HyperHide 可以过VMP强壳
HyperHide 可以过VMP强壳
1、注意事项
- 虚拟机要开启VT模式
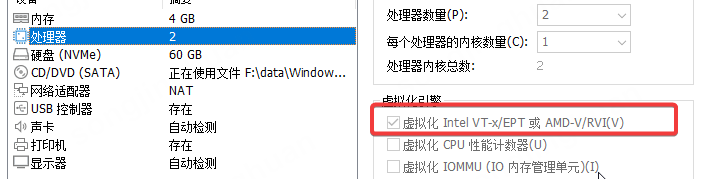
这个不开的下场就是有一个sys驱动文件会启动不了。
-
准备好工具,debugView
-
官方使用的是 al-khaser 但是我们使用debugVinew
-
因该驱动无签名所以要在测试模式下运行。
在Cmd中运行:bcdedit /set testsigning on 随后重启电脑 注意观察桌面右下角提示,提示为测试模式已开启才可以
2、HyperHide下载安装加配置
HyperHide 官方下载即可
官方Github链接:链接直达
release 界面下载最新版据说可以过3.81强壳。
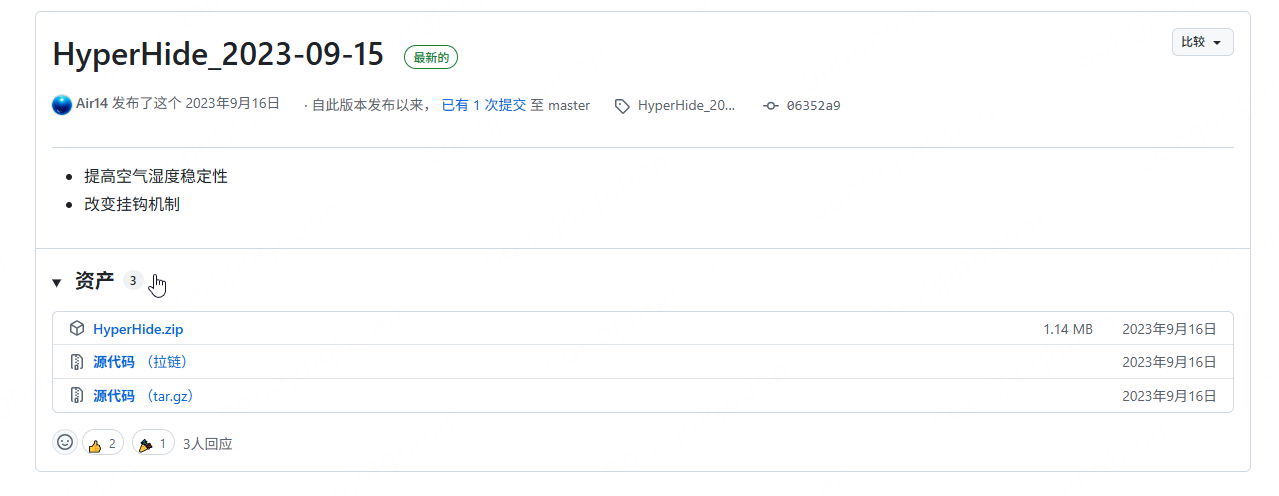
下载解压好后如图:
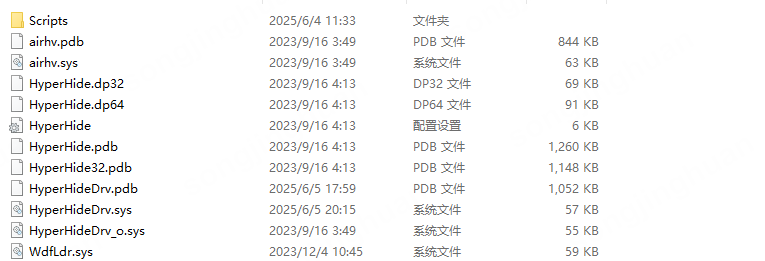
首先,要记得修改Scripts中Create中路径问题。
在这里直接将路径修改为本地两个驱动的路径就好(中文路径没有尝试过),官方原版是指向的drives路径,这里记得复制一下。
