搭建etcd集群
一丶生成ectd自签名证书
- 下载cfssl工具
https://github.com/cloudflare/cfssl/releases
wget -O /usr/bin/cfssl https://github.com/cloudflare/cfssl/releases/download/v1.6.1/cfssl_1.6.1_linux_amd64
wget -O /usr/bin/cfssljson https://github.com/cloudflare/cfssl/releases/download/v1.6.1/cfssljson_1.6.1_linux_amd64
wget -O /usr/bin/cfssl-certinfo https://github.com/cloudflare/cfssl/releases/download/v1.6.1/cfssl-certinfo_1.6.1_linux_amd64
chmod +x /usr/bin/cfssl
chmod +x /usr/bin/cfssljson
chmod +x /usr/bin/cfssl-certinfo - 生成默认的配置文件和证书签名请求文件
mkdir -p /data/app/etcd/etc
mkdir -p /data/app/etcd/ssl
mkdir -p /data/app/etcd/data/wal
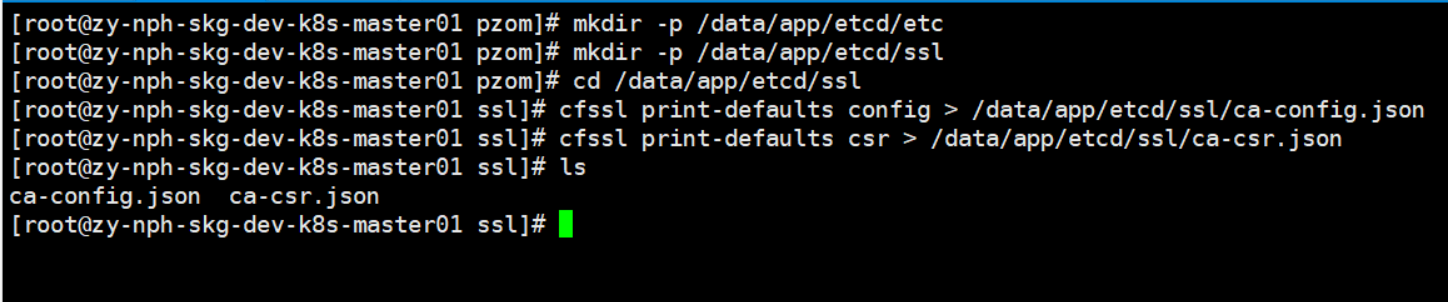
cd /data/app/etcd/sslcfssl print-defaults config > /data/app/etcd/ssl/ca-config.json
cfssl print-defaults csr > /data/app/etcd/ssl/ca-csr.json![]()
- 修改ca 证书请求文件
vim /data/app/etcd/ssl/ca-csr.json
{ "CN": "kubernetes", "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "ST": "BJ", "L": "BJ", "O": "k8s", "OU": "system" } ], "ca": { "expiry": "87600h" } }
注解:
CN:Common Name(公用名称),kube-apiserver 从证书中提取该字段作为请求的用户名 (User Name);
浏览器使用该字段验证网站是否合法;对于 SSL 证书,一般为网站域名;而对于代码签名证书则为申请
单位名称;而对于客户端证书则为证书申请者的姓名。
O:Organization(单位名称),kube-apiserver 从证书中提取该字段作为请求用户所属的组 (Group);
对于 SSL 证书,一般为网站域名;而对于代码签名证书则为申请单位名称;而对于客户端单位证书则为
证书申请者所在单位名称。
L 字段:所在城市
S 字段:所在省份
C 字段:只能是国家字母缩写,如中国:CN - 修改ca 证书文件
vim ca-config.json{
"signing": {
"default": {
"expiry": "87600h"
},
"profiles": {
"kubernetes": {
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
],
"expiry": "87600h"
}
}
}
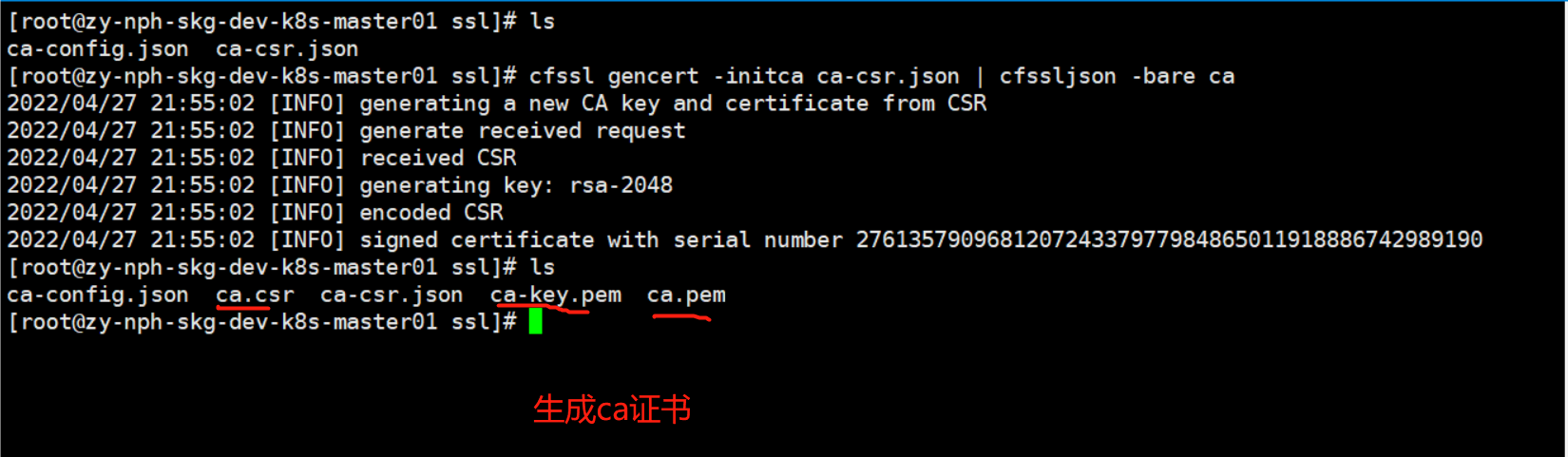
} - 生成ca证书
cfssl gencert -initca ca-csr.json | cfssljson -bare ca![]()
- 配置 etcd 证书请求
vim etcd-csr.json
