eaptls灾备 以及 tls 回调 证书制作
eaptls 中忽略server 端对client端证书校验
SSL_set_verify(conn->ssl, SSL_VERIFY_PEER, tls_verify_cb); 设置是否需要校验对端证书。
对于wpa 客户端是否要忽略校验服务端证书结果;
使用peap-mschap验证
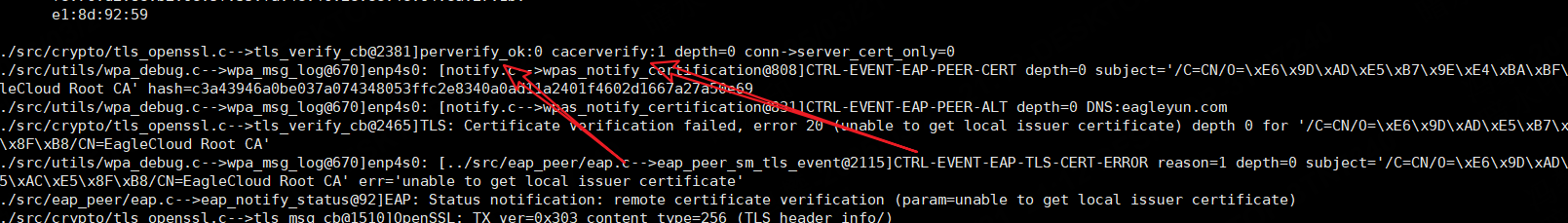
1、如果配置中配置了ca就会显示结果。
network={ 5 key_mgmt=WPA-EAP 6 eap=PEAP 7 phase1="peaplabel=0" 8 phase2="auth=MSCHAPV2" 9 anonymous_identity="term_xxxxx" 10 identity="213256454" 12 password="sdasdasdasd" 13 ca_cert="/etc/freeradius/certs/test/ca.pem" 14 }
network={ 5 key_mgmt=WPA-EAP 6 eap=PEAP 7 phase1="peaplabel=0" 8 phase2="auth=MSCHAPV2" 9 anonymous_identity="term_xxxxx" 10 identity="213256454" 12 password="sdasdasdasd" 14 }

直接显示校验成功
可知:客户端肯定会校验服务端证书,但是是否透传结果就根据配置来
对于服务端是否要校验客户端证书;
SSL_set_verify(conn->ssl, SSL_VERIFY_PEER, tls_verify_cb); 设置是否需要校验对端证书。
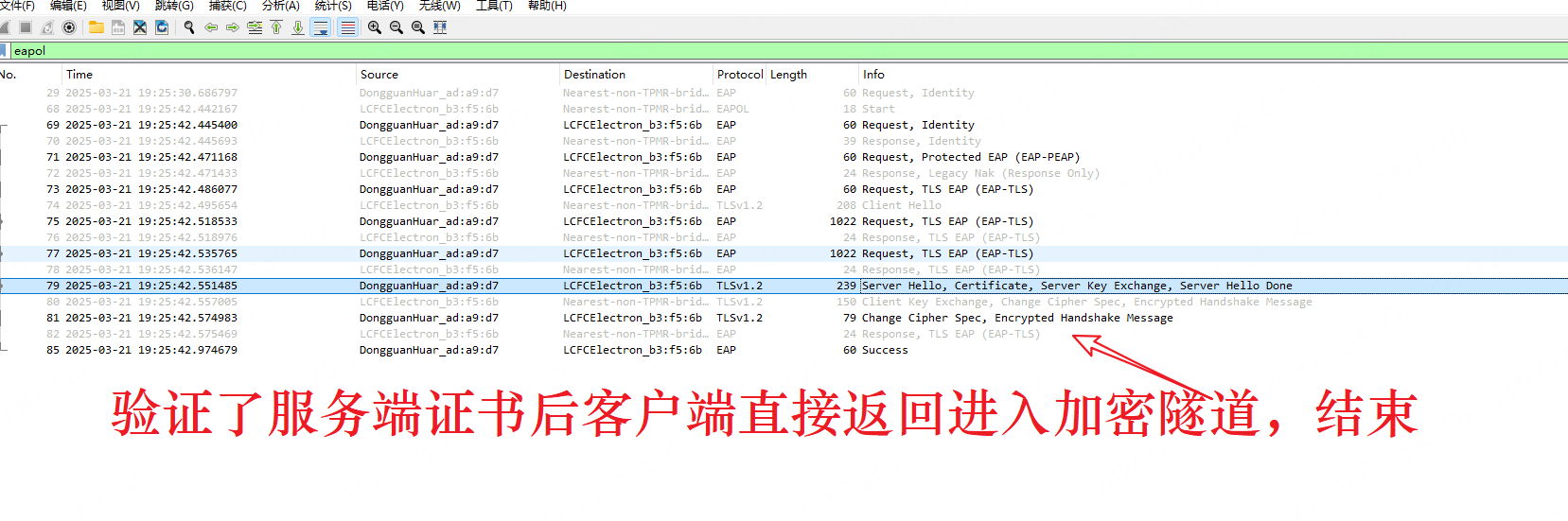

TLS 回调
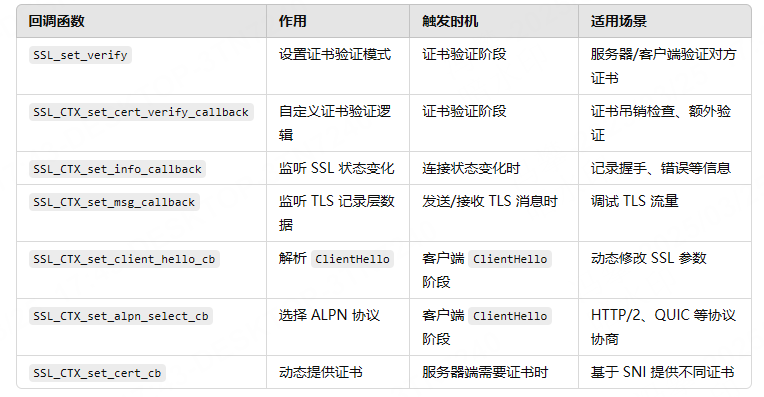
证书包含:
-
公钥
-
使用者信息(域名、公司、邮箱…)
-
有效期
-
颁发者(CA)
-
签名算法和签名值(CA 用它的私钥签的)
证书制作:
#!/bin/bash # 默认路径 ROOT_CA_DIR="./ca" SERVER_DIR="./ca/server" CLIENT_DIR="./ca/client" # 默认密码 ROOT_PASS="root123456" SERVER_PASS="123456" # 函数:生成根证书和私钥 generate_root_cert() { echo "Generating Root Certificate and Private Key..." # 创建根证书目录 mkdir -p $ROOT_CA_DIR cd $ROOT_CA_DIR # 生成根私钥 openssl genpkey -algorithm RSA -out root.key -aes256 -pass pass:$ROOT_PASS # 生成根证书(自签名) openssl req -key root.key -new -x509 -out root.crt -days 3650 -passin pass:$ROOT_PASS \ -subj "/C=US/ST=California/L=San Francisco/O=MyCompany/OU=RootCA/CN=Root CA" echo "Root Certificate (root.crt) and Private Key (root.key) generated successfully." cd - } # 函数:生成私钥和公钥 generate_server_keys() { echo "Generating Server Private Key and Public Key..." # 创建服务器目录 mkdir -p $SERVER_DIR # 生成私钥 openssl genpkey -algorithm RSA -out $SERVER_DIR/server.key -aes256 -pass pass:$SERVER_PASS # 从私钥生成公钥 openssl rsa -in $SERVER_DIR/server.key -pubout -out $SERVER_DIR/server.pub -passin pass:$SERVER_PASS echo "Server Private Key (server.key) and Public Key (server.pub) generated successfully." } # 函数:生成服务器证书并签名 generate_server_cert() { echo "Generating Server Certificate (signed by Root CA)..." # 创建服务器证书目录 mkdir -p $SERVER_DIR # 生成证书签名请求 (CSR) openssl req -key $SERVER_DIR/server.key -new -out $SERVER_DIR/server.csr -passin pass:$SERVER_PASS \ -subj "/C=US/ST=California/L=San Francisco/O=MyCompany/OU=Server/CN=server.example.com" # 使用根证书签发公钥证书 公钥证书中包含了公钥 server.pub内容 openssl x509 -req -in $SERVER_DIR/server.csr -CA $ROOT_CA_DIR/root.crt -CAkey $ROOT_CA_DIR/root.key -CAcreateserial -out $SERVER_DIR/server.crt -days 365 -passin pass:$ROOT_PASS echo "Server Public Key Certificate (server.crt) generated and signed by Root CA.\n openssl x509 -in server.crt -text -noout\n openssl rsa -pubin -in server.pub -text -noout\n" } generate_client_keys() { echo "Generating Client Private Key and Public Key..." # 创建客户端目录 mkdir -p $CLIENT_DIR # 生成客户端私钥 openssl genpkey -algorithm RSA -out $CLIENT_DIR/client.key -aes256 -pass pass:$SERVER_PASS # 从私钥生成客户端公钥 openssl rsa -in $CLIENT_DIR/client.key -pubout -out $CLIENT_DIR/client.pub -passin pass:$SERVER_PASS echo "Client Private Key (client.key) and Public Key (client.pub) generated successfully." } # 函数:执行所有操作 generate_all() { generate_root_cert generate_server_keys generate_server_cert generate_client_keys } # 处理命令行参数 while getopts "rsca" opt; do case $opt in r) generate_root_cert ;; s) generate_server_keys generate_server_cert ;; c) generate_client_keys ;; a) generate_all ;; *) echo "Usage: $0 [-r] [-s] [-c] [-a]" echo " -r Generate Root Certificate and Private Key" echo " -s Generate Server Private Key and Public Key" echo " -c Generate Server Certificate (signed by Root CA)" echo " -a Generate all of the above" exit 1 ;; esac done echo "Script execution completed. openssl x509 -in server.crt -text openssl rsa -in server.key -check"
openssl rsa -in ca/server/server.pub -pubin -text -noout #解析server 端公钥
openssl x509 -text -noout -in ca/server/server.crt # 解析sever证书 可以看到证书就是公钥+ca+签名算法和签名值(CA 用它的私钥签的)
echo "服务器密钥 (server.key, server.pub) \n客户端密钥 (client.key, client.pub)" ## #echo "Hello, this is a test message" > message.txt #openssl pkeyutl -encrypt -pubin -inkey server/server.pub -in message.txt -out encrypted_data.bin #openssl pkeyutl -decrypt -inkey server/server.key -in encrypted_data.bin -out decrypted_message.txt -passin pass:123456 #cat decrypted_message.txt openssl pkeyutl -encrypt -inkey