云原生学习作业5
一,实现基于velero对etcd的单独namespace的备份和恢复
1,向运行minio
2,安装velero
创建好velero-auth.txt文件和velero-system命名空间
velero --kubeconfig /root/.kube/config \ install \ --provider aws \ --plugins velero/velero-plugin-for-aws:v1.3.1 \ --bucket velerodata \ --secret-file /data/velero/velero-auth.txt \ --use-volume-snapshots=false \ --namespace velero-system \ --backup-location-config region=minio,s3ForcePathStyle="true",s3Url=http://172.27.16.5:9000
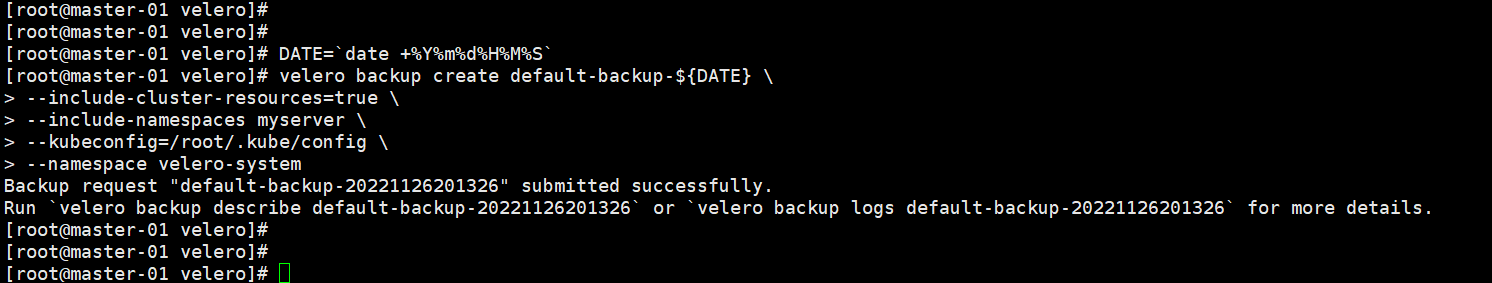
执行备份:
DATE=`date +%Y%m%d%H%M%S` velero backup create default-backup-${DATE} \ --include-cluster-resources=true \ --include-namespaces myserver \ #备份myserver命名空间下资源 --kubeconfig=/root/.kube/config \ --namespace velero-system
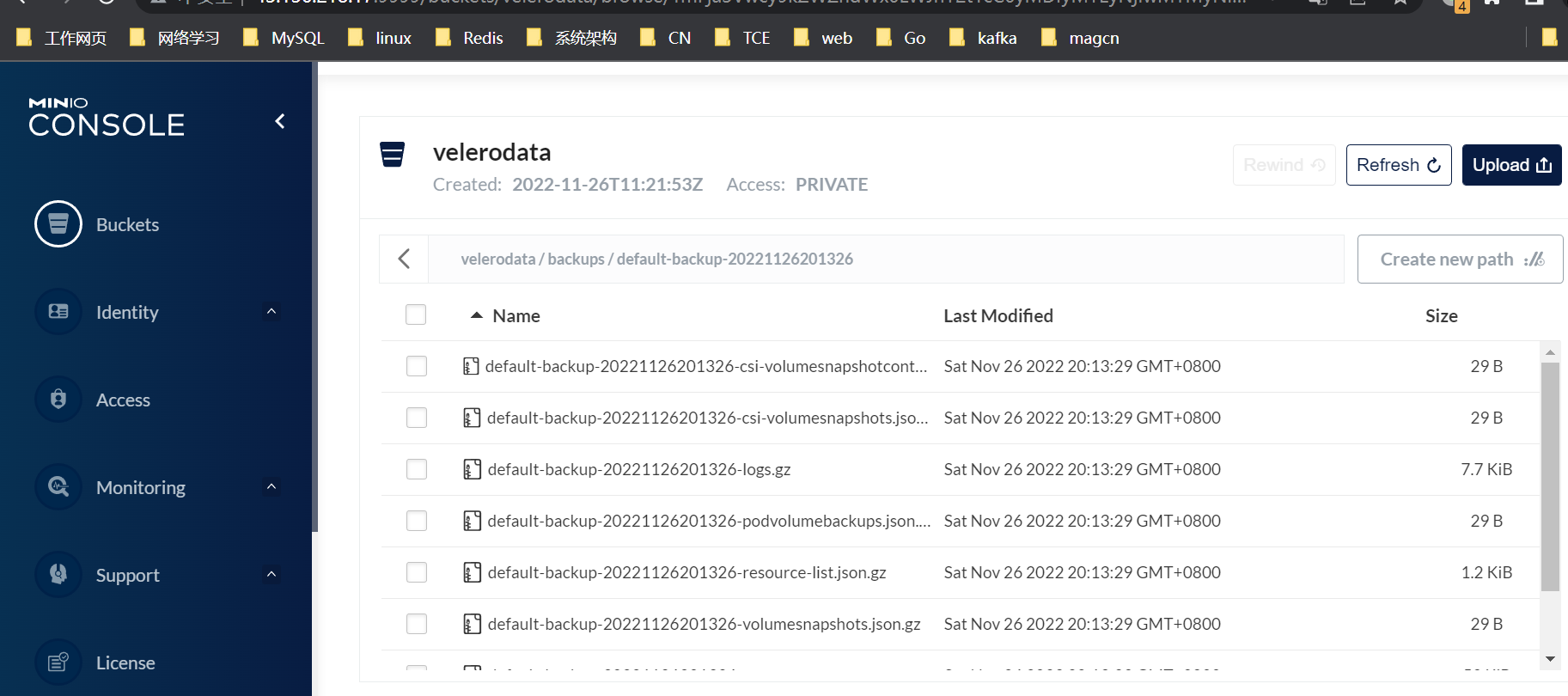
