Kubernetes-1.16部署之二 K8s-dashboard
一、修改Dashboard配置文件
1)在master下载Dashboard服务(下载使用dashboard yaml程序时注意是否支持当前使用的kubernetes版本)
# mkdir -p /opt/kubernetes/dashboard/{ssl,metrics,yaml} # curl -o /opt/kubernetes/dashboard/yaml/dashboard-v2.0.0-beta8.yaml https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.0-beta8/aio/deploy/recommended.yaml
2)修改dashboard-v2.0.0-beta8.yaml文件内容
# vi /opt/kubernetes/dashboard/yaml/dashboard-v2.0.0-beta8.yaml 将部分 spec: ports: - port: 443 targetPort: 8443 selector: k8s-app: kubernetes-dashboard 改为 spec: type: NodePort ports: - port: 443 targetPort: 8443 nodePort: 31944 selector: k8s-app: kubernetes-dashboard 把 kubernetes-dashboard-certs Secret 部分注释掉 #apiVersion: v1 #kind: Secret #metadata: # labels: # k8s-app: kubernetes-dashboard # name: kubernetes-dashboard-certs # namespace: kubernetes-dashboard #type: Opaque
二、部署kubernetes dashboard service
# kubectl apply -f dashboard-v2.0.0-beta8.yaml namespace/kubernetes-dashboard created serviceaccount/kubernetes-dashboard created service/kubernetes-dashboard created secret/kubernetes-dashboard-csrf created secret/kubernetes-dashboard-key-holder created configmap/kubernetes-dashboard-settings created role.rbac.authorization.k8s.io/kubernetes-dashboard created clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created deployment.apps/kubernetes-dashboard created service/dashboard-metrics-scraper created deployment.apps/dashboard-metrics-scraper created
三、生成dashboard管理员证书
1)签发证书
# cd /opt/kubernetes/dashboard/ssl # openssl req -nodes -newkey rsa:2048 -keyout dashboard.key -out dashboard.csr -subj '/CN=kubernetes-dashboard' # openssl x509 -req -sha256 -days 36500 -in dashboard.csr -signkey dashboard.key -out dashboard.crt # ls dashboard.crt dashboard.csr dashboard.key
2)导入kubernetes dashboard证书
# kubectl create secret generic kubernetes-dashboard-certs --from-file=dashboard.key --from-file=dashboard.crt -n kubernetes-dashboard
四、创建登录用户
# cd /opt/kubernetes/dashboard/yaml # vi dashboard-admin.yaml apiVersion: v1 kind: ServiceAccount metadata: name: admin-user namespace: kube-system --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: admin-user roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-admin subjects: - kind: ServiceAccount name: admin-user namespace: kube-system # kubectl apply -f dashboard-admin.yaml
查看service状态
