WriteUp-湖湘杯-reverse 1,2,3
附:dalao wp: https://www.freebuf.com/column/219760.html
re1:
丢die
发现UPX
脱完壳后直接丢IDA 莽 qwq
/*没有修复输入表 分析起来极度痛苦(雾)*/
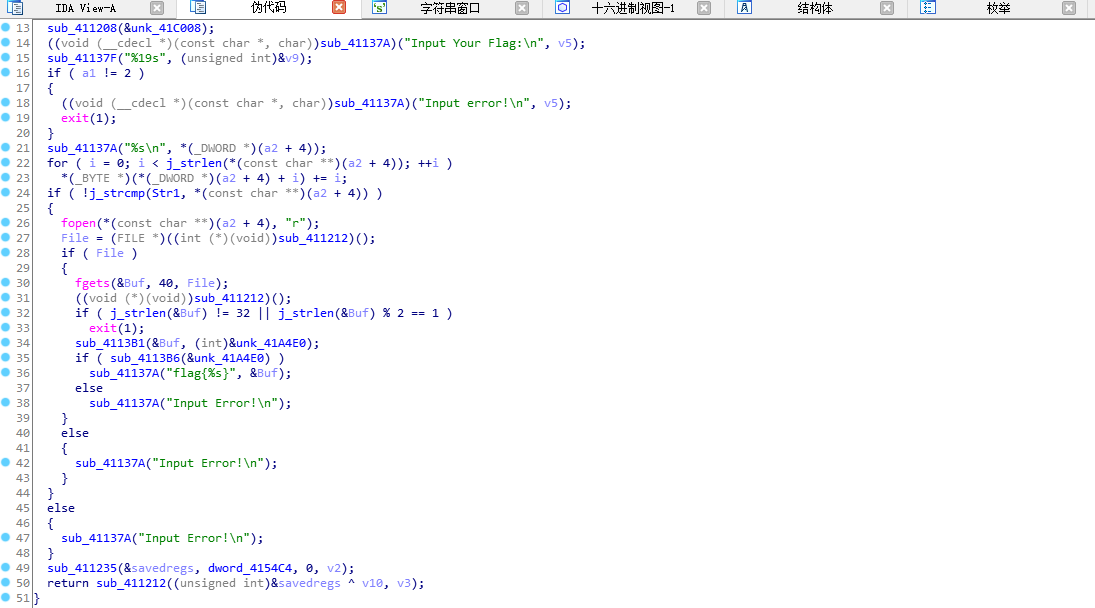
程序不难关注这个:

sub_4113B1 就是atoi ……
buf就是输入 ……
所以flag其实就是dword_41A078里的数据 减一 转字符……
dd 50h, 0C6h, 0F1h, 0E4h, 0E3h, 0E2h, 9Ah, 0A1h,
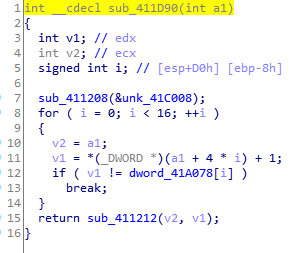
前面有个初始化……

比赛提交时冒出来个28:
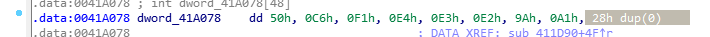
就这个28h dup(0) 我浪费了1h
qwq
re2:
简单的迷宫问题……

1 __int64 sub_1400010E0() 2 { 3 signed __int64 v0; // rbx 4 int v1; // esi 5 int v2; // er14 6 HANDLE v3; // rax 7 CHAR *v4; // rdx 8 HANDLE v5; // rax 9 int *v6; // rdi 10 signed __int64 v7; // r15 11 __int64 v8; // r9 12 signed __int64 v9; // r11 13 unsigned __int64 v10; // rdx 14 unsigned __int64 v11; // r8 15 __int64 v12; // r10 16 __int64 v13; // rdx 17 __int64 v14; // r8 18 int v15; // ecx 19 HKEY phkResult; // [rsp+30h] [rbp-D0h] 20 BOOL Wow64Process; // [rsp+38h] [rbp-C8h] 21 DWORD cbData; // [rsp+3Ch] [rbp-C4h] 22 DWORD Type; // [rsp+40h] [rbp-C0h] 23 int v21[28]; // [rsp+50h] [rbp-B0h] 24 CHAR ValueName[8]; // [rsp+C0h] [rbp-40h] 25 CHAR SubKey[16]; // [rsp+D0h] [rbp-30h] 26 __int128 v24; // [rsp+E0h] [rbp-20h] 27 __int128 v25; // [rsp+F0h] [rbp-10h] 28 int v26; // [rsp+100h] [rbp+0h] 29 char v27; // [rsp+104h] [rbp+4h] 30 __int128 v28; // [rsp+110h] [rbp+10h] 31 __int128 v29; // [rsp+120h] [rbp+20h] 32 __int128 v30; // [rsp+130h] [rbp+30h] 33 __int128 v31; // [rsp+140h] [rbp+40h] 34 BYTE Data; // [rsp+150h] [rbp+50h] 35 36 v0 = 0i64; 37 v1 = 0; 38 v2 = 0; 39 v3 = GetCurrentProcess(); 40 IsWow64Process(v3, &Wow64Process); 41 v4 = (CHAR *)&v28; 42 strcpy(ValueName, "Debugger"); 43 *(_OWORD *)SubKey = xmmword_140003260; 44 v26 = 1735746149; 45 v24 = xmmword_140003270; 46 phkResult = 0i64; 47 v25 = xmmword_140003280; 48 v27 = 0; 49 v28 = xmmword_1400032A0; 50 v29 = xmmword_1400032B0; 51 v30 = xmmword_1400032C0; 52 v31 = xmmword_1400032D0; 53 if ( !Wow64Process ) 54 v4 = SubKey; 55 if ( !RegCreateKeyA(HKEY_LOCAL_MACHINE, v4, &phkResult) ) 