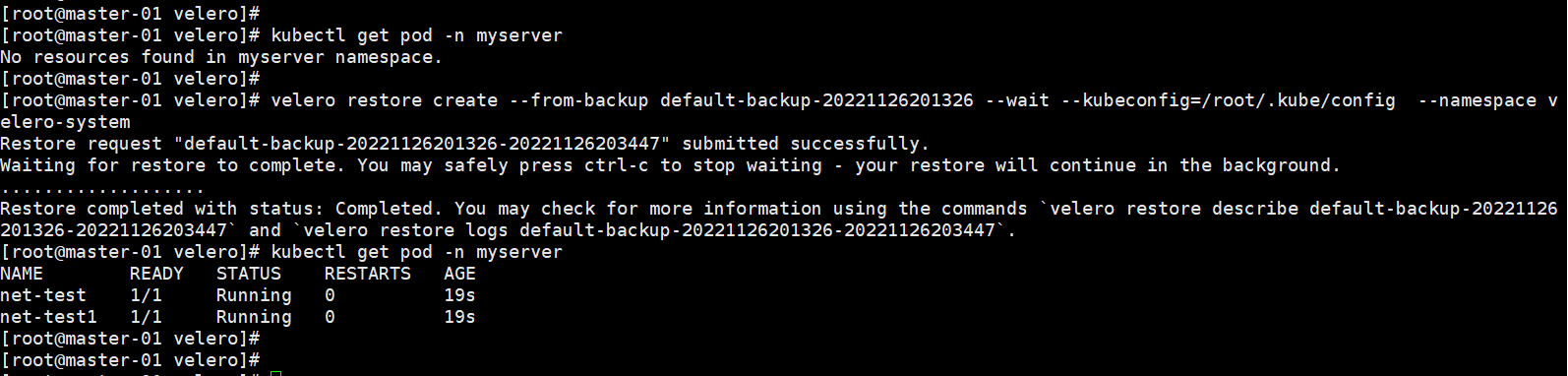
恢复:
先删除mysever下的两个pod,执行恢复
二,掌握k8s中常见的资源对象的使用:
1,创建deployment
apiVersion: apps/v1 kind: Deployment metadata: name: nginx-deployment labels: app: nginx
namespace: myserver spec: replicas: 3 selector: matchLabels: app: nginx template: metadata: labels: app: nginx spec: containers: - name: nginx image: nginx:latest ports: - containerPort: 80
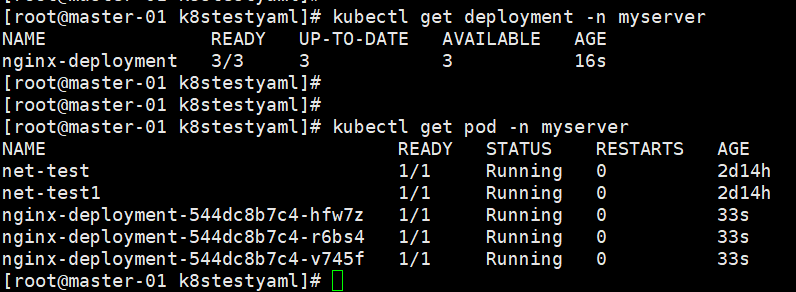
2, 创建service
apiVersion: v1 kind: Service metadata: name: my-service namespace: myserver spec: type: NodePort selector: app: nginx ports: - name: http protocol: TCP port: 80 targetPort: 80 nodePort: 30001
查看绑定后端pod:
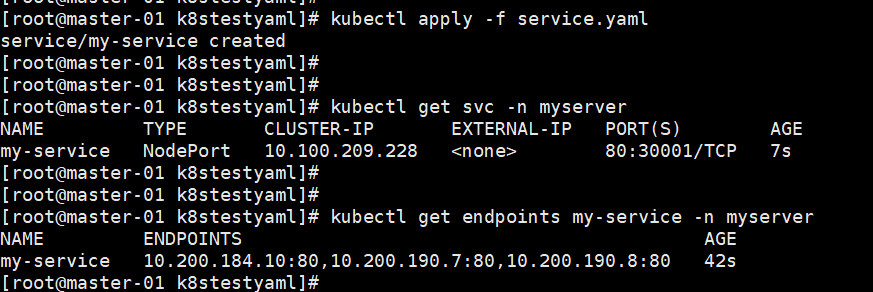
3,创建configmap
