大叔经验分享(30)CM开启kerberos
kerberos安装详见:https://www.cnblogs.com/barneywill/p/10394164.html
一 为CM创建用户
# kadmin.local -q "addprinc scm/admin"
名字和密码任意,后续配置中会使用
二 CM配置过程
1 启用Kerberos
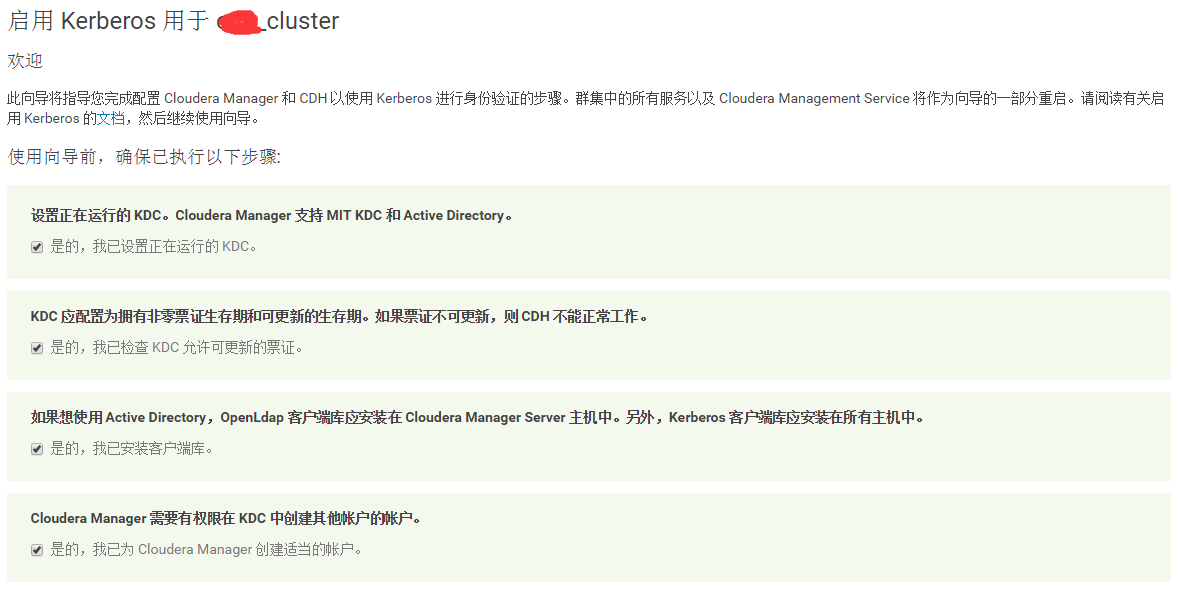
2 全部选中
3 按照/etc/krb5.conf填写

