202312_隐写
tags:AES,PNG高度隐写,文件分离
0x00. 题目
附件路径:https://pan.baidu.com/s/1GyH7kitkMYywGC9YJeQLJA?pwd=Zmxh#list/path=/CTF附件
附件名称:202312_Misc.zip
见附件KEY=154,320,976,543,209.75乘8.txt
0x01. WP
1.从文件内容和文件名可以看出是AES隐写
key=154320976543209.75*8=1234567812345678
使用在线网站或脚本均可获得明文
from Crypto.Cipher import AES
from Crypto.Util.Padding import unpad
import hashlib
import base64
# 预留变量:请在此处填入你的Base64编码密文和密码
# 例如 "k7y6Cq7IeQe5xD5grlHR+Q=="
with open("KEY=154,320,976,543,209.75乘8.txt",'r') as f:
ciphertext_b64 = f.read()
# AES ECB模式解密
def decrypt_aes_ecb(ciphertext, key):
cipher = AES.new(key, AES.MODE_ECB)
decrypted = cipher.decrypt(ciphertext)
return unpad(decrypted, AES.block_size)
try:
ciphertext = base64.b64decode(ciphertext_b64)
# 执行解密
plaintext = decrypt_aes_ecb(ciphertext, b'1234567812345678')
# 输出结果
print("解密成功!")
print("明文内容(字节):", plaintext)
print("明文文本:", plaintext.decode('utf-8'))
except (ValueError, base64.binascii.Error) as e:
print(f"解密失败:{str(e)}")
print("可能原因:1. 密码错误 2. 密文格式不正确 3. 填充错误")
except UnicodeDecodeError:
print("解密后的数据包含非UTF-8字符,以下是原始字节:")
print(plaintext)
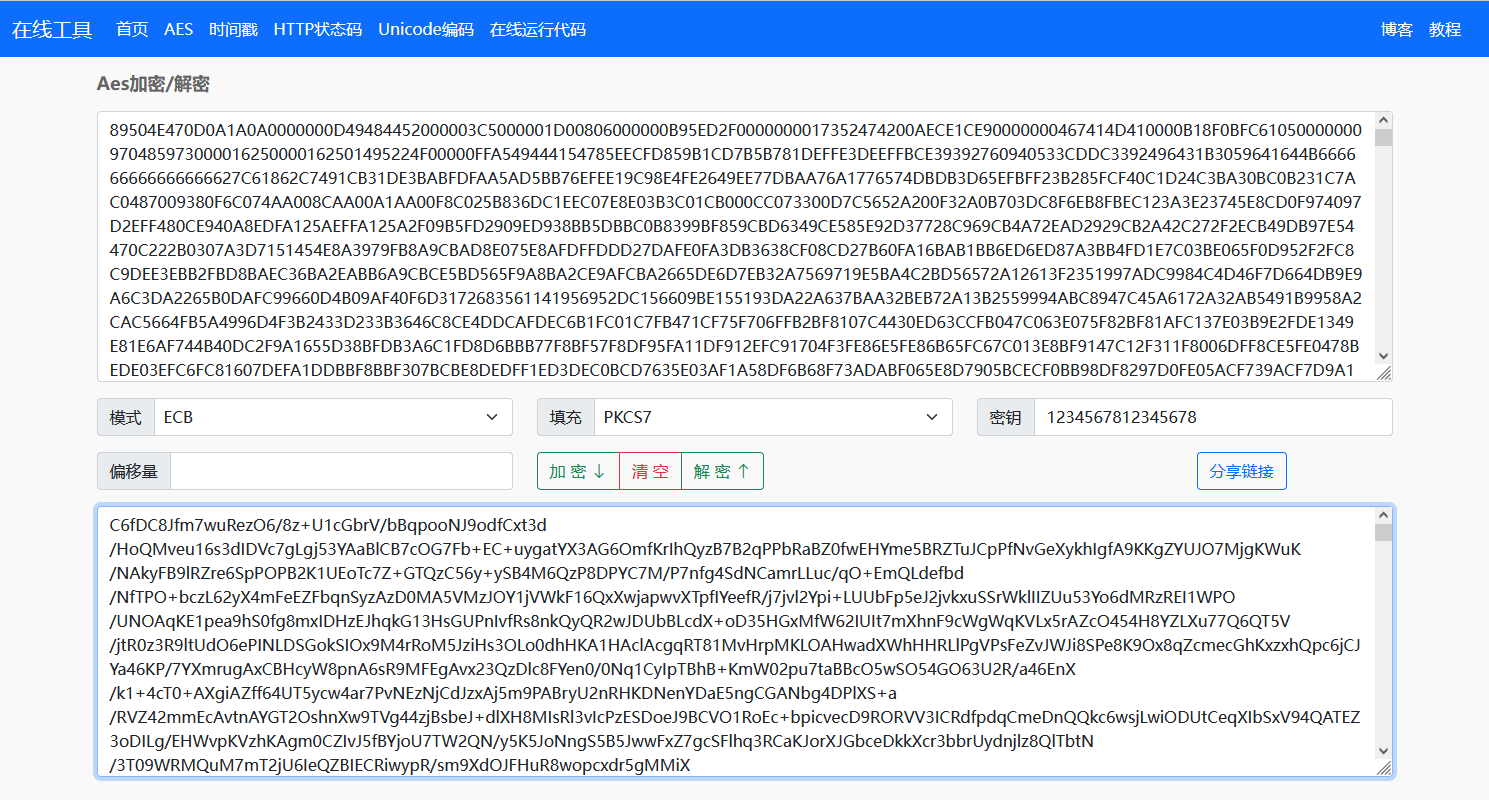
2.从文件头初步判断解码后为PNG文件的十六进制格式
89504E47为标准的PNG文件头,导出另存后使用Tweak进行校验,发现该文件高度被修改,修复后发现被隐藏信息CTF12345fas5v2feq

