安全加解密引擎基础(SKE AES)
1 基本概念
AES相关基本概念
明文P:没有经过加密的数据。
密钥K:用来加密明文的密码,在对称加密算法中,加密与解密的密钥是相同的。
AES加密函数:设AES加密函数为E,则 C = E(K, P),其中P为明文,K为密钥,C为密文。也就是说,把明文P和密钥K作为加密函数的参数输入,则加密函数E会输出密文C。
密文C:经加密函数处理后的数据。
AES解密函数:设AES解密函数为D,则 P = D(K, C),其中C为密文,K为密钥,P为明文。也就是说,把密文C和密钥K作为解密函数的参数输入,则解密函数会输出明文P。
IV - Initialization Vector
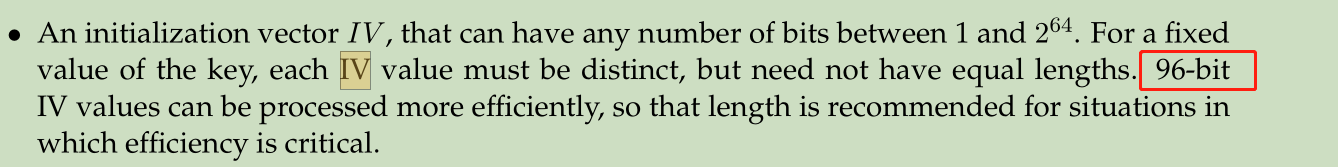

AAD - Additional authentication data.
附加的认证信息,可以简单理解为增强认证的元素。这个不是必须的,可以为空。

AES加密过程
AES加密过程是在一个4×4的字节矩阵上运作,这个矩阵又称为“状态(state)”,其初值就是一个明文区块(矩阵中一个元素大小就是明文区块中的一个Byte)。加密时,各轮AES加密循环(除最后一轮外)均包含4个步骤:
- AddRoundKey:矩阵中的每一个字节都与该次轮秘钥(round key)做XOR运算;每个子密钥由密钥生成方案产生。
- SubBytes:通过非线性的替换函数,用查找表的方式把每个字节替换成对应的字节。
- ShiftRows:将矩阵中的每个横列进行循环式移位。
- MixColumns:为了充分混合矩阵中各个直行的操作。这个步骤使用线性转换来混合每列的四个字节。
最后一个加密循环中省略MixColumns步骤,而以另一个AddRoundKey取代。
AES分组加密
AES为分组密码,分组密码也就是把明文分成一组一组的,每组长度相等,每次加密一组数据,直到加密完整个明文。在AES标准规范中,分组长度只能是128位,也就是说,每个分组为16个字节(每个字节8位)。密钥的长度可以使用128位、192位或256位。密钥的长度不同,推荐加密轮数也不同,如下表所示:
|
AES
|
密钥长度(32位比特字)
|
分组长度(32位比特字)
|
加密轮数
|
|
AES-128
|
4(128bit)
|
4(128bit)
|
10
|
|
AES-192
|
6(192bit)
|
4(128bit)
|
12
|
|
AES-256
|
8(256bit)
|
4(128bit)
|
14
|
分组加密工作模式
分组密码有五种工作体制:1.电码本模式(Electronic Codebook Book (ECB));2.密码分组链接模式(Cipher Block Chaining (CBC));3.计算器模式(Counter (CTR));4.密码反馈模式(Cipher FeedBack (CFB));5.输出反馈模式(Output FeedBack (OFB))。
在密码学中,分组密码操作模式是使用分组密码来提供诸如机密性或真实性的信息服务的算法。基于分组的对称密码算法比如DES/AES算法只是描述如何根据秘钥对一段固定长度(分组块)的数据进行加密,对于比较长的数据,分组密码工作模式描述了如何重复应用某种算法加密分组操作来安全地转换大于块的数据量。
简单的说就是,AES算法描述怎么加密一个数据块,分组密码工作模式决定了如果重复加密比较长的多个数据块。
ECB(Electronic Codebook, 电子密码本)模式是最简单的加密模式,明文消息被分成固定大小的块(分组),并且每个块被单独加密。
每个块的加密和解密都是独立的,且使用相同的方法进行加密,所以可以进行并行计算,但是这种方法一旦有一个块被破解,使用相同的方法可以解密所有的明文数据,安全性比较差。
适用于数据较少的情形,加密前需要把明文数据填充到块大小的整倍数。
CBC(Cipher Block Chaining, 密码块链)模式中每一个分组要先和前一个分组加密后的数据进行XOR异或操作,然后再进行加密。
这样每个密文块依赖该块之前的所有明文块,为了保持每条消息都具有唯一性,第一个数据块进行加密之前需要用初始化向量IV进行异或操作。
CBC模式是一种最常用的加密模式,它主要缺点是加密是连续的,不能并行处理,并且与ECB一样消息块必须填充到块大小的整倍数。