56 { 57 cbData = 256; 58 RegQueryValueExA(phkResult, ValueName, 0i64, &Type, &Data, &cbData); 59 if ( !strstr((const char *)&Data, "OllyIce") 60 && !strstr((const char *)&Data, "OllyDBG") 61 && !strstr((const char *)&Data, "WinDbg") 62 && !strstr((const char *)&Data, "x64dbg") ) 63 { 64 strstr((const char *)&Data, "Immunity"); 65 } 66 } 67 v5 = GetCurrentProcess(); 68 CheckRemoteDebuggerPresent(v5, (PBOOL)&Type); 69 v6 = v21; 70 v7 = 26i64; 71 do 72 { 73 sub_140001080("%d", v6); 74 --dword_140005034; 75 ++v6; 76 --v7; 77 } 78 while ( v7 ); 79 v8 = 0i64; 80 v9 = 0i64; 81 v10 = 0i64; 82 v11 = 0i64; 83 v12 = 0i64; 84 do 85 { 86 switch ( v21[v9] ) 87 { 88 case 1: 89 --v1; 90 v12 -= 7i64; 91 --v11; 92 break; 93 case 2: 94 ++v1; 95 v12 += 7i64; 96 ++v11; 97 break; 98 case 3: 99 --v2; 100 --v8; 101 --v10; 102 break; 103 default: 104 if ( v21[v9] != 4 ) 105 exit(0); 106 ++v2; 107 ++v8; 108 ++v10; 109 break; 110 } 111 if ( *(_DWORD *)&asc_140003350[4 * (v12 + v8)] == 1 ) 112 { 113 sub_140001020("You lost", v10, v11); 114 exit(0); 115 } 116 if ( v11 > 6 || v10 > 6 ) 117 { 118 puts("illegal access"); 119 exit(0); 120 } 121 ++v9; 122 } 123 while ( v9 < 26 ); 124 if ( *(_DWORD *)&asc_140003350[4 * (v2 + 7i64 * v1)] != 99 ) 125 _exit(0); 126 puts("You win!"); 127 sub_140001020("flag{", v13, v14); 128 do 129 { 130 switch ( v21[v0] ) 131 { 132 case 1: 133 v15 = 82; 134 break; 135 case 2: 136 v15 = 35; 137 break; 138 case 3: 139 v15 = 90; 140 break; 141 case 4: 142 v15 = 70; 143 break; 144 default: 145 goto LABEL_37; 146 } 147 putchar(v15); 148 LABEL_37: 149 ++v0; 150 } 151 while ( v0 < 26 ); 152 putchar(125); 153 system("pause"); 154 return 0i64; 155 }
DFS爆(比赛时自己走的迷宫qwq):

1 import numpy as np 2 3 4 def pad_ndmap(ndmap, dim, wall): 5 pad_option = ((1, 1), )* dim 6 return np.pad(ndmap, pad_option, 'constant', constant_values = wall) 7 # continue......... 