apiVersion: v1 kind: ConfigMap metadata: name: nginx-config namespace: myserver data: default: | server { listen 80; server_name www.magcn.com; listen 443 ssl; ssl_certificate /etc/nginx/conf.d/certs/tls.crt; ssl_certificate_key /etc/nginx/conf.d/certs/tls.key; location / { root /usr/share/nginx/html; index index.html; if ($scheme = http ) { rewrite / https://www.magcn.com permanent; } if (!-e $request_filename) { rewrite ^/(.*) /index.html last; } } }
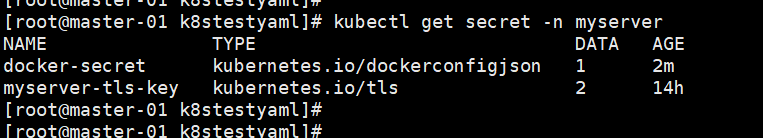
4,创建secret:(通过dockerconfig创建)
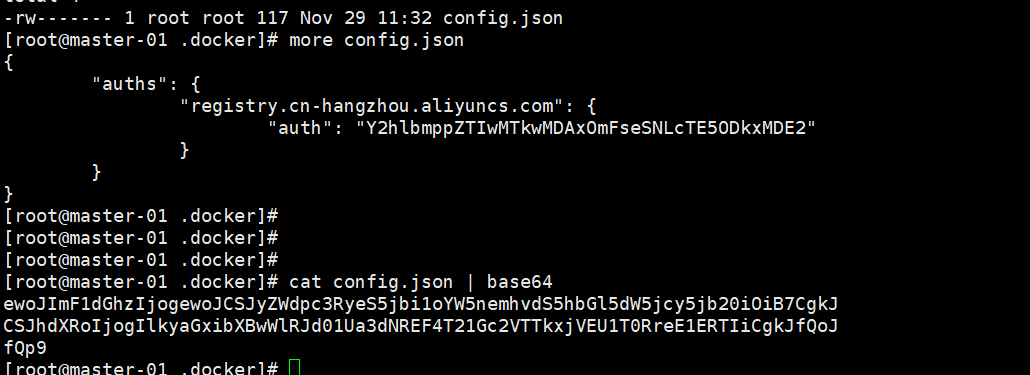
docker-secret.yaml
apiVersion: v1
kind: Secret
metadata:
name: docker-secret
namespace: myserver
type: kubernetes.io/dockerconfigjson
data:
.dockerconfigjson: ewoJImF1dGhzIjogewoJCSJyZWdpc3RyeS5jbi1oYW5nemhvdS5hbGl5dW5jcy5jb20iOiB7CgkJCSJhdXRoIjogIlkyaGxibXBwWlRJd01Ua3dNREF4T21Gc2VT