CFB(Cipher Feedback, 密码反馈)模式和CBC模式比较相似,前一个分组的密文加密后和当前分组的明文XOR异或操作生成当前分组的密文。CFB模式的解密和CBC模式的加密在流程上其实是非常相似的。
OFB(Output Feedback, 输出反馈)模式将分组密码转换为同步流密码,也就是说可以根据明文长度先独立生成相应长度的流密码。通过流程图可以看出,OFB和CFB非常相似,CFB是前一个分组的密文加密后XOR当前分组明文,OFB是前一个分组与前一个明文块异或之前的流密码XOR当前分组明文。由于异或操作的对称性,OFB模式的解密和加密完全一样的流程。
CTR(Counter, 计数器)模式与OFB模式一样,计数器模式将分组密码转换为流密码。它通过加密“计数器”的连续值来产生下一个密钥流块。
GCM( Galois/Counter Mode ) GCM中的G就是指GMAC,C就是指CTR。
GCM可以提供对消息的加密和完整性校验,另外,它还可以提供附加消息的完整性校验。在实际应用场景中,有些信息是我们不需要保密,但信息的接收者需要确认它的真实性的,例如源IP,源端口,目的IP,IV,等等。因此,我们可以将这一部分作为附加消息加入到MAC值的计算当中。
2 基于openssl进行加解密
AES的组合包括算法、秘钥宽度、模式。
openssl enc -aes-256-cbc -d -k 1234567890 -iv 1234567890 -in outfile -out replainfile openssl enc -aes-256-cbc -d -k 1234567890 -iv 1234567890 -in outfile -out replainfile
算法和模式的组合有:
aes-[128|192|256]-cbc 128/192/256 bit AES in CBC mode aes[128|192|256] Alias for aes-[128|192|256]-cbc aes-[128|192|256]-cfb 128/192/256 bit AES in 128 bit CFB mode aes-[128|192|256]-cfb1 128/192/256 bit AES in 1 bit CFB mode aes-[128|192|256]-cfb8 128/192/256 bit AES in 8 bit CFB mode aes-[128|192|256]-ctr 128/192/256 bit AES in CTR mode aes-[128|192|256]-ecb 128/192/256 bit AES in ECB mode aes-[128|192|256]-ofb 128/192/256 bit AES in OFB mode
3 PyCryptodome关于AES使用
借助PyCryptodome的AES进行不同模式的加解密。
#参考文档:https://blog.csdn.net/weixin_43790276/article/details/100063132 from Crypto.Cipher import AES import random import struct from binascii import b2a_hex, a2b_hex from base64 import b64decode, b64encode edge10_gcm_plain = [0x58, 0x99, 0xf1, 0x69, 0xaa, 0x8f, 0x33, 0x33, 0xfa, 0x35, 0x35, 0x79, 0x31, 0x3d, 0x7e, 0xb0, 0xc5, 0xae, 0xa6, 0x8b, 0x86, 0x42, 0x75, 0x58, 0x65, 0x80, 0x8b, 0xac, 0x59, 0xab, 0x99, 0x73] edge10_gcm_key = [0x12, 0x34, 0x56, 0x78, 0x12, 0x34, 0x56, 0x78, 0x12, 0x34, 0x56, 0x78, 0x12, 0x34, 0x56, 0x78, 0x12, 0x34, 0x56, 0x78, 0x12, 0x34, 0x56, 0x78, 0x12, 0x34, 0x56, 0x78, 0x12, 0x34, 0x56, 0x78] edge10_gcm_iv = [0x12, 0x34, 0x56, 0x78, 0x12, 0x34, 0x56, 0x78, 0x12, 0x34, 0x56, 0x78] #edge10_gcm_iv = [ord('a'), ord('l'), ord('@'), ord('I'), ord('n'), ord('t'), ord('e'), ord('l'), ord('l'), ord('i'), ord('f'), ord('!')] edge10_aad = [] def hex_to_array(array, list): print("unsigned char %s[] = {" % (array), end='') for i in range(int(len(list))): print("0x%x, "%(list[i]), end='') if (i + 1) % 32 == 0: print("") print("};") std_in = bytes([0x81,0x70,0x99,0x44,0xE0,0xCB,0x2E,0x1D,0xB5,0xB0,0xA4,0x77,0xD1,0xA8,0x53,0x9B, 0x0A,0x87,0x86,0xE3,0x4E,0xAA,0xED,0x99,0x30,0x3E,0xA6,0x97,0x55,0x95,0xB2,0x45, 0x4D,0x5D,0x7F,0x91,0xEB,0xBD,0x4A,0xCD,0x72,0x6C,0x0E,0x0E,0x5E,0x3E,0xB5,0x5E, 0xF6,0xB1,0x5A,0x13,0x8E,0x22,0x6E,0xCD,0x1B,0x23,0x5A,0xB5,0xBB,0x52,0x51,0xC1, 0x33,0x76,0xB2,0x64,0x48,0xA9,0xAC,0x1D,0xE8,0xBD,0x52,0x64,0x8C,0x0B,0x5F,0xFA, 0x94,0x44,0x86,0x82,0xE3,0xCB,0x4D,0xE9,0xCB,0x8A,0xE7,0xF4,0xBD,0x41,0x0E,0xD5, 0x02,0xB1,0x25,0x3A,0xD0,0x8B,0xB2,0x79,0x69,0xB5,0xF0,0x2B,0x10,0x02,0x9D,0x67, 0xD0,0x7E,0x18,0x64,0xD9,0x4D,0x4F,0xCA,0x20,0x81,0x51,0xE2,0x6F,0x5F,0xEE,0x26,]) std_key = bytes([0xE0,0x70,0x99,0xF1,0xBF,0xAF,0xFD,0x7F,0x24,0x0C,0xD7,0x90,0xCA,0x4F,0xE1,0x34, 0xB4,0x42,0x60,0xE1,0x56,0x8D,0x9E,0x85,0x0A,0x0C,0x95,0x37,0x44,0x02,0xDE,0x28,]) std_iv = bytes([0xC7,0x2B,0x65,0x91,0xA0,0xD7,0xDE,0x8F,0x6B,0x40,0x72,0x33,0xAD,0x35,0x81,0xD6]) std_ecb_out = bytes([0xBD, 0xE8, 0x9A, 0xF4, 0xC0, 0x9D, 0xE4, 0x51, 0x34, 0x04, 0x7B, 0x45, 0xF6, 0x58, 0xB2, 0x51, 0x75, 0x71, 0x45, 0x7D, 0xAF, 0xA0, 0x81, 0xCF, 0x54, 0x68, 0xA9, 0x35, 0x06, 0xD9, 0x6C, 0xF9, 0x17, 0x85, 0x12, 0x5F, 0xA0, 0xDE, 0x5B, 0xF0, 0x8C, 0x56, 0x24, 0xB8, 0x29, 0x4F, 0xD7, 0x56, 0xEC, 0x0D, 0x55, 0x96, 0xF4, 0xF4, 0xC5, 0xFC, 0x2A, 0x86, 0x78, 0x8A, 0x1C, 0x5D, 0x74, 0xFF, 0x27, 0x2C, 0x15, 0xA2, 0xDE, 0x13, 0x54, 0x69, 0x89, 0x49, 0x9F, 0x79, 0xEE, 0xED, 0x6B, 0xE2, 0x64, 