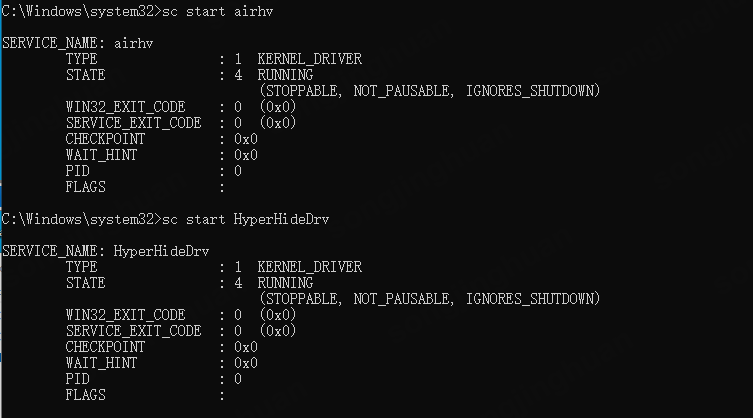
随后直接以管理员方式启动Script路径下create.bat文件。
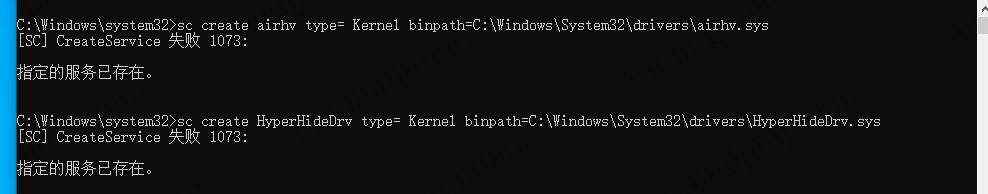
这里我是已经启动了,会弹出这个,第一次驱动会是服务启动成功。
然后再以管理员身份运行on.bat即可
下一步将,
HyperHide.ini 与 HyperHide.dp64 拷贝到X64的插件文件夹中即可。
初始打开的时候,。会提示这样。
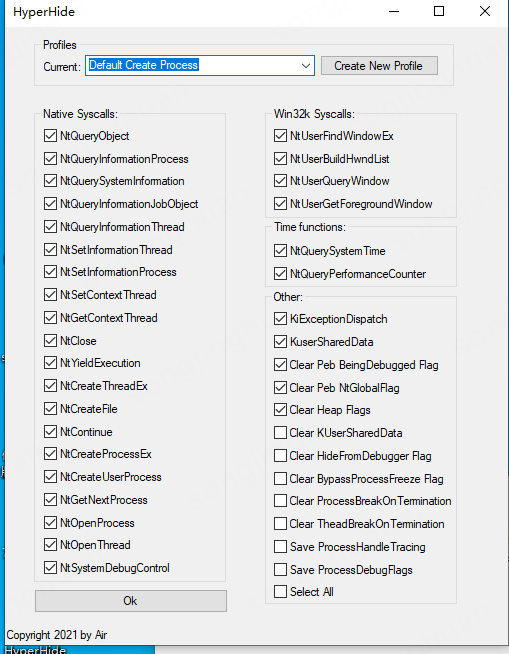
但是VMP一般不能启动调试,还是要附加的方式来
所以将Current改为:Default Attach
即可解决该问题。AI-Khaser输出如下:
[al-khaser version 0.82]
-------------------------[Initialisation]-------------------------
[*] You are running: Microsoft Windows 10 (build 19045) 64-bit
[*] All APIs present and accounted for.
