linux第九周作业
1、简述DNS服务器原理,并搭建主-辅服务器。
DNS:Domain Name System 域名系统,应用层协议,是互联网的一项服务。它作为将域名和IP地址相互
映射的一个分布式数据库,能够使人更方便地访问互联网,基于C/S架构,服务器端:53/udp, 53/tcp;
dns工作原理:
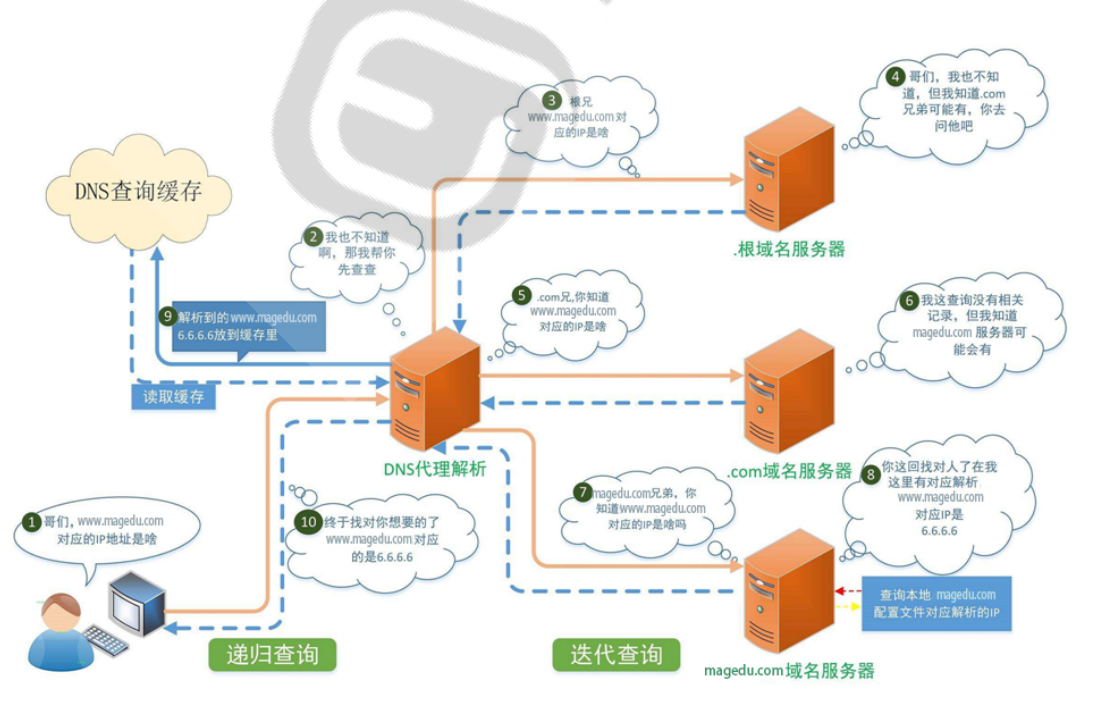
搭建主从DNS服务器:
需要4台主机
DNS客户端:192.168.6.130 /24
主DNS服务器:192.168.6.136/24
从DNS服务器:192.168.6.137/24
WEB服务器:192.168.6.131/24
1>主服务器配置
yum install bind -y #下载DNS服务器包
#修改配置文件
vim /etc/named.conf
#注释掉下面两行
// listen-on port 53 { 127.0.0.1; };
// allow-query { localhost; };
#只允许从服务器进行区域传输
allow-transfer {192.168.6.137;};
vim /etc/named.rfc1912.zones
#加上这段
zone "magedu.org" {
type master;
file "magedu.org.zone";
};
cp -p /var/named/named.localhost /var/named/magedu.org.zone
#如果没有-p,-a,需要改权限。chgrp named magedu.org.zone
vim /var/named/magedu.org.zone
$TTL 1D
@ IN SOA master admin.magedu.org. (
1 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS master
NS slave
master A 192.168.6.137
slave A 192.168.6.137
www A 192.168.6.131
systemctl start named #第一次启动服务
rndc reload #不是第一次启动服务
2>从服务器配置
yum install bind -y
vim /etc/named.conf
// listen-on port 53 { 127.0.0.1; };
// allow-query { localhost; };
#不允许其它主机进行区域传输
allow-transfer { none;};
vim /etc/named.rfc1912.zones
zone "magedu.org" {
type slave;
masters { 192.168.6.136;};
file "slaves/magedu.org.slave";
};
systemctl start named #第一次启动服务
rndc reload #不是第一次启动服务
#查看区域数据库文件是否生成
[root@localhost ~]# ll /var/named/slaves/magedu.org.slave
-rw-r--r-- 1 named named 317 Feb 20 15:18 /var/named/slaves/magedu.org.slave
3>web服务和客户端配置
web:
#安装http服务 yum install httpd #配置主页面 echo www.xinye.org > /var/www/html/index.html #启动服务 systemctl start httpd
客户端配置:
vim /etc/sysconfig/network-scripts/ifcfg-eth0 DNS1=192.168.6.136 DNS2=192.168.6.137 #重启网卡 systemclt restart NetworkManager [root@centos7-130 ~]#cat /etc/resolv.conf # Generated by NetworkManager nameserver 192.168.6.136 nameserver 192.168.6.137
4>客户端测试
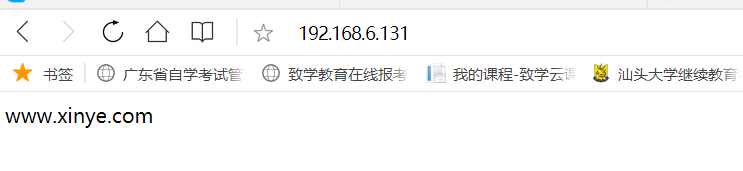
[root@centos7-130 ~]#dig www.magedu.org ; <<>> DiG 9.11.13-RedHat-9.11.13-3.el8 <<>> www.magedu.org ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 1263 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 3 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ; COOKIE: 01cef15e2ace286fd6382471621462fa9ebd552f2152b63c (good) ;; QUESTION SECTION: ;www.magedu.org. IN A ;; ANSWER SECTION: www.magedu.org. 86400 IN A 192.168.6.131 ;; AUTHORITY SECTION: magedu.org. 86400 IN NS slave.magedu.org. magedu.org. 86400 IN NS master.magedu.org. ;; ADDITIONAL SECTION: master.magedu.org. 86400 IN A 192.168.6.136 slave.magedu.org. 86400 IN A 192.168.6.137 ;; Query time: 0 msec ;; SERVER: 192.168.6.136#53(192.168.6.136) ;; WHEN: Tue Feb 22 12:13:47 CST 2022 ;; MSG SIZE rcvd: 160 [root@centos7-130 ~]#curl www.magedu.org www.xinye.com
#在主服务器上停止DNS服务
systemctl stop named