4

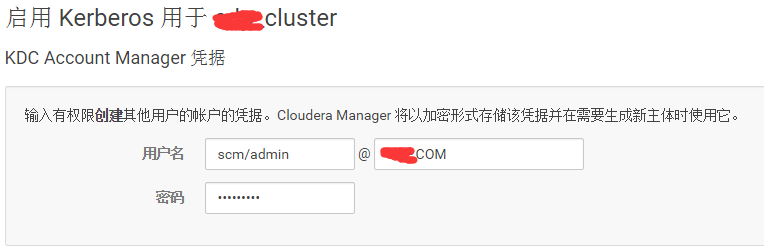
5 填写刚才创建的用户名密码
6 下一步
7 下一步

8

可以查看cm创建的用户
# kadmin.local -q 'listprincs'
三 可能的问题
如果安装过程中有问题,有些组件可能会启动失败,
1)impala
statestored启动报错
SASL message (Kerberos (internal)): Couldn't find mech GSSAPI
或者catalogd和impalad启动报错
I0219 00:31:16.314851 857 statestore-subscriber.cc:238] statestore registration unsuccessful: Couldn't open transport for $server2.bj:24000 (No more data to read.)
F0219 00:31:16.314926 857 catalogd-main.cc:88] Couldn't open transport for $server2.bj:24000 (No more data to read.)
. Impalad exiting.
检查如下library是否安装
# yum install cyrus-sasl-plain cyrus-sasl-devel cyrus-sasl-gssapi
2)hue
hue实例 Kerberos Ticket Renewer 启动失败
INFO kt_renewer
Renewing kerberos ticket to work around kerberos 1.8.1: /bin/kinit -R -c /var/run/hue/hue_krb5_ccache
ERROR kt_renewer
Couldn't renew kerberos ticket in order to work around Kerberos 1.8.1 issue. Please check that the ticket for 'hue/$server1@ANYTHING.COM' is still renewable:
$ klist -f -c /var/run/hue/hue_krb5_ccache
If the 'renew until' date is the same as the 'valid starting' date, the ticket cannot be renewed. Please check your KDC configuration, and the ticket renewal policy (maxrenewlife) for the 'hue/$server1@ANYTHING.COM' and `krbtgt' principals.
[19/Feb/2019 07:32:04 ] settings INFO Welcome to Hue 3.9.0
重现问题
# klist -f -c /var/run/hue/hue_krb5_ccache
Ticket cache: FILE:/var/run/hue/hue_krb5_ccache
Default principal: hue/$server1@ANYTHING.COMValid starting Expires Service principal
02/19/2019 10:06:50 02/20/2019 10:06:50 krbtgt/ANYTHING.COM@ANYTHING.COM
Flags: FI
# /bin/kinit -R -c /var/run/hue/hue_krb5_ccache
kinit: KDC can't fulfill requested option while renewing credentials
检查:
1)检查配置文件
# vi /etc/krb5.conf
ticket_lifetime = 24h
renew_lifetime = 7d
# vi /var/kerberos/krb5kdc/kdc.conf
max_renewable_life = 7d 0h 0m 0s
default_principal_flags = +renewable
2)检查krbtgt用户的Maximum renewable life
# kadmin.local -q 'getprinc krbtgt/ANYTHING.COM@ANYTHING.COM'
Principal: krbtgt/ANYTHING.COM@ANYTHING.COM
Expiration date: [never]
Last password change: [never]
Password expiration date: [never]
Maximum ticket life: 1 day 00:00:00
Maximum renewable life: 0 days 00:00:00
Last modified: Mon Feb 18 22:02:42 CST 2019 (db_creation@ANYTHING.COM)
Last successful authentication: [never]
Last failed authentication: [never]
Failed password attempts: 0
Number of keys: 9
Key: vno 1, aes256-cts-hmac-sha1-96
Key: vno 1, aes128-cts-hmac-sha1-96
Key: vno 1, des3-cbc-sha1
Key: vno 1, arcfour-hmac
Key: vno 1, camellia256-cts-cmac
Key: vno 1, camellia128-cts-cmac
Key: vno 1, des-hmac-sha1
Key: vno 1, des-cbc-md5
Key: vno 1, des-cbc-crc
MKey: vno 1
Attributes: LOCKDOWN_KEYS
Policy: [none]
重点是
Maximum renewable life: 0 days 00:00:00
修改krbtgt的maxrenewlife
# kadmin.local -q 'modprinc -maxrenewlife "7d" krbtgt/ANYTHING.COM'
如果有必要,修改其他用户的maxrenewlife
# kadmin.local -q 'modprinc -maxrenewlife "7d" +allow_renewable $user/$host@ANYTHING.COM'
删除cache
# /bin/rm /var/run/hue/hue_krb5_ccache
重启Kerberos Ticket Renewer
3)
Activity Monitor 报错
ERROR Main
Failed to start Firehose
java.lang.RuntimeException: java.util.concurrent.ExecutionException: java.lang.RuntimeException: java.io.IOException: Login failure for hue/$server1@ANYTHING.COM from keytab cmon.keytab
...
Caused by: KrbException: no supported default etypes for default_tkt_enctypes
查找default_tkt_enctypes
# vi /etc/krb5.conf
default_tkt_enctypes = aes256-cts
查找cmon.keytab
# find /opt -name cmon.keytab
/opt/cloudera-manager/cm-5.16.1/run/cloudera-scm-agent/process/240-cloudera-mgmt-ACTIVITYMONITOR/cmon.keytab
查看keytab中的principal
# klist -k /opt/cloudera-manager/cm-5.16.1/run/cloudera-scm-agent/process/240-cloudera-mgmt-ACTIVITYMONITOR/cmon.keytab
Keytab name: FILE:/opt/cloudera-manager/cm-5.16.1/run/cloudera-scm-agent/process/240-cloudera-mgmt-ACTIVITYMONITOR/cmon.keytab
KVNO Principal
---- --------------------------------------------------------------------------
2 hue/$server1@ANYTHING.COM (aes256-cts-hmac-sha1-96)
2 hue/$server1@ANYTHING.COM (aes128-cts-hmac-sha1-96)
2 hue/$server1@ANYTHING.COM (des3-cbc-sha1)
2 hue/$server1@ANYTHING.COM (arcfour-hmac)
2 hue/$server1@ANYTHING.COM (camellia256-cts-cmac)
2 hue/$server1@ANYTHING.COM (camellia128-cts-cmac)
2 hue/$server1@ANYTHING.COM (des-hmac-sha1)
2 hue/$server1@ANYTHING.COM (des-cbc-md5)
发现确实没有 aes256-cts,修改
# vi /etc/krb5.conf
default_tgs_enctypes = aes256-cts des3-cbc-sha1
default_tkt_enctypes = aes256-cts des3-cbc-sha1
permitted_enctypes = aes256-cts des3-cbc-sha1
重启Activity Monitor
4)如果遇到
[javax.security.sasl.SaslException: GSS initiate failed [Caused by GSSException: Failure unspecified at GSS-API level (Mechanism level: Encryption type AES256 CTS mode with HMAC SHA1-96 is not supported/enabled)]]
请见:https://www.cnblogs.com/barneywill/p/10540008.html
---------------------------------------------------------------- 结束啦,我是大魔王先生的分割线 :) ----------------------------------------------------------------
- 由于大魔王先生能力有限,文中可能存在错误,欢迎指正、补充!
- 感谢您的阅读,如果文章对您有用,那么请为大魔王先生轻轻点个赞,ありがとう


 浙公网安备 33010602011771号
浙公网安备 33010602011771号