8 9 10 def index(array): 11 return tuple(array.astype(int)) 12 13 14 def get_dimension(ndarray): 15 return len(ndarray.shape) 16 17 18 def get_nd_direction(dim): 19 posi_direction = np.eye(dim, dim) 20 nega_direction = -posi_direction 21 return np.append(posi_direction, nega_direction).reshape((dim * 2, dim)) 22 23 24 def possible_direction(ndmap, p, directions, trace, wall): 25 for di in directions: 26 next_p = p + di 27 next_p_var = ndmap[index(next_p)] 28 if next_p_var != trace and next_p_var != wall: 29 return di 30 31 return None 32 33 34 def back_one_step(ndmap, p, path, trace): 35 last_step = path.pop() 36 ndmap[index(p)] = trace 37 next_p = p - last_step 38 return next_p 39 40 41 def forward_one_step(ndmap, p, path, direction, trace): 42 path.append(direction) 43 next_p = p + direction 44 ndmap[index(p)] = trace 45 return next_p 46 47 48 def print_dire(dire): 49 down = np.array([1., 0.]) 50 up = np.array([-1., -0.]) 51 right = np.array([0., 1.]) 52 left = np.array([-0., -1.]) 53 if (dire == down).all(): 54 print("down") 55 elif (dire == up).all(): 56 print("up") 57 elif (dire == right).all(): 58 print("right") 59 elif (dire == left).all(): 60 print("left") 61 else: 62 print("??") 63 64 65 def print_path(path): 66 for dire in path: 67 print_dire(dire) 68 69 70 def DFS(ndmap, start, end): 71 trace = 0xbe 72 dim = get_dimension(ndmap) 73 directions = get_nd_direction(dim) 74 75 wall = 1 76 path = [] 77 ndmap = pad_ndmap(ndmap, dim, wall) 78 79 p = np.array(start) 80 ndmap[index(start)] = trace 81 while ndmap[index(p)] != end: 82 dire = possible_direction(ndmap, p, directions, trace, wall) 83 if dire is None: 84 if (p == start).all(): 85 return False 86 else: 87 p = back_one_step(ndmap, p, path, trace) 88 else: 89 p = forward_one_step(ndmap, p, path, dire, trace) 90 91 return path 92 93 94 maze = np.array([[8, 1, 14, 11, 7, 16, 1], 95 [11, 15, 15, 1, 1, 9, 1], 96 [1, 1, 1, 1, 1, 11, 1], 97 [12, 12, 8, 14, 1, 8, 1], 98 [8, 1, 1, 12, 9, 14, 1], 99 [13, 8, 11, 1, 1, 1, 1], 100 [1, 1, 9, 10, 9, 9, 99]]) 101 102 start_ = np.array([1, 1]) 103 end_ = 99 104 105 print_path(DFS(maze, start_, end_))
re3:
无壳健康dot net 程序, dnspy 走起.