-------------------------[TLS Callbacks]-------------------------
[*] TLS process attach callback [ GOOD ]
[*] TLS thread attach callback [ GOOD ]
-------------------------[Debugger Detection]-------------------------
[*] Checking IsDebuggerPresent API [ GOOD ]
[*] Checking PEB.BeingDebugged [ GOOD ]
[*] Checking CheckRemoteDebuggerPresent API [ GOOD ]
[*] Checking PEB.NtGlobalFlag [ BAD ]
[*] Checking ProcessHeap.Flags [ BAD ]
[*] Checking ProcessHeap.ForceFlags [ BAD ]
[*] Checking Low Fragmentation Heap [ GOOD ]
[*] Checking NtQueryInformationProcess with ProcessDebugPort [ GOOD ]
[*] Checking NtQueryInformationProcess with ProcessDebugFlags [ GOOD ]
[*] Checking NtQueryInformationProcess with ProcessDebugObject [ GOOD ]
[*] Checking WudfIsAnyDebuggerPresent API [ GOOD ]
[*] Checking WudfIsKernelDebuggerPresent API [ GOOD ]
[*] Checking WudfIsUserDebuggerPresent API [ GOOD ]
[*] Checking NtSetInformationThread with ThreadHideFromDebugger [ GOOD ]
[*] Checking CloseHandle with an invalide handle [ GOOD ]
[*] Checking NtSystemDebugControl [ GOOD ]
[*] Checking UnhandledExcepFilterTest [ GOOD ]
[*] Checking OutputDebugString [ GOOD ]
[*] Checking Hardware Breakpoints [ GOOD ]
[*] Checking Software Breakpoints [ GOOD ]
[*] Checking Interupt 0x2d [ GOOD ]
[*] Checking Interupt 1 [ GOOD ]
[*] Checking trap flag [ GOOD ]
[*] Checking Memory Breakpoints PAGE GUARD [ GOOD ]
[*] Checking If Parent Process is explorer.exe [ GOOD ]
[*] Checking SeDebugPrivilege [ GOOD ]
[*] Checking NtQueryObject with ObjectTypeInformation [ GOOD ]
[*] Checking NtQueryObject with ObjectAllTypesInformation [ GOOD ]
[*] Checking NtYieldExecution [ BAD ]
[*] Checking CloseHandle protected handle trick [ GOOD ]
[*] Checking NtQuerySystemInformation with SystemKernelDebuggerInformation [ GOOD ]
[*] Checking SharedUserData->KdDebuggerEnabled [ GOOD ]
[*] Checking if process is in a job [ GOOD ]
[*] Checking VirtualAlloc write watch (buffer only) [ GOOD ]
[*] Checking VirtualAlloc write watch (API calls) [ GOOD ]
[*] Checking VirtualAlloc write watch (IsDebuggerPresent) [ GOOD ]
[*] Checking VirtualAlloc write watch (code write) [ GOOD ]
[*] Checking for page exception breakpoints [ GOOD ]
[*] Checking for API hooks outside module bounds [ GOOD ]
DebugView显示如下:(直接监视了所有消息)
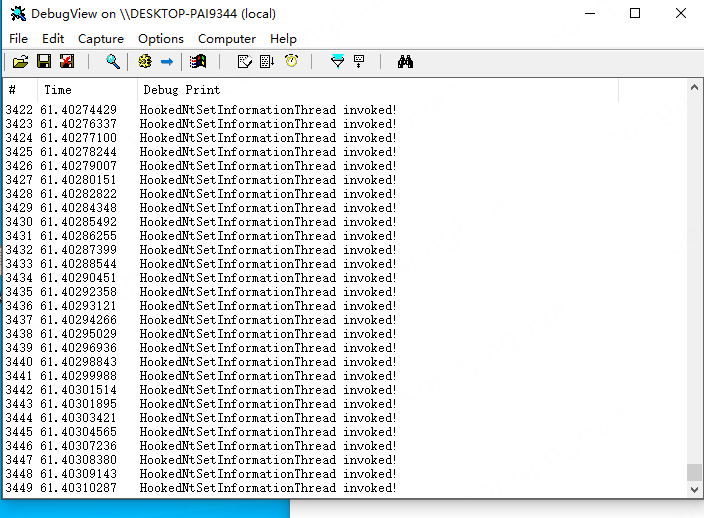
附加程序随时暂停:
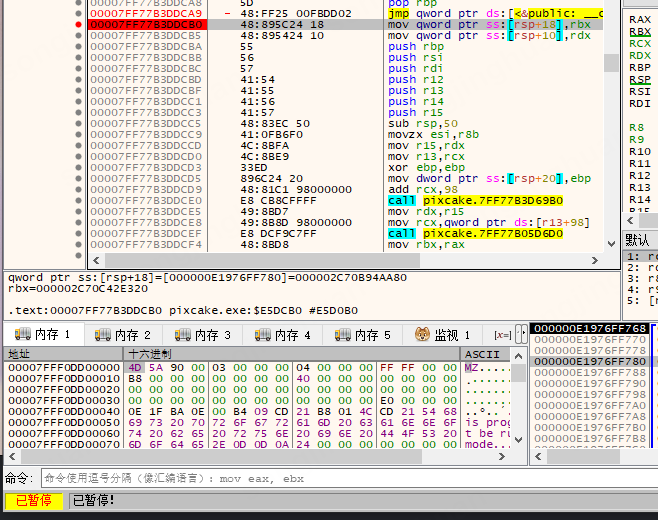
最后:
注意系统更新那么多,要不然会有更多的问题,其次要再虚拟机运行,一天能蹦好多次


 浙公网安备 33010602011771号
浙公网安备 33010602011771号