0x52, 0xEE, 0x96, 0x69, 0x8C, 0x49, 0x76, 0xCA, 0x9B, 0x62, 0x26, 0xC9, 0xCF, 0x61, 0x65, 0x5E, 0x3B, 0x8B, 0x0C, 0xE4, 0x90, 0xAA, 0x80, 0xD4, 0x78, 0x8C, 0x56, 0x3E, 0x74, 0xB3, 0x83, 0x83, 0x61, 0xB4, 0x9F, 0xE6, 0x0C, 0x69, 0xDE, 0x55, 0x3D, 0xB7, 0xA1, 0xA9, 0xE7, 0xB7, 0x89,]) std_cbc_out = bytes([0x7C, 0xA4, 0x8E, 0x82, 0x99, 0xFC, 0x5A, 0xD3, 0xE9, 0x08, 0xB7, 0x65, 0xE3, 0x0D, 0x7A, 0x3B, 0x63, 0xE3, 0x82, 0xF6, 0x46, 0x23, 0xAC, 0xE0, 0x41, 0xC4, 0x0B, 0x29, 0xF5, 0x92, 0x59, 0x2F, 0x96, 0xAD, 0xBB, 0xA5, 0x58, 0x52, 0x49, 0x32, 0x59, 0x25, 0x20, 0xBA, 0x17, 0xDB, 0x52, 0xE9, 0x42, 0x32, 0x64, 0x38, 0x86, 0xF2, 0x02, 0xA9, 0x6B, 0xA2, 0x58, 0x76, 0xC6, 0x30, 0x2D, 0xFC, 0xE9, 0x93, 0x46, 0x7F, 0xB1, 0x38, 0xE2, 0x93, 0x98, 0xA7, 0x30, 0x61, 0xEC, 0xCF, 0xBE, 0x5A, 0xA1, 0xAE, 0x0E, 0xDC, 0x93, 0x7C, 0xCA, 0x4E, 0x0C, 0x7A, 0x60, 0x87, 0x14, 0x82, 0x9D, 0x4E, 0x7E, 0x47, 0x16, 0x77, 0x06, 0xA1, 0x8F, 0xA7, 0x45, 0x59, 0x16, 0x1A, 0x00, 0xB4, 0x41, 0x29, 0xA9, 0x5C, 0x3E, 0x41, 0x65, 0xB8, 0xC9, 0x24, 0xAB, 0xE0, 0x4A, 0x4A, 0x2D, 0xC2, 0xB3, 0x2D,]) std_cfb_out = bytes([0xBF, 0xDE, 0x14, 0xD0, 0xE9, 0x92, 0xFA, 0x6B, 0xAF, 0x4B, 0xF1, 0x17, 0xA7, 0x7C, 0x16, 0x6D, 0xAD, 0x38, 0x53, 0xFA, 0xFF, 0x38, 0xF0, 0xF2, 0xD1, 0xD1, 0x33, 0x7B, 0x56, 0xE5, 0xA1, 0x1B, 0xF1, 0x11, 0xAB, 0x91, 0xDA, 0x05, 0xBE, 0x47, 0xEE, 0xFD, 0x3D, 0x22, 0xA5, 0x49, 0x61, 0x9A, 0x27, 0x19, 0xEF, 0xEA, 0xEE, 0x3A, 0x36, 0xD9, 0xC8, 0x96, 0xA8, 0xD4, 0x3B, 0xBE, 0x92, 0xA0, 0x03, 0x84, 0x20, 0x7E, 0x45, 0x1C, 0x42, 0x95, 0x86, 0xB4, 0x82, 0x71, 0x65, 0xFB, 0xC8, 0x60, 0x08, 0x9C, 0xAB, 0x2E, 0x24, 0xB1, 0x64, 0x01, 0x53, 0x10, 0x11, 0x0C, 0x1C, 0xF1, 0x00, 0x21, 0x23, 0xA8, 0x8C, 0xC7, 0xD6, 0x78, 0xE3, 0xAE, 0xEA, 0x3B, 0xE8, 0xA1, 0x6B, 0x58, 0x38, 0x49, 0x01, 0x5B, 0xAC, 0xA4, 0xF1, 0x6D, 0x93, 0x96, 0xAA, 0x12, 0x54, 0x82, 0x0B, 0x05, 0xB7, 0x8F,]) std_ofb_out = bytes([0xBF, 