Centos7 k8s v1.5.2二进制部署安装-基本准备
一、实验
1、实验架构图
2、实验架构图
3、安装方式
Minkube 单节点微型k8s(仅供学习、预览使用)
二进制安装部署(生产首选,新手推荐)
使用kubeadmin进行部署,k8s的部署工具,跑在k8s里(相对简单,熟手推荐)
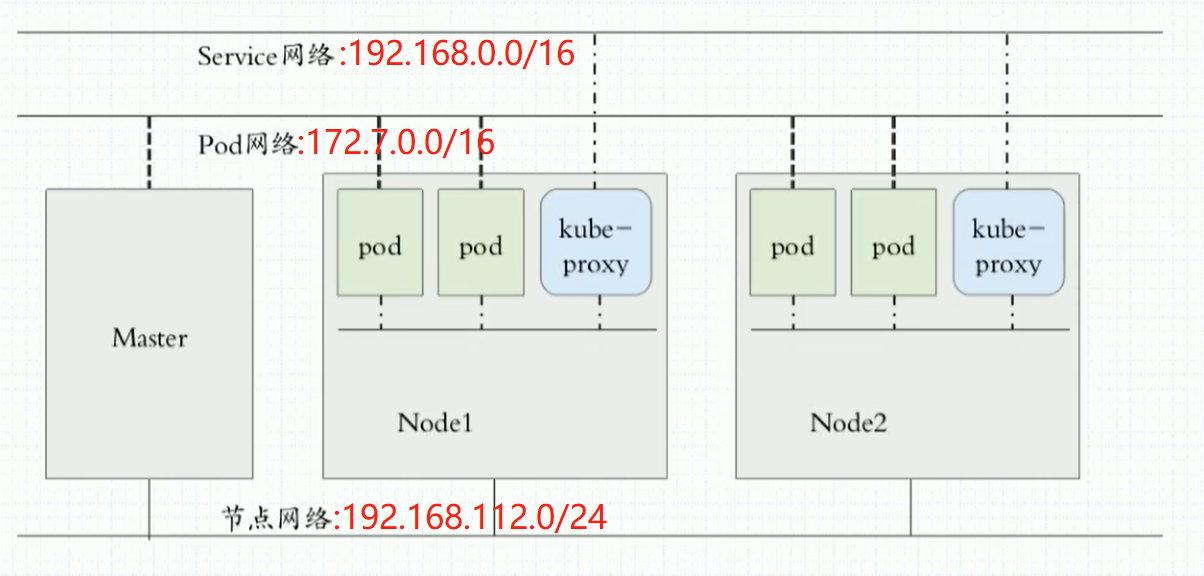
4、本实验使用的三条网络规划
二、部署k8s(所有主机上)
1、准备工作(所有主机上)
1)关闭防火墙
systemctl stop firewalld
备注:必须关闭
2)关闭selinux
setenforce 0 临时关闭 sed -i 's/SELINUX=enforcing/SELINUX=disabled/g' /etc/selinux/config 永久关闭
3)关闭swap
swapoff -a && sysctl -w vm.swappiness=0 临时关闭
free -h 可以通过这个命令查看swap是否关闭了
4)在各节点中关闭自动挂载swap交换分区
[root@ k8s-masters01 ~]#vim /etc/fstab 把swap注释掉: 永久关闭
#UUID=a11cdd2a-eeed-4ed7-af6b-779094652766 swap swap defaults 0 0
2、安装源(所有主机上)
yum install epel-release -y
yum install wget net-tools telnet tree nmap sysstat lrzsz dos2unix bind-utils -y
3、安装bind9软件(dns服务器20)
yum install -y bind
4、修改配置文件(dns服务器20)
vim /etc/named.conf
listen-on port 53 { 192.168.112.20; }; #将127.0.0.1修改为当前主机IP
//listen-on-v6 port 53 { ::1; };
allow-query { any; }; #为哪些服务器提供解析服务
forwarders { 192.168.112.1; }; #用来指定上一层DNS地址,一般指定网关,确保服务能够访问公网
recursion yes;
dnssec-enable no; # 是否支持DNSSEC开关 PS:dnssec作用:1.为DNS数据提供来源验证 2.为数据提供完整性性验证 3.为查询提供否定存在验证
dnssec-validation no; #是否进行DNSSEC确认开关
5、检查配置文件(dns服务器20)
named-checkconf
6、修改区域配置文件(dns服务器20)
vim /etc/named.rfc1912.zones zone "host.com" IN { type master; file "host.com.zone"; allow-update { 192.168.112.20; }; }; zone "od.com" IN { type master; file "od.com.zone"; allow-update { 192.168.112.20; }; };
7、配置区域数据文件(dns服务器20)
vim /var/named/host.com.zone $ORIGIN host.com. $TTL 600 ; 10 minutes @ IN SOA dns.host.com. dnsadmin.host.com. ( 2021020701 ; serial 10800 ; refresh (3 hours) 900 ; retry (15 minutes) 604800 ; expire (1 week) 86400 ; minimum (1 day) ) NS dns.host.com. $TTL 60 ; minute dns A 192.168.112.20 k8s-nginx-proxy1 A 192.168.112.20 k8s-nginx-proxy2 A 192.168.112.21 kubectl1 A 192.168.112.22 kubectl2 A 192.168.112.23 operations A 192.168.112.24 vim /var/named/od.com.zone $ORIGIN od.com. $TTL 600 ; 10 minutes @ IN SOA dnsod.com. dnsadmin.od.com. ( 2021020701 ; serial 10800 ; refresh (3 hours) 900 ; retry (15 minutes) 604800 ; expire (1 week) 86400 ; minimum (1 day) ) NS dns.host.com. $TTL 60 ; minute dns A 192.168.112.20 harbor A 192.168.112.24