TkxjVEU1T0RreE1ERTIiCgkJfQoJfQp9
三, 掌握基于NFS实现pod数据持久化的使用方式,测试emptyDir、hostPath的使用
1,在mater-03节点安装nfs服务,目录为
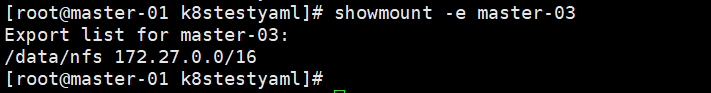
apiVersion: v1 kind: Pod metadata: name: nfs-test namespace: myserver spec: containers: - image: registry.cn-hangzhou.aliyuncs.com/chenjie2022/nginx:latest name: test-container volumeMounts: - mountPath: /my-nfs-data name: nfs-volume volumes: - name: nfs-volume nfs: server: 172.27.16.17 path: /data/nfs imagePullSecrets: - name: docker-secret
2,测试emptyDir
apiVersion: v1
kind: Pod
metadata:
name: empty-test
namespace: myserver
spec:
containers:
- image: registry.cn-hangzhou.aliyuncs.com/chenjie2022/nginx:latest
name: empty-container
volumeMounts:
- mountPath: /my-empty-data
name: empty-volume
volumes:
- name: empty-volume
emptyDir: {}
imagePullSecrets:
- name: docker-secret
3,测试hostPath
apiVersion: v1
kind: Pod
metadata:
name: hostpath-test
namespace: myserver
spec:
containers:
- image: registry.cn-hangzhou.aliyuncs.com/chenjie2022/nginx:latest
name: hostpath-container
volumeMounts:
- mountPath: /my-hostpath-data
name: hostpath-volume
volumes:
- name: hostpath-volume
hostPath:
path: /data
imagePullSecrets:
- name: docker-secret
四,实现基于Secret实现nginx的tls认证、并实现私有仓库镜像的下载认证
1,实现基于Secret实现nginx的tls认证
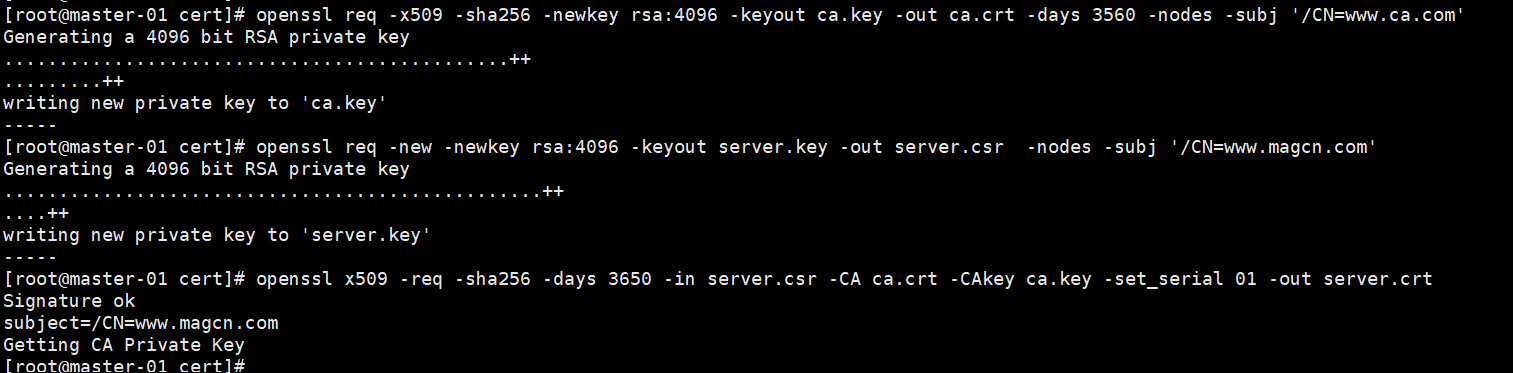
1),创建证书
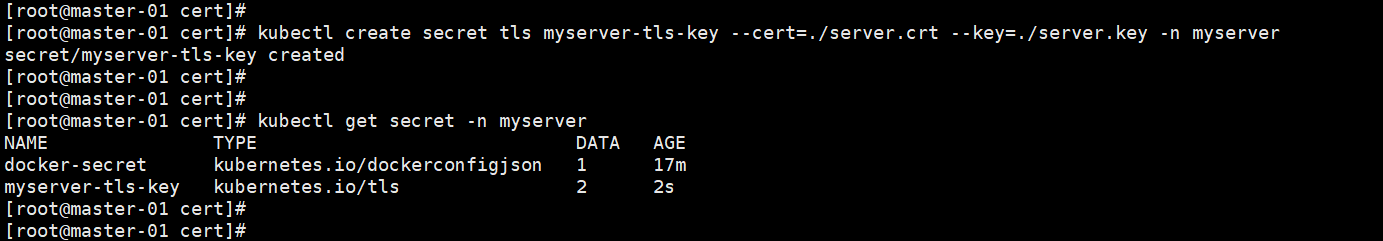
2),创建secret
3),deployment-nginx-tls.yaml
