9.13 RSA the same mod attack
Assume that we have 2 groups of data, we find that n is the same and m also is.
What can we do to work out m without factorize n?(actually we cannot factorize n at all.)
Notice that (e1,e2)=1
We could use ExGcd to calculate (s1,s2) satisfied with the equal: s1xe1+s2xe2=1
Next, m = (c1^s1) * (c2^s2) % n
It can be easily proved just to take c1=m^e1%n and c2=m^e2%n into it.
Now, we have our solution but there still is a problem: we know that either s1 or s2 is negative.We cannot let a negative to be exponent.So we can use inv of c1 to transfer s1 ---> -s1, for the reason that c1^s1 % n = inv(c1)^(-s1) % n
Here we code:
from Crypto.Util.number import *
import primefac
import gmpy2
def same_mod_attack(n,e1,e2,c1,c2):
def modinv(a,n):
return primefac.modinv(a,n) % n
def exgcd(a,b):
x , lastx = 0,1
y , lasty = 1,0
while b!=0:
q = a // b
a , b = b , a%b
x , lastx = lastx - q*x , x
y , lasty = lasty - q*y , y
return (lastx,lasty)
s = exgcd(e1,e2)
s1 = s[0]
s2 = s[1]
if s1<0 :
s1 = -s1
c1 = modinv(c1,n)
if c1<n:
c1 += n
elif s2<0:
s2 = -s2
c2 = modinv(c2,n)
if c2<n:
c2 += n
m = (pow(c1,s1,n)*pow(c2,s2,n)) % n
return m
if __name__ == '__main__':
c1 = 22322035275663237041646893770451933509324701913484303338076210603542612758956262869640822486470121149424485571361007421293675516338822195280313794991136048140918842471219840263536338886250492682739436410013436651161720725855484866690084788721349555662019879081501113222996123305533009325964377798892703161521852805956811219563883312896330156298621674684353919547558127920925706842808914762199011054955816534977675267395009575347820387073483928425066536361482774892370969520740304287456555508933372782327506569010772537497541764311429052216291198932092617792645253901478910801592878203564861118912045464959832566051361
n = 22708078815885011462462049064339185898712439277226831073457888403129378547350292420267016551819052430779004755846649044001024141485283286483130702616057274698473611149508798869706347501931583117632710700787228016480127677393649929530416598686027354216422565934459015161927613607902831542857977859612596282353679327773303727004407262197231586324599181983572622404590354084541788062262164510140605868122410388090174420147752408554129789760902300898046273909007852818474030770699647647363015102118956737673941354217692696044969695308506436573142565573487583507037356944848039864382339216266670673567488871508925311154801
e1 = 11187289
c2 = 18702010045187015556548691642394982835669262147230212731309938675226458555210425972429418449273410535387985931036711854265623905066805665751803269106880746769003478900791099590239513925449748814075904017471585572848473556490565450062664706449128415834787961947266259789785962922238701134079720414228414066193071495304612341052987455615930023536823801499269773357186087452747500840640419365011554421183037505653461286732740983702740822671148045619497667184586123657285604061875653909567822328914065337797733444640351518775487649819978262363617265797982843179630888729407238496650987720428708217115257989007867331698397
e2 = 9647291
m = same_mod_attack(n,e1,e2,c1,c2)
print(long_to_bytes(m))
Rember the process of ExGcd, which is a little different from what I coded in C++.
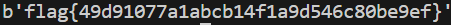
Finally, we get the flag:


 浙公网安备 33010602011771号
浙公网安备 33010602011771号