[root@centos7-130 ~]#dig www.magedu.org ; <<>> DiG 9.11.13-RedHat-9.11.13-3.el8 <<>> www.magedu.org ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 38660 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 3 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ; COOKIE: 7af74bc9369332320ff396526214630e58a350e4f94aecaa (good) ;; QUESTION SECTION: ;www.magedu.org. IN A ;; ANSWER SECTION: www.magedu.org. 86400 IN A 192.168.6.131 ;; AUTHORITY SECTION: magedu.org. 86400 IN NS slave.magedu.org. magedu.org. 86400 IN NS master.magedu.org. ;; ADDITIONAL SECTION: master.magedu.org. 86400 IN A 192.168.6.136 slave.magedu.org. 86400 IN A 192.168.6.137 ;; Query time: 2 msec ;; SERVER: 192.168.6.137#53(192.168.6.137) ;; WHEN: Tue Feb 22 12:14:07 CST 2022 ;; MSG SIZE rcvd: 160 [root@centos7-130 ~]#curl www.magedu.org www.xinye.com
2、搭建并实现智能DNS。
需要五台主机
DNS主服务器和web服务器1:192.168.6.133,172.16.0.8/16
web服务器2:192.168.6.134 /24
web服务器3:172.16.0.7 /16
DNS客户端1:192.168.6.136 /24
DNS客户端2:172.16.0.6/16
#配置DNS主服务器两个IP地址
#eth0:192.168.6.133/24
#eth1: 172.16.0.8/16
#主DNS服务端配置文件实现 view
vim /etc/named.conf
#在文件最前面加下面行
acl beijingnet {
192.168.6.0/24;
};
acl shanghainet {
172.16.0.0/16;
};
acl othernet {
any;
};
#注释掉下面两行
// listen-on port 53 { 127.0.0.1; };
// allow-query { localhost; };
#其它略
# 创建view
view beijingview {
match-clients { beijingnet;};
include "/etc/named.rfc1912.zones.bj";
};
view shanghaiview {
match-clients { shanghainet;};
include "/etc/named.rfc1912.zones.sh";
};
view otherview {
match-clients { othernet;};
include "/etc/named.rfc1912.zones.other";
};
#实现区域配置文件
vim /etc/named.rfc1912.zones.bj
zone "." IN {
type hint;
file "named.ca";
};
zone "magedu.org" {
type master;
file "magedu.org.zone.bj";
};
vim /etc/named.rfc1912.zones.sh
zone "." IN {
type hint;
file "named.ca";
};
zone "magedu.org" {
type master;
file "magedu.org.zone.sh";
};
vim /etc/named.rfc1912.zones.other
zone "." IN {
type hint;
file "named.ca";
};
zone "magedu.org" {
type master;
file "magedu.org.zone.other";
};
#设置区域文件权限
[root@localhost ~]#chgrp named /etc/named.rfc1912.zones.bj
[root@localhost ~]#chgrp named /etc/named.rfc1912.zones.sh
[root@localhost ~]#chgrp named /etc/named.rfc1912.zones.other
#创建区域数据库文件
vim /var/named/magedu.org.zone.bj
$TTL 1D
@ IN SOA master admin.magedu.org. (
2019042214 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS master
master A 192.168.6.133
websrv A 192.168.6.134
www CNAME websrv
vim /var/named/magedu.org.zone.sh
$TTL 1D
@ IN SOA master admin.magedu.org. (
2019042214 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS master
master A 172.16.0.8
websrv A 172.16.0.7
www CNAME websrv
vim /var/named/magedu.org.zone.other
$TTL 1D
@ IN SOA master admin.magedu.org. (
2019042214 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS master
master A 192.168.6.133