apiVersion: v1 kind: ConfigMap metadata: name: nginx-config namespace: myserver data: default: | server { listen 80; server_name www.magcn.com; listen 443 ssl; ssl_certificate /etc/nginx/conf.d/certs/tls.crt; ssl_certificate_key /etc/nginx/conf.d/certs/tls.key; location / { root /usr/share/nginx/html; index index.html; if ($scheme = http ) { rewrite / https://www.magcn.com permanent; } if (!-e $request_filename) { rewrite ^/(.*) /index.html last; } } } --- apiVersion: apps/v1 kind: Deployment metadata: name: deploymen-nginx-tls namespace: myserver spec: replicas: 1 selector: matchLabels: app: nginx template: metadata: labels: app: nginx spec: containers: - name: nginx image: registry.cn-hangzhou.aliyuncs.com/chenjie2022/nginx:latest ports: - containerPort: 80 volumeMounts: - name: nginx-config mountPath: /etc/nginx/conf.d/myserver - name: myserver-tls-key mountPath: /etc/nginx/conf.d/certs volumes: - name: nginx-config configMap: name: nginx-config items: - key: default path: mysite.conf - name: myserver-tls-key secret: secretName: myserver-tls-key imagePullSecrets: - name: docker-secret --- apiVersion: v1 kind: Service metadata: name: service-nginx namespace: myserver spec: type: NodePort ports: - name: http port: 80 targetPort: 80 nodePort: 30080 protocol: TCP - name: https port: 443 targetPort: 443 nodePort: 30443 protocol: TCP selector: app: nginx
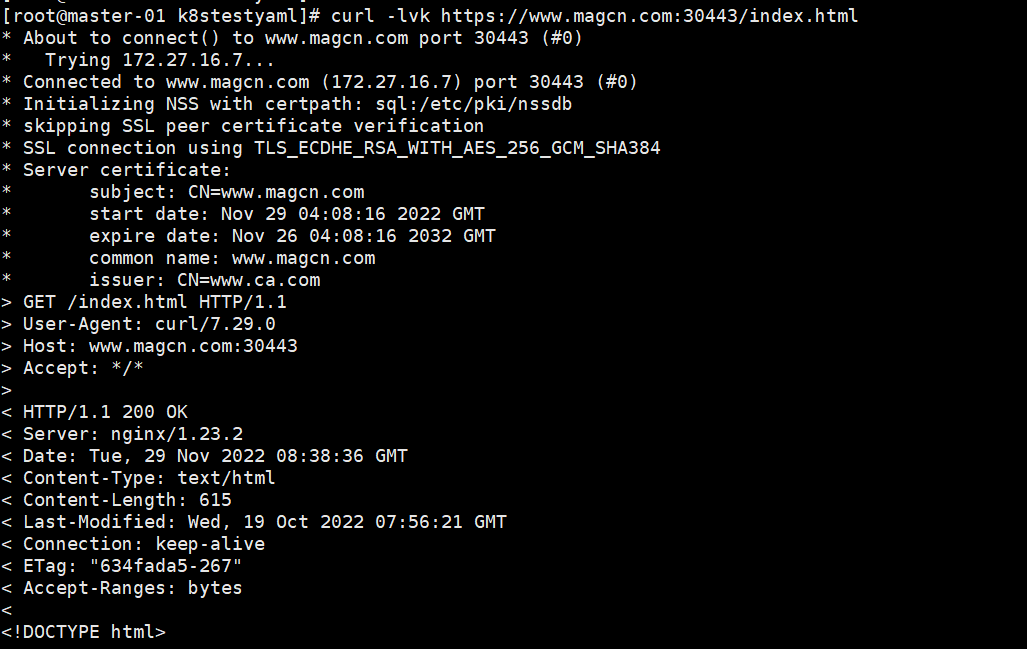
修改pod 内部nginx.conf 文件、重启nginx后,访问https端口
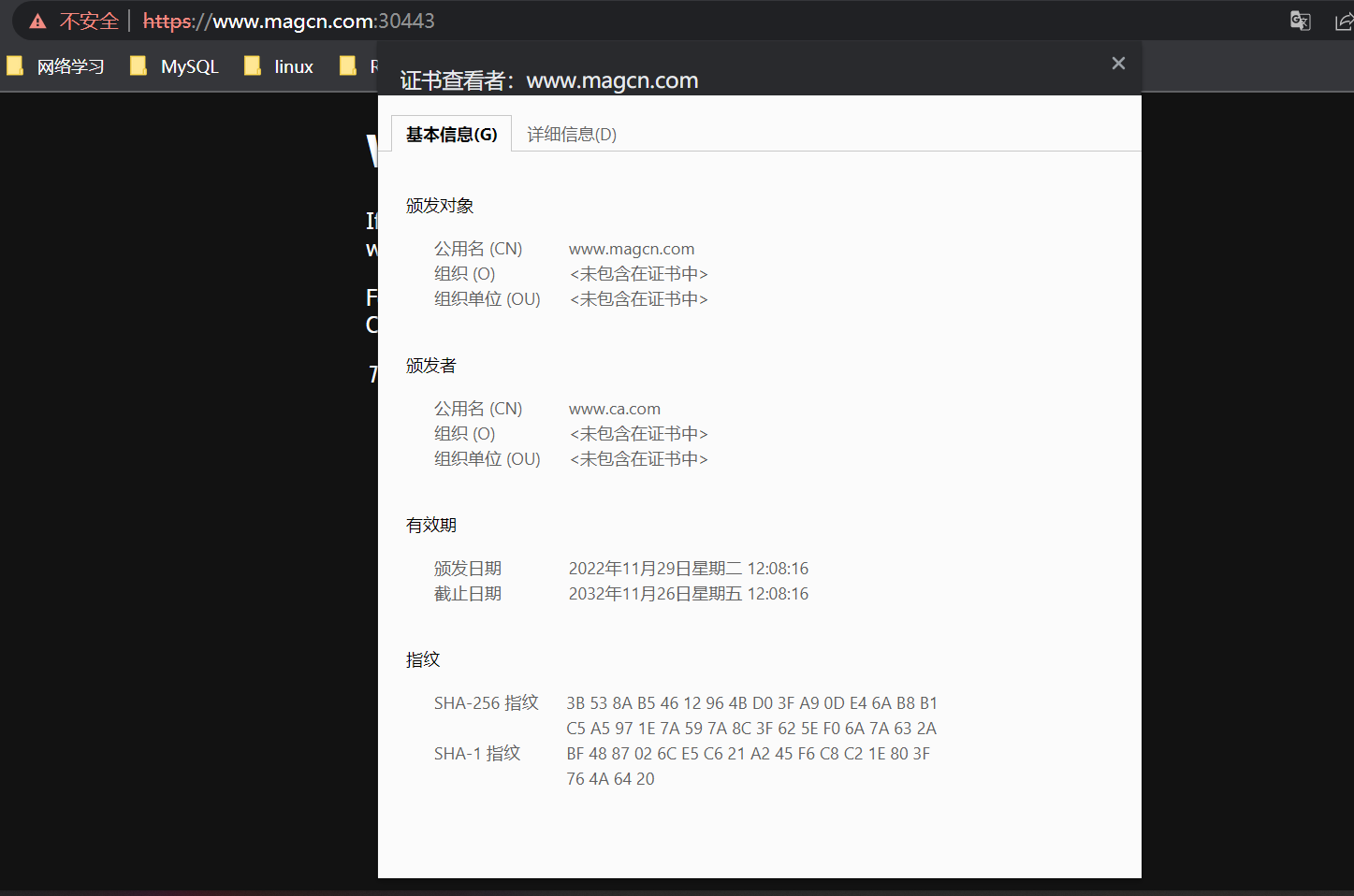
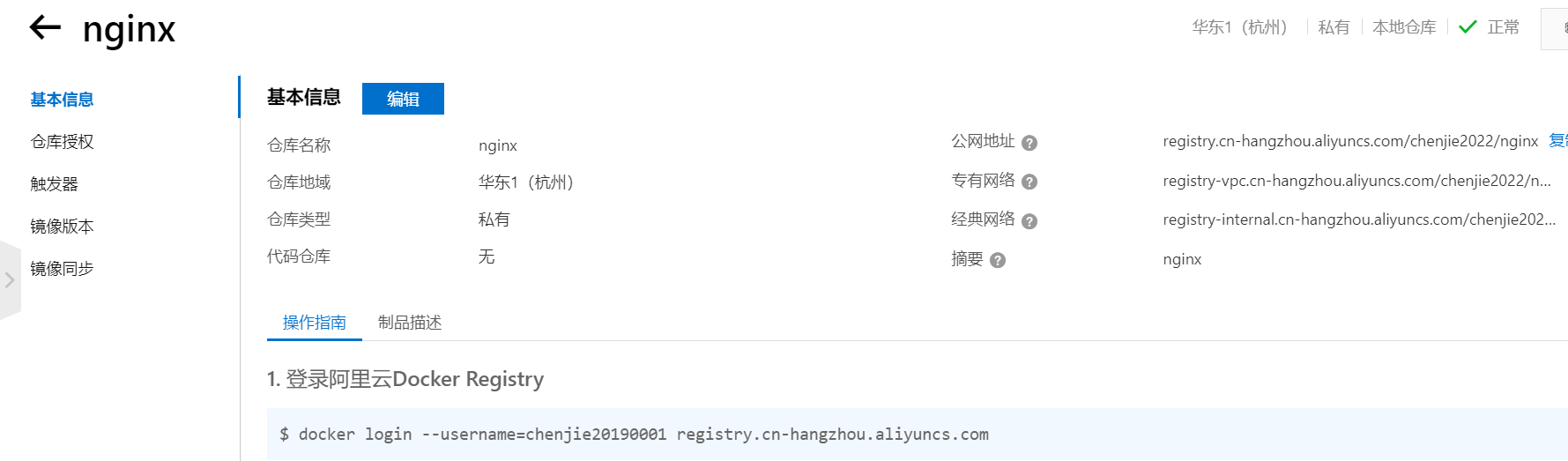
2,私有仓库镜像的下载认证
先登录仓库,推送镜像
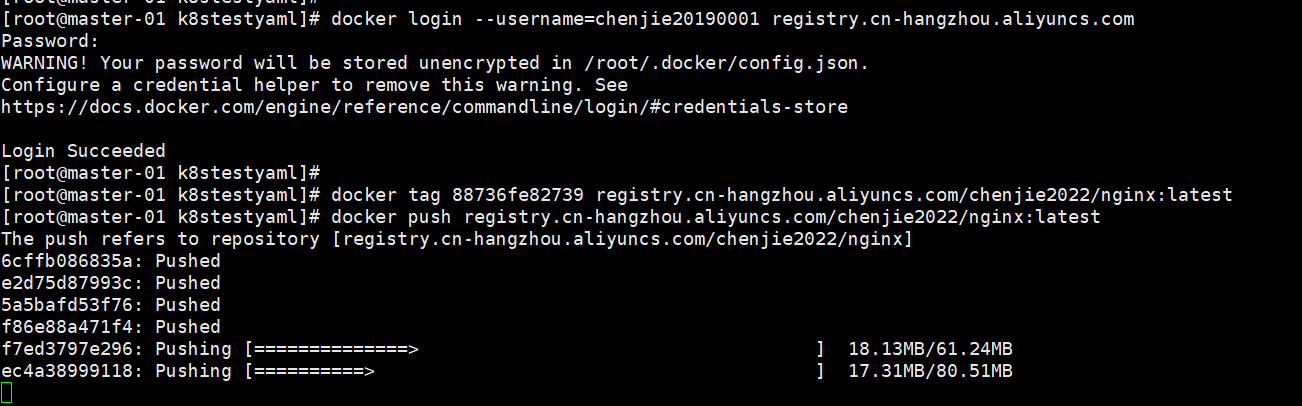