0xDE, 0x14, 0xD0, 0xE9, 0x92, 0xFA, 0x6B, 0xAF, 0x4B, 0xF1, 0x17, 0xA7, 0x7C, 0x16, 0x6D, 0x2A, 0xE0, 0x78, 0x06, 0x68, 0x92, 0xD7, 0xF5, 0x2A, 0x3D, 0x82, 0x43, 0x5A, 0xEE, 0xA9, 0xD6, 0x07, 0x68, 0x8A, 0x00, 0x2A, 0xAF, 0x45, 0x52, 0xF9, 0x29, 0x65, 0x43, 0xCF, 0xCA, 0xD6, 0x5D, 0xEB, 0xF1, 0xB0, 0x5D, 0x1D, 0xC7, 0xDA, 0x6B, 0x48, 0x14, 0x36, 0xA1, 0x04, 0x70, 0x60, 0xA0, 0xD4, 0xBD, 0xAD, 0x40, 0x77, 0x6E, 0x0D, 0xBA, 0x87, 0x06, 0x9F, 0x50, 0x2D, 0x95, 0x27, 0x0A, 0x39, 0x51, 0x44, 0xFB, 0x58, 0x10, 0x6F, 0x48, 0xC0, 0xB1, 0x09, 0xD9, 0x72, 0x66, 0x35, 0xF8, 0x8F, 0xD4, 0xAB, 0xB0, 0x4C, 0x6E, 0xFE, 0xF1, 0x2B, 0x97, 0x8A, 0xC3, 0x64, 0xED, 0xA9, 0x7C, 0xA4, 0x73, 0x0C, 0xA6, 0xBF, 0x3E, 0x41, 0xB7, 0xA9, 0x6F, 0xD3, 0x2D, 0xC9, 0x56, 0xCA, 0x39,]) std_ctr_out = bytes([0xBF, 0xDE, 0x14, 0xD0, 0xE9, 0x92, 0xFA, 0x6B, 0xAF, 0x4B, 0xF1, 0x17, 0xA7, 0x7C, 0x16, 0x6D, 0x9B, 0x34, 0xDC, 0xCD, 0x00, 0x58, 0x0A, 0xBB, 0xEB, 0x92, 0x9A, 0x67, 0x8F, 0xE9, 0xC4, 0x9F, 0x50, 0x47, 0x57, 0x3D, 0x2A, 0xBE, 0xE8, 0x71, 0x17, 0x8B, 0x39, 0x0D, 0xC0, 0x11, 0xA6, 0x10, 0x71, 0x15, 0x64, 0xB4, 0xFF, 0xA5, 0xAA, 0x95, 0xFE, 0xFA, 0x2B, 0xBE, 0x3C, 0xB9, 0xA2, 0x3D, 0xA2, 0x69, 0x0F, 0xA2, 0x56, 0x59, 0x7E, 0x01, 0x45, 0x43, 0x2F, 0xAC, 0xB9, 0xCB, 0xAB, 0xA2, 0x91, 0xC5, 0x93, 0xF9, 0xC4, 0x72, 0xEF, 0x41, 0x16, 0x3B, 0xC7, 0x19, 0x50, 0x5C, 0xC7, 0xD3, 0x43, 0x67, 0xDB, 0xAD, 0x8F, 0xA4, 0x3E, 0xFD, 0x9E, 0x6E, 0xEB, 0xEF, 0x09, 0xE4, 0x9E, 0x14, 0x0F, 0xD2, 0x36, 0x2A, 0x74, 0xF5, 0xCE, 0x6C, 0xC2, 0x66, 0xEA, 0x71, 0x1B, 0x57, 0xED, 0xB7,]) std_xts_out = bytes([0x4E, 0x2B, 0xA3, 0xAD, 0xA1, 0xBC, 0x79, 0xAF, 0x26, 0x04, 0xFC, 0x2B, 0x7D, 0x71, 0xC8, 0xCB, 0x71, 0xFB, 0x82, 0x3E, 0x0A, 0x6B, 0x34, 0x31, 0x77, 0x37, 0x05, 0xD9, 0xAD, 0x86, 0x0F, 0x29, 0xFE, 0x7A, 0x65, 0x5A, 0xCD, 0x43, 0x14, 0xDD, 0x46, 0x74, 0x6C, 0xEF, 0x79, 0xFA, 0xAE, 0x71, 0x38, 0x8C, 0x42, 