BUUCTF RSA 刷题记录
RSA 刷题记录
rsa2
题目
N = 101991809777553253470276751399264740131157682329252673501792154507006158434432009141995367241962525705950046253400188884658262496534706438791515071885860897552736656899566915731297225817250639873643376310103992170646906557242832893914902053581087502512787303322747780420210884852166586717636559058152544979471
e = 46731919563265721307105180410302518676676135509737992912625092976849075262192092549323082367518264378630543338219025744820916471913696072050291990620486581719410354385121760761374229374847695148230596005409978383369740305816082770283909611956355972181848077519920922059268376958811713365106925235218265173085
import hashlib
flag = "flag{" + hashlib.md5(hex(d)).hexdigest() + "}"
解决
hack_RSA 得到 d
环境改为python2,得到flag
RSA & what
共模攻击后得到base64密文
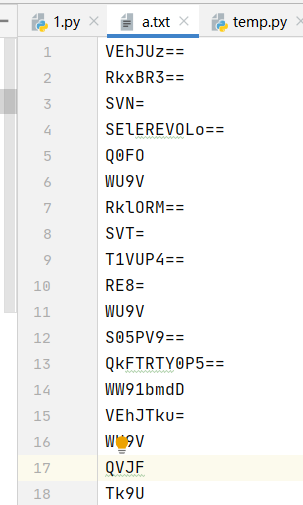
base64隐写解密
payload
def inttobin(a, n):
ret = bin(a)[2:]
while len(ret) < n:
ret = '0' + ret
return ret
def base64Steganography(filepath):
table = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'
f = open(filepath, "r") # r读取,'\n'占一位
tmpbin = ''
res = ''
line = f.readline()
while line:
if line[-2] == '=':
if line[-3] == '=':
tmpbin += inttobin(table.index(line[-4]), 6)[2:]
else:
tmpbin += inttobin(table.index(line[-3]), 6)[4:]
line = f.readline()
quotient = len(tmpbin) // 8
for i in range(quotient):
res += chr(int(tmpbin[8 * i:8 * i + 8], 2))
print(res)
[De1CTF2019]babyrsa
assert(c1==pow(flag,e1,p*q1))
assert(c2==pow(flag,e2,p*q2))
已知 c1,e1,p,q1 c2,e2,q2 求flag
\(gcd(e1,(p-1)*(q1-1))=14\ \ \ gcd(e2,(p-1)*(q2-1))=14\)
可以得到
\(m^{14}\equiv a_1\ mod\ p*q1\\m^{14}\equiv a_2\ mod\ p*q2\)
由模因子可得
\(m^{14}\equiv a_1 mod\ q1\\m^{14}\equiv a_2\ mod\ q2\)
由CRT可得
\(m^{14}\equiv a_3\ mod\ q1*q2\)
问题重新回归到 \(gcd(e,phi)!=1\)
而 \(gcd(7,(q1-1)*(q2-1))=1\)
解得 \(m^2\),开方进而得到 m

 BUUCTF RSA 刷题记录
BUUCTF RSA 刷题记录


 浙公网安备 33010602011771号
浙公网安备 33010602011771号