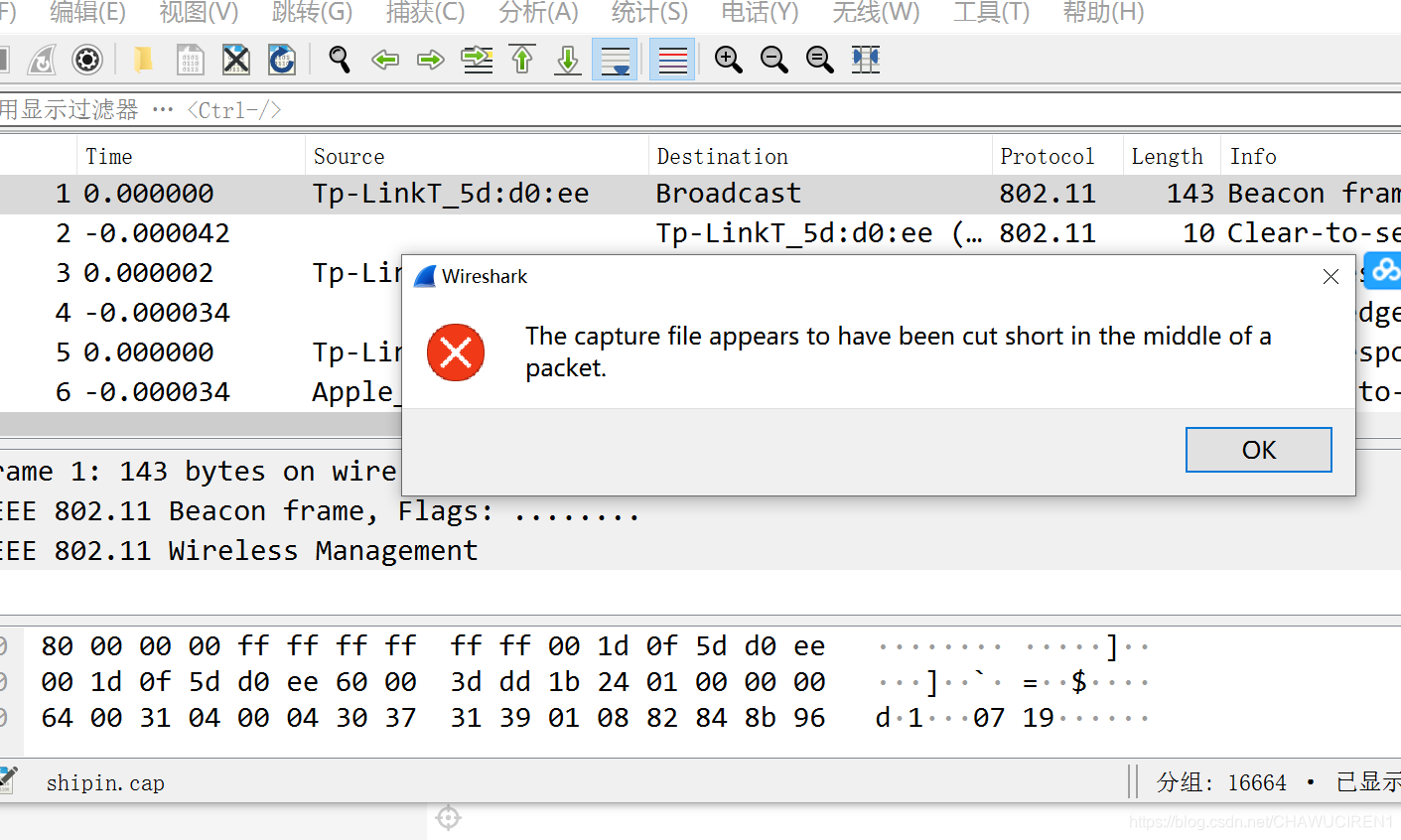
经过大佬指点知道是流量包加密,怎么办?百度一下,发现竟然是19年的原题,ok,首先要判断一下这个流量包的信息,这里有一个工具需要了解,airdecap-ng
这是kali自带的工具
root@kali:~# airdecap-ng
Airdecap-ng 1.3 - (C) 2006-2018 Thomas d'Otreppe
https://www.aircrack-ng.org
usage: airdecap-ng [options] <pcap file>
Common options:
-l : don't remove the 802.11 header
-b <bssid> : access point MAC address filter
-e <essid> : target network SSID
-o <fname> : output file for decrypted packets (default <src>-dec)
WEP specific option:
-w <key> : target network WEP key in hex
-c <fname> : output file for corrupted WEP packets (default <src>-bad)
WPA specific options:
-p <pass> : target network WPA passphrase
-k <pmk> : WPA Pairwise Master Key in hex
--help : Displays this usage screen
No file to decrypt specified.
然后我们可以使用这个工具对流量包进行信息查看
root@kali:~/桌面# airdecap-ng shipin.cap
Total number of packets read 16664
Total number of WEP data packets 0
Total number of WPA data packets 27
Number of plaintext data packets 0
Number of decrypted WEP packets 0
Number of corrupted WEP packets 0
Number of decrypted WPA packets 0
利用字典进行解码
root@kali:~/桌面# airdecap-ng shipin.cap
Total number of packets read 16664
Total number of WEP data packets 0
Total number of WPA data packets 27
[00:00:00] 16/43 keys tested (3676.47 k/s)
Time left: 0 seconds 37.21%
KEY FOUND! [ 88888888 ]
Master Key : B4 30 38 0F 24 7B 57 AC DE B5 3A 7F 2E FE 6B 45
0B 34 02 C3 89 F9 69 D5 B7 35 87 1B FB 4C EE 7F
Transient Key : 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
EAPOL HMAC : 75 19 C5 F3 3E 33 58 23 CA 4B A1 85 FB 46 C0 2A
利用这个命令对流量包进行爆破 -wg是添加字典(字典可以自己生成,也可以用github上现成的字典)
aircrack-ng shipin.cap -w zidian.txt
开始解密
airdecap-ng /root/Desktop/shipin.cap -e 0719 -p 88888888
生成未加密的流量包
然后在wireshark里面搜索dns就可以。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号