0x5F, 0xEF, 0xEF, 0x23, 0x61, 0x33, 0x79, 0x78, 0xB4, 0x68, 0xC8, 0x54, 0x99, 0x5A, 0x04, 0xE1, 0x99, 0x02, 0x3C, 0x15, 0x56, 0x86, 0x42, 0x2E, 0x92, 0x66, 0x1E, 0xB9, 0x90, 0x5C, 0xBF, 0x21, 0x4B, 0x56, 0x8D, 0x34, 0x71, 0x5C, 0x9E, 0x16, 0xDE, 0xE2, 0x99, 0x52, 0xC9, 0x52, 0xEA, 0xF7, 0x5B, 0x90, 0x6D, 0x20, 0xD8, 0x29, 0xD6, 0x1D, 0x28, 0xB8, 0x1D, 0xBB, 0x76, 0x93, 0x1D, 0x2C, 0xA7, 0x4C, 0xD0, 0x71, 0xB6, 0x8F, 0x7D, 0xBB, 0xE5, 0x48, 0xFC, 0x96, 0x6A,]) std_gcm_plain = bytes([0xd9,0x31,0x32,0x25,0xf8,0x84,0x06,0xe5,0xa5,0x59,0x09,0xc5,0xaf,0xf5,0x26,0x9a, 0x86,0xa7,0xa9,0x53,0x15,0x34,0xf7,0xda,0x2e,0x4c,0x30,0x3d,0x8a,0x31,0x8a,0x72, 0x1c,0x3c,0x0c,0x95,0x95,0x68,0x09,0x53,0x2f,0xcf,0x0e,0x24,0x49,0xa6,0xb5,0x25, 0xb1,0x6a,0xed,0xf5,0xaa,0x0d,0xe6,0x57,0xba,0x63,0x7b,0x39,0x1a,0xaf,0xd2,0x55, 0xB4,0xD1,0x4B,0x82,0xE0,0x03,0xCA,0x48,0x4C,0x28,0x1B,0x5D,0x4D,0x9B,0xBC,0x29, 0xF3,0x61,0xD1,0x61,0x79,0x36,0xF5,0x3E,0x37,0xEF,0x97,0x73,0xB3,0x31,0x8C,0x8C, 0x4E,0xCB,0x31,0x9E,0x26,0x4D,0xF6,0x29,0xBE,0x8C,0x41,0x1B,0xF5,0xC4,0xBE,0x45, 0x03,0x62,0x56,0xE4,0xD8,0x2F,0x64,0x5A,0x4D,0x0A,0xDF,0x44,0x55,0xB1,0x31,0xA1, 0x7B,0xC6,0x74,0x21,0x86,0xC4,0x2E,0x28,0x3A,0xA5,0xBA,0xD5,0x4A,0x18,0xEC,0x14, 0x3B,0xAF,0x1E,0x6C,0x85,0x7F,0x32,0xEC,0x5D,0x92,0xB1,0x96,0xCF,0x7E,0x31,0x13, 0x71,0xBD,0xA2,0xEA,0xE8,0xDF,0xD0,0x82,0xCF,0xEB,0x58,0x3A,0x41,0xCF,0xCE,0xAA, 0x78,0x0F,0xD1,0x7F,0xBA,0xE9,0x31,0xDE,0xF7,0x17,0xB4,0x5B,0xB8,0x6F,0x15,0xD6, 0x01,0xF5,0x44,0xFB,0xCC,0xB2,0x43,0x5F,0x80,0xE8,0x9D,0x6F,0x21,0x87,0x06,0x37, 0x86,0x01,0xEA,0x99,0x15,0x6E,0x8A,0x88,0xAA,0xED,0x8C,0xE6,0x14,0x2F,0xB6,0x65, 0xB6,0xEE,0xEB,0x6F,0x06,0xEA,0x9D,0x45,0xB0,0x14,0x04,0x00,0x59,0xB4,0x26,0x77, 0x32,0xD7,0x33,0xB2,0xF0,0x92,0xE8,0x5E,0x40,0xF2,0x21,0x04,0xC4,0xF0,0x9C,0x80,]) std_gcm_key = bytes([0xfe,0xff,0xe9,0x92,0x86,0x65,0x73,0x1c,0x6d,0x6a,0x8f,0x94,0x67,0x30,0x83,0x08, 