# kubectl get svc -o wide --all-namespaces NAMESPACE NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE SELECTOR default kubernetes ClusterIP 10.1.0.1 <none> 443/TCP 2d13h <none> kube-system kube-dns ClusterIP 10.1.0.2 <none> 53/UDP,53/TCP,9153/TCP 22h k8s-app=kube-dns kubernetes-dashboard dashboard-metrics-scraper ClusterIP 10.1.178.235 <none> 8000/TCP 24m k8s-app=dashboard-metrics-scraper kubernetes-dashboard kubernetes-dashboard NodePort 10.1.253.141 <none> 443:31944/TCP 24m k8s-app=kubernetes-dashboard # kubectl get service -n kubernetes-dashboard -o wide NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE SELECTOR dashboard-metrics-scraper ClusterIP 10.1.178.235 <none> 8000/TCP 24m k8s-app=dashboard-metrics-scraper kubernetes-dashboard NodePort 10.1.253.141 <none> 443:31944/TCP 25m k8s-app=kubernetes-dashboard # kubectl get pods -A -o wide NAMESPACE NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES default busybox-555c656b9-gwsbn 1/1 Running 0 71m 10.2.196.144 work-node01 <none> <none> kube-system calico-kube-controllers-7c4fb94b96-7qg9d 1/1 Running 0 71m 192.168.168.3 work-node01 <none> <none> kube-system calico-node-8kr9t 1/1 Running 5 11h 192.168.168.3 work-node01 <none> <none> kube-system calico-node-k4vg7 1/1 Running 5 11h 192.168.168.4 work-node02 <none> <none> kube-system coredns-788bb5bd8d-82rsl 1/1 Running 0 71m 10.2.196.146 work-node01 <none> <none> kubernetes-dashboard dashboard-metrics-scraper-76585494d8-9c6dd 1/1 Running 0 29m 10.2.140.66 work-node01 <none> <none> kubernetes-dashboard kubernetes-dashboard-5996555fd8-cmk8h 1/1 Running 0 29m 10.2.140.65 work-node01 <none> <none> 可确定访问kubernetes dashboard使用work-node01节点的ip # kubectl get secret -n kubernetes-dashboard NAME TYPE DATA AGE dashboard-admin-token-thtbz kubernetes.io/service-account-token 3 20m default-token-974zq kubernetes.io/service-account-token 3 22m kubernetes-dashboard-certs Opaque 2 21m kubernetes-dashboard-csrf Opaque 1 22m kubernetes-dashboard-key-holder Opaque 2 22m kubernetes-dashboard-token-bshn6 kubernetes.io/service-account-token 3 22m
注:PORT(S)值中31944为dashboard访问端口
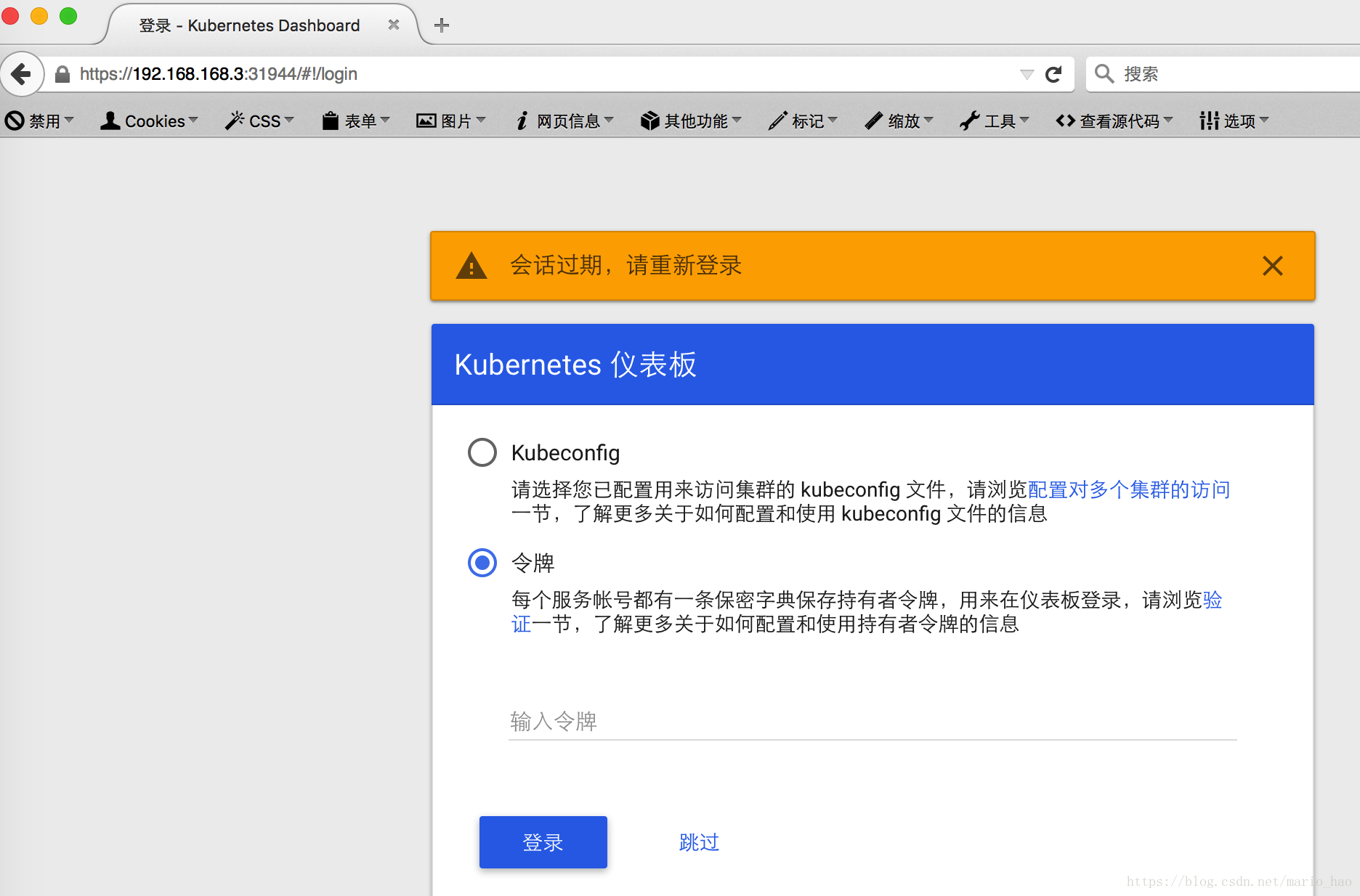
五、使用node节点IP访问dashboard(http://%nodeIP%:31944),选择“令牌”登录方式后先不要点击“确定”
1)在master上查询token令牌
