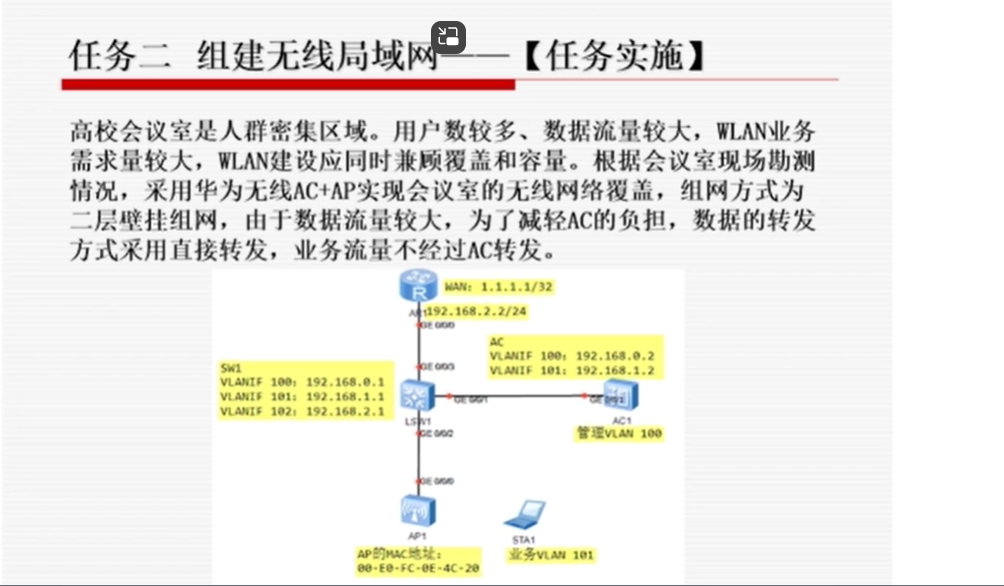
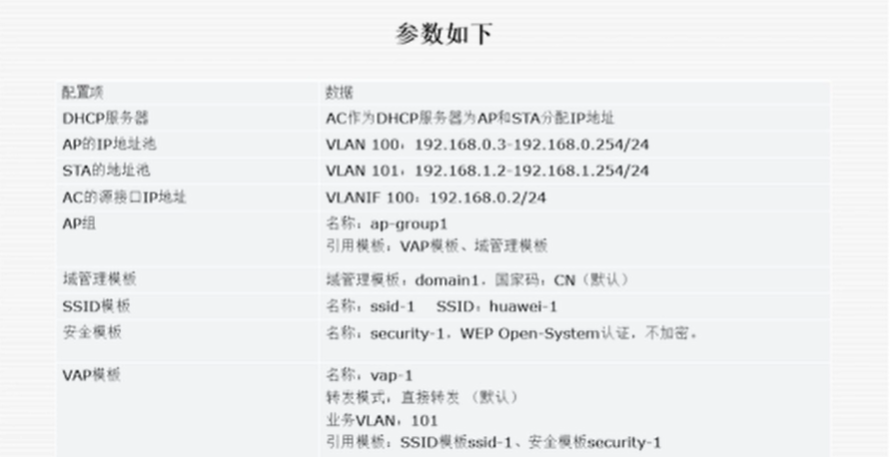
组件无线局域网
SW1:
[SW1]dis cu
#
sysname SW1
#
vlan batch 100 to 102
#
cluster enable
ntdp enable
ndp enable
#
drop illegal-mac alarm
#
diffserv domain default
#
drop-profile default
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password simple admin
local-user admin service-type http
#
interface Vlanif1
#
interface Vlanif100
ip address 192.168.0.1 255.255.255.0
#
interface Vlanif101
ip address 192.168.1.1 255.255.255.0
#
interface Vlanif102
ip address 192.168.2.1 255.255.255.0
#
interface MEth0/0/1
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 100 to 101
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk pvid vlan 100
port trunk allow-pass vlan 100 to 101
#
interface GigabitEthernet0/0/3
port link-type access
port default vlan 102
#
interface GigabitEthernet0/0/24
#
interface NULL0
#
ospf 1 router-id 2.2.2.2
area 0.0.0.0
network 192.168.2.0 0.0.0.255
network 192.168.1.0 0.0.0.255
#
user-interface con 0
user-interface vty 0 4
#
return
AC1:
<AC1>dis cu
#
sysname AC1
#
set memory-usage threshold 0
#
ssl renegotiation-rate 1
#
vlan batch 100 to 101
#
authentication-profile name default_authen_profile
authentication-profile name dot1x_authen_profile
authentication-profile name mac_authen_profile
authentication-profile name portal_authen_profile
authentication-profile name macportal_authen_profile
#
dhcp enable
#
diffserv domain default
#
radius-server template default
#
pki realm default
rsa local-key-pair default
enrollment self-signed