server/server.key -in message.txt -out encrypted_data.bin -passin pass:123456 openssl pkeyutl -decrypt -pubin -inkey server/server.pub -in encrypted_data.bin -out decrypted_message.txt #echo "Hello, this is a signed message" > message.txt openssl pkeyutl -sign -inkey server/server.key -in message.txt -out signed_data.bin -passin pass:123456 openssl pkeyutl -verify -pubin -inkey server/server.pub -sigfile signed_data.bin -in message.txt openssl dgst -sha256 -binary message.txt > message_hash.bin #使用私钥签名 openssl pkeyutl -sign -inkey server/server.key -in message_hash.bin -out signed_data.bin -passin pass:123456 #使用私钥签名 #接收方验证签名 openssl dgst -sha256 -binary message.txt > received_hash.bin openssl pkeyutl -verify -pubin -inkey server/server.pub -sigfile signed_data.bin -in received_hash.bin
可以看到证书中有颁发者ca的信息:Issuer: C = US, ST = California, L = San Francisco, O = MyCompany, OU = RootCA, CN = Root CA
有申请者的身份信息:Subject: C = US, ST = California, L = San Francisco, O = MyCompany, OU = Server, CN = server.example.com
有公钥信息:Public-Key: (2048 bit)
还有:CA 用它的私钥对证书正文 (TBSCertificate) 生成的签名结果Signature Value:
openssl x509 -text -noout -in ca/server/server.crt Certificate: Data: Version: 1 (0x0) Serial Number: 2d:34:7f:c1:57:5b:e7:7a:2b:a5:57:0e:f8:30:66:f5:42:cb:19:09 Signature Algorithm: sha256WithRSAEncryption Issuer: C = US, ST = California, L = San Francisco, O = MyCompany, OU = RootCA, CN = Root CA Validity Not Before: Sep 25 07:29:53 2025 GMT Not After : Sep 25 07:29:53 2026 GMT Subject: C = US, ST = California, L = San Francisco, O = MyCompany, OU = Server, CN = server.example.com Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:8c:d9:ec:75:3d:d7:45:fc:02:75:38:35:11:eb: 63:72:2b:0a:ce:09:16:91:2f:cd:42:85:71:45:d0: 57:b6:6f:43:8a:54:11:9d:55:b4:2f:09:b7:1f:83: b7:1f:f1:e1:73:9b:2c:f8:83:74:38:21:cf:57:c5: 04:4e:c6:81:25:1f:28:5c:8f:dd:19:cf:ed:fc:8e: 6f:9d:e4:75:47:5f:ed:ac:45:61:0f:46:b6:d3:6d: e8:f5:cd:28:d4:cb:a9:cf:96:89:00:5f:73:d8:7d: 36:c3:3f:c5:a9:47:f7:21:ed:66:5b:12:83:1e:89: 9b:56:07:0e:8a:29:58:f6:33:da:38:46:eb:43:07: 5e:5d:80:16:a3:6c:1f:ca:08:62:09:d2:1d:29:f5: dd:a3:f2:b5:cf:83:00:77:4a:64:4e:aa:4f:fb:da: 69:45:99:8f:cd:5e:68:86:17:46:14:46:13:82:86: 