BUUCTF 其余刷题记录
BUUCTF 其余刷题记录
[BJDCTF2020]这是base??
考察 base64 映射表
根据自定义的映射表还原出索引,替换成标准表对应字母
payload
import base64
dict={0: 'J', 1: 'K', 2: 'L', 3: 'M', 4: 'N', 5: 'O', 6: 'x', 7: 'y', 8: 'U', 9: 'V', 10: 'z', 11: 'A', 12: 'B', 13: 'C', 14: 'D', 15: 'E', 16: 'F', 17: 'G', 18: 'H', 19: '7', 20: '8', 21: '9', 22: 'P', 23: 'Q', 24: 'I', 25: 'a', 26: 'b', 27: 'c', 28: 'd', 29: 'e', 30: 'f', 31: 'g', 32: 'h', 33: 'i', 34: 'j', 35: 'k', 36: 'l', 37: 'm', 38: 'W', 39: 'X', 40: 'Y', 41: 'Z', 42: '0', 43: '1', 44: '2', 45: '3', 46: '4', 47: '5', 48: '6', 49: 'R', 50: 'S', 51: 'T', 52: 'n', 53: 'o', 54: 'p', 55: 'q', 56: 'r', 57: 's', 58: 't', 59: 'u', 60: 'v', 61: 'w', 62: '+', 63: '/', 64: '='}
chipertext = 'FlZNfnF6Qol6e9w17WwQQoGYBQCgIkGTa9w3IQKw'
cipher=""
b64_dict=[]
for i in range(ord('A'),ord('A')+26):
b64_dict.append(chr(i))
for i in range(ord('a'),ord('a')+26):
b64_dict.append(chr(i))
for i in range(0,10):
b64_dict.append(i)
b64_dict.append('+')
b64_dict.append('/')
new_dict={}
for key,value in dict.items():
new_dict[value]=key
for i in chipertext:
cipher+=str(b64_dict[new_dict[i]])
m = base64.b64decode(cipher)
print(m)
[NCTF2019]Sore
cipher = ''.join( itoc( ( ctoi(p) + ctoi( key[i % len_key] ) ) % 52 ) for i,p in enumerate(plain) )
类似维吉尼亚密码,只是空间扩大了一倍
在线解密得到key
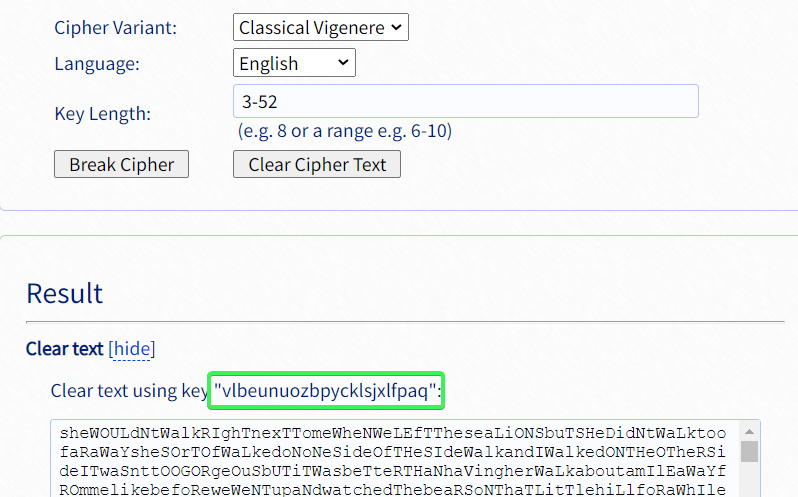
维吉尼亚空间为26,所以解密存在大小写的误差区别
decode: sheWOULdNtWalkRIghTnexT
real_m: Shewouldntwalkrightnext
cipher: nsfAIHFrMuLynuCApeEstxJ
根据明文,密文求解真实的key
from string import ascii_letters
m = "Shewouldntwalkrightnext"
c = "nsfAIHFrMuLynuCApeEstxJ"
for i in range(len(m)):
a = ascii_letters.index(m[i])
b = ascii_letters.index(c[i])
t = (b-a)%52
print(ascii_letters[t],end="")
[SUCTF2019]MT
def convert(m):
m = m ^ m >> 13
m = m ^ m << 9 & 2029229568
m = m ^ m << 17 & 2245263360
m = m ^ m >> 19
return m
搞定该函数的逆函数即可
以 m = m ^ m << 9 & 2029229568 为例
m4 m3 m2 m1
m .....|.........|.........|.........
m3[-5:] m2 m1 00
m' .....|.........|.........|.........
m1 = c[-9:]
m2 = c[-18:-9]^(m1 & n[-18:-9])
m3 = c[-27:-18] ^ (m2 & n[-27:-18])
m4 = c[:5] ^ (m3[-5:] & n[:5])
m = m4+m3+m2+m1
其余以此类推
payload
def myfill(num,fill_num):
return bin(num)[2:].zfill(fill_num)
n1 = myfill(2245263360,32)
n2 = myfill(2029229568,32)
def mydecode(c):
c = int(c,16)
c = myfill(c,32)
#4
m1 = int(c[:13],2)^int(c[-13:],2)
m1 = myfill(m1,13)
c = c[:19]+m1
#3
m1 = int(c[:15],2)^(int(c[-15:],2)&int(n1[:15],2))
m1 = myfill(m1,15)
c = m1+c[15:]
#2
m1 = c[-9:]
m2 = int(c[-18:-9],2)^(int(m1,2)&int(n2[-18:-9],2))
m2 = myfill(m2,9)
m3 = int(c[-27:-18],2)^(int(m2,2)&int(n2[-27:-18],2))
m3 = myfill(m3,9)
m4 = int(c[:5],2)^(int(m3[-5:],2)&int(n2[:5],2))
m4 = myfill(m4,5)
c = m4+m3+m2+m1
#1
m1 = int(c[13:26],2)^int(c[:13],2)
m1 = myfill(m1,13)
m2 = int(m1[:6],2)^int(c[-6:],2)
m2 = myfill(m2,6)
c = c[:13]+m1+m2
return c
cipher = "641460a9e3953b1aaa21f3a2"
r = ''
for i in range(0,len(cipher),8):
c = cipher[i:i+8]
r += mydecode(c)
print(hex(int(r,2))[2:])

 buuctf刷题记录
buuctf刷题记录

 浙公网安备 33010602011771号
浙公网安备 33010602011771号