0xfe,0xff,0xe9,0x92,0x86,0x65,0x73,0x1c,0x6d,0x6a,0x8f,0x94,0x67,0x30,0x83,0x08]) std_gcm_iv = bytes([0xca,0xfe,0xba,0xbe,0xfa,0xce,0xdb,0xad,0xde,0xca,0xf8,0x88]) std_aad = bytes([0xfe,0xed,0xfa,0xce,0xde,0xad,0xbe,0xef,0xfe,0xed,0xfa,0xce,0xde,0xad,0xbe,0xef, 0xab,0xad,0xda,0xd2,0x7C,0xA4,0x8E,0x82,0x99,0xFC,0x5A,0xD3,0xE9,0x08,0xB7,0x65, 0x1B,]) std_gcm_out = bytes([0x52,0x2D,0xC1,0xF0,0x99,0x56,0x7D,0x07,0xF4,0x7F,0x37,0xA3,0x2A,0x84,0x42,0x7D, 0x64,0x3A,0x8C,0xDC,0xBF,0xE5,0xC0,0xC9,0x75,0x98,0xA2,0xBD,0x25,0x55,0xD1,0xAA, 0x8C,0xB0,0x8E,0x48,0x59,0x0D,0xBB,0x3D,0xA7,0xB0,0x8B,0x10,0x56,0x82,0x88,0x38, 0xC5,0xF6,0x1E,0x63,0x93,0xBA,0x7A,0x0A,0xBC,0xC9,0xF6,0x62,0x89,0x80,0x15,0xAD, 0xD0,0x7E,0x30,0xD4,0x00,0xEE,0xB7,0x02,0x04,0xBD,0x95,0x40,0xBB,0x63,0x5C,0xC6, 0x2F,0xFF,0x3F,0xD5,0x92,0x20,0x5C,0x37,0x6C,0x98,0x8A,0xA5,0xEB,0xF5,0x95,0x79, 0x29,0x30,0xA5,0x16,0x3C,0x39,0x65,0x5A,0xEB,0xD3,0x9C,0x66,0x85,0xF3,0x73,0xE8, 0x83,0xEC,0x3F,0x5B,0xB6,0xE4,0x60,0x95,0xE3,0x39,0xF4,0xEB,0x40,0x38,0xD5,0xF2, 0xC7,0x5F,0x45,0xC0,0x62,0x20,0x03,0x0B,0xB0,0x4B,0x75,0x6B,0x45,0x30,0xA0,0x4B, 0x71,0xFE,0xD7,0x0E,0x6A,0xAB,0xC8,0xD9,0x0A,0x84,0xC1,0x37,0xF6,0x86,0xBF,0x6A, 0x8D,0x4C,0xD9,0x7E,0x70,0xD9,0x4B,0xB5,0x9E,0xFE,0xFB,0x4A,0x87,0x33,0xB3,0x21, 0x35,0x50,0xC8,0x2D,0x14,0xB3,0x4C,0xCF,0x07,0xFB,0xA9,0xFE,0xC4,0x92,0xD2,0x04, 0xD9,0xE9,0x61,0xEF,0x6A,0xB5,0x4F,0xFD,0x2D,0x9A,0x16,0xDF,0xC7,0x06,0xEC,0x72, 0x11,0xCF,0x32,0x74,0x4D,0x6D,0xAC,0x7F,0xE0,0x43,0x31,0x50,0xDA,0x5C,0xCC,0xFF, 0x03,0x10,0xFE,0x8B,0xA5,0x2C,0xD4,0xBC,0x85,0xF9,0x78,0xC9,0xA7,0x58,0x7C,0x26, 0xD5,0x3B,0x08,0xCC,0xEE,0x10,0x75,0xD0,0xC0,0x9E,0xF4,0xFB,0x80,0x45,0xA8,0xCD]) def gen_aes_256_gcm_for_osr(): #type(struct.pack('B', random.randint(0, 255))) #for i in range(512): # edge10_gcm_plain.append(random.randint(0, 255)) #for i in range(32): # edge10_gcm_key.append(random.randint(0, 