#
ike proposal default
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
free-rule-template name default_free_rule
#
portal-access-profile name portal_access_profile
#
ip pool sta
gateway-list 192.168.1.1
network 192.168.1.0 mask 255.255.255.0
excluded-ip-address 192.168.1.2
dns-list 114.114.114.114
#
aaa
authentication-scheme default
authentication-scheme radius
authentication-mode radius
authorization-scheme default
interface Vlanif100
ip address 192.168.0.2 255.255.255.0
dhcp select interface
#
interface Vlanif101
ip address 192.168.1.2 255.255.255.0
dhcp select global
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 100 to 101
#
interface GigabitEthernet0/0/2
#
interface GigabitEthernet0/0/3
#
interface GigabitEthernet0/0/4
interface NULL0
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
ssh server secure-algorithms cipher aes256_ctr aes128_ctr
ssh server key-exchange dh_group14_sha1
ssh client secure-algorithms cipher aes256_ctr aes128_ctr
ssh client secure-algorithms hmac sha2_256
ssh client key-exchange dh_group14_sha1
#
capwap source ip-address 192.168.0.2
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
protocol inbound all
user-interface vty 16 20
protocol inbound all
#
wlan
traffic-profile name default
security-profile name sec-1
security-profile name sex-1
security-profile name default
security-profile name default-wds
security-profile name default-mesh
ssid-profile name default
ssid-profile name huawei-1
vap-profile name vap-1
service-vlan vlan-id 101
ssid-profile huawei-1
security-profile sec-1
vap-profile name default