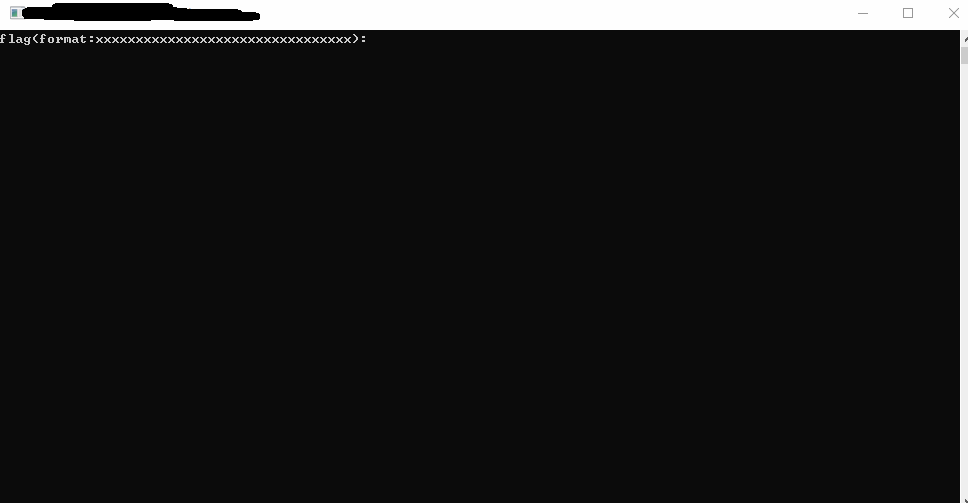
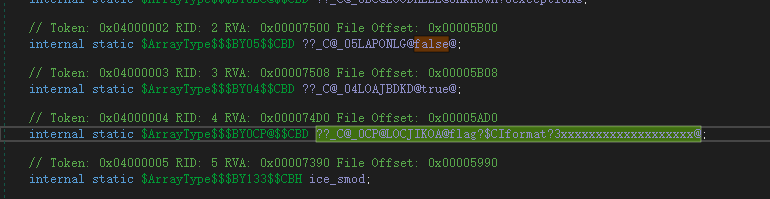
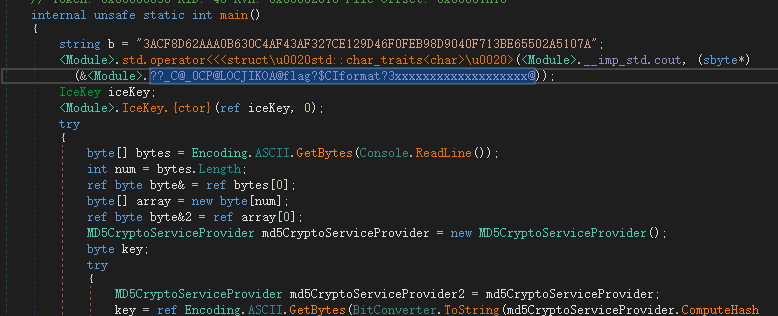

1 internal unsafe static int main() 2 { 3 string b = "3ACF8D62AAA0B630C4AF43AF327CE129D46F0FEB98D9040F713BE65502A5107A"; 4 <Module>.std.operator<<<struct\u0020std::char_traits<char>\u0020>(<Module>.__imp_std.cout, (sbyte*)(&<Module>.??_C@_0CP@LOCJIKOA@flag?$CIformat?3xxxxxxxxxxxxxxxxxxx@)); 5 IceKey iceKey; 6 <Module>.IceKey.{ctor}(ref iceKey, 0); 7 try 8 { 9 byte[] bytes = Encoding.ASCII.GetBytes(Console.ReadLine()); 10 int num = bytes.Length; 11 ref byte byte& = ref bytes[0]; 12 byte[] array = new byte[num]; 13 ref byte byte&2 = ref array[0]; 14 MD5CryptoServiceProvider md5CryptoServiceProvider = new MD5CryptoServiceProvider(); 15 byte key; 16 try 17 { 18 MD5CryptoServiceProvider md5CryptoServiceProvider2 = md5CryptoServiceProvider; 19 key = ref Encoding.ASCII.GetBytes(BitConverter.ToString(md5CryptoServiceProvider.ComputeHash(Encoding.ASCII.GetBytes("iriszero"))).Replace("-", "").ToLower())[0]; 20 } 21 catch 22 { 23 MD5CryptoServiceProvider md5CryptoServiceProvider2; 24 ((IDisposable)md5CryptoServiceProvider2).Dispose(); 25 throw; 26 } 27 ((IDisposable)md5CryptoServiceProvider).Dispose(); 28 <Module>.IceKey.Set(ref iceKey, ref key); 29 if (0 < num) 30 { 31 long num2 = 0L; 32 uint num3 = (num - 1 >> 3) + 1; 33 do 34 { 35 <Module>.IceKey.Encrypt(ref iceKey, ref byte& + num2, ref byte&2 + num2); 36 num2 += 8L; 37 num3 += uint.MaxValue; 38 } 39 while (num3 > 0u); 40 } 41 sbyte* val = ref (BitConverter.ToString(array).Replace("-", "").ToString() == b) ? ref <Module>.??