1.0 PHPStan
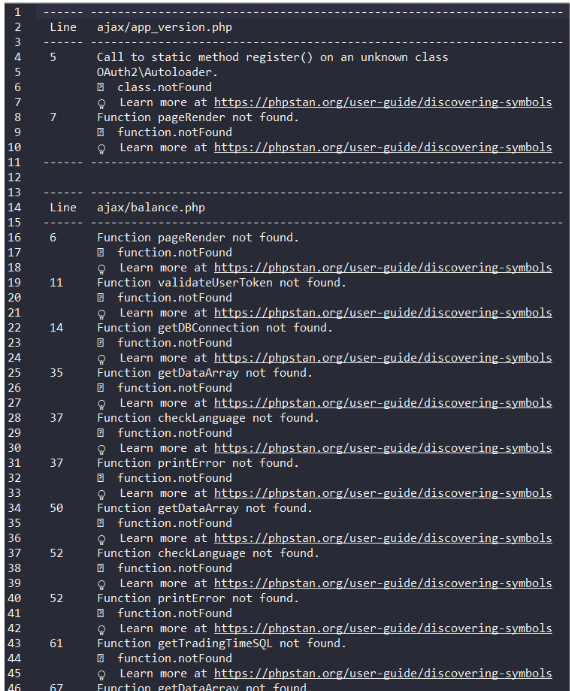
PHPStan: Find Bugs Without Writing Tests
https://phpstan.org/
sudo docker pull ghcr.io/phpstan/phpstan:2-php8.3 sudo docker run --rm -v /home/user/dbpower/app:/app ghcr.io/phpstan/phpstan:2-php8.3 analyse /app > phpstan-results.txt
鏡像跑。https://phpstan.org/user-guide/docker
sudo docker run --rm -v /home/user/dbpower/app:/app ghcr.io/phpstan/phpstan:2-php8.3 analyse /app --level max > phpstan-result.txt
lv10
parameters:
ignoreErrors:
- '#Function .*? not found#'
- '#Cannot access property .*? on mixed#'
- '#Part .*? \(mixed\) of encapsed string cannot be cast to string#'
- '#Cannot access offset .*? on mixed#'
- '#Binary operation "\." between non-falsy-string and mixed results in an error#'
- identifier: offsetAccess.notFound
phpstan.neon
cd /home/user/dbpower sudo docker run --rm -v /home/user/dbpower/app:/app ghcr.io/phpstan/phpstan:2-php8.3 analyse -c phpstan.neon /app --level max > phpstan-result-`date +\%Y\%m\%d_\%H\%M\%S`.txt
lv10 with config, ignore errors
cd /home/user/dbpower sudo docker run --rm -v /home/user/dbpower/app:/app ghcr.io/phpstan/phpstan:2-php8.3 analyse --error-format=table -c phpstan.neon /app --level max > phpstan-result-`date +\%Y\%m\%d_\%H\%M\%S`.txt
output format = table
cd /home/user/dbpower sudo docker run --rm -v /home/user/dbpower/app:/app ghcr.io/phpstan/phpstan:2-php8.3 analyse --error-format=json -c phpstan.neon /app --level max > phpstan-result-`date +\%Y\%m\%d_\%H\%M\%S`.json
output format = json
2.0 RIPS
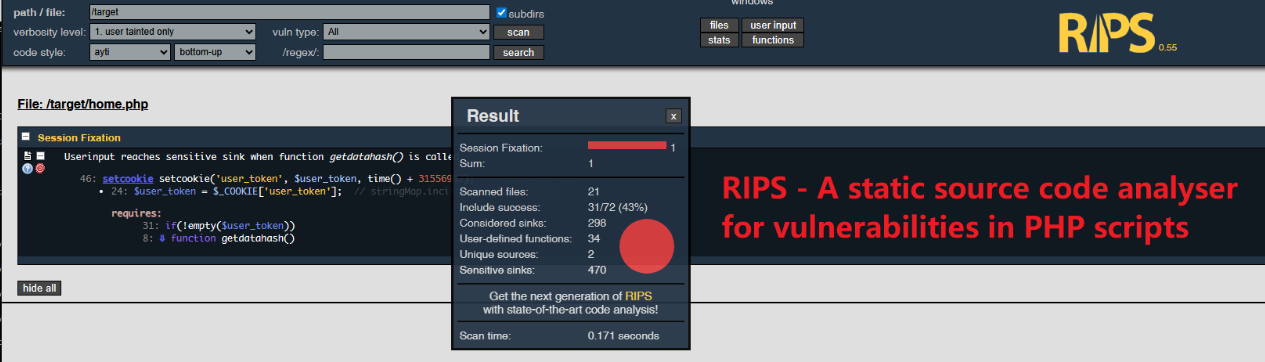
RIPS - A static source code analyser for vulnerabilities in PHP scripts
https://github.com/ripsscanner/rips
sudo docker pull gsfish/rips-docker sudo docker run -d --rm -p 83:80 -v /home/user/dbpower/app:/target gsfish/rips-docker
鏡像跑。https://github.com/gsfish/rips-docker




 浙公网安备 33010602011771号
浙公网安备 33010602011771号