# kubectl -n kube-system describe secret $(kubectl -n kube-system get secret | grep admin-user | awk '{print $1}') Name: admin-user-token-jm46g Namespace: kube-system Labels: <none> Annotations: kubernetes.io/service-account.name: admin-user kubernetes.io/service-account.uid: be379339-6188-47d9-9768-3f5eaec20ac9 Type: kubernetes.io/service-account-token Data ==== ca.crt: 1359 bytes namespace: 11 bytes token: eyJhbGciOiJSUzI1NiIsImtpZCI6IjZqVVluWlY1UFBrUDBOdGVISGZEX25CRUhwS1RFVEJiS3UyTTgtY0JXQlEifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJhZG1pbi11c2VyLXRva2VuLWptNDZnIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQubmFtZSI6ImFkbWluLXVzZXIiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiJiZTM3OTMzOS02MTg4LTQ3ZDktOTc2OC0zZjVlYWVjMjBhYzkiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6a3ViZS1zeXN0ZW06YWRtaW4tdXNlciJ9.GCiJi_OHJd5ovsdxW0MRo88XTYH4j-Rl9Mk8JaAdbTVIg8SJyuORCa8AhDxVpEVeXe9V2MPv4PeSkdgFOgCNEqh1G8b45lslT6zLvo2wjDAxGHy53glEhohysvUCHWL842Txg7bmGa6AS3roa_HfNbWr71qyld-Al-ginOOsMR6YofEcgEFx2ARNQJZwdeWBzBaWKvDogMziF_DdPydg405YROTIj-h1kUWZpR158ImzIvcRAcBRZMp8go1tOLFWNWqGg2z9kDjGYbAKKSl0Exwog2jc15Nt-PyEr1Nly2cv-zetq-9pYTCZP0JhdiZBCjfRiE-qhSuyFlB1xgDRUA
注:将生成的token字符串复制到上图的“输入领牌”栏中,然后点击“确定 ”
2)Dashboard登录页面

注:此时获取不到cpu和内存信息,因为没有安装metrics-server
六、安装metrics-server
# yum -y install git # git clone https://github.com/kubernetes-incubator/metrics-server.git # cp /opt/software/metrics-server/deploy/1.8+/* /opt/kubernetes/dashboard/metrics/ # ll /opt/kubernetes/dashboard/metrics/ total 28 -rw-r--r-- 1 root root 397 Dec 14 15:17 aggregated-metrics-reader.yaml -rw-r--r-- 1 root root 303 Dec 14 15:18 auth-delegator.yaml -rw-r--r-- 1 root root 324 Dec 14 15:18 auth-reader.yaml -rw-r--r-- 1 root root 298 Dec 14 15:18 metrics-apiservice.yaml -rw-r--r-- 1 root root 1316 Dec 14 15:24 metrics-server-deployment.yaml -rw-r--r-- 1 root root 297 Dec 14 15:19 metrics-server-service.yaml -rw-r--r-- 1 root root 532 Dec 14 15:20 resource-reader.yaml # mkdir /opt/kubernetes/metrics/ssl/
2)修改metrics-server yaml文件配置
# cd /opt/kubernetes/dashboard/metrics/ # sed -i 's/k8s.gcr.io/mirrorgooglecontainers/g' metrics-server-deployment.yaml # vi metrics-server-deployment.yaml 将此处 - name: metrics-server image: k8s.gcr.io/metrics-server-amd64:v0.3.6 imagePullPolicy: IfNotPresent args: - --cert-dir=/tmp - --secure-port=4443 改为 - name: metrics-server image: mirrorgooglecontainers/metrics-server-amd64:v0.3.6 imagePullPolicy: IfNotPresent command: - /metrics-server - --metric-resolution=30s - --kubelet-insecure-tls - --kubelet-preferred-address-types=InternalIP,ExternalIP,Hostname args: - --cert-dir=/tmp - --secure-port=4443
3)签发metrics证书