8、启动服务(dns服务器20)
systemctl start named systemctl enable named dig -t A k8s-nginx-proxy1.host.com @192.168.112.20 +short
9、客户端配置(所有主机)
修改网卡dns为dns服务器
vim /etc/resolv.conf search host.com nameserver 10.4.7.11
10、修改网卡配置:PS:如果网卡指定了DNS1配置(所有主机)
vim /etc/sysconfig/network-scripts/ifcfg-ens192 DNS1=192.168.112.20
三、签发证书(在运维主机上操作)
1、、在运维节点中安装证书生成工具cfssl:
cd /usr/bin wget https://pkg.cfssl.org/R1.2/cfssl_linux-amd64 -O /usr/bin/cfssl wget https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64 -O /usr/bin/cfssl-json wget https://pkg.cfssl.org/R1.2/cfssl-certinfo_linux-amd64 -O /usr/bin/cfssl-certinfo chmod +x /usr/bin/cfssl*
2、查看验证
which cfssl which cfssl-json which cfssl-certinfo
3、创建自签证书目录
mkdir /opt/certs
cd /opt/certs
4、创建根证书
vi /opt/certs/ca-csr.json { "CN": "OldboyEdu", "hosts":[ ], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "L": "Beijing", "ST": "Beijing" } ], "ca":{ "expiry": "175200h" } }
CN:Common Name,浏览器使用该字段验证网站是否合法,一般写的是域名。非常重要。浏览器使用该字段验证网站是否合法
C:Country,国家
ST:State ,州,省
L:Locality,地区,城市
O:Organization Name:组织名称,公司名称
OU:Organization Unit Name 组织单位名称,公司部门
expiry:过期时间,如果使用kubeadmin安装,默认证书有效期是1年,我们这里手动部署为20年,这里如果证书失效,会导致整个k8s集群瘫痪。
生成证书:
cfssl gencert -initca ca-csr.json | cfssl-json -bare ca 做成承载式证书
四、部署docker环境
1、安装docker(在22、23、24上操作)
方法一: curl -fsSL https://get.docker.com | bash -s docker --mirror Aliyun 方法二: 1)安装必要的系统工具 yum install –y yum-utils device-mapper-persistent-data lvm2 2)添加docker的yum yum-config-manager --add-repo http://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repo 3)更新yum缓存 yum makecache fas yum makecache fast 4)安装docker-ce yum -y install docker-ce
2、设置docker国内镜像加速