2e:47:47:91:62:e6:6e:89:66:50:6e:ac:87:45:9d: 99:25:9a:19:80:32:14:22:e1:af:fe:23:9c:52:59: f5:a6:c6:9d:ca:16:e9:6e:be:72:68:80:32:5a:28: b1:f0:7c:d2:78:ad:fe:c8:2a:32:ff:cf:f6:bd:23: 53:82:8a:81:38:c9:d8:76:a1:27:6d:62:3c:5b:ad: b6:73 Exponent: 65537 (0x10001) Signature Algorithm: sha256WithRSAEncryption Signature Value: 48:d1:64:8b:63:a7:28:12:90:ab:af:a7:73:f9:71:fb:db:28: 48:4f:44:b0:ce:96:dc:37:d2:dd:63:44:d5:1b:36:f8:8f:67: 71:7a:66:3e:5b:5c:31:0e:f2:4f:ae:38:66:94:71:30:18:62: f8:d7:2f:01:e3:83:fa:20:74:94:31:15:19:00:cb:d8:ef:66: 05:6d:23:4a:74:c7:63:94:be:e5:61:28:15:c5:24:a1:43:ce: 11:a9:53:9c:f1:d6:1f:1d:5a:46:c7:ab:74:81:9e:11:0a:1c: dd:c6:d6:3d:80:79:3a:b4:e3:8a:74:8e:da:36:dd:8a:5c:83: 28:fd:16:8f:54:99:28:f7:af:f5:2e:94:81:cb:03:a2:df:f0: df:66:cb:cf:a2:94:37:2f:19:80:a6:3b:12:fe:05:f8:00:b4: 34:44:a6:9a:a4:c0:06:16:0e:b6:58:a4:7c:ad:0e:be:7c:98: ad:90:8a:f4:82:82:46:c9:1f:9f:f1:65:c3:4a:cf:83:9a:e4: 22:1e:50:37:1f:d7:0f:94:ac:d9:b0:ca:8f:c0:ba:4d:d4:42: b7:a5:16:c4:bc:c7:6c:31:d6:76:2b:f2:b4:46:2d:c1:70:fb: 91:54:a9:62:aa:d8:51:5a:0b:a9:35:29:56:45:48:4d:07:90: c2:89:41:9f openssl rsa -in ca/server/server.pub -pubin -text -noout Public-Key: (2048 bit) Modulus: 00:8c:d9:ec:75:3d:d7:45:fc:02:75:38:35:11:eb: 63:72:2b:0a:ce:09:16:91:2f:cd:42:85:71:45:d0: 57:b6:6f:43:8a:54:11:9d:55:b4:2f:09:b7:1f:83: b7:1f:f1:e1:73:9b:2c:f8:83:74:38:21:cf:57:c5: 04:4e:c6:81:25:1f:28:5c:8f:dd:19:cf:ed:fc:8e: 6f:9d:e4:75:47:5f:ed:ac:45:61:0f:46:b6:d3:6d: e8:f5:cd:28:d4:cb:a9:cf:96:89:00:5f:73:d8:7d: 36:c3:3f:c5:a9:47:f7:21:ed:66:5b:12:83:1e:89: 9b:56:07:0e:8a:29:58:f6:33:da:38:46:eb:43:07: 5e:5d:80:16:a3:6c:1f:ca:08:62:09:d2:1d:29:f5: dd:a3:f2:b5:cf:83:00:77:4a:64:4e:aa:4f:fb:da: 69:45:99:8f:cd:5e:68:86:17:46:14:46:13:82:86: 2e:47:47:91:62:e6:6e:89:66:50:6e:ac:87:45:9d: 99:25:9a:19:80:32:14:22:e1:af:fe:23:9c:52:59: f5:a6:c6:9d:ca:16:e9:6e:be:72:68:80:32:5a:28: b1:f0:7c:d2:78:ad:fe:c8:2a:32:ff:cf:f6:bd:23: 53:82:8a:81:38:c9:d8:76:a1:27:6d:62:3c:5b:ad: b6:73 Exponent: 65537 (0x10001)
http代理服务器(3-4-7层代理)-网络事件库公共组件、内核kernel驱动 摄像头驱动 tcpip网络协议栈、netfilter、bridge 好像看过!!!!
但行好事 莫问前程
--身高体重180的胖子



 浙公网安备 33010602011771号
浙公网安备 33010602011771号