{ "CN": "etcd", "hosts": [ "127.0.0.1", "172.31.24.96", "172.31.24.97", "172.31.24.98", "172.31.24.200", "172.31.24.201", "172.31.24.202", "172.31.24.203", "172.31.24.204", "172.31.24.205" ], "key": { "algo": "rsa", "size": 2048 }, "names": [{ "C": "CN", "ST": "BJ", "L": "BJ", "O": "k8s", "OU": "system" }] }
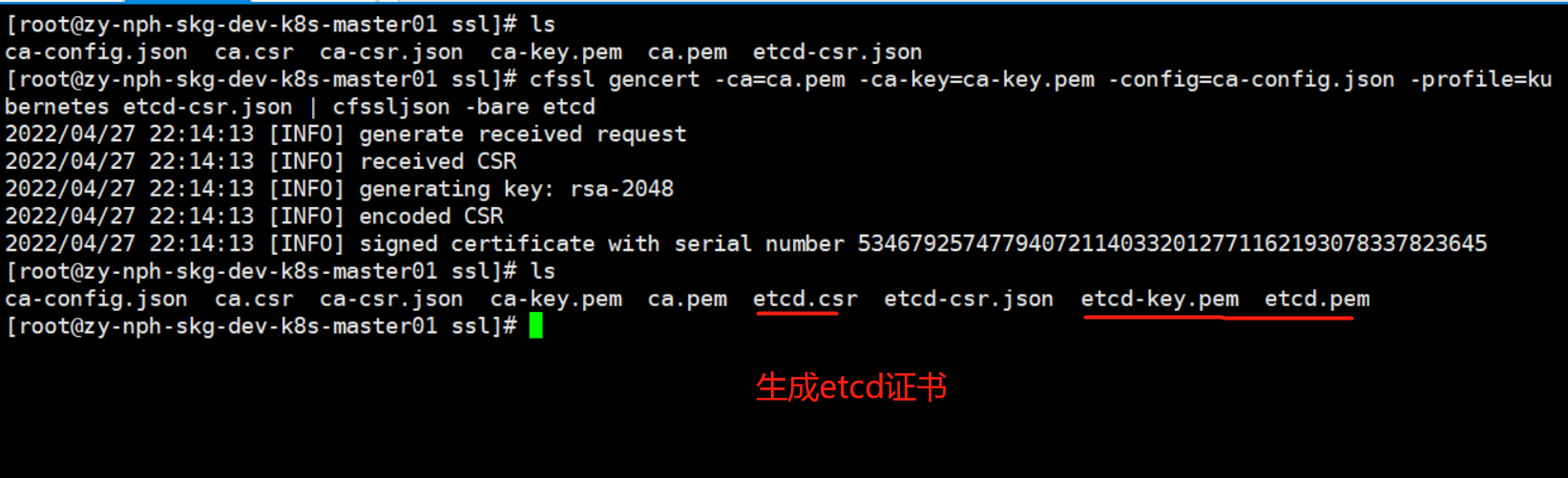
- 生成etcd证书
cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=kubernetes etcd-csr.json | cfssljson -bare etcd![]()
注解:
hosts 字段中 的IP 是 etcd 所有节点的 IP,可以预留几个,做扩容用。
二丶生成ectd自签名证书
- 下载etcd二进制包
下载地址:https://github.com/etcd-io/etcd/releases
cd /data/app/etcd
wget https://github.com/etcd-io/etcd/releases/download/v3.4.13/etcd-v3.4.13-linux-amd64.tar.gz - 部署 etcd 集群
tar xf etcd-v3.4.13-linux-amd64.tar.gz
mv etcd-v3.4.13-linux-amd64/etcd /usr/bin/
mv etcd-v3.4.13-linux-amd64/etcdctl /usr/bin/
rm -rf etcd-v3.4.13-linux-amd64![]()
-
创建etcd集群配置文件
cat > /data/app/etcd/etc/etcd.config.yml <<EOF name: 'etcd1' data-dir: /data/app/etcd/data wal-dir: /data/app/etcd/data/wal snapshot-count: 5000 heartbeat-interval: 100 election-timeout: 1000 quota-backend-bytes: 0 listen-peer-urls: 'https://172.31.170.15:2380' listen-client-urls: 'https://172.31.170.15:2379,http://127.0.0.1:2379' max-snapshots: 3 max-wals: 5 cors: initial-advertise-peer-urls: 'https://172.31.170.15:2380' advertise-client-urls: 'https://172.31.170.15:2379' discovery: discovery-fallback: 'proxy' discovery-proxy: discovery-srv: initial-cluster: 'etcd1=https://172.31.170.15:2380,etcd2=https://172.31.170.16:2380,etcd3=https://172.31.170.17:2380' initial-cluster-token: 'etcd-cluster' initial-cluster-state: 'new' strict-reconfig-check: false enable-v2: true enable-pprof: true proxy: 'off' proxy-failure-wait: 5000 proxy-refresh-interval: 30000 proxy-dial-timeout: 1000 proxy-write-timeout: 5000 proxy-read-timeout: 0 client-transport-security: cert-file: '/data/app/etcd/ssl/etcd.pem' key-file: '/data/app/etcd/ssl/etcd-key.pem' client-cert-auth: true trusted-ca-file: '/data/app/etcd/ssl/ca.pem' auto-tls: true peer-transport-security: cert-file: '/data/app/etcd/ssl/etcd.pem' key-file: '/data/app/etcd/ssl/etcd-key.pem' peer-client-cert-auth: true trusted-ca-file: '/data/app/etcd/ssl/ca.pem' auto-tls: true debug: false log-package-levels: log-outputs: [default] force-new-cluster: false EOF
注解:
ETCD_NAME:节点名称,集群中唯一
ETCD_DATA_DIR:数据目录
ETCD_LISTEN_PEER_URLS:集群通信监听地址
ETCD_LISTEN_CLIENT_URLS:客户端访问监听地址
ETCD_INITIAL_ADVERTISE_PEER_URLS:集群通告地址
ETCD_ADVERTISE_CLIENT_URLS:客户端通告地址
ETCD_INITIAL_CLUSTER:集群节点地址
ETCD_INITIAL_CLUSTER_TOKEN:集群 Token
ETCD_INITIAL_CLUSTER_STATE:加入集群的当前状态,new 是新集群,existing 表示加入已有集群 - 创建etcd服务启动脚本
cat > /usr/lib/systemd/system/etcd.service <<EOF [Unit] Description=Etcd Service Documentation=https://coreos.com/etcd/docs/latest/ After=network.target [Service] Type=notify ExecStart=/usr/bin/etcd --config-file=/data/app/etcd/etc/etcd.config.yml Restart=on-failure RestartSec=10 LimitNOFILE=65536 [Install] WantedBy=multi-user.target Alias=etcd3.service EOF
- 启动 etcd 集群
systemctl daemon-reload
systemctl enable etcd.service
systemctl start etcd.service - 查看 etcd 集群
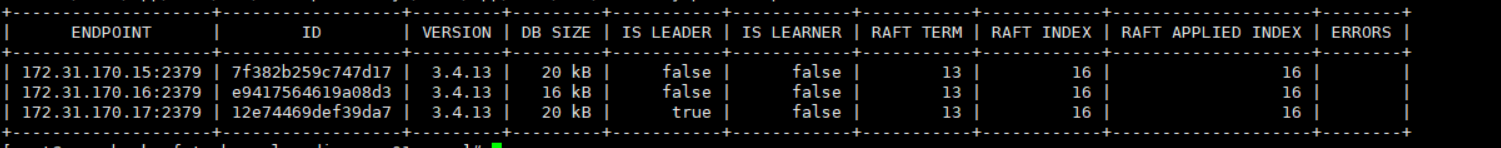
export ETCDCTL_API=3
etcdctl --endpoints="172.31.170.15:2379,172.31.170.16:2379,172.31.170.17:2379" --cacert=/data/app/etcd/ssl/ca.pem --cert=/data/app/etcd/ssl/etcd.pem --key=/data/app/etcd/ssl/etcd-key.pem endpoint status --write-out=table
etcdctl --endpoints="172.31.170.15:2379,172.31.170.16:2379,172.31.170.17:2379" --cacert=/data/app/etcd/ssl/ca.pem --cert=/data/app/etcd/ssl/etcd.pem --key=/data/app/etcd/ssl/etcd-key.pem endpoint health --write-out=table![]()




 浙公网安备 33010602011771号
浙公网安备 33010602011771号