_C@_04LOAJBDKD@true@ : ref <Module>.??_C@_05LAPONLG@false@; 42 <Module>.std.basic_ostream<char,std::char_traits<char>\u0020>.<<(<Module>.std.operator<<<struct\u0020std::char_traits<char>\u0020>(<Module>.__imp_std.cout, val), <Module>.__unep@??$endl@DU?$char_traits@D@std@@@std@@$$FYAAEAV?$basic_ostream@DU?$char_traits@D@std@@@0@AEAV10@@Z); 43 if (0 < num) 44 { 45 long num4 = 0L; 46 uint num5 = (num - 1 >> 3) + 1; 47 do 48 { 49 <Module>.IceKey.Decrypt(ref iceKey, ref byte&2 + num4, ref byte& + num4); 50 num4 += 8L; 51 num5 += uint.MaxValue; 52 } 53 while (num5 > 0u); 54 } 55 } 56 catch 57 { 58 <Module>.___CxxCallUnwindDtor(ldftn(IceKey.{dtor}), (void*)(&iceKey)); 59 throw; 60 } 61 <Module>.IceKey.{dtor}(ref iceKey); 62 return 0; 63 }
输入到bytes
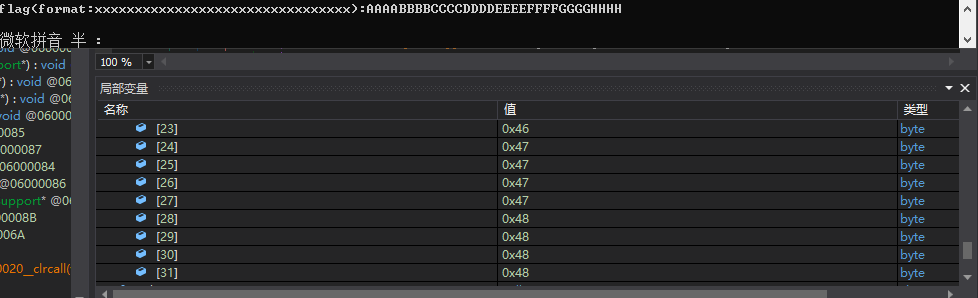
加密后放到array
转string后与string 对比
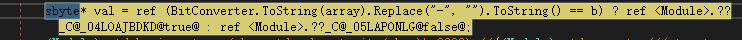
string b:

接着解密 :
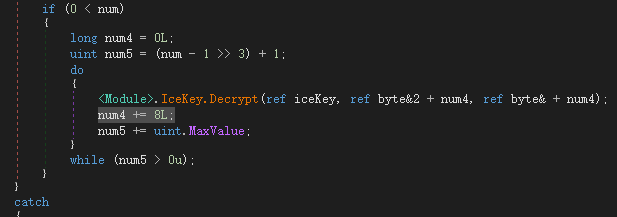
深入Decrypt :

第一轮解密前:
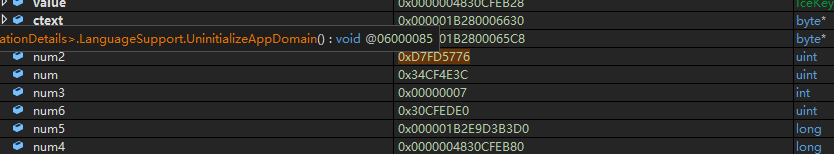
之前加密后的array:
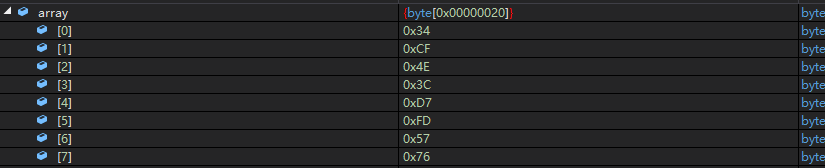
第一轮解密后:
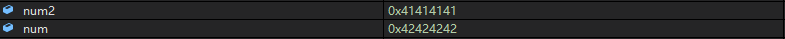
取巧: 每轮解密前用字符串b转成数字的对应位的值放到num, num2中
re4:
安卓逆向不会 比赛时没有A qwq
3个签到题 emmmm……(虽然我也只会做签到题)
后面A pwn 与crypto去了qwq
(pwn好难qwq)
最后总分才2000多 rk150+ qwq
凉了凉了XD



 浙公网安备 33010602011771号
浙公网安备 33010602011771号