sudo mkdir -p /etc/docker /data/docker sudo tee /etc/docker/daemon.json <<-'EOF' { "graph": "/data/docker", "storage-driver": "overlay2", "insecure-registries": ["registry.access.redhat.com","quay.io","harbor.od.com"], "registry-mirrors": ["https://blcknu57.mirror.aliyuncs.com"], "bip": "172.7.22.1/24", "exec-opts": ["native.cgroupdriver=systemd"], "live-restore": true } EOF
bip:和你规划的IP地址有关,每台需自行修改
3、启动docker并设置成后台启动
systemctl restart docker && systemctl enable docker
4、安装本地仓库(docker私有仓库服务器上)
harbor私有仓库下载地址:https://github.com/goharbor/harbor/releases/tag/ wget https://github.com/goharbor/harbor/releases/download/v1.9.2/harbor-offline-installer-v1.9.2.tgz tar -zxf harbor-offline-installer-v1.9.2.tgz -C /opt/ cd /opt/ mv harbor harbor-1.9.2 ln -s /opt/harbor-1.9.2 /opt/harbor #方便版本管理 编辑harbor配置文件: vim /opt/harbor/harbor.yml hostname: harbor.od.com #这里添加的是我们开始在hdss7-11的自建dns上添加的域名解析 port: 180 #避免和nginx端口冲突 data_volume: /data/harbor location: /data/harbor/logs 创建数据目录和日志目录 mkdir -p /data/harbor/logs
5、接下来安装docker-compose
Docker Compose是 docker 提供的一个命令行工具,用来定义和运行由多个容器组成的应用。使用 compose,我们可以通过 YAML 文件声明式的定义应用程序的各个服务,并由单个命令完成应用的创建和启动。
yum install docker-compose -y #根据网络情况不同,可能需要一些时间 执行harbor脚本: sh /opt/harbor/install.sh #根据网络情况不同,可能需要一些时间
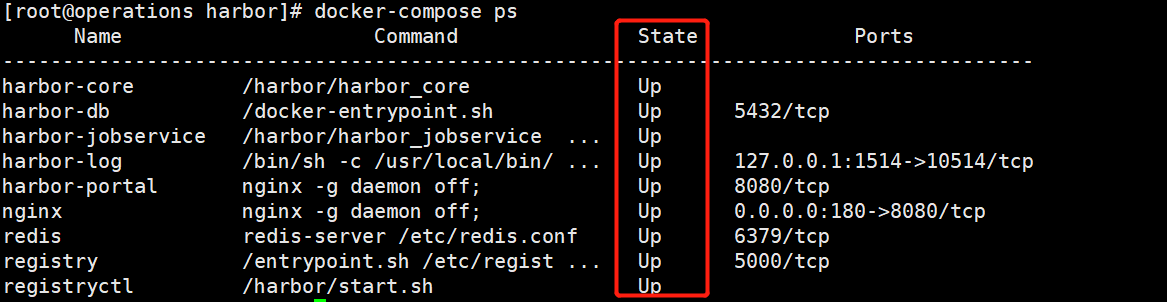
cd /opt/harbor
docker-compose ps
6、安装nginx
yum install nginx -y #可是直接yum,也可以安装源码安装 编辑nginx配置文件: vi /etc/nginx/conf.d/harbor.od.com.conf 反代harbor: server { listen 80; server_name harbor.od.com; client_max_body_size 1000m; location / { proxy_pass http://127.0.0.1:180; } } 启动nginx并设置开机启动: systemctl start nginx systemctl enable nginx 试着访问harbor,使用宿主机浏览器打开harbor.od.com,如果访问不了,检查dns是否是10.4.7.11,也就是部署bind服务的服务器IP,也可以做host解析:harbor.od.com 默认账号:admin 默认密码:Harbor12345 登录后创建一个新的仓库,一会测试用
6、私有仓库推镜像
docker pull nginx:1.7.9 docker login harbor.od.com docker tag 84581e99d807 harbor.od.com/public/nginx:v1.7.9 docker push harbor.od.com/public/nginx:v1.7.9
重启harbor命令