websrv A 127.0.0.1
www CNAME websrv
[root@localhost ~]#chgrp named /var/named/magedu.org.zone.bj
[root@localhost ~]#chgrp named /var/named/magedu.org.zone.sh
[root@localhost ~]#chgrp named /var/named/magedu.org.zone.other
#实现位于不同区域的三个WEB服务器
#分别在三台主机上安装http服务
#在web服务器1:192.168.6.133实现
yum install httpd
echo www.magedu.org in Other > /var/www/html/index.html
systemctl start httpd
#在web服务器2:192.168.6.134
echo www.magedu.org in Beijing > /var/www/html/index.html
systemctl start httpd
#在web服务器3:172.16.0.7
yum install httpd
echo www.magedu.org in Shanghai > /var/www/html/index.html
systemctl start httpd
#在客户端测试
#分别在三台主机上访问
#DNS客户端1:192.168.6.136 实现,确保DNS指向192.168.6.133
curl www.magedu.org
www.magedu.org in Beijing
#DNS客户端2:172.16.0.6 实现,确保DNS指向172.16.0.8
curl www.magedu.org
www.magedu.org in Shanghai
#DNS客户端3:192.168.6.133 实现,,确保DNS指向127.0.0.1
curl www.magedu.org
www.magedu.org in Other
3、使用iptable实现: 放行ssh,telnet, ftp, web服务80端口,其他端口服务全部拒绝
#放行ssh,telnet, ftp, web服务80端口
[root@localhost ~]#iptables -IINPUT -p tcp -m multiport --dport 21,22,23,80 -j ACCEPT
#拒绝其他全部端口
[root@localhost ~]#iptables -A INPUT -j DROP
[root@localhost ~]#iptables -vnL
Chain INPUT (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
376 26904 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 multiport dports 21,22,23,80
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0
4、NAT原理总结
NAT的作用:
IP地址分为公网IP与私网IP。一般情况下,在互联网中,公网IP可直接访问,私网IP无法直接访问。而NAT则是将私网IP地址转换为公网IP地址(将IP报文头部的私网IP地址改为可以提供访问的公网IP地址),从而实现用户上网功能或服务器在互联网上提供服务。NAT还可以使得一个公网IP代表多个不同的内网IP,这样便节省了IP地址资源。
NAT的类型与分类:
- 静态转换:私有地址与公有地址进行一对一的映射。这种一对一映射无法缓解可用公有地址短缺的问题。
- 动态转换:私有地址与公有地址进行一对多的映射。首先建立公有地址地址池,私有地址向外通信时,会从公有地址地址池中选择非在用的公有地址进行映射,当通信结束时,释放映射关系,公有地址重新恢复到地址池中待用。弊端:若私有地址向外通信,而公有地址地址池中无可用公有地址时,会等待公有地址释放后在进行通信。
- 端口转换:在大多数网络中,一般都使用的是IP上的某个端口(如80、443、3389等),所以不需要进行全地址映射,只需要私有地址端口映射到公有地址端口上,直接访问公有地址加端口号的形式便可以。这样可以使得一个公有地址可以对应多个私有地址,从而大大缓解了公有地址紧缺的问题。
- Easy IP:为小型网络,一般为家庭、小型网吧、办公室等内部主机不多的地方。通过拨号方式获取一个临时公网IP地址进行外网的访问
SNAT与DNAT区别:
- SNAT是私网访问外网时,报文中源IP地址(私网IP地址)转换为公网IP地址过程。此转换可以使用静态、动态等转换方式,且内部的多台主机共用同一公网IP地址进行外网访问。
- DNAT是外网访问私网时,报文中目的IP地址(公网IP地址)转换为私网IP地址过程。此转换过程可以使用静态、动态、端口等转换方式。
5、iptables实现SNAT和DNAT,并对规则持久保存。
SNAT:
防火墙设备:192.168.6.133/24;192.168.160.129/24
lan-server:192.168.6.136 /24
internet:192.168.160.128 /24
#firewall IP配置
[root@localhost ~]#ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:7b:d4:26 brd ff:ff:ff:ff:ff:ff
inet 192.168.6.133/24 brd 192.168.6.255 scope global noprefixroute eth0
valid_lft forever preferred_lft forever
inet6 fe80::1c6e:6381:e70f:a29b/64 scope link noprefixroute
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:7b:d4:30 brd ff:ff:ff:ff:ff:ff
inet 192.168.160.129/24 brd 192.168.160.255 scope global noprefixroute dynamic eth1
valid_lft 999sec preferred_lft 999sec
