9.14 BUUCTF RSA 1
This is the problem that requires some math skills.
We have p,q,dp,dq,c.
Now let's start to solve it.
dp ≡ d mod(p-1)
dq ≡ d mod(q-1)
m ≡ c^d mod n
m = kxn + c^d = kpq + c^d
we let m % p and m % q
=> m1 = c^d mod p
m2 = c^d mod q
c^d = pxk' + m1
m2 = pxk' + m1 mod q
=> k' = (m2-m1)xinv(p) mod q
Now, we can easily calculate k', then we take k' into above.
m ≡ c^d = pxk' + m1 mod n
So, we just need to work out m1,m2.
Notice that dp ≡ d mod(p-1), according to Fermat's, c^(p-1) ≡ 1 mod p.So c^d ≡ c^dp mod p.The same for dq, c^d ≡ c^dq mod q.
Finally we solve it.
Here we code:
from Crypto.Util.number import *
import primefac
import gmpy2
def modinv(a,n):
return primefac.modinv(a,n) % n
p = 8637633767257008567099653486541091171320491509433615447539162437911244175885667806398411790524083553445158113502227745206205327690939504032994699902053229
q = 12640674973996472769176047937170883420927050821480010581593137135372473880595613737337630629752577346147039284030082593490776630572584959954205336880228469
n = p*q
dp = 6500795702216834621109042351193261530650043841056252930930949663358625016881832840728066026150264693076109354874099841380454881716097778307268116910582929
dq = 783472263673553449019532580386470672380574033551303889137911760438881683674556098098256795673512201963002175438762767516968043599582527539160811120550041
c = 24722305403887382073567316467649080662631552905960229399079107995602154418176056335800638887527614164073530437657085079676157350205351945222989351316076486573599576041978339872265925062764318536089007310270278526159678937431903862892400747915525118983959970607934142974736675784325993445942031372107342103852
m1 = pow(c,dp,p)
m2 = pow(c,dq,q)
pf1 = modinv(p,q)
k = ((pf1*(m2-m1)%q)+q)%q
m = (p*k+m1)%n
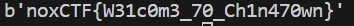
print(long_to_bytes(m))
Then we get the flag.


 浙公网安备 33010602011771号
浙公网安备 33010602011771号