255)) mode = AES.MODE_GCM cryptor = AES.new(bytes(edge10_gcm_key), mode, bytes(edge10_gcm_iv)) cipher_list = list(cryptor.encrypt(bytes(edge10_gcm_plain))) cryptor = AES.new(bytes(edge10_gcm_key), mode, bytes(edge10_gcm_iv)) plain_list = list(cryptor.decrypt(bytes(cipher_list))) if edge10_gcm_plain == plain_list: print("Encrypt/Decrypt successful.") hex_to_array('edge10_gcm_plain', edge10_gcm_plain) hex_to_array('edge10_aes256_gcm_cipher', cipher_list) hex_to_array('edge10_gcm_key', edge10_gcm_key) hex_to_array('edge10_gcm_iv', edge10_gcm_iv) def aes_test(key, mode, input, std_cipher): aes = AES.new(key, mode) cipher_bytes = aes.encrypt(input) if cipher_bytes == std_cipher: print("Encrypt successful.") aes = AES.new(key, mode) replain_bytes = aes.decrypt(cipher_bytes) if input == replain_bytes: print("Decrypt successful.") print("PlainText:", input.hex()) print("CipherText:", cipher_bytes.hex()) print("ReplainText:", replain_bytes.hex()) def aes_test_iv(key, mode, input, std_cipher, iv): aes = AES.new(key, mode, iv) cipher_bytes = aes.encrypt(input) if cipher_bytes == std_cipher: print("Encrypt successful.") aes = AES.new(key, mode, iv) replain_bytes = aes.decrypt(cipher_bytes) if input == replain_bytes: print("Decrypt successful.") print("PlainText:", input.hex()) print("CipherText:", cipher_bytes.hex()) print("ReplainText:", replain_bytes.hex()) if __name__ == '__main__': #gen_aes_256_gcm_for_osr() aes_test(std_key, AES.MODE_ECB, std_in, std_ecb_out) aes_test_iv(std_key, AES.MODE_CBC, std_in, std_cbc_out, std_iv) aes_test_iv(std_key, AES.MODE_CFB, std_in, std_cfb_out, std_iv) aes_test_iv(std_key, AES.MODE_OFB, std_in, std_ofb_out, std_iv) #aes_test_iv(std_key, AES.MODE_CTR, std_in, std_ctr_out, std_iv) aes_test_iv(std_gcm_key, AES.MODE_GCM, std_gcm_plain, std_gcm_out, std_gcm_iv)
联系方式:arnoldlu@qq.com



 浙公网安备 33010602011771号
浙公网安备 33010602011771号