wds-profile name default
mesh-handover-profile name default
mesh-profile name default
regulatory-domain-profile name default
regulatory-domain-profile name domain1
air-scan-profile name default
rrm-profile name default
radio-2g-profile name default
radio-5g-profile name default
wids-spoof-profile name default
wids-profile name default
wireless-access-specification
ap-system-profile name default
port-link-profile name default
wired-port-profile name default
serial-profile name preset-enjoyor-toeap
ap-group name default
ap-group name ap-group1
regulatory-domain-profile domain1
radio 0
vap-profile vap-1 wlan 1
radio 1
vap-profile vap-1 wlan 1
radio 2
vap-profile vap-1 wlan 1
ap-id 1 type-id 69 ap-mac 00e0-fc87-1560 ap-sn 210235448310B0385D7F
ap-name AP1
ap-group ap-group1
provision-ap
#
dot1x-access-profile name dot1x_access_profile
#
mac-access-profile name mac_access_profile
#
return
AR1:
<AR1>dis current-configuration
[V200R003C00]
#
sysname AR1
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
#
interface GigabitEthernet0/0/0
ip address 192.168.2.2 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 1.1.1.1 255.255.255.255
#
ospf 1 router-id 1.1.1.1
area 0.0.0.0
network 1.1.1.1 0.0.0.0
network 192.168.2.0 0.0.0.255
#
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
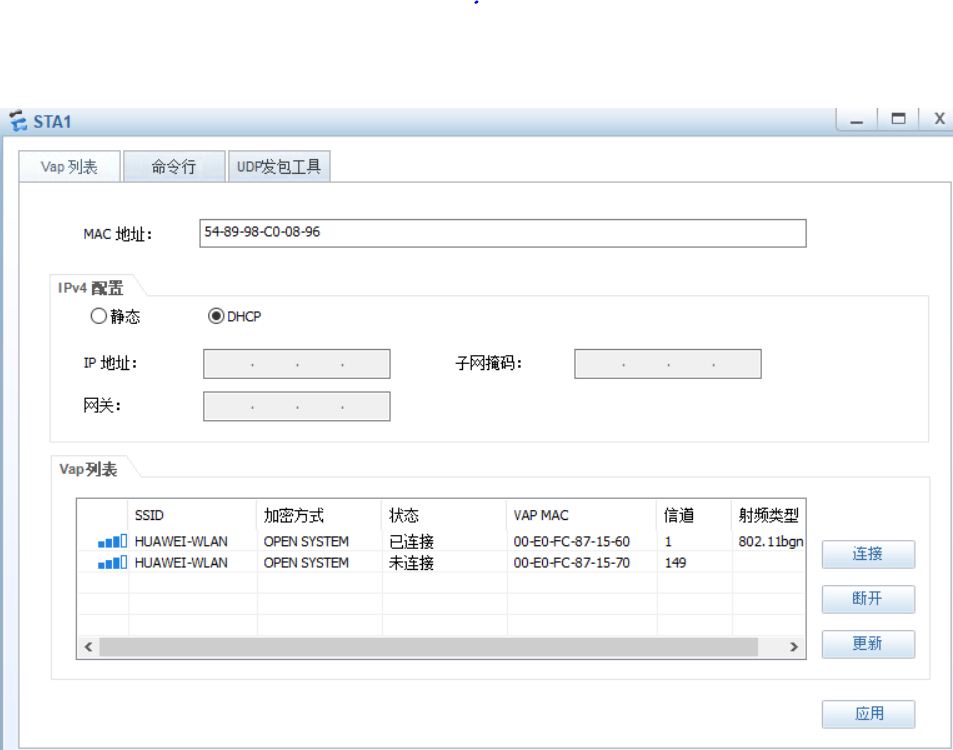
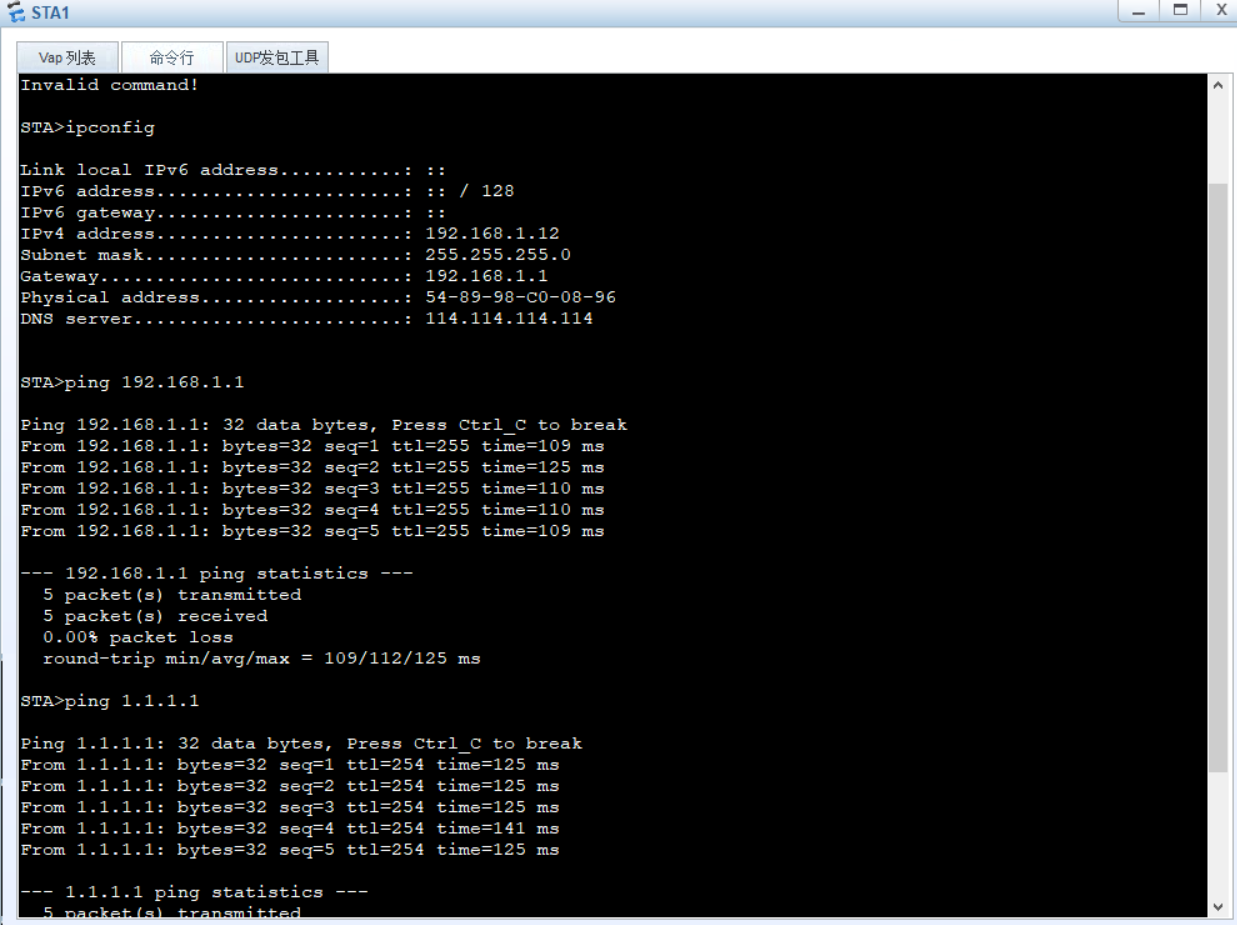
最终实验效果:
作者:AshJo
出处:https://www.cnblogs.com/ashjo009/
本文版权归作者所有,欢迎转载,但未经作者同意必须保留此段声明,且在文章页面明显位置给出原文连接,否则保留追究法律责任的权利。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号