docker-compose down 关闭 cd /opt/harbor ./prepare 更新配置文件 docker-compose up -d 启动
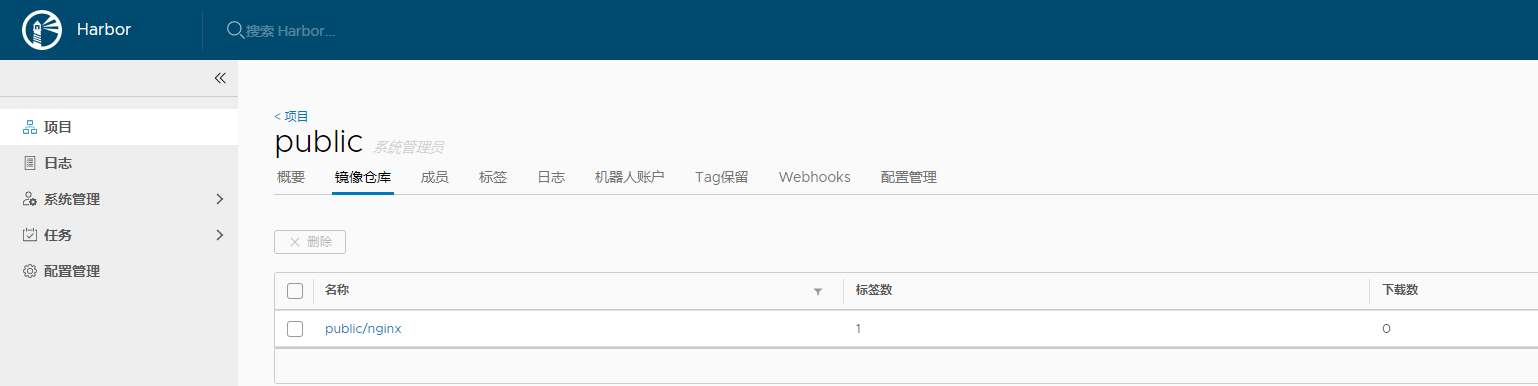
然后去私有仓库上看下:
五、搭建etcd集群
1、签发证书
vim /opt/certs/ca-config.json { "signing": { "default": { "expiry": "175200h" }, "profiles": { "server": { "expiry": "175200h", "usages": [ "signing", "key encipherment", "server auth" ] }, "client": { "expiry": "175200h", "usages": [ "signing", "key encipherment", "client auth" ] }, "peer": { "expiry": "175200h", "usages": [ "signing", "key encipherment", "server auth", "client auth" ] } } } } vim /opt/certs/etcd-peer-csr.json { "CN": "k8s-etcd", "hosts": [ "192.168.112.20", "192.168.112.21", "192.168.112.22", "192.168.112.23" ], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "L": "BeiJing", "ST": "BeiJing", "O": "od", "OU": "ops" } ] } cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=peer etcd-peer-csr.json | cfssl-json -bare etcd-peer
2、在需要安装etcd服务得主机上创建etcd用户
按照架构设计,在21,22, 23三台上部署etcd服务:
首先创建etcd用户:
useradd -s /sbin/nologin -M etcd
id etcd
3、安装etcd
wget https://github.com/etcd-io/etcd/releases/download/v3.1.20/etcd-v3.1.20-linux-amd64.tar.gz
tar -zxvf etcd-v3.1.20-linux-amd64.tar.gz
ln -s /opt/etcd-v3.1.20-linux-amd64 /opt/etcd mkdir -p /opt/etcd/certs /data/etcd /data/logs/etcd-server
4、编写启动脚本
scp operations:/opt/certs/ca.pem . scp operations:/opt/certs/etcd-peer.pem . scp operations:/opt/certs/etcd-peer-key.pem . vim /opt/etcd/etcd-server-startup.sh #!/bin/sh ./etcd --name etcd-server-112-112 \ --data-dir /data/etcd/etcd-server \ --listen-peer-urls https://192.168.112.112:2380 \ --listen-client-urls https://192.168.112.112:2379,http://127.0.0.1:2379 \ --quota-backend-bytes 8000000000 \ --initial-advertise-peer-urls https://192.168.112.112:2380 \ --advertise-client-urls https://192.168.112.112:2379,http://127.0.0.1:2379 \ --initial-cluster etcd-server-112-112=https://192.168.112.112:2380,etcd-server-112-113=https://192.168.112.113:2380,etcd-server-112-114=https://192.168.112.114:2380 \ --ca-file ./certs/ca.pem \ --cert-file ./certs/etcd-peer.pem \ --key-file ./certs/etcd-peer-key.pem \ --client-cert-auth \ --trusted-ca-file ./certs/ca.pem \ --peer-ca-file ./certs/ca.pem \ --peer-cert-file ./certs/etcd-peer.pem \ --peer-key-file ./certs/etcd-peer-key.pem \ --peer-client-cert-auth \ --peer-trusted-ca-file ./certs/ca.pem \ --log-output stdout chmod +x /opt/etcd/etcd-server-startup.sh chown -R etcd.etcd /data/etcd/ chown -R etcd.etcd /data/logs/etcd-server/ chown -R etcd.etcd /opt/etcd-v3.1.20-linux-amd64/ chown -R etcd.etcd /opt/etcd/ chown -R etcd.etcd /opt/etcd/certs
六、安装etcdkeeper工具
etcd服务搭建完成后,里面其实存储了很多的key,如何查看和管理这些key,需要使用一个小工具,叫做etcdkeeper:
下载etcd,在etcd节点选一台
mkdir /opt/src && cd /opt/src wget https://github.com/evildecay/etcdkeeper/releases/download/v0.7.5/etcdkeeper-v0.7.5-linux_x86_64.zip 解开压缩包,需安装unzip: yum install unzip -y unzip etcdkeeper-*-linux_x86_64.zip rm etcdkeeper-*-linux_x86_64.zip mv etcdkeeper ../etcdkeeper-0.7.5 ln -s /opt/etcdkeeper-0.7.5/ /opt/etcdkeeper cd /opt/etcdkeeper chmod +x etcdkeeper
编写一个服务文件,该服务文件主要用于在后台运行etcd程序,用以提供http服务
cd /lib/systemd/system vim etcdkeeper.service [Unit] Description=etcdkeeper service After=network.target [Service] Type=simple ExecStart=/opt/etcdkeeper/etcdkeeper -h 192.168.112.21 -p 8800 ExecReload=/bin/kill -HUP $MAINPID KillMode=process Restart=on-failure PrivateTmp=true [Install] WantedBy=multi-user.target -h 指定etcdkeeper http监听的地址,这里监听的是IPV4地址10.4.7.12 -p 指定etcdkeeper http监听的端口
# systemctl start etcdkeeper 启动etcdkeeper服务 # systemctl stop etcdkeeper 停止etcdkeeper服务 # systemctl enable etcdkeeper.service 设置开机自启动 # systemctl disable etcdkeeper.service 停止开机自启动 访问安全 如果启用了etcd自身的授权,无需特别关心 如果没有自动,可以考虑使用Nginx反代,使用base auth授权. 遗留的问题 当发布到公网环境时,v2可以查看到数据,v3查看不到数据。 目前没查到原因. 测试访问 http://192.168.112.20:8800/etcdkeeper/




 浙公网安备 33010602011771号
浙公网安备 33010602011771号