inet6 fe80::39c4:3c14:ddd7:6f70/64 scope link noprefixroute
valid_lft forever preferred_lft forever
#LAN-server配置
[root@centos7-136 ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:16:cf:d7 brd ff:ff:ff:ff:ff:ff
inet 192.168.6.136/24 brd 192.168.6.255 scope global noprefixroute eth0
valid_lft forever preferred_lft forever
inet6 fe80::9498:d2c7:5a01:e5fd/64 scope link noprefixroute
valid_lft forever preferred_lft forever
[root@centos7-136 ~]# ip route
default via 192.168.6.133 dev eth0 proto static metric 100
192.168.6.0/24 dev eth0 proto kernel scope link src 192.168.6.136 metric 100
#外网设备配置
[root@centos7-135 ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:d5:e4:c7 brd ff:ff:ff:ff:ff:ff
inet 192.168.160.128/24 brd 192.168.160.255 scope global noprefixroute eth0
valid_lft forever preferred_lft forever
inet6 fe80::ede9:a8fc:d618:52bb/64 scope link noprefixroute
valid_lft forever preferred_lft forever
3: eth1: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc pfifo_fast state DOWN group default qlen 1000
link/ether 00:0c:29:d5:e4:d1 brd ff:ff:ff:ff:ff:ff
[root@centos7-135 ~]# ip route
192.168.160.0/24 dev eth0 proto kernel scope link src 192.168.160.128 metric 100
#lan-server上测试 [root@lan-server ~]# ping 192.168.160.128 PING 192.168.160.128 (192.168.160.128) 56(84) bytes of data. 64 bytes from 192.168.160.128: icmp_seq=1 ttl=63 time=0.804 ms 64 bytes from 192.168.160.128: icmp_seq=2 ttl=63 time=1.52 ms 64 bytes from 192.168.160.128: icmp_seq=3 ttl=63 time=1.68 ms ^C --- 192.168.160.128 ping statistics --- 3 packets transmitted, 3 received, 0% packet loss, time 2009ms rtt min/avg/max/mdev = 0.804/1.338/1.688/0.384 ms [root@lan-server ~]# curl 192.168.160.128 www.magedu.org
DNAT:
防火墙设备:192.168.6.133/24;192.168.160.129/24
lan-server:192.168.6.136 /24
internet:192.168.160.128 /24
#启用路由转发 [root@firewall ~]#vim /etc/sysctl.conf net.ipv4.ip_forward=1 [root@firewall ~]#sysctl -p [root@firewall ~]#iptables -t nat -A PREROUTING -d 192.168.0.8 -p tcp --dport 80 -j DNAT --to-destination 10.0.0.7:80 [root@centos7-135 ~]# curl 192.168.160.129 lan-server
保存规则:
[root@localhost ~]#iptables-save > /etc/sysconfig/iptables [root@localhost ~]#cat /etc/sysconfig/iptables # Generated by iptables-save v1.4.21 on Sat Feb 19 13:49:42 2022 *filter :INPUT ACCEPT [189:13636] :FORWARD ACCEPT [0:0] :OUTPUT ACCEPT [115:24108] COMMIT # Completed on Sat Feb 19 13:49:42 2022 # Generated by iptables-save v1.4.21 on Sat Feb 19 13:49:42 2022 *nat :PREROUTING ACCEPT [0:0] :INPUT ACCEPT [0:0] :OUTPUT ACCEPT [1:76] :POSTROUTING ACCEPT [0:0] -A PREROUTING -d 192.168.160.129/32 -p tcp -m tcp --dport 80 -j DNAT --to-destination 192.168.6.136:80 -A POSTROUTING -s 192.168.6.0/24 -j MASQUERADE COMMIT # Completed on Sat Feb 19 13:49:42 2022







 浙公网安备 33010602011771号
浙公网安备 33010602011771号