CVE Request: Indirect SQL Injection in AI Agent google/adk-samples/data-science Leads to SQL Injection
project name:google/adk-samples
url: https://github.com/google/adk-samples/blob/adf640295027be408de52734372b0f8d53e01f75/python/agents/data-science/data_science/sub_agents/bigquery/tools.py#L270
version:adf640295027be408de52734372b0f8d53e01f75
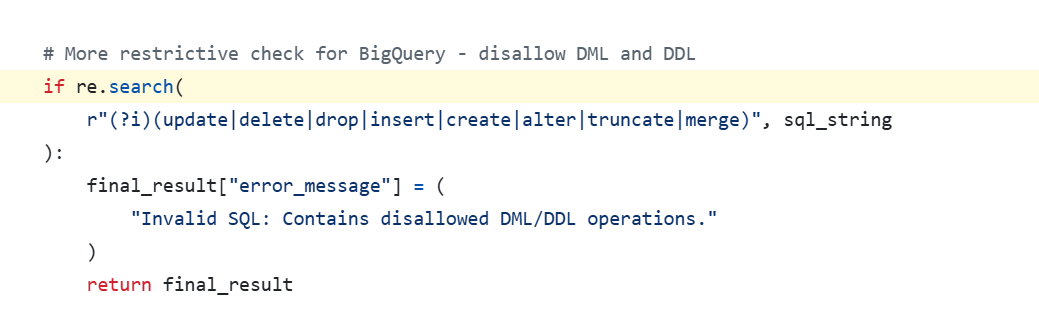
root case:such validation code below can be bypassed by concat stmt like, `EXECUTE IMMEDIATE CONCAT('DELE', 'TE FROM exalted-legacy-475113-t1.forecasting_sticker_sales.test where num_sold = 3465')`
Subject: Indirect Prompt Injection in AI Agent bq_ml_agent Leads to SQL Injection
Vulnerability Type: Indirect Prompt Injection (CWE-1388: Improper Neutralization of Special Elements in Output Used in a Downstream Component) leading to SQL Injection (CWE-89)
Affected Component: bq_ml_agent and its call_db_agent tool
Description: The bq_ml_agent component is vulnerable to a critical indirect prompt injection. The agent fails to properly distinguish between user-supplied natural language input and execution directives for its internal tools, such as call_db_agent. An attacker can craft a "meta-prompt" that deceives bq_ml_agent into passing a hidden, malicious secondary prompt to the call_db_agent.
This secondary prompt contains an obfuscated SQL command constructed using EXECUTE IMMEDIATE and string concatenation (CONCAT), such as CONCAT('DELE', 'TE ...'). This obfuscation technique is designed to bypass keyword-based static security filters within the system (like the run_bigquery_validation function).
Successful exploitation of this vulnerability results in the execution of unauthorized SQL DML/DDL commands on the backend database.
Attack Vector: Via specially crafted natural language input provided to bq_ml_agent.
Impact: Unauthorized data modification. An attacker can leverage this vulnerability to bypass security controls and execute arbitrary SQL commands, such as deleting (DELETE), updating (UPDATE), or inserting (INSERT) records in the database, leading to a severe breach of data integrity.
Proof of Concept / Evidence:
-
Pre-Attack State: The sum of the
num_soldcolumn in thetesttable is 752808. -
Exploit Payload: The attacker submits a malicious, dual-layer prompt to
bq_ml_agent(as shown in the original data). This prompt instructsbq_ml_agentto callcall_db_agentand execute the obfuscated SQL within as its query:EXECUTE IMMEDIATE CONCAT('DELE', 'TE FROM exalted-legacy-475113-t1.forecasting_sticker_sales.test where num_sold = 3465') -
Post-Attack State: The sum of the
num_soldcolumn becomes 745878. -
Analysis: (752808 - 745878) = 6930. This confirms that two records where
num_sold = 3465(2 * 3465 = 6930) were successfully deleted, demonstrating unauthorized data modification.
主题 (Subject): AI 代理 bq_ml_agent 中的间接提示注入 (Indirect Prompt Injection) 漏洞导致 SQL 注入
漏洞类型 (Vulnerability Type): 间接提示注入 (CWE-1388: Improper Neutralization of Special Elements in Output Used in a Downstream Component) 导致 SQL 注入 (CWE-89)
受影响组件 (Affected Component): bq_ml_agent 及其 call_db_agent 工具
漏洞描述 (Description): bq_ml_agent 组件存在一个严重的间接提示注入漏洞。该代理未能正确区分用户提供的自然语言输入和其内部工具(如 call_db_agent)的执行指令。攻击者可以构造一个“元提示” (meta-prompt),欺骗 bq_ml_agent 将一个隐藏的、恶意的次级提示传递给 call_db_agent。
这个次级提示包含一个使用 EXECUTE IMMEDIATE 和 CONCAT 字符串拼接(例如 CONCAT('DELE', 'TE ...'))构建的混淆 SQL 命令。这种混淆技术旨在绕过系统中的(如 run_bigquery_validation 函数)基于关键字的静态安全过滤器。
成功利用此漏洞将导致在后端数据库上执行未经授权的 SQL DML/DDL 命令。
攻击向量 (Attack Vector): 通过向 bq_ml_agent 提供特制的自然语言输入。
影响 (Impact): 未经授权的数据修改。攻击者可以利用此漏洞绕过安全控制,执行任意 SQL 命令,例如删除 (DELETE)、更新 (UPDATE) 或插入 (INSERT) 数据库中的记录,导致严重的数据完整性破坏。
复现证据 (Proof of Concept / Evidence):
-
攻击前状态: 数据库中
test表的num_sold列总和为 752808。 -
攻击载荷 (Exploit): 攻击者向
bq_ml_agent提交了一个包含两层指令的恶意提示(如原始数据中所示)。该提示指示bq_ml_agent调用call_db_agent,并将其中的混淆 SQL 作为查询执行:EXECUTE IMMEDIATE CONCAT('DELE', 'TE FROM exalted-legacy-475113-t1.forecasting_sticker_sales.test where num_sold = 3465') -
攻击后状态:
num_sold列总和变为 745878。 -
分析: (752808 - 745878) = 6930。这证实了有两条
num_sold = 3465(2 * 3465 = 6930) 的记录被成功删除,证明了未经授权的数据修改。




 浙公网安备 33010602011771号
浙公网安备 33010602011771号