3. 发现文件十六进制内容中还包含ZIP文件特征码504B0304
使用foremost进行扫描分离或直接将后端附加十六进制内容保存为ZIP文件
或者直接使用脚本分别保存对应文件
import os
# 可选:自定义输出路径(默认使用当前目录的output.bin)
output_path1 = "hex_data1.png"
output_path2 = "hex_data2.zip"
def save_hex_to_file(hex_data, filename):
"""
将十六进制字符串保存为二进制文件
:param hex_data: 十六进制字符串(允许包含空格)
:param filename: 输出文件名
"""
try:
# 预处理字符串(移除空白字符和非十六进制字符)
clean_hex = "".join(c for c in hex_data.strip() if c in "0123456789abcdefABCDEF")
# 校验数据有效性
if len(clean_hex) == 0:
raise ValueError("输入不包含有效十六进制字符")
if len(clean_hex) % 2 != 0:
raise ValueError("十六进制字符串长度应为偶数")
# 转换十六进制到二进制数据
byte_data = bytes.fromhex(clean_hex)
# 写入文件
with open(filename, 'wb') as f:
f.write(byte_data)
return True, os.path.abspath(filename), len(byte_data)
except Exception as e:
return False, str(e), 0
if __name__ == "__main__":
with open("01.aes_decode.txt",'r') as f:
sHEX = f.read()
success, result_info, file_size = save_hex_to_file(sHEX, output_path1)
sHEX = "504B0304140009000800AC912B57A233809F340000002600000008000000666C61672E747874501A6ED5FD0EEC19EA8DDC53A1ACBAC5119805FD976994A3CBFE76C8B08930B20A44A66A83A1696533E34C916D402F68539F13FF504B01021400140009000800AC912B57A233809F3400000026000000080024000000000000002000000000000000666C61672E7478740A0020000000000001001800812A4F9898E4D901812A4F9898E4D901DD6EC38F98E4D901504B050600000000010001005A0000005A000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000"
success, result_info, file_size = save_hex_to_file(sHEX, output_path2)
if success:
print(f"\n✅ 文件保存成功!")
print(f"文件路径:{result_info}")
print(f"文件大小:{file_size} 字节")
print(f"目录内容:{os.listdir(os.path.dirname(result_info))}")
else:
print("\n❌ 保存失败:")
print(f"错误信息:{result_info}")
print("可能原因:")
print("- 包含非法字符(只允许0-9, a-f, A-F)")
print("- 字符串长度为奇数")
print("- 文件路径没有写入权限")
发现压缩包存在密码,尝试使用步骤2中得到的字符串对压缩包进行解压,获得flag为flag{f3e7a7577ddbc64dfcd03f1d97197b03}


 AES,PNG高度隐写,文件分离
AES,PNG高度隐写,文件分离

 浙公网安备 33010602011771号
浙公网安备 33010602011771号