# cd /root/ssl # cat > metrics-proxy-csr.json << EOF { "CN": "metrics-proxy", "hosts": [], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "ST": "BeiJing", "L": "BeiJing", "O": "K8s", "OU": "System" } ] } EOF # cfssl gencert -ca=ca.pem \ -ca-key=ca-key.pem \ -config=ca-config.json \ -profile=kubernetes metrics-proxy-csr.json | cfssljson -bare metrics-proxy # cp metrics-proxy*.pem /opt/kubernetes/metrics/ssl/
4)修改kube-apiserver.service和apiserver.conf文件,添加如下内容
# vi /opt/kubernetes/conf/apiserver.conf ## mertics data capture KUBE_METRICS_PARAMETER="--requestheader-client-ca-file=/opt/kubernetes/ssl/ca.pem \ --requestheader-allowed-names="" \ --enable-aggregator-routing=true \ --requestheader-extra-headers-prefix="X-Remote-Extra-" \ --requestheader-group-headers=X-Remote-Group \ --requestheader-username-headers=X-Remote-User \ --proxy-client-cert-file=/opt/kubernetes/metrics/ssl/metrics-proxy.pem \ --proxy-client-key-file=/opt/kubernetes/metrics/ssl/metrics-proxy-key.pem" # vi /usr/lib/systemd/system/kube-apiserver.service [Service] EnvironmentFile=/opt/kubernetes/conf/apiserver.conf ExecStart=/opt/kubernetes/bin/kube-apiserver \ $KUBE_API_ADDRESS \ $KUBE_ETCD_SERVERS \ $KUBE_SERVICE_ADDRESSES \ $KUBE_ADMISSION_CONTROL \ $KUBE_METRICS_PARAMETER \ //此处为新增部分 $KUBE_API_ARGS Restart=on-failure
重启master kube-apiserver
# systemctl daemon-reload
# systemctl restart kube-apiserver
5)部署metrics-server
# kubectl apply -f ./ clusterrole.rbac.authorization.k8s.io/system:aggregated-metrics-reader created clusterrolebinding.rbac.authorization.k8s.io/metrics-server:system:auth-delegator created rolebinding.rbac.authorization.k8s.io/metrics-server-auth-reader created apiservice.apiregistration.k8s.io/v1beta1.metrics.k8s.io created serviceaccount/metrics-server created deployment.apps/metrics-server created service/metrics-server created clusterrole.rbac.authorization.k8s.io/system:metrics-server created clusterrolebinding.rbac.authorization.k8s.io/system:metrics-server created
6)验证配置
# kubectl top node NAME CPU(cores) CPU% MEMORY(bytes) MEMORY% 192.168.168.3 212m 21% 867Mi 22% 192.168.168.4 143m 14% 1030Mi 26%

少壮不努力,老大干IT。
一入运维深似海,从此不见彼岸花。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号