创建secrets
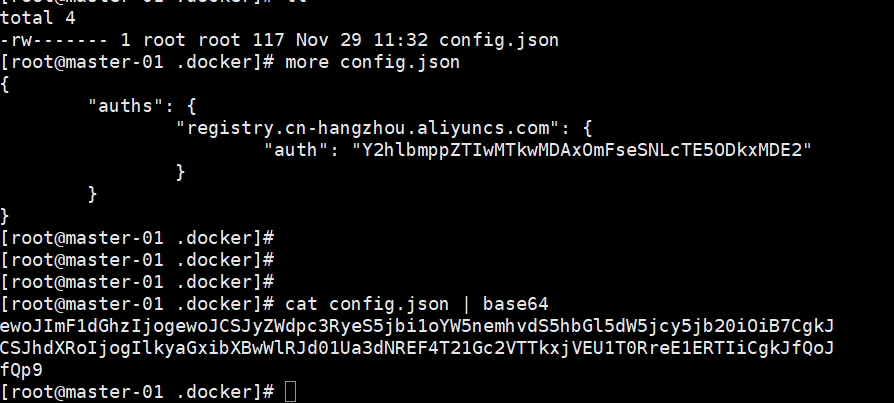
docker-secret.yaml
apiVersion: v1
kind: Secret
metadata:
name: docker-secret
namespace: myserver
type: kubernetes.io/dockerconfigjson
data:
.dockerconfigjson: ewoJImF1dGhzIjogewoJCSJyZWdpc3RyeS5jbi1oYW5nemhvdS5hbGl5dW5jcy5jb20iOiB7CgkJCSJhdXRoIjogIlkyaGxibXBwWlRJd01Ua3dNREF4T21Gc2VT
TkxjVEU1T0RreE1ERTIiCgkJfQoJ
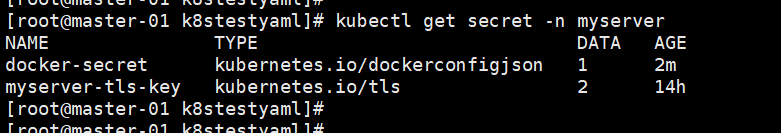
使用secret拉取私有镜像
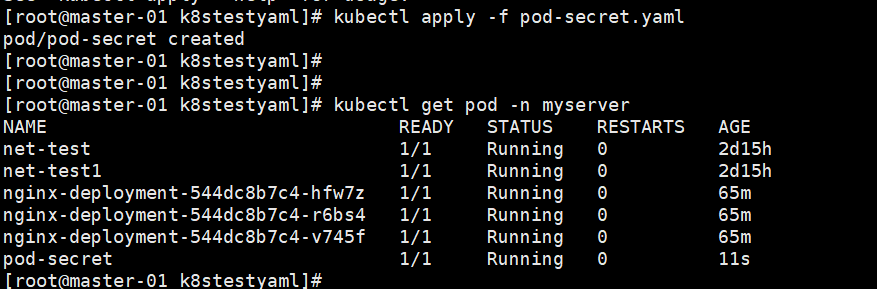
pod-secret.yaml
apiVersion: v1
kind: Pod
metadata:
name: pod-secret
namespace: myserver
spec:
containers:
- name: private-pod
image: registry.cn-hangzhou.aliyuncs.com/chenjie2022/nginx:latest
imagePullSecrets:
- name: docker-secret



 浙公网安备 33010602011771号
浙公网安备 33010602011771号